Seamless Campaign using Rig Exploit Kit to send Ramnit Trojan
Introduction
On Wednesday 2017-05-10, @thlnk3r tweeted about Rig exploit kit (EK) activity. @DynamicAnalysis has already posted an analysis of this traffic on malwarebreakdown.com (always a good read), but I've also looked into it. Today's diary documents my investigation.
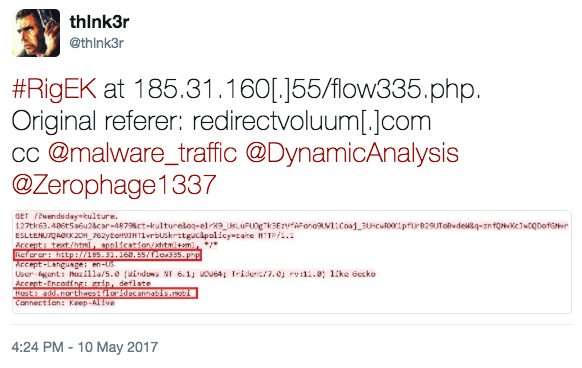
Shown above: Tweet about this Rig EK activity from @thlnk3r (link).
Details
This is not one of the campaigns that use Rig EK like pseudoDarkleech or EITest (both of which I haven't seen since April 2017). This traffic has different characteristics. Cisco is calling it the Seamless Campaign due to an associated iframe attribute back when it was first discovered.
By the time I investigated this traffic, the compromised site that kicked off the chain of events was already off-line. Fortunately, I was able to generate Rig EK by going directly to the Seamless gate URL at 185.31.160.55/flow335.php.
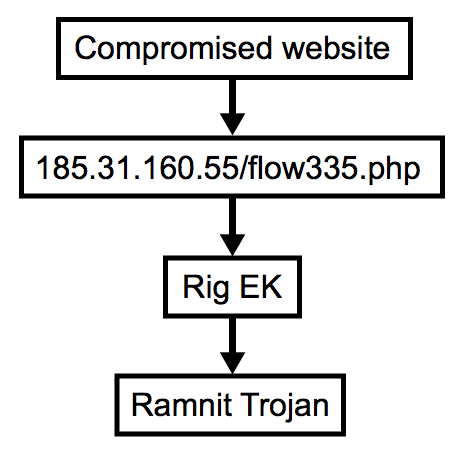
Shown above: Flow chart for this infection traffic.
The Seamless gate led to Rig EK, and network traffic showed indicators of a Ramnit infection after Rig EK.
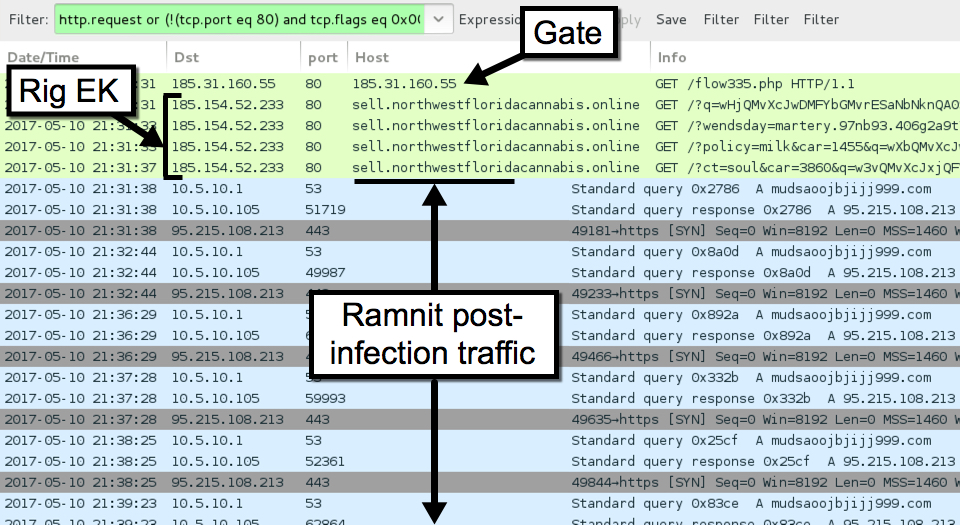
Shown above: Traffic from the infection filtered in Wireshark.
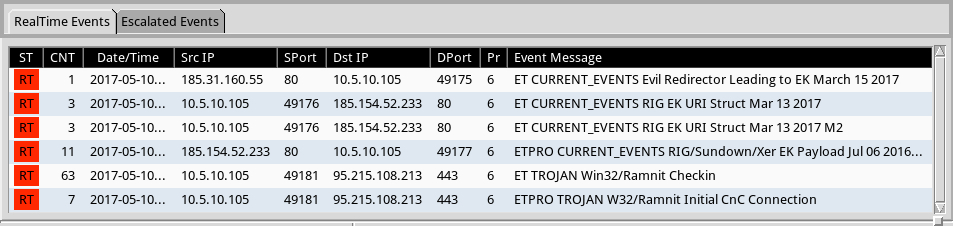
Shown above: Alerts from Sguil on Security Onion using Suricata and the ETPRO ruleset.
Shown above: Some Ramnit alerts after reading the pcap with Snort using the Snort Subscription ruleset.
Indicators of Compromise (IOCs)
The following IP addresses and domains are associated with this traffic:
- 185.31.160.55 port 80 - 185.31.160.55 - GET /flow335.php [Seamless gate]
- 185.154.52.233 port 80 - sell.northwestfloridacannabis.online - Rig EK (1st run)
- 185.154.52.233 port 80 - top.northwestfloridacannabis.org - Rig EK (2nd run)
- 95.215.108.213 port 443 - mudsaoojbjijj999.com - Post-infection encoded/encrypted traffic
- Note: The infected Windows host also tried several attempts at contacting google.com.
The following files are associated with this traffic:
- SHA256 hash: 0b993d0f76a4811a88d57138a8d7a22da15160d89724a9fa9ad34460629985a4
- File size: 16,496 bytes
- File description: Rig EK Flash exploit on 2017-05-10
- SHA256 hash: 4ecb1303c16c0fd5aa44e7dfbdd45efc194e80364facd802768b1581e78fe3fa
- File size: 231,424 bytes
- File description: Rig EK payload - Ramnit (1st run on 2017-05-10)
- SHA256 hash: b868974d3886b79ea164ac2b70941782d3baf183cac0157cc14f07a86cc7327c
- File size: 231,424 bytes
- File description: Rig EK payload - Ramnit (2nd run on 2017-05-10)
- SHA256 hash: 5616c57686191e6c65808ffe8a436e8d1476b1f6c0765efdb887498b86d4d446
- File size: 114,688 bytes
- File location: C:\Users\[username]\AppData\Local\[random letters]\[random letters].exe
- File description: Post-infection malware retrieved from the infected host.
Final words
Rig EK is still an ongoing factor in our current threat landscape. Thanks to everyone on Twitter who tweets about EK activity. Without help from the community, this traffic is difficult to obtain.
As always, if you follow best security practices (keep your Windows computer up-to-date and patched, etc.), your risk of infection is minimal. Unfortunately, many people don't follow best practices. Until this situation changes, EKs will likely remain a profitable method for criminals distributing malware.
Emails, malware samples, and pcaps associated with the 2017-05-10 Rig EK traffic can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments