Threatglass has pcap files with exploit kit activity
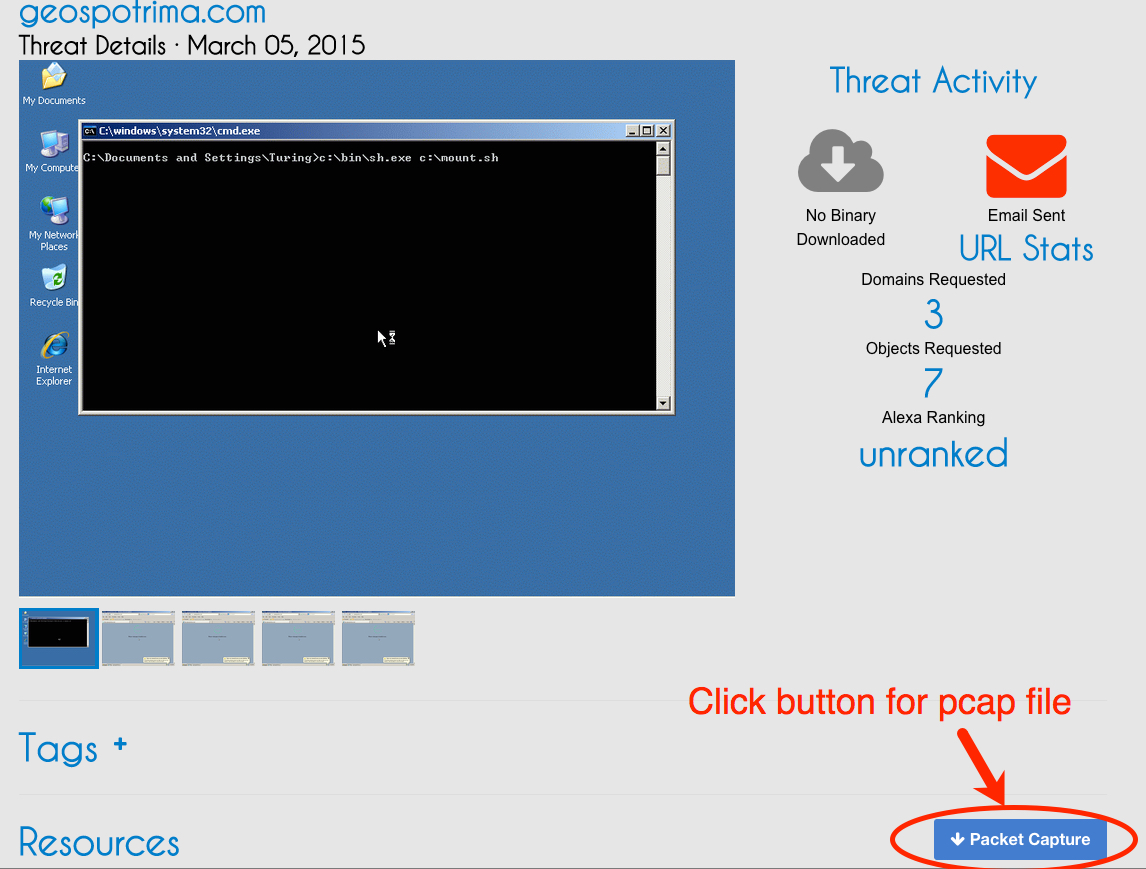
Threatglass is a one way to find up-to-date examples of exploit kit traffic. Not all of it is exploit kit traffic, but all of it represents some sort of malicious activity. Threatglass doesn't explain what type of traffic you're looking at from the pcaps the site provides. Let's look at a page from last week on Thursday, March 5th 2015 [1]. This one is exploit kit activity. In the image below, you'll find a link to the packet capture in the lower right-hand corner of the window:
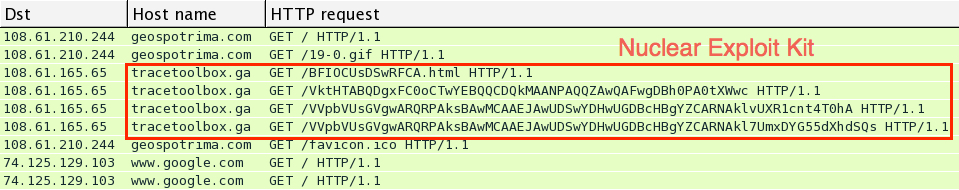
Download the pcap and open it in Wireshark. User http.request as the filter, and make sure you're showing the host name in the column display. We quickly find some unusual traffic, which I know from personal experience is the Nuclear Exploit Kit.
