Happy New Year from the Syrian Electronic Army - Skype‚??s Social Media Accounts Hacked
UPDATE 1500 PDT 01 JAN: Skype Blogs now recovered and reverted to normal. Be sure to add all available protection to your social media accounts and don't use one password to access them all.
The Syrian Electronic Army (SEA) has compromised Skype’s blog and posted anti-NSA and anti-Microsoft messages with such joyful tidbits as "Don’t use Microsoft emails (hotmail,outlook), They are monitoring your accounts and selling the data to the governments."
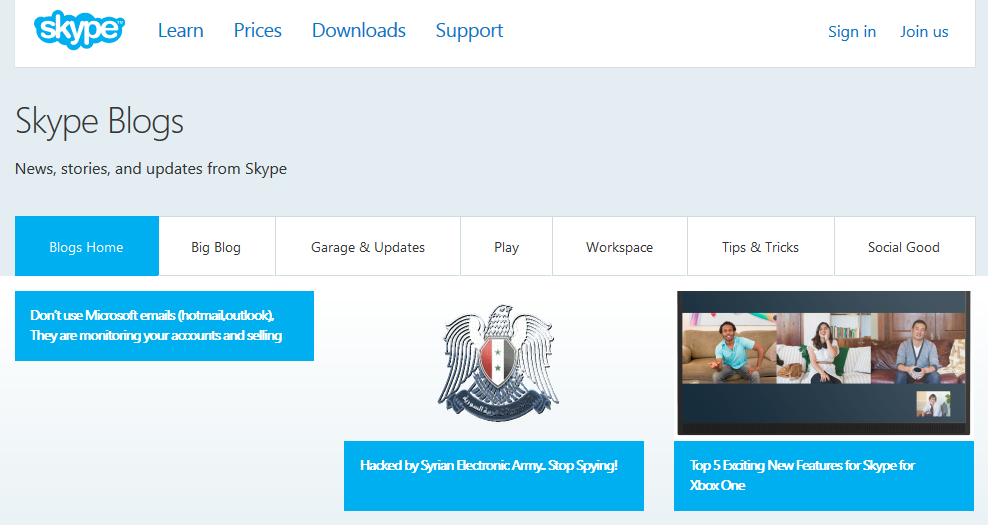
SEA also gained control of Skype’s Facebook and Twitter accounts although messages posted have since been removed.
Follow all the fun on Twitter.
Six degrees of celebration: Juniper, ANT, Shodan, Maltego, Cisco, and Tails
Happy New Year! Hope 2014 is a great year for you.
Ok, so I'm stretching a bit here on the six degrees but its a chance to tie a few interesting pieces of news together for you as we celebrate the new year.
1) As reported earlier by John, Juniper had an issue with its Juniper SSL VPN specifiv to a UAC Host Checker issue.
KB article on the issue: https://kb.juniper.net/TSB16290
Software fix: http://www.juniper.net/support/downloads/?p=esap
2) The latest bit of news regarding the NSA includes the ANT group for the Tailored Access Operations unit. Their tactics revealed in the Der Spiegel article include malware for Juniper and Cisco firewalls such as Jetplow, a "firmware persistence implant" for taking over Cisco PIX and ASA firewalls.
3) The Shodan blog announced a facelift for the Shodan add-on for Maltego and its relaunch on https://maltego.shodan.io.
4) The Shodan add-on for Maltego (Shodan API key required) is really useful for conducting transforms to search Shodan for the likes of Juniper and Cisco firewalls.
As an example, you can conduct a searchShodan transform on the phrase Cisco ASA as seen in Figure 1.
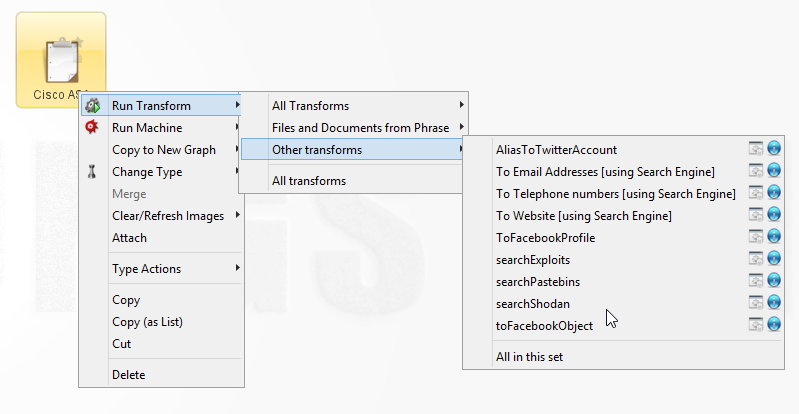
Figure 1
You could then conduct a toShodanHost transform on the results generated by searchShodan, as seen in Figure 2.
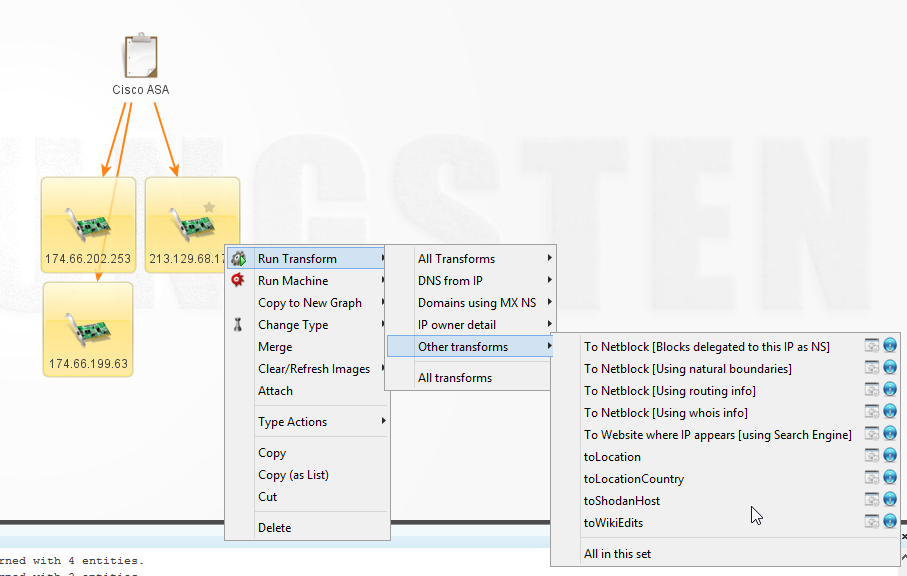
Figure 2
Your results would then likely appear as seen in Figure 3.
.png)
Figure 3
5) Cisco says they're very concerned over the NSA allegations and have posted a reply via Cisco Security Response as well as additional comments from John Stewart.
6) Many readers are also concerned about their privacy as a result of all the NSA disclosures and allegations. To aid in attempting improved privacy, I've posted my latest toolsmith on Tails: The Amnesiac Incognito Live System, privacy for anyone anywhere.
So how all that ties together in six little steps? :-)
With that, good reader, I again bid you and yours a happy new year and best wishes in 2014.


Comments