Investigating an Odd DNS Query
I have been asked this question a few times, and figure it may be worthwhile to document this in a quick diary. This is typically the result of watching for odd DNS queries (and I highly recommend that). But not all DNS queries are created equal, and sometimes you will see odd, or even malicious, hostnames and domain names in your logs without any wrongdoing on your end.
The latest example I just ran into: faraisp.ir . IR being the country level domain for Iran, and I am currently not doing business with Iran, which certainly makes this a bit suspect if it bubbles up to the top of the "odd domain list".
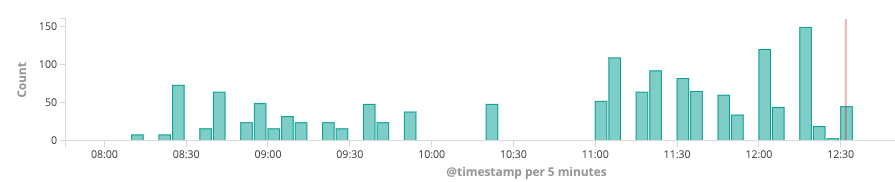
The queries for this domain came in at a rate of 100-150/5min in my Zeek logs:
Next, let's break down all the queries for the "faraisp.ir" domain
You can click on the image to get a larger view. But the queries are essentially A/AAAA queries for ns[1-4].faraisp.ir. To add to this: they all came from my DNS server. Now the DNS server's query log would usually be my next step. But in this case, the query log does not show any queries for *.faraisp.ir. I also didn't see any queries from any of my hosts to the name server for *.faraisp.ir . The reason for these queries was that a prior query returned these hostnames as authority records. This triggered my name server to do a lookup for these hostnames. So I need to search for answers that contain faraisp.ir.
It turned out that a prior reverse lookup by the mail servers spam filter returned the authority record, and as a result, the name server then kept looking for ns[1-4].faraisp.ir. So why did the mail server try to reverse resolve the IP address over and over? My first guess was spam, but it turned out to be a brute force attack against the server:
May 23 16:47:35 mail postfix/smtpd[3420]: connect from unknown[185.137.111.145] May 23 16:47:42 mail postfix/smtpd[3420]: warning: unknown[185.137.111.145]: SASL LOGIN authentication failed: authentication failure May 23 16:47:42 mail postfix/smtpd[3420]: disconnect from unknown[185.137.111.145] May 23 16:47:58 mail postfix/smtpd[3420]: connect from unknown[185.137.111.44] May 23 16:48:05 mail postfix/smtpd[3420]: warning: unknown[185.137.111.44]: SASL LOGIN authentication failed: authentication failure May 23 16:48:05 mail postfix/smtpd[3420]: disconnect from unknown[185.137.111.44]
So at least not entirely a "false positive", but also not terribly exciting. Mail servers are probably the main source of odd DNS queries. They tend to do a lot of reverse lookups for anti-spam, and they also use various DNS based anti-spam and email validation features that often look very much like data exfiltration. You will also see a lot of less common record types in DNS queries from mail servers (TXT, SPF..).
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|



Comments