For most exploit kits, the pattern of traffic is: Landing page --> Exploit (Java, Flash, Silverlight, IE, etc) --> Malware payload if the exploit is successful
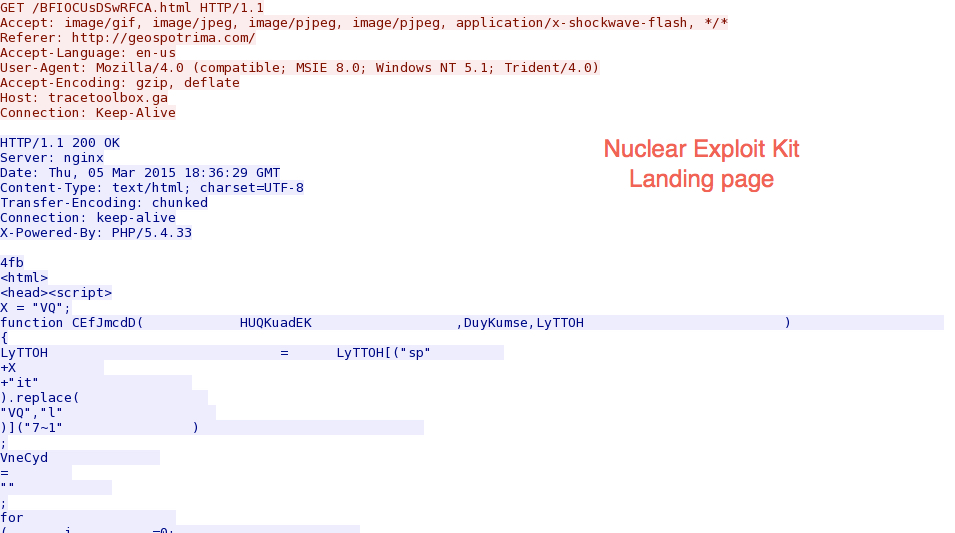
Let's look at this example by following a few TCP streams in the pcap. First, we have the landing page:
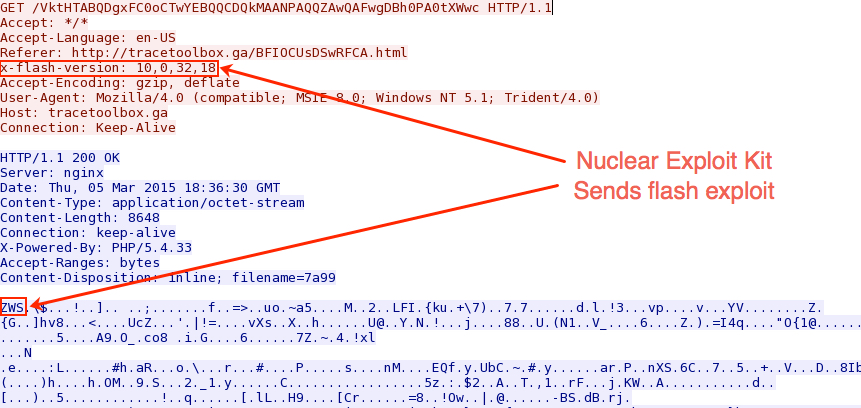
Next, the exploit kit sends a Flash exploit to the victim host:
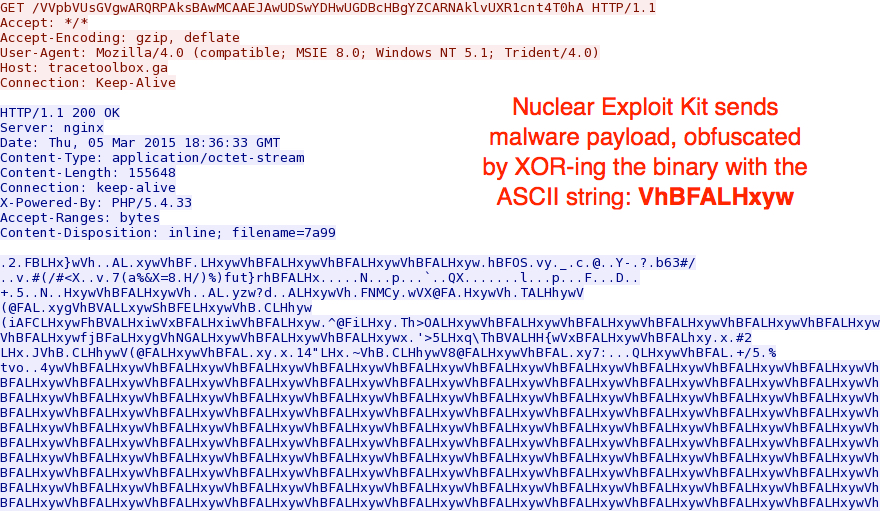
When the Flash exploit works, a malware payload is sent. Currently, Nuclear Exploit Kit obfuscates the malware payload with an ASCII string. In this case, the binary was XOR-ed with the ASCII string: VhBFALHxyw
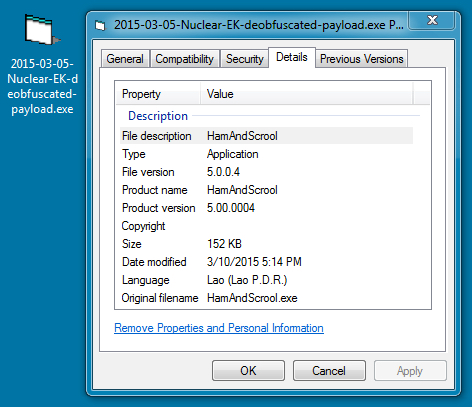
Using a Python script, I was able to XOR the payload with that ASCII string again, and I got the original malicious executable:
The Virus Total results indicate the malware is a Tofsee variant - https://www.virustotal.com/en/file/7659b2be203a34b7491c7101c0275b9e20e8d801d236817a5285c2e63e0ad0e5/analysis/
If you want a sample of the deobfuscated payload, you can get it from malwr.com at: https://malwr.com/analysis/N2U3NDUwMjQ5MWViNGZkNWFlMTBkMjkxMzExZGQxNTM/
If you have the time, review some of the other entries on Threatglass to figure out which ones are exploit kit activity, and which ones are other activity, like fake flash installer pop-up windows. This is one of many resources on line that aspiring analysts can use to build their skills.
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
Microsoft March Patch Tuesday
Overview of the March 2015 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS15-018 | Cumulative Security Update For Internet Explorer (Replaces MS15-009 ) (note that for IE8 and later, the VBScript vulnerability CVE-2015-0032 is addressed by MS15-019) | |||||
| Internet Explorer CVE-2015-0032 CVE-2015-0056 CVE-2015-0072 CVE-2015-0099 CVE-2015-0100 CVE-2015-1622 CVE-2015-1623 CVE-2015-1624 CVE-2015-1625 CVE-2015-1626 CVE-2015-1627 CVE-2015-1634 |
KB 3040297 | CVE-2015-1625 has been disclosed in public, but no exploits seen yet.. | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS15-019 | Remote Code Execution Vulnerability in VBScript Scripting Engine (Replaces MS14-084 ) | |||||
