Phishing for Payroll with unpatched Java
Few things are as juicy for the bad guys as getting a key-logger onto the computer of someone who manages payroll. HR/payroll employees tend to have access to personal data of staff and usually have some form of access to a well-stocked bank account that is used to pay the wages. Getting spyware onto such a computer used to be mostly "luck", but it looks like the crooks have stepped up their game, yet again:
For the past couple of weeks, companies that offer outsourced payroll management services have seen their name being abused for phishing scams. One prominent example is ADP, whose website [1] currently alerts their customers to four different samples of phishing emails that make the rounds and claim to be from ADP.
The average recipient of such a phish .. would have no idea who or what ADP is, and would be highly unlikely to "click". But a HR/Payroll employee of a company that actually uses ADP services would certainly be alarmed to read, for example, that his/her access to ADP is about to be cut off:
Hence, the odds are pretty high that someone who clicks on the link in the email is actually a HR/Payroll person. Combine the link with a nice fresh set of exploits that have near-zero detection in anti-virus, and you have a Get-Rich-Quick scheme for the crooks that's hard to beat.
One particular phish that ISC reader Richard sent to us two days ago wasn't all that hard to identify as a phish: The hover-your-mouse-pointer-over-the-link test showed clearly that the link in the Email was not going to ADP:
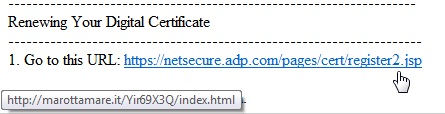
Those who clicked nonetheless, have likely been "had" though. The shown marottamare link redirected via three other web sites, and then ended up on 50.116.36.175, a very temporary home on what looks like a rented Linux VServer. From there, the exploits were delivered, and at least one of them, Java CVE2012-1723, is currently netting the bad guys a lot of illicit system access.
Antivirus detection rate is and stays low, three days later, it is still only at 8/41 on Virustotal. The main reason for this seems to be that the exploit packs are encoded - looking at the decompiled Java source shows functions like this one
which means that the original attack code and payload are split up into five byte blocks, and each of these individual five bytes is encoded by XOR with a different static value. For most anti-virus tools, it seems like all the bad guys need to escape detection again and again is to change the XOR values. Some of the AV tools are getting better at providing generic detection for encoded CVE2012-1723, but don't hold your breath...
As for defenses:
1. PATCH your Java JRE. CVE2012-1723 is deadly, and is widely being exploited in the wild at the moment. Even better, uninstall Java JRE completely from your computers if you can get away with it.
2. Make sure your HR and Payroll folks are treated to another round of "DONT CLICK ON THIS LINK" training. They are your first line of defense, and - given Antivirus' ineffectiveness - usually even your ONLY line of defense.
3. If you have an outsourced payroll provider, acquaint yourself with the email logs, so that you know how REAL email coming from this provider looks like. This knowledge is priceless during an incident, and might even help you to automatically block some of the more egregious phishes.
4. If you have any other tips to keep HR/Payroll staff protected against targeted payroll phishing, please use our contact form, or share in the comments below.
[1] http://www.adp.com/about-us/trust-center/security-alerts.aspx


Comments