WiFi Still Remains a Good Attack Vector
WiFi networks are everywhere! When we plan to visit a place or reserve a hotel for our holidays, we always check first if free WiFi is available (be honest, you do!). Once we connected our beloved devices to an external wireless network, they will keep trying to connect to it forever or until you clean the list of known networks. As a small test, I checked on a friend’s computer and I found 87 saved wireless networks:
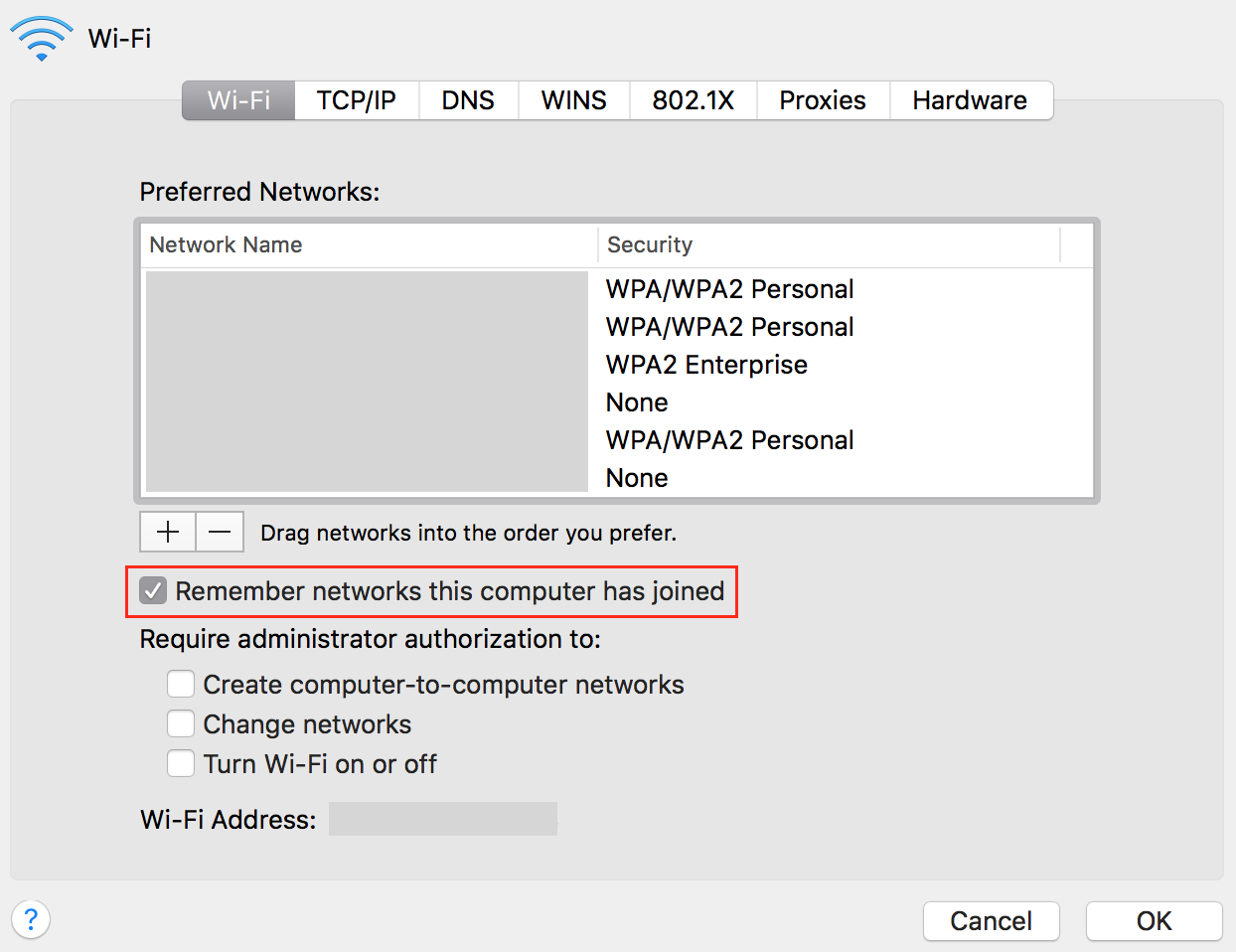
You can see that the default behaviour is to remember all the networks. Your devices may not only connect to dangerous networks but also disclose interesting information about yourself. A long time ago, I wrote a script to collect SSID's broadcasted from wireless devices present in the neighbourhood[1]. The amount of details you can learn about people close to you is just crazy: where they work, where they went on holidays, if they go to the hospital, etc...
