CSAM Some more unusual scans
Most of us who regularly look at firewall and other logs get to know the usual targets, 22, 5900, 5060, etc. Most of the time these are fairly obvious and self explanetory. However on occasion you do see some that are a bit more unusual. For example this morning a scan was detected along these lines:
A port scan looking for PPTP VPN connections, not something you see every day. The next step when a connection is made? not sure, if you have any packets or logs you can share relating to this that would be much appreciated.
Another scan picked up was a brute force password guessing attempt with a small change:
Instead of guessing the same userid with many passwords, they are guessing one password with many different userids. Works more often than you would think and also stays below the lockout threshold. We saw this about April-May last year, but it looks like it is still going strong.
Enjoy digging.
Mark
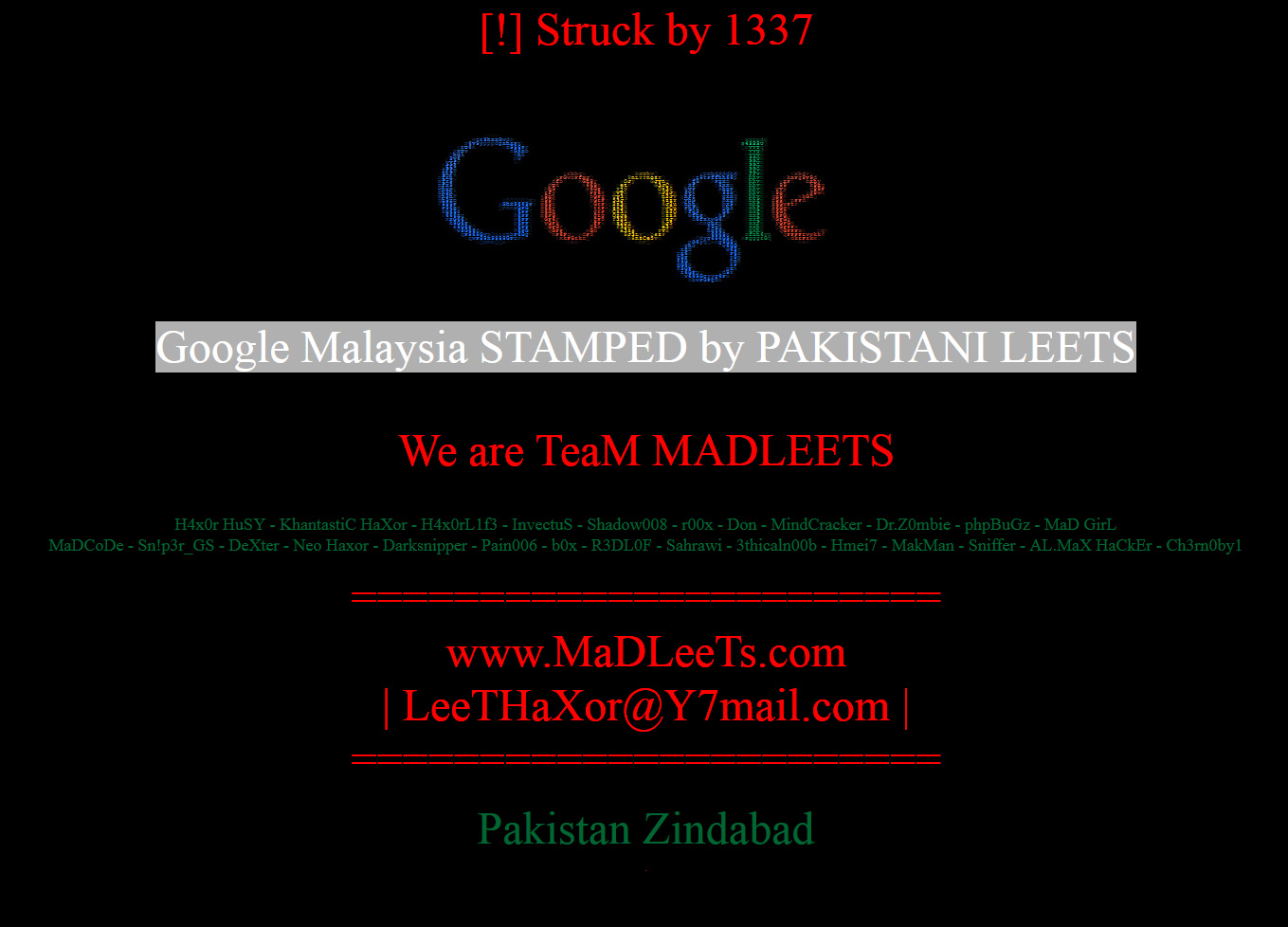
google.com.my DNS hijack
DNS for the Malaysian copy of Google (Google.com.my) got appearanty hijacked. Right now, the hostnames google.com.my and www.google.com.my point to a host in Canada (142.4.211.228).
(thx Alex for capturing the screen shot. My system would not allow me to connect to the IP address anymore). The NS records point to servers that do not appear to be "genuine" as well. Before, the NS records pointed to ns1.google.com and ns2.google.com, which are also authoritative for google.com. Now they point to sdns1.ovh.ca and ks4003824.ip-142-4-211.net .
The whois information does not reflect that this is a google domain, but it didn't change recently and the site used to host a copy of Google's homepage according to archive.org. It is very much possible that Google uses a third party to operate part of its Malaysia site.
Update (via Twitter from @TheBackpackr): " We're the official co managing the domain for google.com.my @GoogleMsia. We are liaising with MYNIC on the DNS change."
The same group behind this attack also claims to have been successful against other Google country level sites (Burundi and Kenia) recently.
If you haven't yet: start monitoring your DNS data! A quick minimum script to do so in 5 minutes (just cron it... )
#!/bin/sh
TLD='edu';
DOMAIN='sans.edu';
ADMIN='your email';
ns=`dig +short NS $TLD | tail -1`
dig NS $DOMAIN @$ns | grep 'IN\tNS' | grep -v '^;' | sort > .$DOMAIN.new
if [ -f .$DOMAIN.old ]; then
if ! cmp -s .$DOMAIN.old .$DOMAIN.new; then
cat .$DOMAIN.new | mail -s "Possible $DOMAIN hijack" $ADMIN
echo possible $DOMAIN hijack
fi
fi
mv .$DOMAIN.new .$DOMAIN.old
(and please change the variable at the top ;-) )
------ Johannes B. Ullrich, Ph.D. SANS Technology Institute Twitter


Comments