Kippo and dshield
In this diary I will talk about how to configure kippo honeypot and how to submit your kippo’s log to SANS Dshield .
If you are planning to run your kippo behind router/firewall then you have to set a static IP address for your sensor:
If you are using Debian Linux , you add the following lines to :
/etc/network/interfaces
|
auto eth0 iface eth0 inet static address 10.0.1.10 netmask 255.255.255.0 gateway 10.0.1.1 |
Then you have to configure the DNS settings in the:
/etc/resolv.conf
In my case I will use my router as a DNS server
|
nameserver 10.0.1.1 |
Then we have to change the default ssh port from 22 to something else, to do so you have to modify the
|
vi /etc/ssh/sshd_config |
Then locate
|
# What ports, IPs and protocols we listen for port 22 |
To something similar to this:
|
# What ports, IPs and protocols we listen for port 2222 |
Now install kippo's dependencies:
|
apt-get install python-dev openssl python-openssl python-pyasn1 python-twisted |
Then create a user name for kippo
|
useradd -d /home/kippo -s /bin/bash -m kippo -g sudo |
Now we will install authbind to allow kippo to listen on port 22 (if it’s not already installed)
|
apt-get install authbind |
Then create a new file with touch command:
|
touch /etc/authbind/byport/22 |
Now change the owner to kippo user
|
chown kippo /etc/authbind/byport/22 |
Now change the permissions of the file
|
chmod 755 /etc/authbind/byport/22 |
Now su to kippo user and download and install kippo:
|
svn checkout http://kippo.googlecode.com/svn/trunk/ ./kippo |
Now cd to kippo directory
Copy kippo.cfg.dist to kippo.cfg and change the listening port from 2222 to 22
|
# Port to listen for incoming SSH connections. # # (default: 2222) ssh_port = 2222 |
To
|
# Port to listen for incoming SSH connections. # # (default: 2222) ssh_port = 22 |
The last step in configuring kippo is to modify start.sh to start kippo using authbind
In the start.sh file change the following
|
twistd -y kippo.tac -l log/kippo.log --pidfile kippo.pid |
To
|
authbind --deep twistd -y kippo.tac -l log/kippo.log --pidfile kippo.pid |
If you are planning to expose your honeypot to the internet ,don’t forget to configure port forwarding or dmz at your router/firewall.
Now you can start kippo by typing
|
./start.sh |
All the attempts will be stored in log/kippo.log file
Finally what is the point of having your own Honeypot if you will not share your logs with the community, we have a ready script that can submit your logs to SANS ISC.
You can download the script from the following link
https://isc.sans.edu/clients/kippo/kippodshield.pl
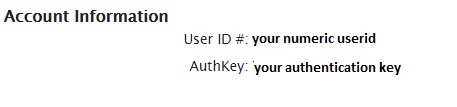
Then on line 33 and line 34 you have to provide your numeric userid and your authentication key, which you can obtain from you SANS ISC portal under my account section
To send you logs type the following
|
perl kippodshield.pl |
You can use crontab to schedule kipposhield.pl to run every day and submit your logs to dshield .



Comments