October is the month of security awareness and it's good to remind you why unknown wireless networks remain dangerous. Last week, I made a demo during a corporate event about the cyber security landscape and was authorized to deploy a rogue wireless access point for security awareness purposes. The setup was simple:
- A Pineapple[2]
- One laptop running Dofler[2]
Dofler is a "dashboard of fail" or a "wall of sheep” used, mainly in security conference (I'm using it at BruCON) to raise the attendees' security awareness. Its main feature is to extract on the fly pictures from the web traffic generated by the user:
.png)
As you can imagine, many people felt into the trap and their smartphone connected to my rogue AP. An interesting finding: a smart watch connected to the honeypot but the paired smartphone had wireless disabled! The demo was not too invasive, no SSL MitM was performed and I collected only some pictures live from the network flows. No impact for the users, except maybe for the one who was discovered playing Minecraft during the presentations.
However, things may go wrong and more evil actions may be performed against the victims. Yesterday, we received a message from one of our readers, Siddhu Yetheendra[4], who implemented the same kind of attack as the one implemented by Mubix[5] a few weeks ago. Based on USB-sized computer devices, he found a way to steal user's credentials from a locked Windows computer. The principle remains the same but via a rogue wireless access point, the responder[6] tool is poisoning the network and collect credentials hashes (NTLM responses). If many computers are vulnerable to this attack, they are hopefully limitations. The victim computer:
- must be a corporate device joined to a Windows domain
- must be running Windows 7+
- must have the option 'Connect automatically' enabled
Note that the vulnerability has been fixed by Microsoft (MS16-112[7]).
Basically, only "open" networks will work because computers will always try to reconnect to "known" networks transparently. Corporate wireless networks are not affected. But the risk comes, as always, from the end user. How to prevent him/her connecting to the local Starbucks network while drinking his/her morning coffee?
To mitigate this attack, the classic advices are: Patch your systems (MS16-112 has been released in September), do not use the "connect automatically' feature and do not use wireless networks in public areas. Stay safe!
[1] https://blog.rootshell.be/2012/01/12/show-me-your-ssids-ill-tell-who-you-are/
[2] https://www.wifipineapple.com/
[3] https://github.com/SteveMcGrath/DoFler
[4] https://zone13.io/post/Snagging-credentials-over-WiFi-Part1/
[5] https://room362.com/post/2016/snagging-creds-from-locked-machines/
[6] https://github.com/SpiderLabs/Responder
[7] https://technet.microsoft.com/en-us/library/security/ms16-112.aspx?f=255&MSPPError=-2147217396
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
Microsoft and Adobe Patch Tuesday, October 2016
Microsoft published nine bulletins plus one bulletin affecting Adobe Flash. These bulletins fix 43 vulnerabilities in Microsoft software, and 11 in Flash.
Several of the bulletins address vulnerabilities that are already exploited in the wild. Most of these vulnerabilities are information disclosure vulnerabilities. One of them, CVE-2016-3393 is a remote code execution vulnerability which is why I labeled it as "Patch Now".
For more details, see how summary here:
https://isc.sans.edu/mspatchdays.html?viewday=2016-10-11
or our API for automatic processing of the data.


Comments