Malspam pushes Emotet with Qakbot as the follow-up malware
Introduction
I've posted several diaries about malicious spam (malspam) pushing Emotet malware. In recent years, I've made sure to include information on the follow-up malware, since Emotet is also a distributor for other malware families. Not much has changed since my previous diary about Emotet malspam in November 2018. In the past two or three weeks, I've consistently seen Trickbot as the follow-up malware; however, this past Monday I also saw Qakbot as the follow-up malware. Today's diary examines an Emotet infection from Monday 2019-03-11 that had Qakbot as the follow-up malware.
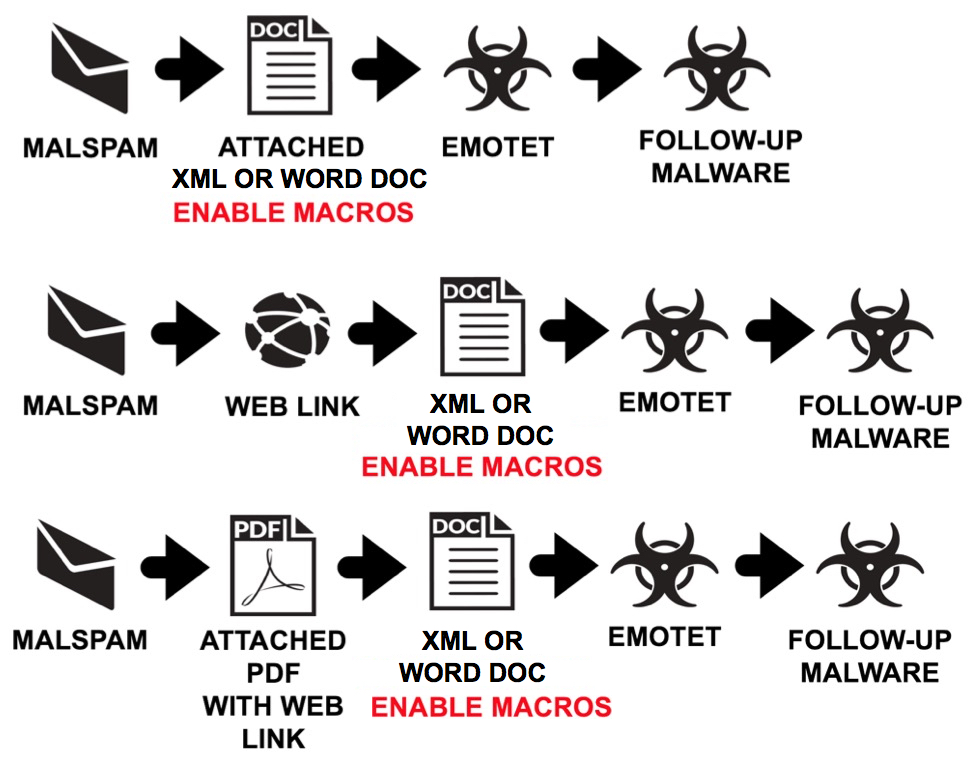
Shown above: Flow chart for recent Emotet malspam infections I've seen during the past month or so.
Email example
Shown below is an example of Emotet malspam with a link for the XML document. Clicking on the link downloaded an XML document with a .doc file extension that opens in Microsoft Word by default, if Word is installed on the victim's host.
