Analysis of drive-by attack sample set
I thought I'd subtitle this diary more humorously as The Twelve Ways of Pwnmas in celebration of June-uary here in the Seattle area, where it really does rain all the time.
I am priviliged to be party to a wide variety of data and telemetry for malfeasance and evil. One source in particular in use at Microsoft is a list of drive-by attack URLs discovered via detection technology utilized by MSRC Engineering.
From this feed I selected twelve (with me here on the theme?) unique URLs detected as drive-by exploit delivery vehicles bountiful in malicious JavaScript. Unfortunately the reporting for the tool is currently limited only to a basic yes or no response regarding a URL's maliciousness. As such I wanted to dig in to learn more about the attributes of these attacks and share them with you here. To do so I used a specifically configured VM and copied the appropriate obfuscated content between <script> tags and ran it through tools such as Malzilla, Burp's decoder, and JSUNPACK. Obfuscation methods included UTF-16 and HEX encoding, amongst others.
Please note: all URLS herein mentioned should be considered hostile and dangerous. Should you choose to explore, please do so at your own risk with the appropriate prophylactic measures. I will post domains here but not full exploit URLs; I'm glad to do so by request. I'm also glad to share samples as requested.
Such a story is better told with pictures, in keeping with the depth of my analysis skills, but first some notes of interest:
- While the likes of the JS/Mult family indicates malicious JavaScript written to exploit multiple vulnerabilities (Adobe, Java, etc.), almost all these exploits universally favor exploiting Internet Explorer vulnerabilities such as CVE-2010-0249, CVE-2010-0806, and CVE-2009-0075. CVE-2010-0249, aka "HTML Object Memory Corruption Vulnerability" was used during Operation Aurora. If you followed Aurora closely back in the day, you'll likely find the country of origin statistics below of no surprise. CVE-2010-0806 was addressed in MS10-018 and and CVE-2009-0075 was addressed in MS09-002 to correct Internet Explorer issues described as unitialized memory corruption vulnerabilities. For what are vulnerabilities where updates were issued as much as three years ago, clearly enough unpatched systems remain to warrant such common exploitation.
- Six of twelve samples exhibit signs of exact code reuse (Exploit:JS/AdoStream), and a seventh is a very slight variant (Exploit:JS/Mult.EA). Additional reference reading for the samples detected: Exploit:JS/AdoStream
The details on the domains of nefariousness are as follows:
| Domain | Analysis Links | VT detections (of 42) |
| www.kasuidojo.com.ar | Exploit:JS/AdoStream | 32 |
| www.ascororadea.ro | Exploit:JS/AdoStream | 32 |
| www.suportemetrocard.com.br | Exploit:JS/AdoStream | 31 |
| pacoaraujodesign.com.br | Exploit:JS/AdoStream | 30 |
| www.czgtgj.com | Exploit:JS/CVE-2010-0806.B | 30 |
| www.stubllanet.com | Exploit:JS/AdoStream | 30 |
| elnido.realtyworldphils.com | Exploit:JS/AdoStream | 29 |
| mj.zhuhai.gd.cn | Exploit:JS/CVE-2010-0806.gen!A | 27 |
| www.meydanoptik.com | Exploit:JS/Mult.EA | 26 |
| voteforomega.info | Exploit:JS/Cripac.A | 13 |
| space.argstorm.com | Exploit:JS/Mult.CR | 9 |
| fedeteniselsalvador.com | Mal/JSBO-Gen | 5 |
Because infographics are all the rage:
These samples also presented a great opportunity to use an ISC Handler favorite. When you suspect code reuse or matching, Jesse Kornblum's ssdeep is an ideal tool with which to validate your assumption. As seen above, I stated that the malicious JS from six of the twelve URLs was identical. Comparing the sample (Exploit:JS/AdoStream) from Germany against the sample from Brazil proved to be a 97% match.
![]()
The Exploit:JS/Mult.EA sample was also noted as a slight variant of Exploit:JS/AdoStream. Using the German sample to compare against the slight variant from Turkey showed a 94% match.
