NTP reflection attack
Symantec has notice in the last few weeks that there is a significant NTP reflection attacks. NTP is Network time protocol and it’s used to synch the time between client and server, it is a UDP protocol and it’s run on port 123.
In the NTP reflection attack the attacker send a crafted packet which request a large amount of date send to the host.
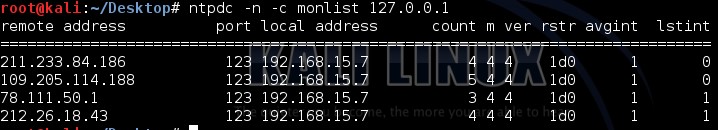
“In this case, the attackers are taking advantage of the monlist command. Monlist is a remote command in older version of NTP that sends the requester a list of the last 600 hosts who have connected to that server. For attackers the monlist query is a great reconnaissance tool. For a localized NTP server it can help to build a network profile. However, as a DDoS tool, it is even better because a small query can redirect megabytes worth of traffic:”
Here is an example of monlist request
|
Ntpdc –n –c monlist 127.0.0.1 |
And here is the output
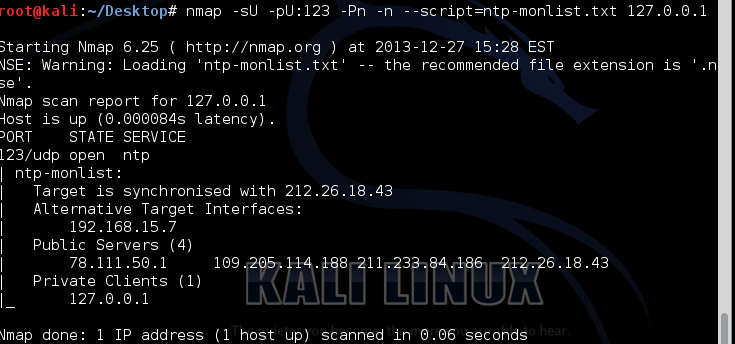
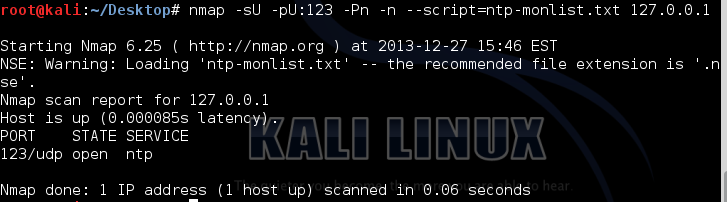
Or you can run a nse script which can be found at https://svn.nmap.org/nmap/scripts/ntp-monlist.nse
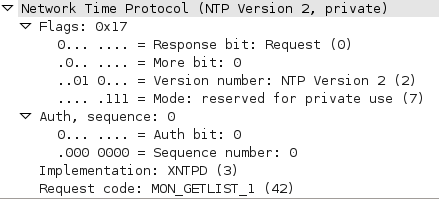
And here is the packet capture of the NMAP script request:
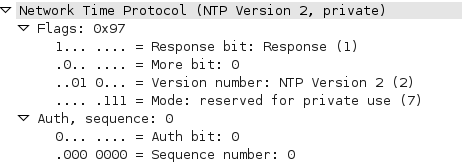
And here is the packet capture of the response:
One way of protecting NTP server from such attack is adding
|
disable monitor |
To /etc/ntp.conf file
And here is the output of the NMAP script after adding this command :
Windows Autorun Part-1
When someone suspecting that a malware activity that may exist in a system or a compromised systemone of the most obvious places to check is the startup locations .In this diary I am going to discuss some of the startup locations in Windows Systems:
1-Startup Folders:
On Windows XP systems:
C:\Documents and Settings\All Users\Start Menu\Programs\Startup
C:\Documents and Settings\%UserName%\Start Menu\Programs\Startup
On Windows Vista/7/8
C:\Users\All Users\Microsoft\Windows\Start Menu\Programs\Startup
C:\Users\%UserName%\Appdata\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
When an executable file (application or batch file) is located in the All Users folder will run for any user when he/she logon, while when it's located in particular user’s folder it will run only for that user when he/she logon.
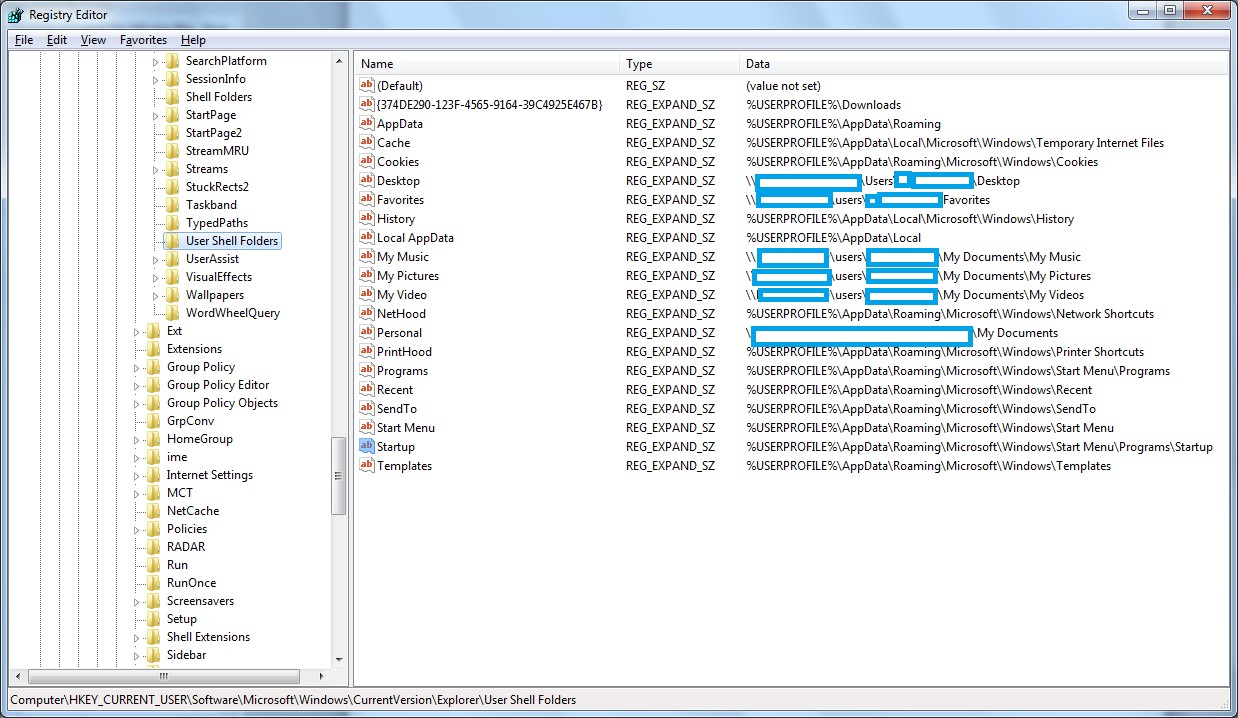
Please note that the above locations are the default and it can be changed, I will suggest first to check the following registry keys:
On Windows XP /Windows Vista/7/8 (See figure 2):
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders


Comments