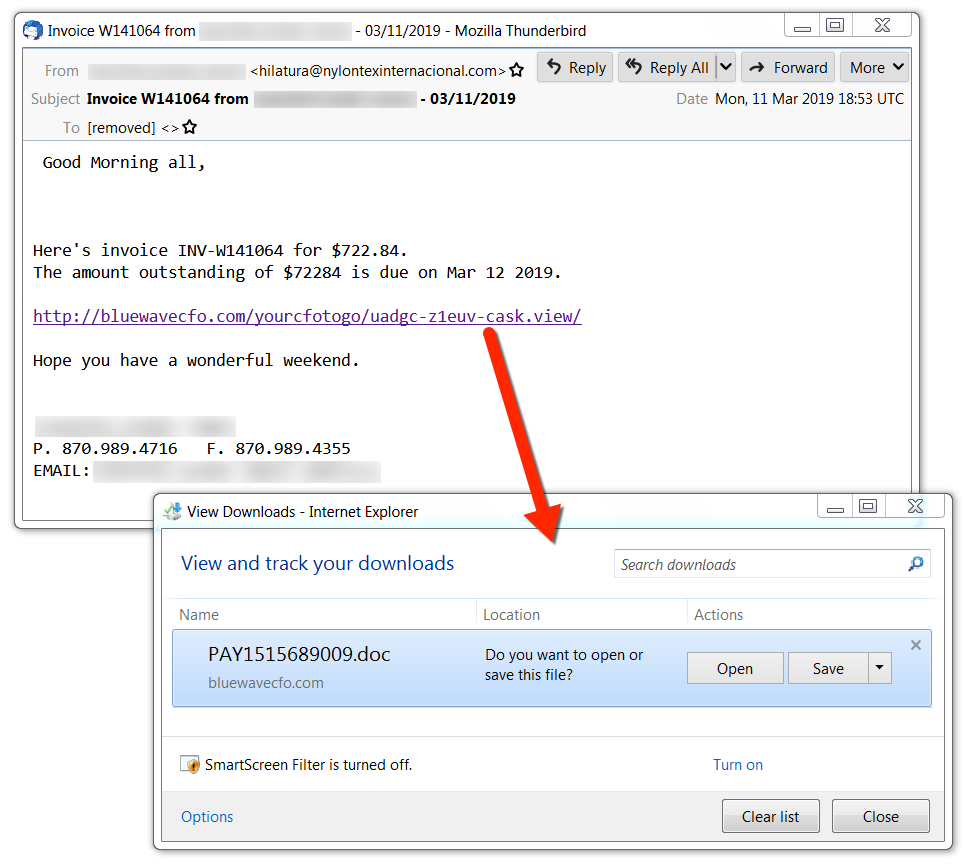
Shown above: Screenshot of Emotet malspam with a link for an XML document.
Downloaded XML doc
The downloaded XML document has macros that, if enabled, will infected a vulnerable Windows host with Emotet.

Shown above: An XML document downloaded from a link in Emotet malspam.
Infection traffic
Infection traffic was typical for what I've seen with Emotet, and the Qakbot traffic was similar to patterns seen the last time I documented an example of Emotet + Qakbot in December 2018.

Shown above: Traffic from an infected Windows host.
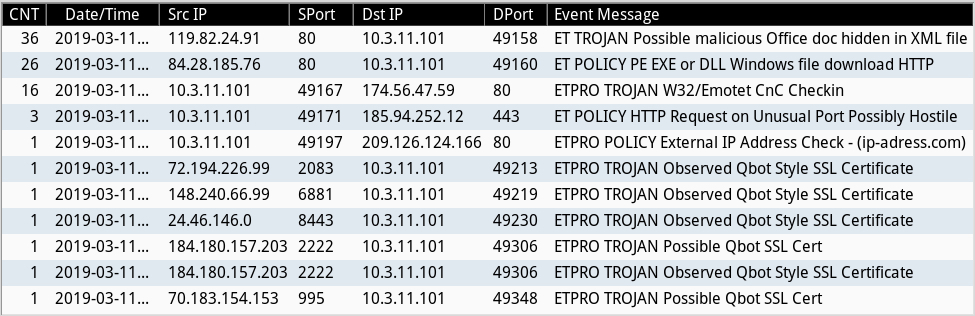
Shown above: Alerts from Security Onion using Sguil with Suricata and the EmergingThreats Pro ruleset.
Post-infection forensics
The infected Windows host had post-infection artifacts similar to the last time I saw Emotet + Qakbot. Both Emotet and Qakbot were kept persistent through the Windows registry. Emotet generally saves follow-up malware under the C:\ProgramData folder, and that was where the Qakbot EXE was originally saved. However, when Qakbot executed, it copied itself to another directory and replaced the original file with a re-named calc.exe.
