Subscribing to the DShield Top 20 on a Palo Alto Networks Firewall
This question has come up a few times in my recent travels and it seemed like something to post for our readers, hope you find it useful, comments welcome!
Overview
This will walk you through the steps of subscribing to our top 20 block list on a Palo Alto Networks firewall. It will also show you how to make a rule using the external block list. You can create a rule to block both inbound and outbound, however in this instruction it will include only an outbound rule. Any traffic transiting outbound from an internal host to this list on the top 20 should be considered suspect, prevented, and then investigated.
Our DShield Top 20 List can always be found here:
http://feeds.dshield.org/block.txt
The source for the parsed and Palo Alto Networks formatted version of the DShield block list can be found here:
http://panwdbl.appspot.com/lists/dshieldbl.txt
The full source of external block lists:
It is my understanding that this ‘unofficial’ source is maintained by a Palo Alto Networks systems engineer, although this is not confirmed.
Creating the External Block List Subscription
1. Goto Objects -> Dynamic Block Lists
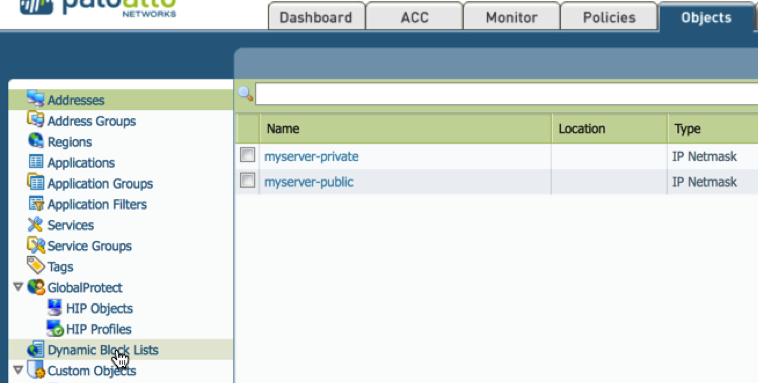
2. Click Add
A. Name the External Block List Subscription (e.g. DShield Recommended Block List.)
B. Copy the preformatted subscription from our unofficial formatting app http://panwdbl.appspot.com/lists/dshieldbl.txt and paste into source block.
C. Click Test Source URL
.png)
You have just subscribed to an External Block List (EBL). Once an hour this subscription will poll the external block source and automatically update the subscription. This does not actually apply the feed to any rules or polices, in the next section we will create an outbound blocking rule looking for Indicators of Compromise.
Creating the Outbound Rule
Overview
There are several ways to use an EBL. One of the most common is to block/restrict on inbound flows, and although this should be done we will be using a different method for this example. In the creating the outbound rule section we will block and alert on outbound traffic from our L3-Trust to L3-Untrust (basically from our trusted internal zone to our untrusted external zone, your naming convention may differ). This will serve as a possible indicator of compromise (IoC).
On the topic of of IoC, let’s be clear that this can only serve as a possible indicator of compromise. Miliage may vary depending on your EBL. The DShield EBL (the EBL selected for this lab) list is hosted by the Internet Storm Center that has been maintained for over a decade. Any communication to those hosts should be consider suspect, however not a clear case for declaration of compromise. Regardless, it should be best current practice (BCP) to at least alert on this traffic outbound. Traffic from these hosts and netblocks inbound are largely considered noise. Any questions regarding the DShield Recommended Block list please direct them to handlers@isc.sans.edu. For a history behind the DShield top 20 check out https://isc.sans.edu/about.html.
WARNING!!!!!!!!!
Step 2.d. critical! If you miss step 2.d. you will shadow all your other rules and stop all traffic outbound in your environment, please pay CLOSE attention to step 2.d, YOU HAVE BEEN WARNED!!!!. Do not miss this step. Also for troubleshooting reasons if all your traffic stops after this walk-though, you can disable the rule and troubleshoot your External Block List.
1. Goto Policies -> Security
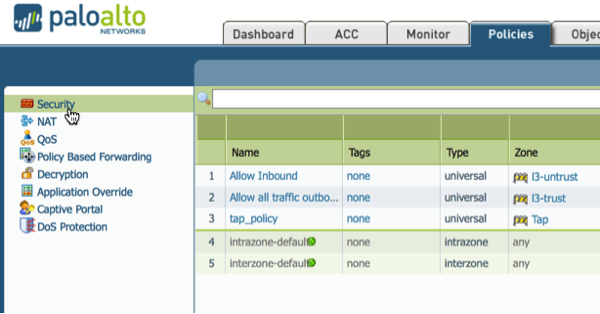
2. Click Add
A. Give the Rule a Name (e.g. EBL DShield Rule)
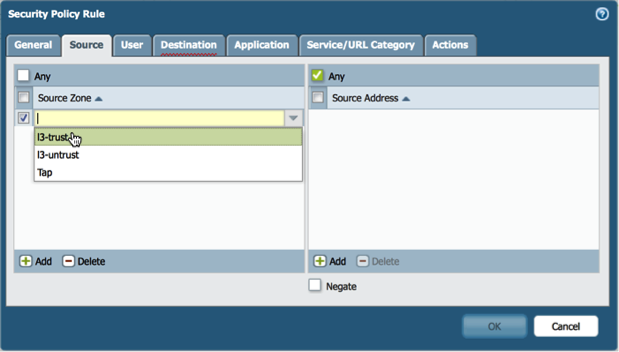
B. Under the source tab select L3-Trust or your trusted internal zone name (remember this is an IoC rule, not just a normal block noise rule).
