Retrieving malware over Tor on Windows
I found an easier way to retrieve malware over Tor on Windows, using free open-source software.
Tallow uses Tor and WinDivert to redirect network connections over the Tor network.
After starting Tallow, press the Tor button:
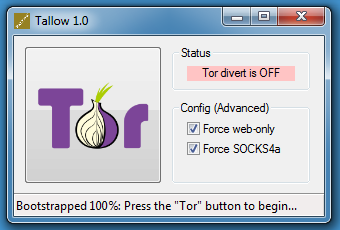
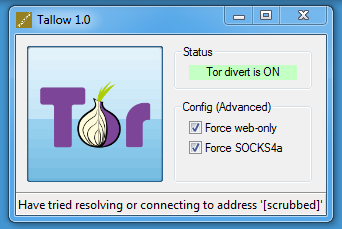
Then you can use wget on Windows:
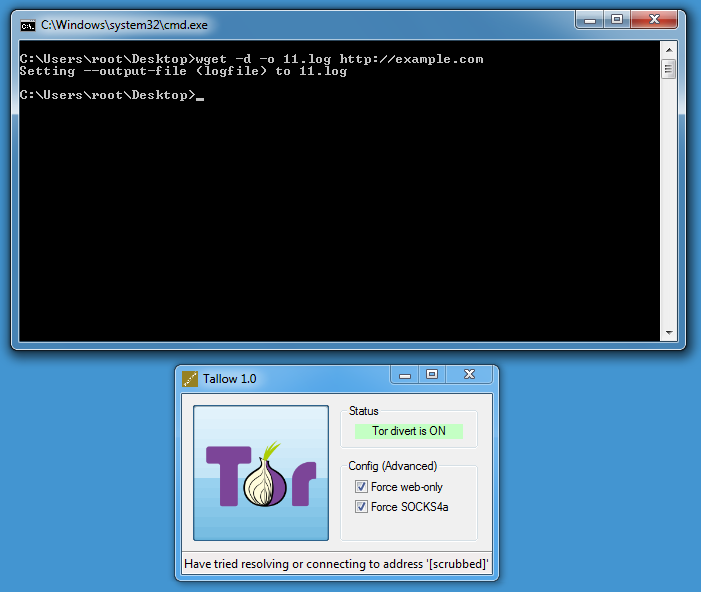
DEBUG output created by Wget 1.11.4 on Windows-MSVC.
--2018-02-25 23:56:22-- http://example.com/
Resolving example.com... seconds 0.00, 44.223.23.63
Caching example.com => 44.223.23.63
Connecting to example.com|44.223.23.63|:80... seconds 0.00, connected.
Created socket 300.
Releasing 0x0142ea78 (new refcount 1).---request begin---
GET / HTTP/1.0User-Agent: Wget/1.11.4
Accept: */*
Host: example.com
Connection: Keep-Alive
---request end---
HTTP request sent, awaiting response...
---response begin---
HTTP/1.0 200 OKCache-Control: max-age=604800
Content-Type: text/html
Date: Sun, 25 Feb 2018 22:56:24 GMT
Etag: "1541025663+gzip+ident"
Expires: Sun, 04 Mar 2018 22:56:24 GMT
Last-Modified: Fri, 09 Aug 2013 23:54:35 GMT
Server: ECS (lga/1386)
Vary: Accept-Encoding
X-Cache: HIT
Content-Length: 1270
Connection: keep-alive
---response end---
200 OK
Registered socket 300 for persistent reuse.
Length: 1270 (1.2K) [text/html]
Saving to: `index.html'0K . 100% 32.1M=0s
2018-02-25 23:56:23 (32.1 MB/s) - `index.html' saved [1270/1270]
Onion services can be accessed too:
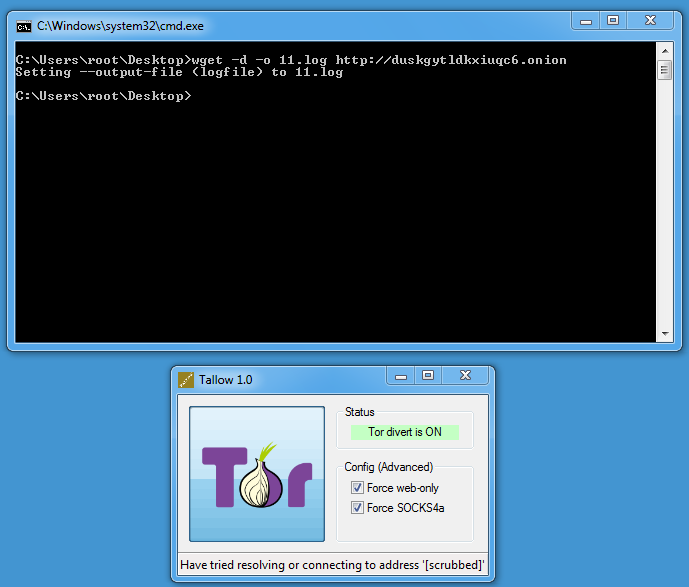
By default, Tallow only allows TCP connections on port 80 and 443 (Force web-only). Disable this toggle if you need to access other ports.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Blackhole Advertising Sites with Pi-hole
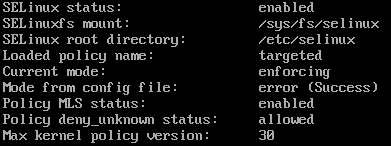
A coworker told me a few weeks ago that he started using Pi-hole to block all advertising and that got me curious. I checked the hardware requirements and already had a server I could install this on. I used CentOS 7.4 as my platform but before starting, make sure selinux isn't running because it isn't supported (It is one of the checks the installation script does). To check execute:
sestatus
If it return enabled change the configuration (see below) and reboot after it has been saved:
vi /etc/sysconfig/selinux, set selinux=disabled
Next make sure your server has a static address before running the installation and then you are ready to install.
I followed their recommended installation command: curl -sSL https://install.pi-hole.net | bash [1] but you can also install everything manually by following the steps here as Method 1 or 2.
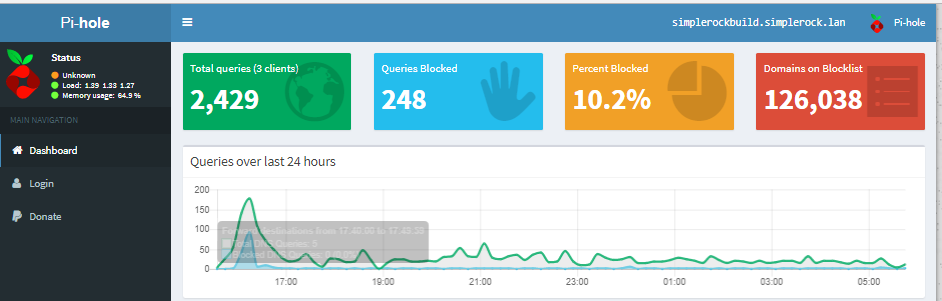
The installation was pretty straight forward and it checked for any missing packages and added them to the server. I answered a series of question to setup the Pi-hole DNS server. After the installation you need to point all your clients to your new DNS server (forward internal DNS server to Pi-hole) to take advantage of the blocking capabilities. If you setup the web interface you can login via http://IP/admin and login with the default password provided after the installation (the password can be changed at the command line with: sudo pihole -a -p) or view the statistics via the Dashboard provided by the web server.
[1] https://pi-hole.net
[2] https://discourse.pi-hole.net/t/hardware-software-requirements/273
[3] https://github.com/pi-hole/pi-hole/#one-step-automated-install
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments