Secure vs. cleartext protocols - couple of interesting stats
For a very long time, there has been a strong effort aimed toward moving all potentially sensitive network-based communications from unencrypted protocols to the secure and encrypted ones. And with the recently released APWG report noting that 74% of phishing sites used HTTPS in the last quarter of 2019[1] and Apple’s supposed plan to start supporting only TLS certificates with no more than one year period of validity[2], I thought that this might be a good time to take a look the current protocol landscape on the internet. Specifically at how the support for protocols, which offer cryptographic protection to data in transit, has changed in relation to support of cleartext protocols in the last months.
To this end, I analyzed data gathered from Shodan over the last six months – from the beginning of September 2019 to the end of February 2020 – which were related to servers running services on ports 22 and 23 (SSH and Telnet) and 80 and 443 (HTTP and HTTPS). While it is true that other services may be running on these ports than the ones mentioned above, since such configurations are not too usual, they shouldn’t bring too large a variance into our numbers. One last thing, which should be mentioned before we get to the interesting part, is that since timelines formed from absolute values gathered from Shodan often contain quite large peaks and valleys [3], we will take a look at ratios (or rather percentages of the aggregate values) rather than the absolute counts.
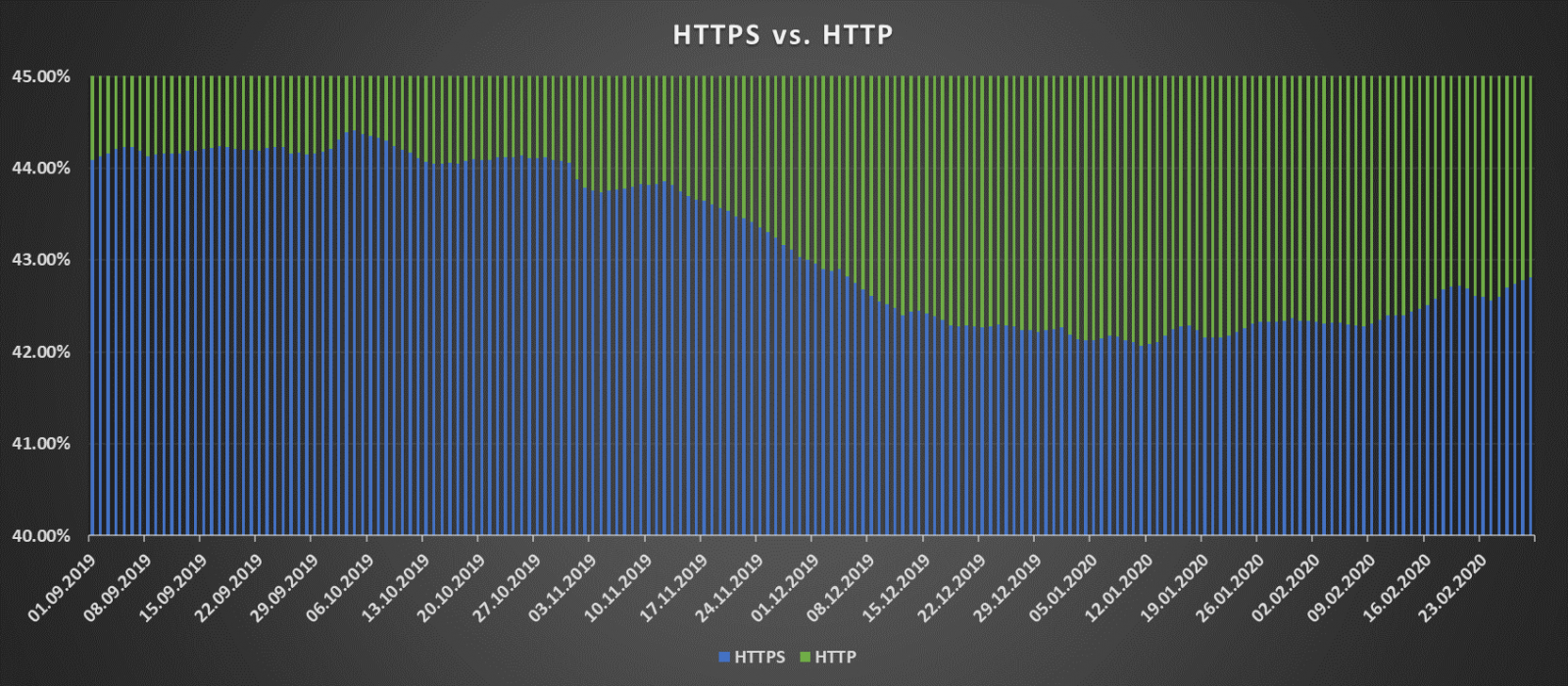
Let’s start with HTTP and HTTPS since these protocols differ from the other two, which we are interested in, in that support for the unencrypted one is not necessarily something which we’d want to get rid of. For ease of access, a web server, which supports HTTPS, usually supports HTTP as well and when a browser connects to the server using the cleartext protocol, it is immediately redirected to HTTPS. Keeping this in mind, an ideal state of affairs would be if the ratio between servers supporting HTTP and HTTPS was 1:1, or higher, in favor of the TLS-enabled protocol.
Unfortunately, we’re not quite there yet. On the contrary, near the end of last year, the ratio moved decidedly in favor of HTTP support and at the "lowest" point, it was almost 6:4. Since the start of 2020, a slow relative rise of HTTPS support is apparent, but it is certain, that there will be more servers offering HTTP than HTTPS for a while yet.
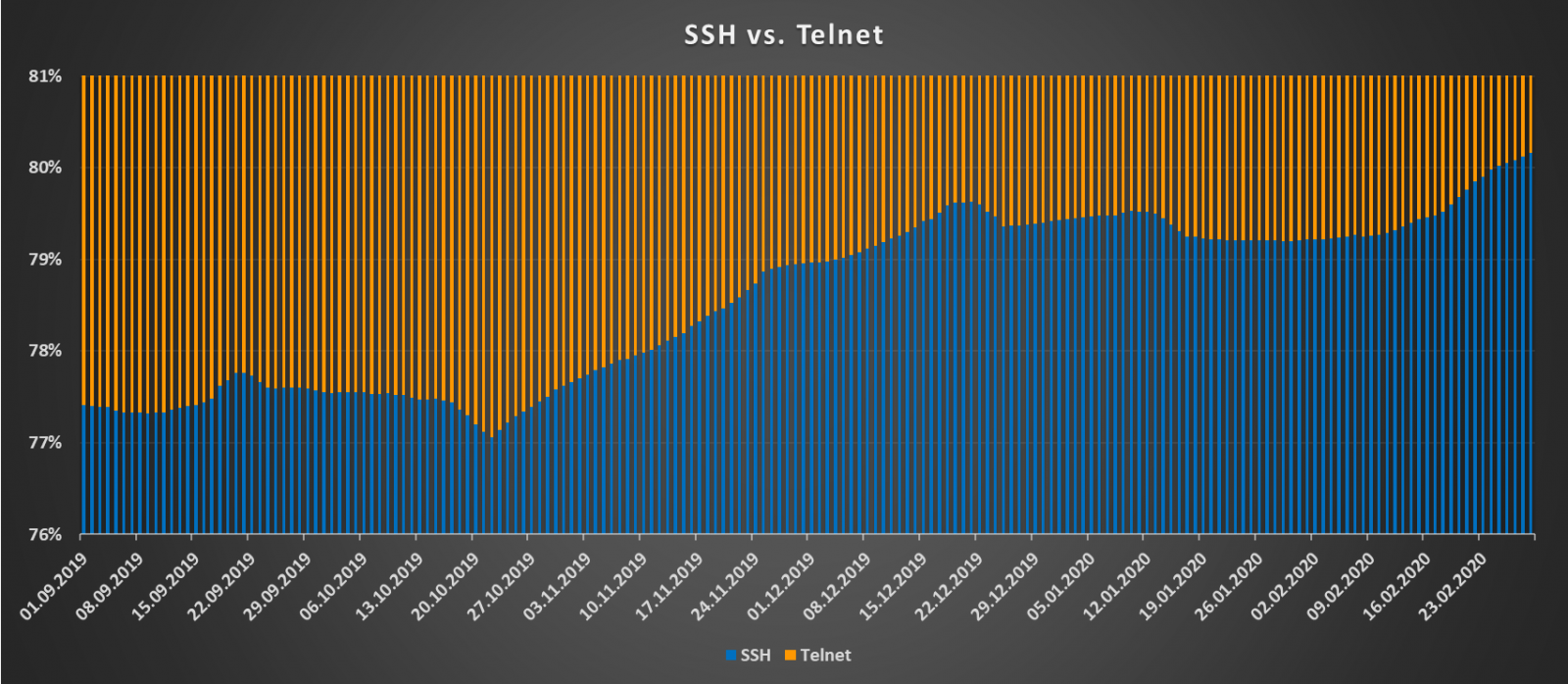
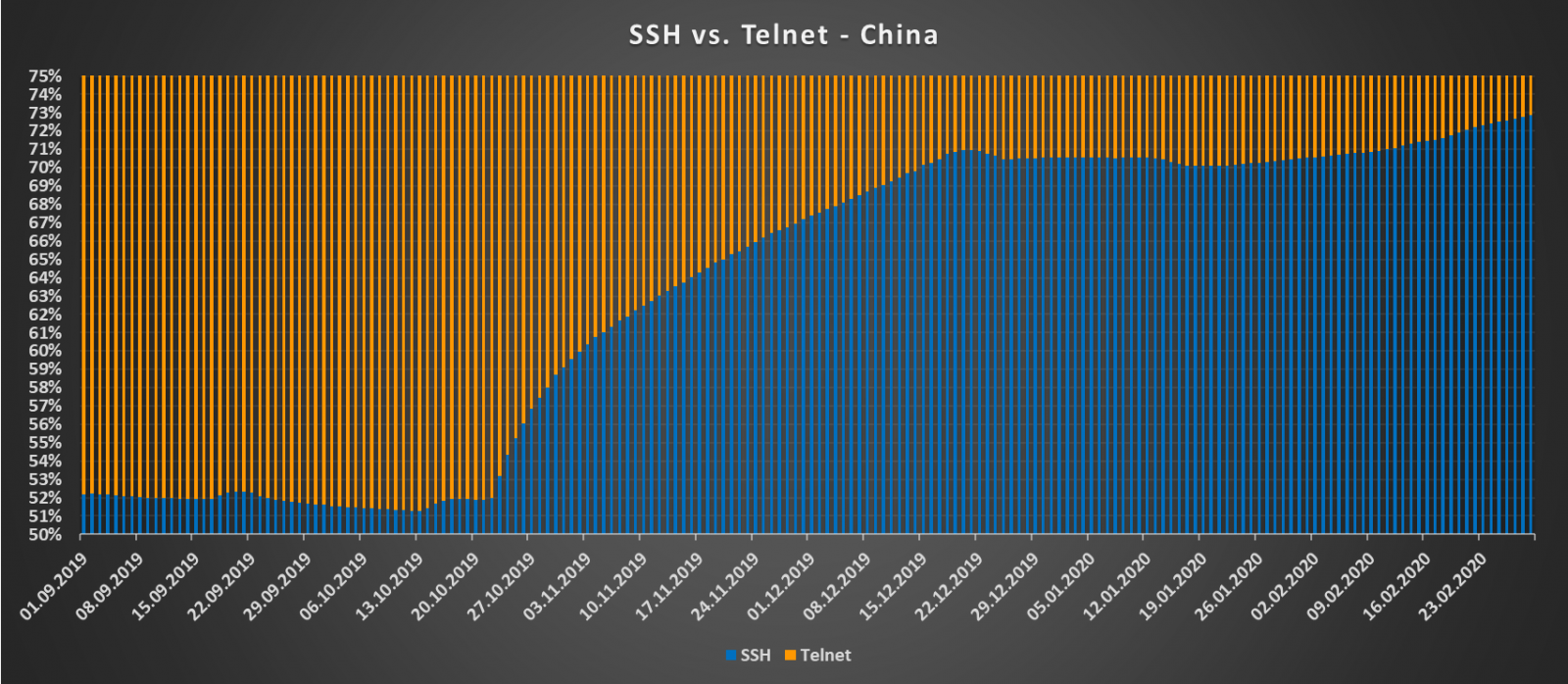
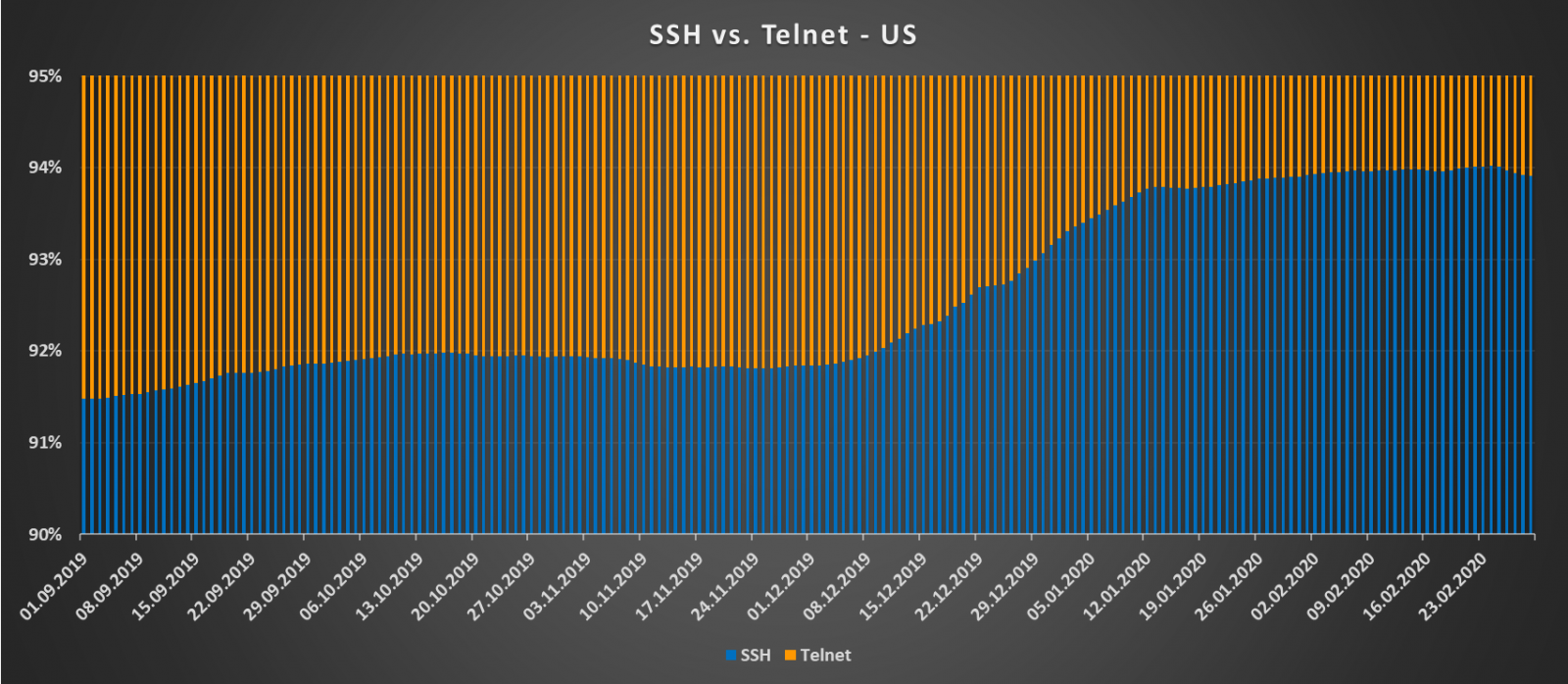
In case of Telnet and SSH, the situation is luckily rather different. Unlike with HTTP, there aren’t many reasons to support Telnet and not to use SSH exclusively, especially over the internet. It is therefore not surprising that the ratio between servers supporting Telnet and SSH has been firmly in favor of the encrypted protocol over the last six months. In fact, except for a couple of small drops, the ratio was steadily growing in favor of SSH up to the current state of 4:1.