C. Under the destination tab select L3-Untrust or your untrusted external zone.
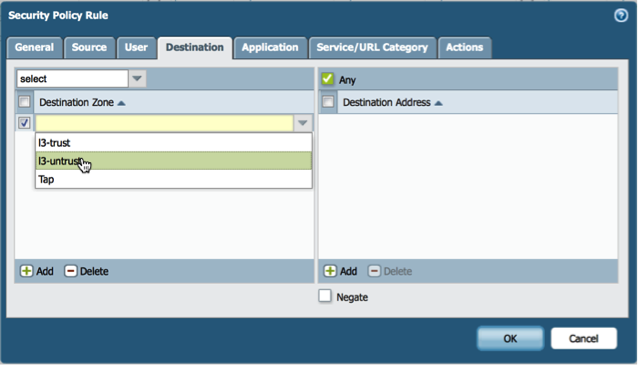
D. Under the destination tab in the destination address select the DShield EBL subscription. (DO NOT MISS THIS STEP!)
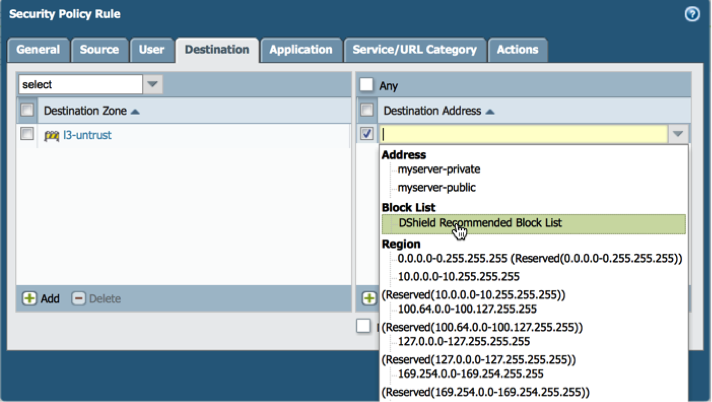
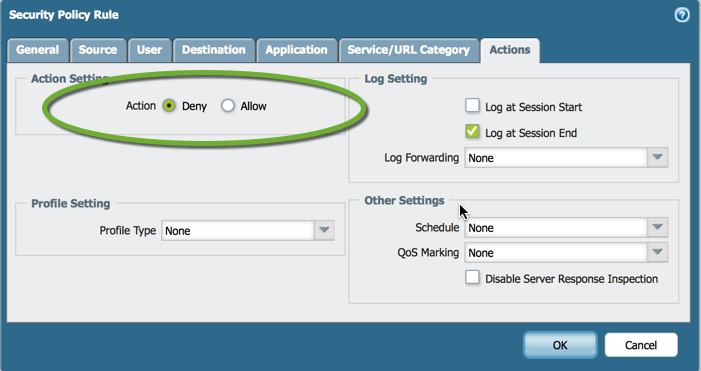
E. Under the actions tab change allow to deny. Optionally you can set logging to an external syslog here as well.
F. Click okay.
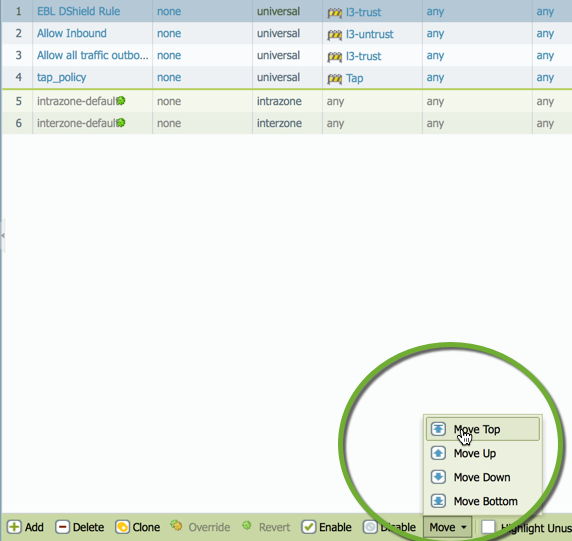
G. Highlight the new rule, click move, which can be found at the bottom of the GUI, and select top. We are moving this rule to the top as we want to catch all attempts to reach the EBL outbound before any other rule is triggered.
H. Commit
NOTE: if you receive warning as indicated in the screenshot check your internet connection as it indicates that the EBL was not reachable. Also, some EBL have maximum polling counts and only allow refresh every so often (e.g. 1 hour). This could have been triggered when you tested the URL connection. These are two reasons why your EBL may not be reachable.
It is also possible to check the EBL on the CLI:
> request system external-list refresh name
Screencast of the Above


Comments