I'm All Up in Your Blockchain, Pilfering Your Wallets
With the latest “gold rush” in cryptocurrency, many people are investing (or speculating, depending on your perspective) in Bitcoin and various other currencies. Many of these people are not the same tech-savvy people who have been mining for years, they are chasing big rates of returns. While the economic risks are its own discussion, this post will talk about some observations in how to protect the security of your cryptocurrency.
For the most part, an individual’s cryptocurrency is controlled by their wallet (or wallets) which are the recipient and holder of the “coins”. Much like your physical wallet, if that wallet gets taken, most bets are off in terms of your data being taken. Unlike your physical wallet, there is no external way to know your cryptocurrency wallet has been taken. It’s a file, and files can be duplicated and copied.
This happens organically a wide variety of ways, even security tools will copy and sandbox files it may see on the endpoint. If the wallet is not encrypted and the sandbox allows for open downloads, that allows for situations where entrepreneurial researchers to search for wallet files and use them to appropriate your assets. For example, see the wallet below, which had about $18M USD worth of bitcoin, that was seen freely available for download (no I didn’t take their bitcoins).
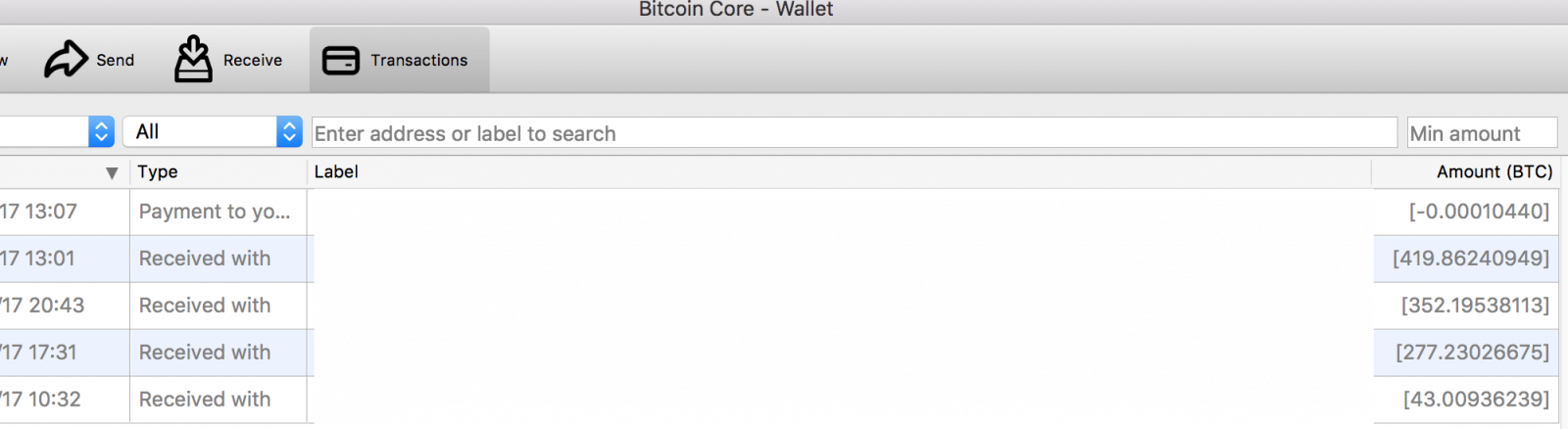
The key against this is to encrypt the wallet, but for a wallet this size, to keep most of the assets in a “cold wallet” stored offline (i.e. USB key in a safe), and to minimize any security tools or Microsoft Windows from sending telemetry of the machine. As a note, many wallets are encrypted with laughably weak passwords… strong passwords are a must here. Here are some more tips from Bitcoin.org in protecting your wallet.
Many less tech-savvy users rely on various web-wallets, where a vendor controls the actual wallet file. If you are working with a reputable vendor, you are probably ok, but exchanges can and do get hacked (Mt. Gox for one), such as this recent story about YouBit from S. Korea filing for bankruptcy after having lost 4,000 bitcoin. There isn’t much a consumer can do about these kinds of threats because the market is unregulated. If there is a large pool of assets, storing that across multiple vendors can give some degree of risk mitigation.
While people are looking at the upside (well not at this moment, as BTC is down), there are risks that are unique and in an unregulated market, it all falls on the user to protect themselves.
--
John Bambenek
bambenek \at\ gmail /dot/ com
Fidelis Cybersecurity



Comments