![]()
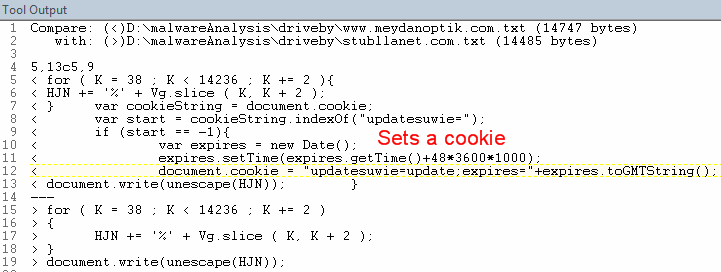
I found it interesting that the very slight difference in JS resulted in four less detections by AV vendors. Here's the VT detection for www.meydanoptik.com sample (Exploit:JS/Mult.EA) versus the VT detection for www.stubllanet.com sample (Exploit:JS/AdoStream).
The diff between the two files as seen below shows only that the www.meydanoptik.com sample sets a cookie while www.stubllanet.com does not.
You get the idea. There are clearly commonalities in vulnerabilities targeted, methods used for exploitation, and even country of origin.
Hopefully you've found this relevant and interesting. Please share any related insight or experience you may have via comments.
Cheers.
Print Bomb? (Take 2)
A week ago we mentioned a "print bomb" malware specimen doing the rounds, with a gradually improving AV detection ratio. However, we are receiving reports (Thanks Conor!) with variants of what looks like the same malware, with a very reduced AV detection ratio (0/37), so do not relax your defenses.
Virus Total: https://www.virustotal.com/file/90910a49226f6488de42d27ac1b347c68a0d5a9c1b070bf5dfdaea8ac368cfc9/analysis/1340227448/.
This new sample, called "xpsp4ress.dll", is stored on C:\Windows\System32 and creates a scheduled task in Windows with what seems to be a random name (e.g. "UUSCPK"), running "C:\WINDOWS\system32\rundll32.exe 'C:\WINDOWS\system32\
Some of the domains that has been identified when the malware phones home (C&C) are:
- hxxp://http://somethingclosely.com
- hxxp://ads.alpha00001.com
- hxxp://storage1.static.itmages.ru
- hxxp://storage5.static.itmages.ru
Look for them in your logs. There is a related write up available from Symantec: http://www.symantec.com/business/support/index?page=content&id=TECH190982.
The beauty of this unexpected malware behavior is that it can easily be detected throughout the organization printers and print servers, although at the expense of wasting precious paper, and trees as a consequence. Let's save the planet! ... and don't forget this is a good opportunity to evaluate the security of your printing architecture (network isolation, access controls, printer management, etc).
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
Cisco Security Advisories 20 JUN 2012
Cisco issued three security advisories today, 20 JUN 2012; two are new, one is an update.
- NEW: Cisco ASA 5500 Series Adaptive Security Appliances and Cisco Catalyst 6500 Series ASA Services Module Denial of Service Vulnerability
Cisco ASA 5500 Series Adaptive Security Appliances (Cisco ASA) and Cisco Catalyst 6500 Series ASA Services Module (Cisco ASASM) contain a vulnerability that may allow an unauthenticated, remote attacker to cause the reload of the affected device.
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20120620-asaipv6 - NEW: Multiple Vulnerabilities in Cisco AnyConnect Secure Mobility Client
The Cisco AnyConnect Secure Mobility Client is affected by the following vulnerabilities:
Cisco AnyConnect Secure Mobility Client VPN Downloader Arbitrary Code Execution Vulnerability
Cisco AnyConnect Secure Mobility Client VPN Downloader Software Downgrade Vulnerability
Cisco AnyConnect Secure Mobility Client and Cisco Secure Desktop HostScan Downloader Software Downgrade Vulnerability
Cisco AnyConnect Secure Mobility Client 64-bit Java VPN Downloader Arbitrary Code Execution Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20120620-ac
- UPDATED: Cisco Application Control Engine Administrator IP Address Overlap Vulnerability
A vulnerability exists in Cisco Application Control Engine (ACE) software. Administrative users may be logged into an unintended context (virtual instance) on the ACE when running in multicontext mode.
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20120620-ace
.png)


Comments