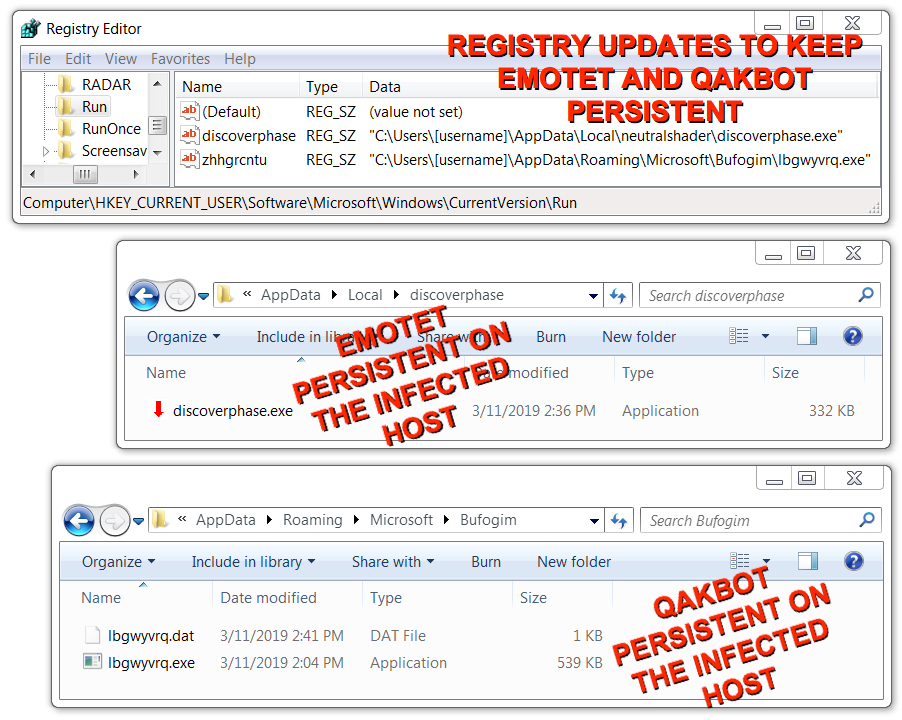
Shown above: Emotet and Qakbot persistent on my infected lab host.
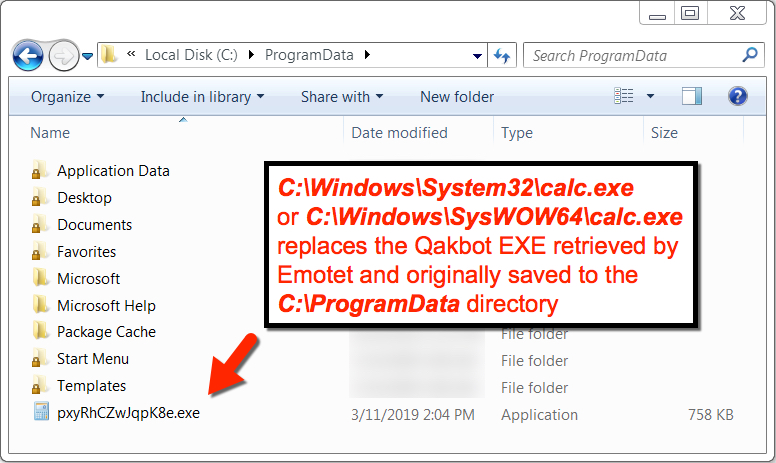
Shown above: Qakbot replaces the file it was originally downloaded as with calc.exe, a non-malicious file.
The following is data from malware I retrieved from my infected Windows host:
SHA256 hash: cf59f0ff182405c068262b1879f559f4244d4e94cc813f900c96c3eb89a59b10
- File size: 199,348 bytes
- File description: Downloaded XML doc with macro for Emotet
SHA256 hash: e6308496a22d317cf7e5a5469351c5cf4dc11ef7e47b39e9a97ea85707cbec8a
- File size: 229,640 bytes
- File description: Emotet malware binary retrieved by XML doc macro
SHA256 hash: ebb4e12bcc3b95e4b8b16798b7c46d24f8b973a210424512d580112534c2012e
- File size: 229,640 bytes
- File description: Updated Emotet malware binary (1st update)
SHA256 hash: c6ff3a2fd9e623754056a39f379eba289105f0a935dc05249ca1957cf35e84ac
- File size: 339,720 bytes
- File description: Updated Emotet malware binary (2nd update)
SHA256 hash: 9978756e1daf844bd734c6282fec583d5f3089be4e21d7fbd43877d25598f8f6
- File size: 551,936 bytes
- File description: Qakbot retrieved by Emotet-infected host (1st run)
Final words
On Monday 2019-03-11, I also saw Emotet + Trickbot on another lab host within an hour after I infected my first lab host with Emotet + Qakbot. Pcap and malware from these two infections can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments