Mambo Exploit Confirmed in the Wild
In reference to yesterday's diary entry about the vulnerability in the Mambo content management system, we received several confirmations that it is being exploited in the wild. An ISC reader supplied us with a captured attack packet, which demonstrated an attempt to upload a copy of a PHP-based backdoor (Loader'z WEB Shell) to the vulnerable system.
The official fix to address the flaw will be released later this month as part of Mambo 4.5.3. In the mean while, you can patch your Mambo system manually by following instructions in the following posting:
http://forum.mamboserver.com/showthread.php?t=65917
Thanks to Rick Hoppe for the pointer to the fix.
Although we initially reported that some versions of PHP may not be vulnerable to this attack, the Mambo Development Team has revised their assessment to state that all versions of PHP are vulnerable. They also point out that the flaw "is not specific to Mambo and has not been totally blocked in Joomla, as can be verified in the Joomla forum." The fix listed on the Mambo forum "can be applied at the entry point to any PHP application that may be vulnerable, including Joomla." Joomla is another PHP-based content management system. This, along with other security issues, is addressed in Joomla 1.0.4.
If you applied the Mambo fix yesterday, you may want to revisit their forum, because they've updated their recommendations since originally publishing them.
Matt Jonkman at Bleeding Snort has developed a Snort signature to detect attempts to exploit this vulnerability. The signature is available at the following URL:
http://www.bleedingsnort.com/cgi-bin/viewcvs.cgi/sigs/WEB/WEB_Mambo?view=markup
Please send us your feedback regarding the effectiveness of this signature, and we'll be sure to relay your commends to Bleeding Snort.
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
The official fix to address the flaw will be released later this month as part of Mambo 4.5.3. In the mean while, you can patch your Mambo system manually by following instructions in the following posting:
http://forum.mamboserver.com/showthread.php?t=65917
Thanks to Rick Hoppe for the pointer to the fix.
Although we initially reported that some versions of PHP may not be vulnerable to this attack, the Mambo Development Team has revised their assessment to state that all versions of PHP are vulnerable. They also point out that the flaw "is not specific to Mambo and has not been totally blocked in Joomla, as can be verified in the Joomla forum." The fix listed on the Mambo forum "can be applied at the entry point to any PHP application that may be vulnerable, including Joomla." Joomla is another PHP-based content management system. This, along with other security issues, is addressed in Joomla 1.0.4.
If you applied the Mambo fix yesterday, you may want to revisit their forum, because they've updated their recommendations since originally publishing them.
Matt Jonkman at Bleeding Snort has developed a Snort signature to detect attempts to exploit this vulnerability. The signature is available at the following URL:
http://www.bleedingsnort.com/cgi-bin/viewcvs.cgi/sigs/WEB/WEB_Mambo?view=markup
Please send us your feedback regarding the effectiveness of this signature, and we'll be sure to relay your commends to Bleeding Snort.
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
Keywords:
0 comment(s)
AIM worm and AV...
We received a file called pics.exe from one of our readers. This file was appearing in a url from one of those AIM worms...nothing new, right? Almost...the thing with this file is:
- It is a RAR file, which contatins 4 different files, which will be installed at C:WINDOWSmsupd
- rep.exe - an SDBot variant
- 1004270.exe - Cheats Explorer Add-on (toolbar for IE)
- YSBAgree.exe - Is the one which will start all the others...(as referenced at the RAR file: Setup=C:WINDOWSmsupdYSBAgree.exe)
- iS.exe - looks like the one which will send the messages to the users at the AIM. Messages like the following:
->let me know if you can open this: http://home.earthlink.net/<Snip>/pics.exe
->this doesn't work for me, does it work for you? http://home.earthlink.net/<Snip>/pics.exe
->let me know what you think: http://home.earthlink.net/<Snip>/pics.exe
->holy cow...this girl is going crazy: http://home.earthlink.net/<Snip>/pics.exe
->these are pretty nice, maybe you should take a look - http://home.earthlink.net/<Snip>/pics.exe
->are these of you? they look just like you - http://home.earthlink.net/<Snip>/pics.exe
->this girl is nuts, I can't believe she did this - http://home.earthlink.net/<Snip>/pics.exe
->wow...check this out, you have to see it: http://home.earthlink.net/<Snip>/pics.exe
->this deleted all my viruses and spyware - http://home.earthlink.net/<Snip>/clean.exe
->I can't believe this acutally fixed my computer: http://home.earthlink.net/<Snip>/clean.exe
->I didn't think it would work, but it fixed everything on my computer - http://home.earthlink.net/<Snip>/clean.exe
Did I mention that from all files, the big pack one called pics.exe, rep.exe, 1004270.exe, YSBAgree.exe and iS.exe, only the rep.exe is alreayd identified by some AV vendors at VirusTotal?
So...be careful and pay attention...!
UPDATE:
As I sent them to my personal AV vendors email list, most of them are already detecting them! Good work!
Pedro Bueno - pbueno //%%// isc. sans. org
http://handlers.sans.org/pbueno
- It is a RAR file, which contatins 4 different files, which will be installed at C:WINDOWSmsupd
- rep.exe - an SDBot variant
- 1004270.exe - Cheats Explorer Add-on (toolbar for IE)
- YSBAgree.exe - Is the one which will start all the others...(as referenced at the RAR file: Setup=C:WINDOWSmsupdYSBAgree.exe)
- iS.exe - looks like the one which will send the messages to the users at the AIM. Messages like the following:
->let me know if you can open this: http://home.earthlink.net/<Snip>/pics.exe
->this doesn't work for me, does it work for you? http://home.earthlink.net/<Snip>/pics.exe
->let me know what you think: http://home.earthlink.net/<Snip>/pics.exe
->holy cow...this girl is going crazy: http://home.earthlink.net/<Snip>/pics.exe
->these are pretty nice, maybe you should take a look - http://home.earthlink.net/<Snip>/pics.exe
->are these of you? they look just like you - http://home.earthlink.net/<Snip>/pics.exe
->this girl is nuts, I can't believe she did this - http://home.earthlink.net/<Snip>/pics.exe
->wow...check this out, you have to see it: http://home.earthlink.net/<Snip>/pics.exe
->this deleted all my viruses and spyware - http://home.earthlink.net/<Snip>/clean.exe
->I can't believe this acutally fixed my computer: http://home.earthlink.net/<Snip>/clean.exe
->I didn't think it would work, but it fixed everything on my computer - http://home.earthlink.net/<Snip>/clean.exe
Did I mention that from all files, the big pack one called pics.exe, rep.exe, 1004270.exe, YSBAgree.exe and iS.exe, only the rep.exe is alreayd identified by some AV vendors at VirusTotal?
So...be careful and pay attention...!
UPDATE:
As I sent them to my personal AV vendors email list, most of them are already detecting them! Good work!
Pedro Bueno - pbueno //%%// isc. sans. org
http://handlers.sans.org/pbueno
Keywords:
0 comment(s)
Online Security Scanner from Microsoft - Windows Live Safety Center
A couple of weeks ago Microsoft revealed a beta version of its free on-line security scanning tool Windows Live Safety Center. The scanner, which currently requires the use of Internet Explorer, uses an ActiveX control to scan the visitor's system for malicious software, open ports, as well as for non-security performance issues. The screen shot below shows the tool's scanning options.
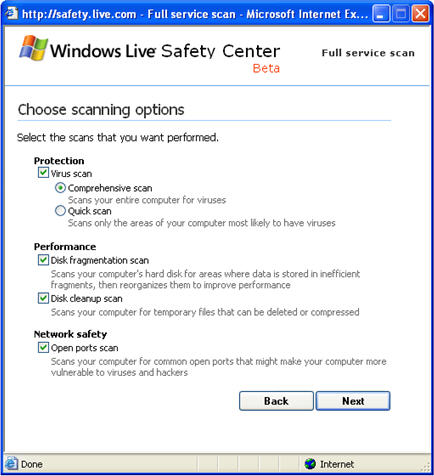

