Turf War
Malware which comes with its own "hosts" file to install in \system32\drivers\etc\hosts is pretty common. Usually, these changes are made with the intention to keep the infected system from updating its virus pattern files and OS patches - eg. by adding an entry that makes "update.microsoft.com" resolve to 127.0.0.1 (localhost), and hence prevents the updater from connecting.
A malware sample that we analyzed earlier today pulled a hosts file from txt<dot>kxwii<dot>com/ad.jpg. The file contains 200 or so domains that are reconfigured to point to 127.0.0.1 ... but, surprisingly, not domains of commercial software. Rather, it looks like a turf war is in progress between malwares, and this particular species tries to null out the connections of the competition.
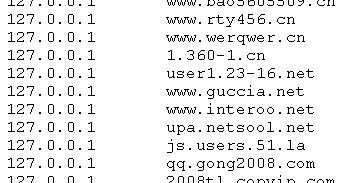
Now if only they could find a way to fight each other directly, without involving us bystanders at all :).
And the Oscar goes to...
ISC reader Gary wrote in to let us know that searching for "oscar presenters" and "oscar winners" with Google brings up a prominently ranked result on a web server in Poland, on a subdomain of "bee<dot>pl", which - surprise, surprise - includes a malicious JavaScript. The end result currently seems to reside on stabilitytraceweb<dot>com, and is yet another incarnation of the "Fake Anti-Virus Program" malware that we have covered repeatedly. Watch out, the EXE has a meager 6/39 on Virustotal.


Comments