| VBScript CVE-2015-0032 |
KB 3040297 | no known exploits. | Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS15-020 | Remote Code Execution Via Loading Untrusted DLLs and Windows Text Service Memory Corruption (Replaces MS14-027 ) | |||||
| Windows Text Services CVE-2015-0081 CVE-2015-0096 |
KB 3041836 | no known exploits. | Severity:Critical Exploitability: 2 |
Critical | Critical | |
| MS15-021 | Remote Code Execution Vulnerability in Adobe Font Drivers (Replaces MS13-081 ) | |||||
| Adobe Font Drivers CVE-2015-0074 CVE-2015-0087 CVE-2015-0088 CVE-2015-0089 CVE-2015-0090 CVE-2015-0091 CVE-2015-0092 CVE-2015-0093 |
KB 3032323 | no known exploits. | Severity:Critical Exploitability: 2 |
Critical | Important | |
| MS15-022 | Remote Code Execution Vulnerability in Microsoft Office (Replaces MS13-072 MS14-022 MS14-023 MS14-050 MS14-073 MS15-012 ) | |||||
| Microsoft Office CVE-2015-0085 CVE-2015-0086 CVE-2015-0097 CVE-2015-1633 CVE-2015-1636 |
KB 3038999 | no known exploits. | Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS15-023 | Elevation of Privilege Vulnerability in Kernel Mode Drivers (Replaces MS15-010 ) | |||||
| Kernel Mode Drivers CVE-2015-0077 CVE-2015-0078 CVE-2015-0094 CVE-2015-0095 |
KB 3034344 | no known exploits. | Severity:Important Exploitability: 2 |
Important | Important | |
| MS15-024 | Information Disclosure Vulnerability in PNG Processing (Replaces MS15-016 ) | |||||
| Windows CVE-2015-0080 |
KB 3035132 | no known exploits. | Severity:Important Exploitability: 3 |
Important | Important | |
| MS15-025 | Elevation of Privilege / Impersonation Vulnerability in Windows Kernel (Replaces MS13-031 MS15-010 MS15-015 ) | |||||
| Windows Kernel CVE-2015-0073 CVE-2015-0075 |
KB 3038680 | no known exploits. | Severity:Important Exploitability: 2 |
Important | Important | |
| MS15-026 | Cross Site Scripting Vulnerabilities in Microsoft Exchange Server | |||||
| Microsoft Exchange Server CVE-2015-1628 CVE-2015-1629 CVE-2015-1630 CVE-2015-1631 CVE-2015-1632 |
KB 3040856 | no known exploits. | Severity:Important Exploitability: 2 |
Important | Important | |
