Are you watching for brute force attacks on IPv6?
For a number of years, I've had a personal blog that for the last 2 or 3 years has been pretty much dormant. A few years ago, I found a deal for a VPS instance for $5/month and decided to host my blog there using WordPress. One of the nice feature of this particular VPS setup is that it has good IPv6 connectivity, so I registered the IPv6 address in DNS. I use fail2ban to protect ssh against brute forcing, but I wanted to also protect my WordPress site, so I configured it to log all authentication attempts so that I could have fail2ban watch that log. For much of the last year, I've noticed something really odd. The vast majority of attempts against my WordPress site have come over IPv6. Here is a typical summary from the log (thank you logwatch, note, the IPs have NOT been changed to protect the guilty).
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2001:41d0:2:3ca::: 3 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2403:cb00:cb02:101:100:211:51:0: 1 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f128:22:4121:312:18:412:2500: 1 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:5:100b::7b:929a: 2 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:5:100f::76c:545a: 1 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:5:104b::fc5:7e49: 2 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:5:110b::6c5:436f: 1 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:5:115b::40e:3c25: 3 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:5:115b::b4d:cc90: 5 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:5:6000::36d:2f48: 1 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2607:f298:6:a066::c55:8af1: 3 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 2a03:6f00:1::5c35:72f5: 2 Time(s)
wordpress(<redacted>): XML-RPC authentication attempt for unknown user jim from 64.13.192.15: 1 Time(s)
We've talked for years about IPv6 and it is a growing percentage of the traffic on the internet, but we haven't really heard about many attacks over IPv6. Clearly, many of the attacks that occur over IPv4 can happen over IPv6 once the bad guys determine that it is worth the effort. Apparently, there are some folks out there who have decided that attacking WordPress is worth the effort. I don't know what kind of ROI (return on investment) they are getting out of it yet, but attacks over IPv6 are only going to increase as we move forward, so we'd better be building up our monitoring and defenses to meet the challenge.
What do you think? Are you monitoring IPv6 to the same extent as IPv4? Are you seeing attacks over IPv6? If so, what? Let us know in the comments or via our contact page.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
Join me to learn about Malware Analysis
Upcoming Courses Taught By Jim Clausing
Microsoft January 2018 Patch Tuesday
Microsoft, as expected included last weeks Meltdown/Spectre update in this months patch Tuesday. But note that in addition to these two flaws, we have a number of other "traditional" privilege escalation and even remote code execution flaws that are probably easier to exploit and should be treated probably with a higher priority. Regardless, I doubt that as many people will work overtime for these run of the mill flaws. For example:
CVE-2018-0788: A quick NVD search shows 15 different vulnerabilities for this Atmfd.dll. Some can even lead to code execution. But I doubt you will have this issue patched this week. Exploitation of CVE-2018-0788 can lead to code execution as administrator. Spectre/Meltdown only allow reading data.
CVE-2018-0773: An attacker may execute arbitrary code in the context of the user running the browser. Spectre, which was patched in many browser again only allows reading data.
and CVE-2018-0802, which is already being exploited.
So better get patching. It worked so well last month :)
January 2018 Security Updates
| Description | |||||
|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity |
| .NET Security Feature Bypass Vulnerability | |||||
| CVE-2018-0786 | No | No | Less Likely | Less Likely | Important |
| .NET and .NET Core Denial Of Service Vulnerability | |||||
| CVE-2018-0764 | No | No | Unlikely | Unlikely | Important |
| ASP.NET Core Cross Site Request Forgery Vulnerabilty | |||||
| CVE-2018-0785 | No | No | Unlikely | Unlikely | Moderate |
| ASP.NET Core Elevation Of Privilege Vulnerability | |||||
| CVE-2018-0784 | No | No | Less Likely | Less Likely | Important |
| Guidance to mitigate speculative execution side-channel vulnerabilities | |||||
| ADV180002 | No | No | Less Likely | Less Likely | Important |
| January 2018 Adobe Flash Security Update | |||||
| ADV180001 | No | No | - | - | Critical |
| Microsoft Access Tampering Vulnerability | |||||
| CVE-2018-0799 | No | No | Unlikely | Unlikely | Important |
| Microsoft Color Management Information Disclosure Vulnerability | |||||
| CVE-2018-0741 | No | No | - | - | Important |
| Microsoft Edge Elevation of Privilege Vulnerability | |||||
| CVE-2018-0803 | No | No | - | - | Important |
| Microsoft Edge Information Disclosure Vulnerability | |||||
| CVE-2018-0766 | No | No | Unlikely | Unlikely | Important |
| Microsoft Excel Remote Code Execution Vulnerability | |||||
| CVE-2018-0796 | No | No | Less Likely | Less Likely | Important |
| Microsoft Office Defense in Depth Update | |||||
| ADV180003 | No | No | - | - | None |
| Microsoft Office Memory Corruption Vulnerability | |||||
| CVE-2018-0802 | No | Yes | Unlikely | Unlikely | Important |
| CVE-2018-0798 | No | No | Less Likely | Less Likely | Important |
| Microsoft Office Remote Code Execution Vulnerability | |||||
| CVE-2018-0795 | No | No | - | - | Important |
| Microsoft Office Remote Code Execution Vulnerability | |||||
| CVE-2018-0801 | No | No | Less Likely | Less Likely | Important |
| Microsoft Outlook Remote Code Execution Vulnerability | |||||
| CVE-2018-0791 | No | No | Less Likely | Less Likely | Important |
| CVE-2018-0793 | No | No | More Likely | More Likely | Important |
| Microsoft SharePoint Cross Site Scripting Elevation of Privilege Vulnerability | |||||
| CVE-2018-0790 | No | No | Less Likely | Less Likely | Important |
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||
| CVE-2018-0789 | No | No | Less Likely | Less Likely | Important |
| Microsoft Word Memory Corruption Vulnerability | |||||
| CVE-2018-0812 | No | No | Unlikely | Unlikely | Important |
| CVE-2018-0797 | No | No | Less Likely | Less Likely | Critical |
| Microsoft Word Remote Code Execution Vulnerability | |||||
| CVE-2018-0805 | No | No | Unlikely | Unlikely | Important |
| CVE-2018-0806 | No | No | Unlikely | Unlikely | Important |
| CVE-2018-0807 | No | No | Unlikely | Unlikely | Important |
| Microsoft Word Remote Code Execution Vulnerability | |||||
| CVE-2018-0804 | No | No | Unlikely | Unlikely | Low |
| CVE-2018-0792 | No | No | Less Likely | Less Likely | Important |
| CVE-2018-0794 | No | No | More Likely | More Likely | Important |
| OpenType Font Driver Elevation of Privilege Vulnerability | |||||
| CVE-2018-0788 | No | No | More Likely | More Likely | Important |
| OpenType Font Driver Information Disclosure Vulnerability | |||||
| CVE-2018-0754 | No | No | More Likely | More Likely | Important |
| SMB Server Elevation of Privilege Vulnerability | |||||
| CVE-2018-0749 | No | No | Less Likely | Less Likely | Important |
| Scripting Engine Information Disclosure Vulnerability | |||||
| CVE-2018-0800 | No | No | Less Likely | Less Likely | Critical |
| CVE-2018-0767 | No | No | Unlikely | Unlikely | Critical |
| CVE-2018-0780 | No | No | - | - | Critical |
| Scripting Engine Memory Corruption Vulnerability | |||||
| CVE-2018-0773 | No | No | - | - | Critical |
| CVE-2018-0774 | No | No | - | - | Critical |
| CVE-2018-0781 | No | No | Unlikely | Unlikely | Critical |
| CVE-2018-0758 | No | No | - | - | Critical |
| CVE-2018-0762 | No | No | More Likely | More Likely | Critical |
| CVE-2018-0768 | No | No | Less Likely | Less Likely | Important |
| CVE-2018-0769 | No | No | - | - | Critical |
| CVE-2018-0770 | No | No | - | - | Critical |
| CVE-2018-0772 | No | No | - | - | Critical |
| CVE-2018-0775 | No | No | - | - | Critical |
| CVE-2018-0776 | No | No | - | - | Critical |
| CVE-2018-0777 | No | No | - | - | Critical |
| CVE-2018-0778 | No | No | Unlikely | Unlikely | Critical |
| Scripting Engine Security Feature Bypass | |||||
| CVE-2018-0818 | No | No | Unlikely | Unlikely | Important |
| Spoofing Vulnerability in Microsoft Office for MAC | |||||
| CVE-2018-0819 | Yes | No | Less Likely | Less Likely | Important |
| Windows Elevation of Privilege Vulnerability | |||||
| CVE-2018-0748 | No | No | Less Likely | Less Likely | Important |
| CVE-2018-0751 | No | No | Less Likely | Less Likely | Important |
| CVE-2018-0752 | No | No | Less Likely | Less Likely | Important |
| CVE-2018-0744 | No | No | More Likely | More Likely | Important |
| Windows GDI Information Disclosure Vulnerability | |||||
| CVE-2018-0750 | No | No | More Likely | More Likely | Important |
| Windows IPSec Denial of Service Vulnerability | |||||
| CVE-2018-0753 | No | No | - | - | Important |
| Windows Information Disclosure Vulnerability | |||||
| CVE-2018-0746 | No | No | More Likely | More Likely | Important |
| CVE-2018-0747 | No | No | More Likely | More Likely | Important |
| CVE-2018-0745 | No | No | More Likely | More Likely | Important |
| Windows Subsystem for Linux Elevation of Privilege Vulnerability | |||||
| CVE-2018-0743 | No | No | Less Likely | Less Likely | Important |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|
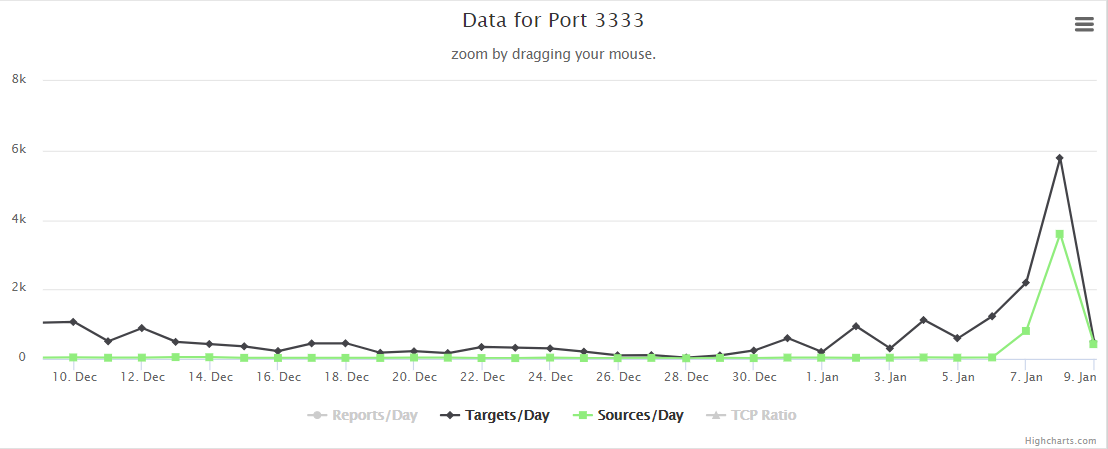
What is going on with port 3333?
We've seen a spike over the last day or so in reports of apparent scanning on TCP port 3333. I have serious doubts that anyone is actually looking for DEC Notes which is the registered IANA use for this port. While we're getting our own honeypots set up, I figured I'd ask our readers, do you have packets and/or any idea what is going on here? Please let us know in the comments or via our contact page. Thanx in advance.
Update: 2018-01-09 03:00 The original version of this diary inadvertantly said the traffic was UDP, the traffic that I am seeing in my logs at home is actually TCP. My apologies for the confusion.
Update: 2018-01-10 00:00 UTC The recurring theme in comments and email we've received suggests that some of the recent Monero miner malware samples are sending their results back to C2 servers on port 3333, so perhaps folks are trying to find and steal the illgotten cryptocurrency. I still haven't examined any traffic captured by our honeypots to confirm or refute that that is what they are looking for.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu



Comments