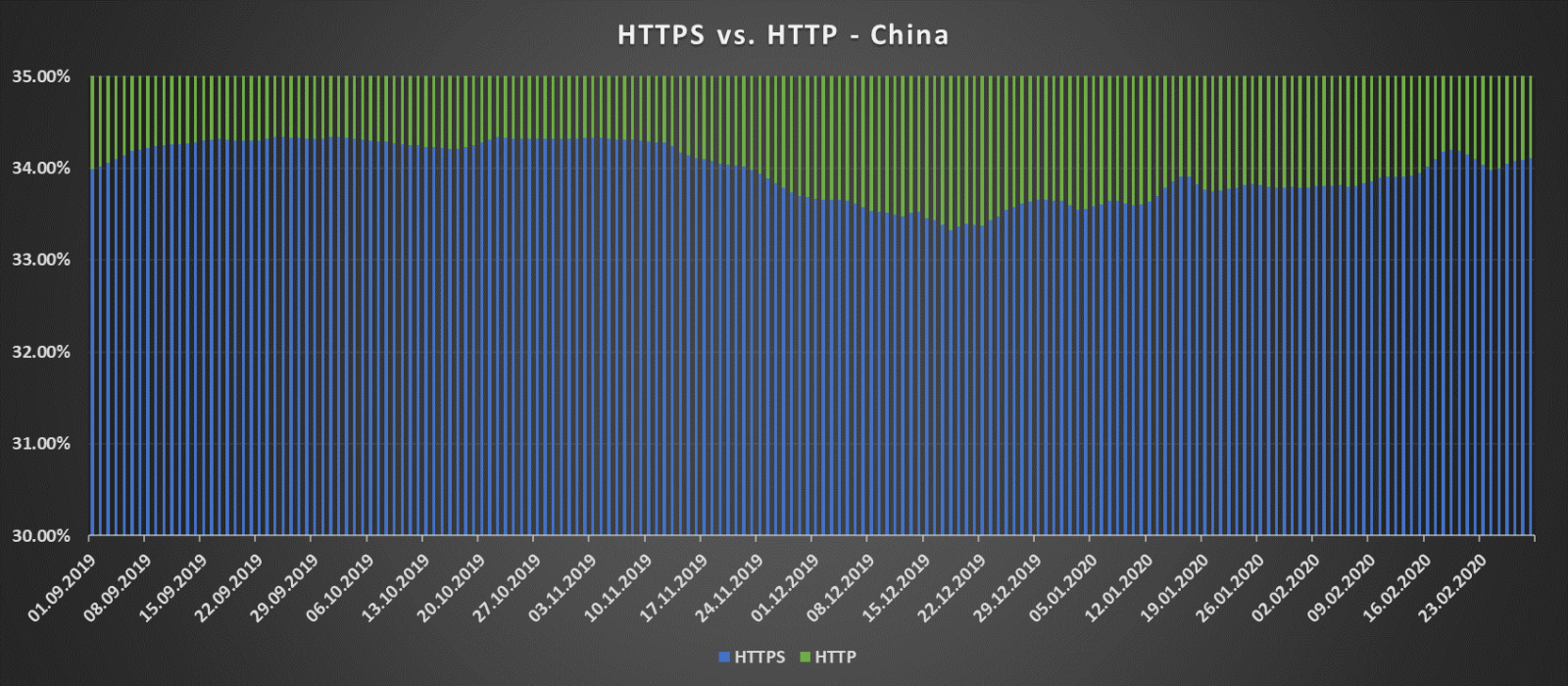
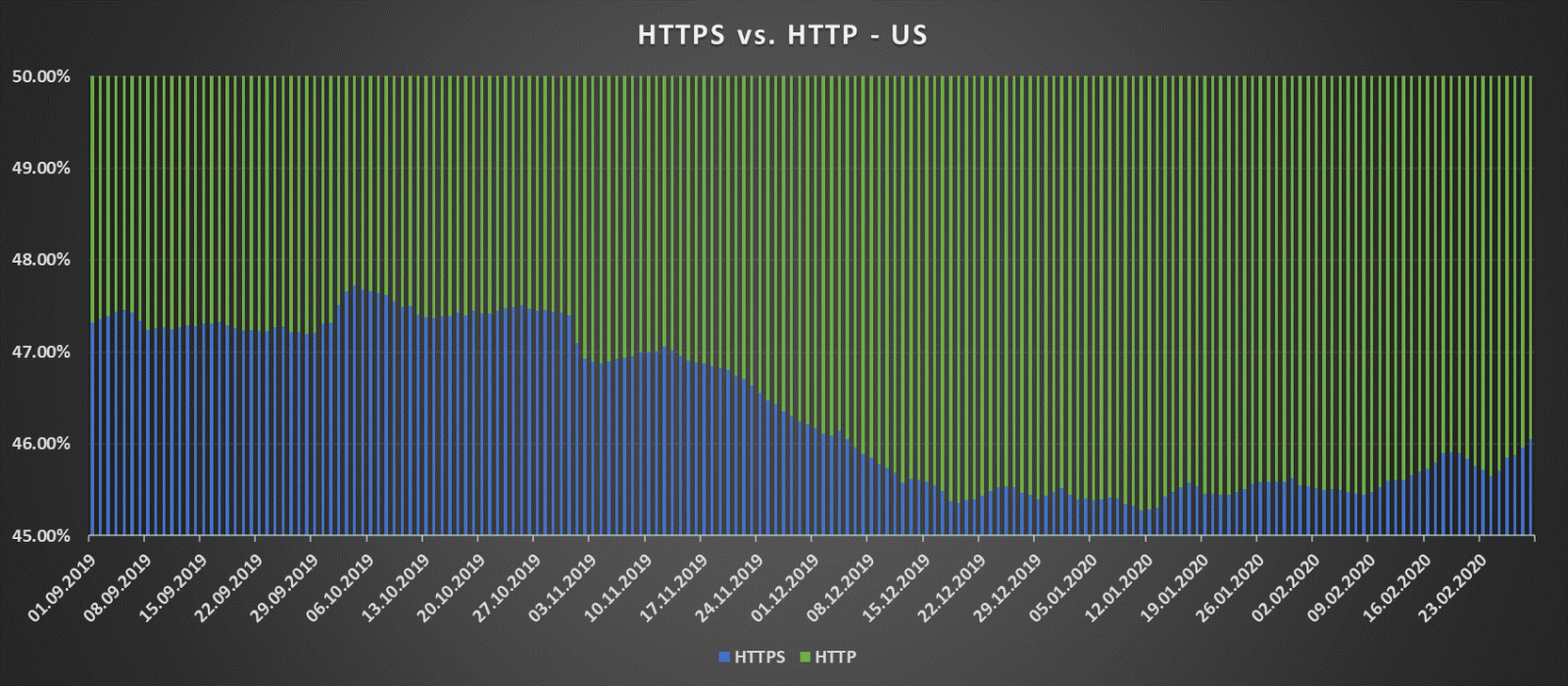
Of course, these are global data, and situation in specific countries varies widely – to demonstrate this, here are charts for the support of HTTP and HTTPS in China and the United States over the same period (note the significant differences between percentages).
And here are the charts for support of Telnet and SSH in both countries.
[1] https://docs.apwg.org/reports/apwg_trends_report_q4_2019.pdf
[2] https://www.thesslstore.com/blog/ssl-certificate-validity-will-be-limited-to-one-year-by-apples-safari-browser/
[3] https://isc.sans.edu/forums/diary/Did+the+recent+malicious+BlueKeep+campaign+have+any+positive+impact+when+it+comes+to+patching/25506/


Comments