Using password cracking as metric/indicator for the organisation's security posture
(Warning, Long)
The strength of passwords used is a good indication of the security posture of an organisation, considering the userid and password combination is in many cases the first and last line of defence. It is quite important to get it right.
Most of us know that when we turn on password complexity in Windows it is no guarantee that the user will select a decent password. After all Passw0rd is an 8 character password that will pass complexity checking in Windows and not many of us would argue that it is a decent password. Another element needs to be in place to get decent passwords, user awareness. When you analyse the passwords you can identify whether reasonable passwords are being used and hence determine whether user awareness training has worked, a refresher is needed or all is good. When cracking passwords you will also be able to determine patterns used by users, admin staff, service accounts, resource accounts, helpdesk etc. All useful information in determining the security posture.
I'll take you through the process that I've been using over the last year or so to examine passwords and get an idea of the security posture or issues within an organisation. Following that I'll take you through some sample outputs and what they show.
Steps
- extract the userids and corresponding password hashes from AD
- split all the different history passwords into separate files and get the total number of users for the files
- for each file run a dictionary crack
- count how many passwords were cracked
- Record the result in a spreadsheet
- For each file run a hybrid attack (dictionary plus numbers)
- count how many passwords were cracked
- Record the result in a spreadsheet
- for each file run a brute force crack for a set amount of time (I use one hour).
- count how many passwords were cracked
- Record the result in a spreadsheet
- Create the graph
- Examine the results
Tools used: fgdump, pwdump, john the ripper, grep, favourite spreadsheet application.
We'll clean out the machine accounts first
grep -v '$' abcomp.pwdump > abc-users- abc-users should now contain only user accounts.
Split each iteration of the password history into different files
grep -i "history_0" abc-users > abc-hist-0- Rinse lather and repeat for each of the histories (typically you will have at least 8, it depends on the site)
For the current password you remove all references to history so use -v
grep -iv "history_" abc-users > abc-hist-c
grep -c ":" abc-hist-?- using the ? will get all the files in one go
- .
/john --format=NT --wordlist=password.lst abc-hist-?(using the ? will process all abc-hist-x files)
--format=NT when I have to compare a number of sites and lanman hashes are unavailable for one or more of these. Using Lanman gives you more obvious results, when using NT hashes the differences are a little bit more subtle between a good and bad site. Another reason to use LanMan is because the whole password needs to be cracked before it will show as a valid guess. For sites where Lanman is disabled the --format=NT option will still give you results. I also use the default password.lst file which is fairly small. If your password is guessed it is truly lame. You can refer to your own words dictionary and tie it into the test. ./john --format=NT --show abc-hist-c
./john --format=NT --wordlist=password.lst --rules abc-hist-?
./john --format=NT --show abc-hist-c
./john --format=NT abc-hist-?
./john --format=NT --show abc-hist-cctrl-c to quit the crack and use ./john --format=NT --show abc-hist-c to display the results. Record these in the column for brute force|
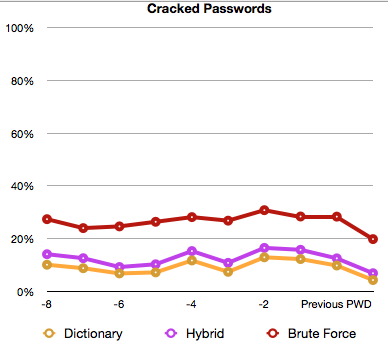
Figure 1 - No password complexity |
Figure 2 - Password complexity, good education initially, but needs a refresher |
When using NT hashes the results will be less obvious than when using lanman hashes but the graphs are still telling. In figure 1 there is no password complexity in place. The dictionary line is above 0%. With the hybrid test it shows in the graph that users are using dictionary words and adding numbers. The brute force password test gets results for over 20% of passwords within one hour again indicating that password selection is not great. There is however a dip at the previous password point, which is when some education was done. The next graph is expected to look more like the first few data points in figure 2.
In figure 2 password complexity is enabled and users are educated. Something started going wrong a few password changes ago which may indicate some awareness training is needed to get the line back to where it started near the 0% line for all three tests.
The test is relatively simple to do, you have all the information above, and it gives a nice graph that can be shown to management (with explanation) showing that your hard work with respect to passwords is paying off. You'll also be able to identify issues with password selection for password resets, service accounts, privileged accounts etc. It provides you with additional information that you can use to help improve the security posture. The above takes about 90 minutes to do from start to finish and can largely be automated.
If you have some nice metrics that you create to measure effectiveness of controls in place in your organisation, let us know. Might be as simple as measuring the number of viruses sent out of an organisation by email (hopefully 0) to measuring the number of attacks dropped by the firewall, etc.
Mark H - Shearwater
.png)


Comments