Angler exploit kit pushing CryptoWall 3.0
Introduction
In the past two days, I've infected two hosts from Angler exploit kit (EK) domains at 216.245.213.0/24. Both hosts were infected with CryptoWall 3.0 ransomware using the same bitcoin address for the ransom payment: 16Z6sidfLrfNoxJNu4qM5zhRttJEUD3XoB
On Tuesday, 2015-05-26 at 15:17 UTC, I infected a host where Angler EK sent Bedep as a malware payload before getting CryptoWall 3.0 [1]. On Wednesday, 2015-05-27 at 17:30 UTC, I infected a host where Angler EK sent CryptoWall 3.0 as the malware payload.
I usually see Angler EK send different types of ransomware [2, 3], and I've seen plenty of CryptoWall 3.0 samples from Magnitude EK; however, this is the first time I've noticed CryptoWall from Angler EK.
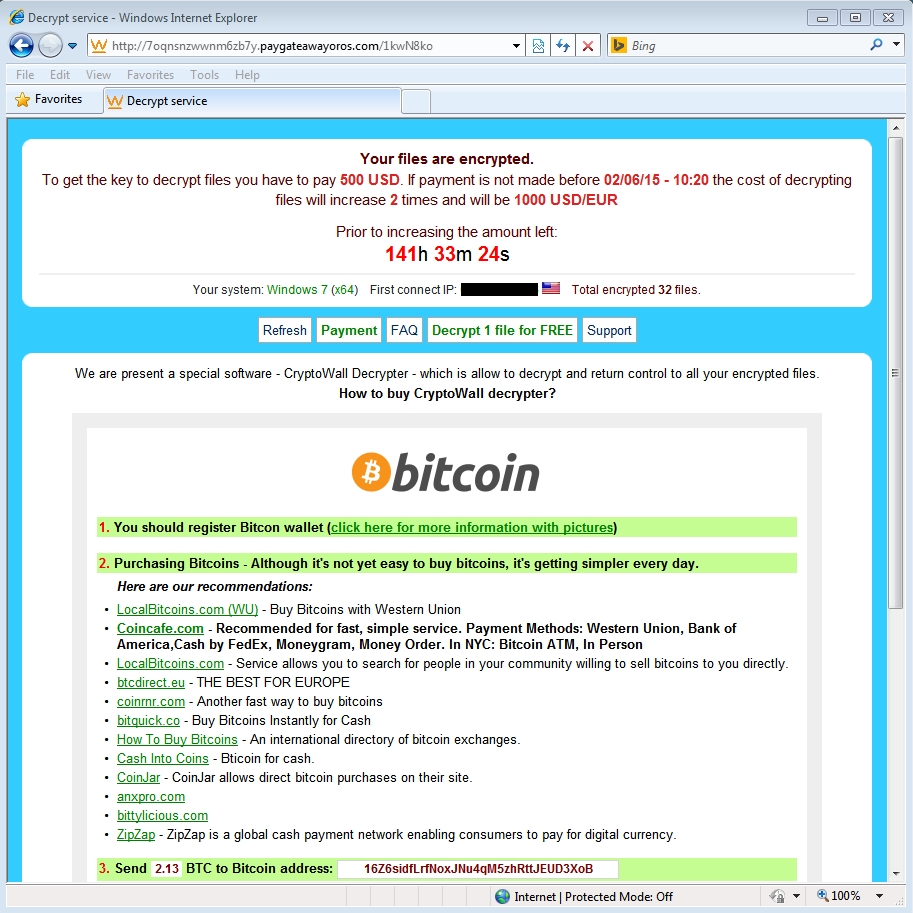
Shown above: CryptWall 3.0 decrypt instructions from the 2015-05-27 sample
Traffic from the infected host
CryptoWall 3.0 traffic has changed a bit from my first diary about it on 2015-01-19 [4]. Traffic below was seen from the infected host on 2015-05-27 starting at 17:30 UTC.