Windows Live Safety Center is reminiscent of Microsoft's free Windows Defender tool, formerly known as Windows AntiSpyware. I've been beta-testing Windows Defender for some time, and I find it quite good at detecting and blocking spyware threats, especially because of its behavioral blocking functionality that automatically blocks suspicious actions on the local system. The on-line scanner doesn't provide such continuously-monitoring features; however, its performance tuning and anti-virus functionality is very similar to the Windows OneCare service.
Windows OneCare, which is still in beta, "runs continuously in the background, offering persistent, always-on security protection and PC maintenance that generally does not require any action on your part," according to the recent Windows OneCare newsletter. Windows Live Safety Center offers similar functionality, but rather than offering continuous protection, it is an on-demand service.
While I was writing this note, Windows Live Safety Center finished scanning one of my laboratory systems. No viruses were found, but it looks like I'll need to defragment my hard drive.
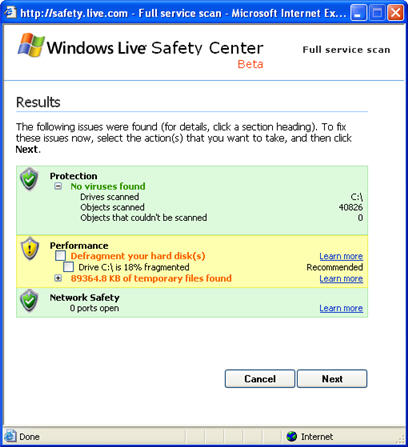
By the way, today marks the twentieth anniversary of Microsoft's release of Windows 1.0, according to the 20 Years of Windows article from Desktop Pipeline. What a fascinating journey!
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
Windows OneCare, which is still in beta, "runs continuously in the background, offering persistent, always-on security protection and PC maintenance that generally does not require any action on your part," according to the recent Windows OneCare newsletter. Windows Live Safety Center offers similar functionality, but rather than offering continuous protection, it is an on-demand service.
While I was writing this note, Windows Live Safety Center finished scanning one of my laboratory systems. No viruses were found, but it looks like I'll need to defragment my hard drive.

By the way, today marks the twentieth anniversary of Microsoft's release of Windows 1.0, according to the 20 Years of Windows article from Desktop Pipeline. What a fascinating journey!
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
Keywords:
0 comment(s)
Researching Information Security Issues
Whenever researching information security issues via a search engine such as Google, I am often presented with numerous marketing-oriented pages from security product vendors. Sometimes this can be useful, but usually what I want to see is information from technical resources, such as security mailing lists, articles, and papers. That's why I am experimenting with a custom-crafted search engine that one can create via the Rollyo service, which allows you to limit your search to specific sites of interest.
You can try my focused Information Security search here:This search scans security articles, blog entries, and mailing list posts; the current list of scanned sources is maintained on my website.
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
You can try my focused Information Security search here:This search scans security articles, blog entries, and mailing list posts; the current list of scanned sources is maintained on my website.
Lenny Zeltser
ISC Handler on Duty
www.zeltser.com
Keywords:
0 comment(s)
×
![modal content]()
Diary Archives


Comments