Malicious Images: What's a QR Code
I just wrote a quick note about the Cisco warranty CD mixup. While writing that, it came to me that currently quite a few of our readers may be visiting Las Vegas for this summers security drink fest. Historically, this has been a time to play various pranks on the audience of these conferences. In the past, fake ATMs, odd wifi networks, weird BGP issues and other tricks were mentioned.
One thing to look out for this year may be QR codes. 25% of internet users are now apparently using mobile devices. Many of them have known vulnerabilities the owner didn't bother to patch yet. At Vegas this week, you may prefer using your mobile device via 3G networks to avoid the notoriously unsafe Wifi networks offered at these conferences.
But there is one problem with mobile devices: The keyboard typically stinks. In particular on cell phones. To help you with that, we have "QR" codes. QR codes are bar codes that encode text and are commonly understood by mobile devices. Take a picture of it, and an app will take you to the encoded URL. Sadly, most people are not all that good in encoding barcode, and have no idea what they are entering. Compare it to handing your phone to a "friend" and telling them to type for you.
These barcodes can link directly to browser exploits, or could include other malicious content to manipulate your phone. If you spot a malicious code, let us know ... most of the applications will tell you what URL they are going to open up before they actually load it (similar to some of the short code URLs).

------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
Cisco shipping malicious warranty CD
Cisco released a somewhat unusual advisory today [1]. instead of talking about a vulnerability in a Cisco product, the advisory warns of a CD shipped by Cisco between December 2010 and August 2011 (= now..).
The CD itself does not include any malware, but documents on the CD, if opened in a browser, may include content from known malicious sites and could have lead to exploitation of the user.
According to Cisco, the site in question is down for some time, and they are not aware of Cisco customers being affected by content from the malicious site. But with all the talk about malicious USB sticks and people focusing counter measures on preventing the use of unauthorized USB sticks, CDs/DVDs certainly should be considered too.
If you are in Vegas this week for Blackhat/Defcosn: Be on the lookup for certified pre-pw0n3d vendor software distributed on USB sticks or CDs. (or QR codes? maybe I should do a diary about that)
[1] http://www.cisco.com/warp/public/707/cisco-sr-20110803-cd.shtml
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
Port 3389 / terminal services scans
Thanks to Pat for pointing out a sharp increase in the number of sources scanning for port 3389 [1].
Port 3389 / TCP is used by Microsoft Terminal Services, and has been a continuing target of attacks. If you have any logs you want to share, please submit them via our contact page . In particular if you observed anything different the last couple days.
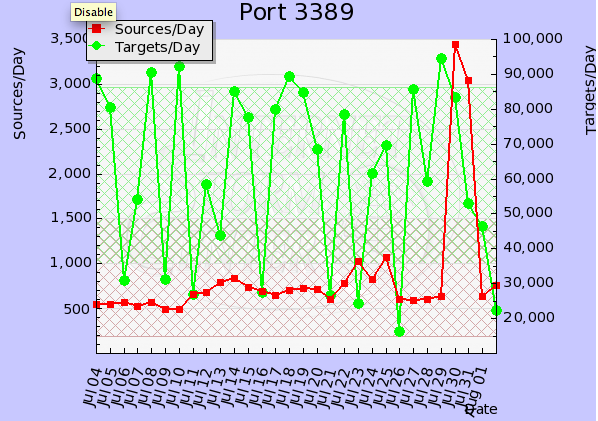
[1] https://isc.sans.edu/port.html?port=3389
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter


Comments