WordPress brute force attack via wp.getUsersBlogs
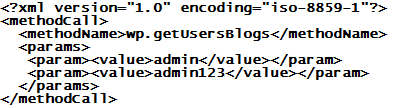
Now that the XMLRPC "pingback" DDoS problem in WordPress is increasingly under control, the crooks now seem to try brute force password guessing attacks via the "wp.getUsersBlogs" method of xmlrpc.php. ISC reader Robert sent in some logs that show a massive distributed (> 3000 source IPs) attempt at guessing passwords on his Wordpress installation. The requests look like the one shown below
and are posted into xmlrpc.php. Unfortunately, the web server responds with a 200-OK in all cases, because the post to xmlrpc.php actually WAS successful. The expected "403 - Not Authorized" error is part of the XML message that the server returns as payload. Hence, to determine what is going on, relying on simple HTTP web server logs is not sufficient. One of the problems with this is that "traditional" means of curbing brute force attacks in WordPress, like using BruteProtect, are less effective, because most of these add-ons tend to watch only wp_login.php and the associated wp_login_failed result, which does not trigger in the case of an xmlrpc login error.
If you are seeing similar attacks, and have found an effective way of thwarting them, please share in the comments below.
App "telemetry"
ISC reader James had just installed "Foxit Reader" on his iPhone, and had answered "NO" to the "In order to help us improve Foxit Mobile PDF, we would like to collect anonymous usage data..." question, when he noticed his phone talking to China anyway. The connected-to site was alog.umeng.com, 211.151.151.7. Umeng is an "application telemetry" and online advertising company. Below is what was sent (some of the ids are masked or have been obfuscated)
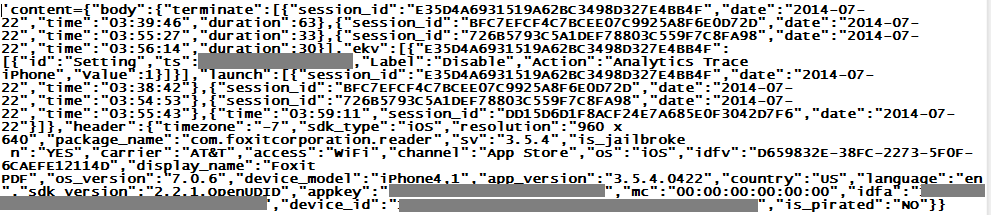
I particularly like the "is_pirated: No". It goes well with "is_snooping: Yes" that is though missing from the exchange...
Ivan's Order of Magnitude
ISC reader Frank reports seeing a couple odd DNS names in his DNS resolver log
4e6.1a4bf.565697d.f52e1.306.60ae.766e0.mdleztmxhvxc.speakan.in. A=193.169.245.133 TTL=30 NS=193.169.245.133
3a.276965.3e6b39.cdaf104.da.e018.72c1a.mdleztmxhvxc.speakan.in. A=193.169.245.133 TTL=30 NS=193.169.245.133
As so often, the first step in the infection chain had been a visit to a benign, but unpatched and hacked Wordpress website. It redirected to an intermediary, which in turn redirected to the domains above. The subsequent http connection with Java exploit attempt was stopped by the proxy filters in Frank's case, so no harm done.
But looking at public passive DNS records, it is obvious that "something" is going on, and has been for a long while. Domain names of this pattern have been observed since about November 2013, and are associated with the Magnitude Exploit Kit. Snort and Emergingthreats have decent signatures, and flag the traffic as "MAGNITUDE EK".
The recently used domain names are all within the Indian TLD ".in", and checking the registration information, they were all registered by the same alleged "Ivan Biloev" from Moscow, and all of them via the same registrar (webiq.in). They even suspended a handful of the domains because of abuse, but they apparently continue to let Ivan happily register new addresses. Maybe a registrar might want to have a chat with a customer who had domains revoked, before letting registrations for additional names go through??
Recent Magnitude mal-domains included, only to name a few: speakan.in busyneeds.in chancessay.in futureroll.in loadsbreak.in suchimages.in touchitems.in waysheader.in putsediting.in regionwhole.in resultsself.in unlikesolve.in advisefailed.in closesthotel.in comesexpands.in installseven.in deducecontact.in poundscaptain.in delayattempted.in lawuniversitys.in obviouslyheads.in
Brad over at malware-traffic-analysis.net has a write-up [1] on a recent sample. If you have current intel on Magnitude EK, the domain name patterns, the exploits pushed in the current set, etc, then please share in the comments below or via our contact form.
[1] http://malware-traffic-analysis.net/2014/07/15/index.html


Comments