Competitive intelligence gathering via LinkedIn's new Company Profile pages
Individuals looking to gather competitive intelligence have a new tool at their disposal: Company Profile pages on LinkedIn, which entered beta on March 20. The new feature, while useful to many, highlights the challenges of controlling the distribution of information about a company's inner-workings.
LinkedIn compiles company details, such as new hires, promotions, office locations, and career path information, by mining the data from LinkedIn users' profiles. The auto-generated page offers an uncommon glimpse into the internal processes of the profiled company. The results are particularly impressive for small non-public organizations, because information about such entities is particularly challenging to obtain.
A LinkedIn Company Profile is a fertile ground for the individuals who gather competitive intelligence. Unfortunately, while some of them could be are pursuing generally-accepted business endeavours (e.g., sales prospecting, market analysis), others may have more nefarious plans (e.g., corporate espionage, social engineering).
Examining a Sample Company Profile
Consider the following sample profile of a private company with less than 500 employees. I revised names, titles and other identifying details without altering the nature of the compiled information. The relevant excerpts from the sample profile are below.
| A profiler of Example Inc may be interested to note which people the company recently hired, and where they came from. A number of hires in a particular division may indicate a major strategy shift. Also, new hires may be particularly vulnerable to the profiler's advances, because they have not yet settled into their new roles. | 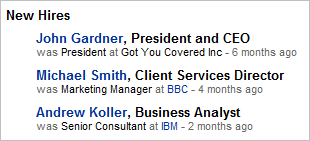 |
| The profiler may gain insight into the inner structure of the company by examining recent promotions and title changes. For example, the large number of changes 6 months ago suggests a major organizational change. Tracking this information over time helps map the company's organizational structure. | 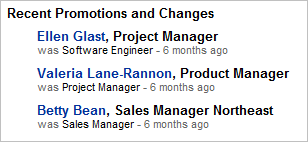 |
| The Popular Profiles section lists employees who are seen "in the news, referenced in blogs, participating in industry groups," or are active on the Linkedin site. Such active individuals might welcome the opportunity to establish a new connection, and could be targeted for sales calls or social engineering scams. | 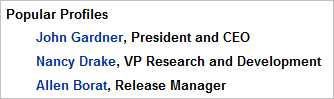 |
| Perhaps the most intriguing component of the profile is the one that outlines career paths for company employees. A profiler may observe where employees come from and head to. For example, it may be interesting to note if employees (and thus intellectual capital) leave for a competitor. |  |
| The section that lists the companies to which Example Inc employees are "most connected to" is powerful, because it may inadvertently point out the company's biggest suppliers or customers. (Employees often link to the people with whom they collaborate.) Many wish to keep this data private to conceal channel details. A profiler may also notice, for instance, if the company hires employees from its best customer. | 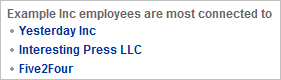 |
To experiment with Company Profile pages, locate an individual's profile on LinkedIn and click on the company name in his work history.
Controlling Data Dissemination
There is little companies can do to prevent such details from leaking into the open. One possibility is to attempt limiting which information employees may disclose information on social networking websites such as LinkedIn. Organizations may consider issuing guidelines that advise employees against including certain data in their profiles. Companies with more controlling cultures, such as some financial institutions, will be more likely to succeed at this.
LinkedIn has indicated that in the future companies may be able to customize their profiles, although it is unclear the extent to which the companies will control the details shown there. It is also unclear how LinkedIn will determine who will be authorized to act on the company's behalf when editing the profile.
LinkedIn allows individuals to remove themselves from Company Profile pages, but this comes at a cost. To be removed, the person also has to give up the ability to notify his connections of all personal profile changes.
I applaud the innovative manner in which LinkedIn now provides insights at inner-workings of companies large and small. However, it is unfortunate that LinkedIn released this feature without allowing companies and individuals to granularly control how they are being profiled.
-- Lenny
Lenny Zeltser leads a security consulting team at SAVVIS Inc and teaches a malware analysis course at SANS Institute.
When is a DMG file not a DMG file
When it is malware?
Steve (a fellow handler) sent in a link to a DMG file. Several of us wondered how to analyze it and what it might contain. While we searched our memory I downloaded it and it was discovered not to be a DMG file at all.
adrien@tester:~/bad$ file jetcodec1000.dmg
jetcodec1000.dmg: PE executable for MS Windows (GUI) Intel 80386 32-bit, Nullsoft Installer self-extracting archive
Virustotal results aren't the greatess:
File jetcodec1000.dmg received on 04.03.2008 00:49:47 (CET)
Antivirus Version Last Update Result
AhnLab-V3 2008.4.1.2 2008.04.02 -
AntiVir 7.6.0.80 2008.04.02 DR/Dldr.DNSChanger.Gen
AVG 7.5.0.516 2008.04.02 DNSChanger.AA
BitDefender 7.2 2008.04.03 Dropped:Trojan.Downloader.Zlob.ABOU
ClamAV 0.92.1 2008.04.02 Trojan.Zlob-2395
F-Prot 4.4.2.54 2008.04.02 W32/Trojan2.AIES
F-Secure 6.70.13260.0 2008.04.02 W32/Malware
Kaspersky 7.0.0.125 2008.04.03 Trojan.Win32.DNSChanger.arn
Norman 5.80.02 2008.04.02 W32/Malware
Prevx1 V2 2008.04.03 Generic.Dropper.xCodec
Symantec 10 2008.04.03 Trojan.Zlob
VBA32 3.12.6.3 2008.03.25 MalwareScope.Trojan.DnsChange.2
Webwasher-Gateway 6.6.2 2008.04.02 Trojan.Dropper.Dldr.DNSChanger.Gen
Additional information
File size: 232561 bytes
MD5: 7db1dded58e7856c4d0dcae14b3b870f
SHA1: 6dbc5ae729102e37a77735712dc17daef6b46916
The exe also has the same characteristics:
adebeaupre@host032:~/bad$ md5sum jetcodec1000.exe
555a43e71a62453b445087ef50781193 jetcodec1000.exe
adebeaupre@host032:~/bad$ md5sum jetcodec1000.dmg
555a43e71a62453b445087ef50781193 jetcodec1000.dmg
Obviously NOT a DMG file! Interesting that the site the file was downloaded from contained the following advertising blurbs:
XX is a multimedia software that allows access to Windows collection of multimedia drivers and integrates with any application using DirectShow and Microsoft Video for Windows. XX will highly increase quality of video files you play.
XX enhances your music listening experience by improving the sound quality of video files sound, MP3, internet radio, Windows Media and other music files. Renew stereo depth, add 3D surround sound, restore sound clarity, boost your audio levels, and produce deep, rich bass sounds.
Sounds like fun. Delivery via social engineering.
Cheers,
Adrien de Beaupré
Bell Canada


Comments