| MS15-027 | Spoofing Vulnerability in NETLOGON (Replaces MS10-101 ) | |||||
| Windows CVE-2015-0005 |
KB 3002657 | no known exploits. | Severity:Important Exploitability: 2 |
Important | Important | |
| MS15-028 | Access Control List Bypass via Windows Task Scheduler | |||||
| Windows CVE-2015-0084 |
KB 3030377 | no known exploits. | Severity:Important Exploitability: 2 |
Important | Important | |
| MS15-029 | Information Disclosure in Windows Photo Decoder | |||||
| Windows Photo Decoder CVE-2015-0076 |
KB 3035126 | no known exploits. | Severity:Important Exploitability: 2 |
Important | Important | |
| MS15-030 | Denial of Service Vulnerability in RDP (Replaces MS14-030 ) | |||||
| Remote Desktop Protocol CVE-2015-0079 |
KB 3039976 | no known exploits. | Severity:Important Exploitability: 3 |
Important | Important | |
| MS15-031 | Schannel Patch for FREAK | |||||
| Schannel CVE-2015-1637 |
KB 3046049 | yes. | Severity:Important Exploitability: 1 |
Important | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urt practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threatatches.
Apple Patches for iOS, OS X and Apple TV
With yesterday's updates for iOS, OS X and Apple TV, Apple also addressed a number of security vulnerabilities, most notably the "Freak" vulnerability. After updating, the affected operating systems no longer support export quality ciphers. However, Apple browsers continue to support SSLv3 and as a result, continue to be vulnerable to POODLE.
Quick Summary of the security content of Apple's updates:
XCode 6.2: This update addresses 4 vulnerabilities in subversion and 1 in git.
OS X: 5 vulnerabilities. The most serious of which is likely a code execution vulnerability in Keychain.
Apple TV: 3 vulnerabilities. One of which would allow an attacker to write files to the system if the user mounts a corrupt disk image.
iOS: 6 vulnerabilities. In addition to FREAK and the above mentioned Keychain problem, a vulnerability that allows an attacker with physical access to the device to see the home screen on a locked devices is patched.
For details from Apple, see https://support.apple.com/en-us/HT1222


Comments