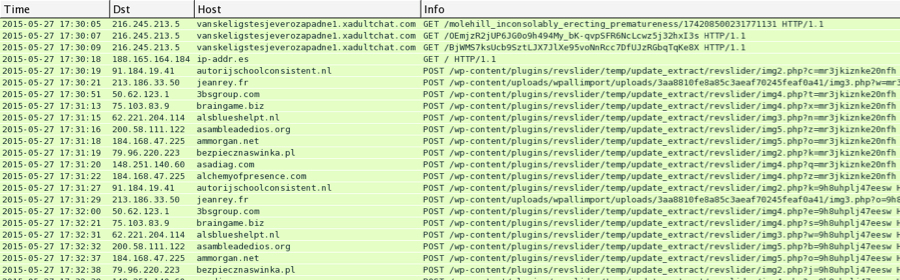
Shown above: Angler EK and CryptWall 3.0 traffic as seen in Wireshark
Associated domains:
- 216.245.213.5 port 80 - vanskeligstesjeverozapadne1.xadultchat.com - Angler EK
- 91.184.19.41 port 80 - autorijschoolconsistent.nl - CryptoWall 3.0 check-in
- 213.186.33.50 port 80 - jeanrey.fr - CryptoWall 3.0 check-in
- 50.62.123.1 port 80 - 3bsgroup.com - CryptoWall 3.0 check-in
- 75.103.83.9 port 80 - braingame.biz - CryptoWall 3.0 check-in
- 62.221.204.114 port 80 - alsblueshelpt.nl - CryptoWall 3.0 check-in
- 184.168.47.225 port 80 - ammorgan.net - CryptoWall 3.0 check-in
- 79.96.220.223 port 80 - bezpiecznaswinka.pl - CryptoWall 3.0 check-in
- 148.251.140.60 port 80 - asadiag.com - CryptoWall 3.0 check-in
- 184.168.47.225 port 80 - alchemyofpresence.com - CryptoWall 3.0 check-in
- 95.163.121.105 port 80 - 7oqnsnzwwnm6zb7y.paygateawayoros.com - CryptoWall decrpyt instructions
- 95.163.121.105 port 80 - 7oqnsnzwwnm6zb7y.paymentgateposa.com - CryptoWall decrpyt instructions
- 7oqnsnzwwnm6zb7y.optionpaymentprak.com (didn't resolve in DNS) - CryptoWall decrpyt instructions
- 7oqnsnzwwnm6zb7y.watchdogpayment.com (didn't resolve in DNS) - CryptoWall decrpyt instructions
Angler EK:
- vanskeligstesjeverozapadne1.xadultchat.com - GET /molehill_inconsolably_erecting_prematureness/174208500231771131
- vanskeligstesjeverozapadne1.xadultchat.com - GET /OEmjzR2jUP6JG0o9h494My_bK-qvpSFR6NcLcwz5j32hxI3s
- vanskeligstesjeverozapadne1.xadultchat.com - GET /BjWMS7ksUcb9SztLJX7JlXe95voNnRcc7DfUJzRGbqTqKe8X
CryptoWall 3.0 check-in traffic:
- ip-addr.es - GET /
- autorijschoolconsistent.nl - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img2.php?c=mr3jkiznke20nfh
- jeanrey.fr - POST /wp-content/uploads/wpallimport/uploads/3aa8810fe8a85c3aeaf70245feaf0a41/img3.php?w=mr3jkiznke20nfh
- 3bsgroup.com - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img4.php?t=mr3jkiznke20nfh
- braingame.biz - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img4.php?x=mr3jkiznke20nfh
- alsblueshelpt.nl - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img3.php?n=mr3jkiznke20nfh
- asambleadedios.org - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img5.php?z=mr3jkiznke20nfh
- ammorgan.net - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img5.php?o=mr3jkiznke20nfh
- bezpiecznaswinka.pl - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img2.php?k=mr3jkiznke20nfh
- asadiag.com - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img4.php?q=mr3jkiznke20nfh
- alchemyofpresence.com - POST /wp-content/plugins/revslider/temp/update_extract/revslider/img4.php?z=mr3jkiznke20nfh
Note: These URLs repeated several times with different random strings at the end.
Traffic caused by viewing the CryptoWall decrypt instructions in a browser:
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /1kwN8ko
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/style.css
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/flags/us.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/flags/it.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/rt.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/flags/fr.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /picture.php?k=1kwn8ko&4d2156f57fb503178f62c2f95690e599
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/rb.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/flags/es.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/flags/de.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/lb.png
- 7oqnsnzwwnm6zb7y.paygateawayoros.com - GET /img/lt.png
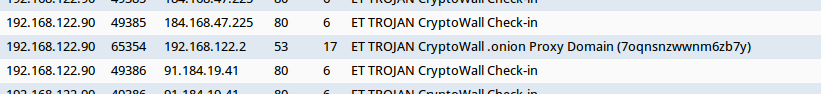
Shown above: Emerging Threats-based Snort events on the infection traffic using Security Onion
Preliminary malware analysis
Malware payload delivered by Angler EK on 2015-05-27:
- File size: 232.5 KB ( 238080 bytes )
- MD5 hash: 30ca927d6e800177937788703fc87301
- Detection ratio: 2 / 57
- First submitted: 2015-05-27 19:15:02 UTC
- https://www.virustotal.com/en/file/086a992a8525d3126a6ac7bb29360739d591c672a8099d4be8faa3fc95651792/analysis/
- https://malwr.com/analysis/NGFmYjBiYmQ0N2M2NGExNDhlOTA0OWMzMDk1ZDg5MzM/
- https://www.hybrid-analysis.com/sample/086a992a8525d3126a6ac7bb29360739d591c672a8099d4be8faa3fc95651792?environmentId=2
Final words
A pcap of the 2015-05-27 infection traffic is available at:
A zip file of the associated malware is available at:
The zip file is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
---
Brad Duncan
ISC Handler and Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://malware-traffic-analysis.net/2015/05/26/index.html
[2] https://isc.sans.edu/diary/Angler+exploit+kit+pushes+new+variant+of+ransomware/19681
[3] http://malware-traffic-analysis.net/2015/03/25/index.html
[4] https://isc.sans.edu/diary/Traffic+Patterns+For+CryptoWall+30/19203


Comments