PE files and debug info
Windows executables (PE files) can contain debug information, like the absolute pathname of the PDB file. A PDB file (Program DataBase) contains debug information and is produced by the linker.
This PDB pathname can be used as an IOC. Parts of the PDB pathname can be used as IOCs too. For example, if the project is stored in the user profile, the path will contain the username. I've successfully used this to track malware created by actors.
Extracting the PDB pathname can be as simple as grepping for string .pdb:
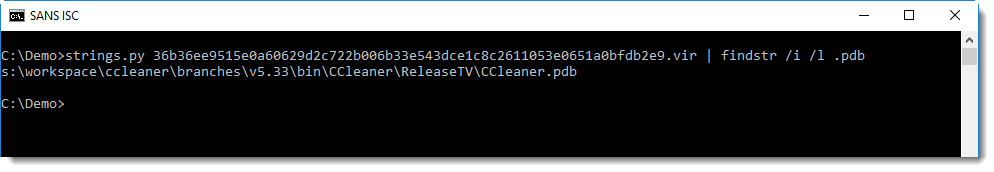
You can also open the PE file in a hex editor, and search for RSDS:
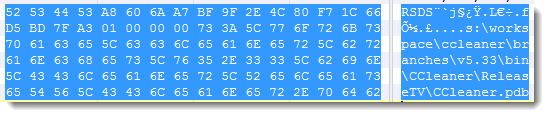
PE file parsers like pecheck.py can extract and parse this codeview information:
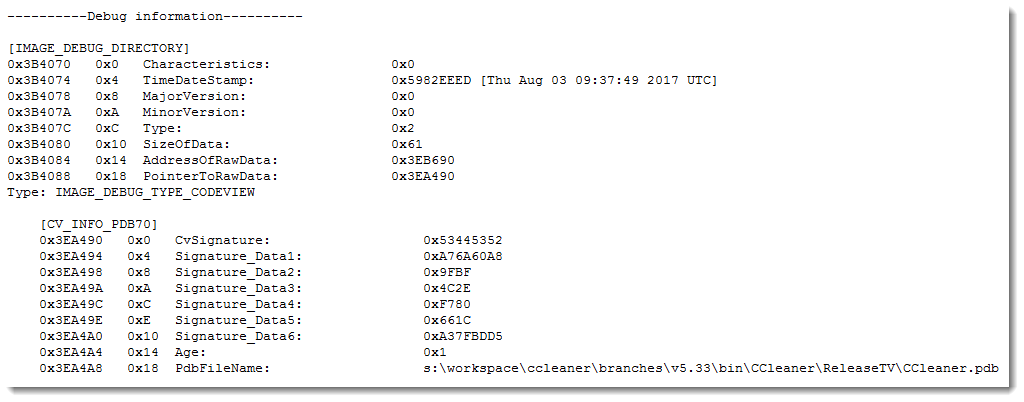
The structure starts with signature RSDS (0x53445352), is followed by a GUID (16 bytes), a counter (4 bytes) and then the PDB pathname.
This unique GUID can be found in the PDB file too, and creates a unique link between the PE file and the PDB file.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Critical Patch For Oracle's Identity Manager
On Friday, Oracle released a critical patch for it's Identity Manager, which is part of Fusion Middleware. The vulnerability patched with this update does affect all current versions of the product, and has a CVSS score of 10. The patch comes just about two weeks after Oracle's regular Critical Patch Update (CPU).
According to Oracle's summary, the patch secures a default account that can be used to log in via HTTP to take over the system. Once these default credentials become known, exploitation should be trivial.
For details, see Oracle's announcement here:
http://www.oracle.com/technetwork/security-advisory/alert-cve-2017-10151-4016513.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|


Comments