Traffic Analysis Quiz: What's the Malware From This Infection?
Introduction
Today's diary is a traffic analysis quiz where you try to identify the malware based on a pcap of traffic from an infected Windows host. Download the pcap from this page, which also has the alerts. Don't open or review the alerts yet, because they give away the answer.
Meanwhile, I'll provide the requirements for this quiz and some background on the infection.
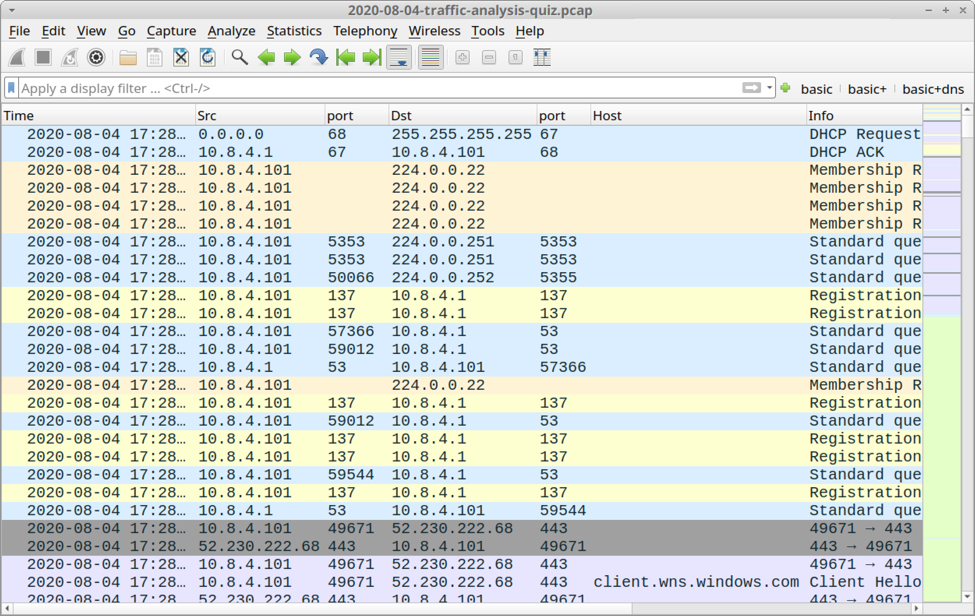
Shown above: Screenshot of the pcap for this quiz opened in Wireshark.
Requirements
This type of analysis requires Wireshark. Wireshark is my tool of choice to review packet captures (pcaps) of infection activity. However, default settings for Wireshark are not optimized for web-based malware traffic. That's why I encourage people to customize Wireshark after installing it. To help, I've written a series of tutorials. The ones most helpful for this quiz are:
- Customizing Wireshark - Changing Your Column Display
- Using Wireshark - Display Filter Expressions
- Using Wireshark - Exporting Objects from a Pcap
Another requirement: use a non-Windows environment like BSD, Linux, or macOS. Why? Because this pcap contains HTTP traffic sending Windows-based malware. If you're using a Windows host to review the pcap, your antivirus (or Windows Defender) may delete the pcap or malware. Worst case? If you extract the malware from the pcap and accidentally run it, you might infect your Windows computer.
So if you're new to this type of analysis, beware. There's malware involved.
Background on the infection
This infection was caused by a malicious Excel spreadsheet. It has macros designed to infect a vulnerable Windows host, so I infected one in my lab. Default settings in recent versions of Microsoft Office would prevent these type of macros from causing an infection. This is much more effective against older versions of Windows like Windows 7.
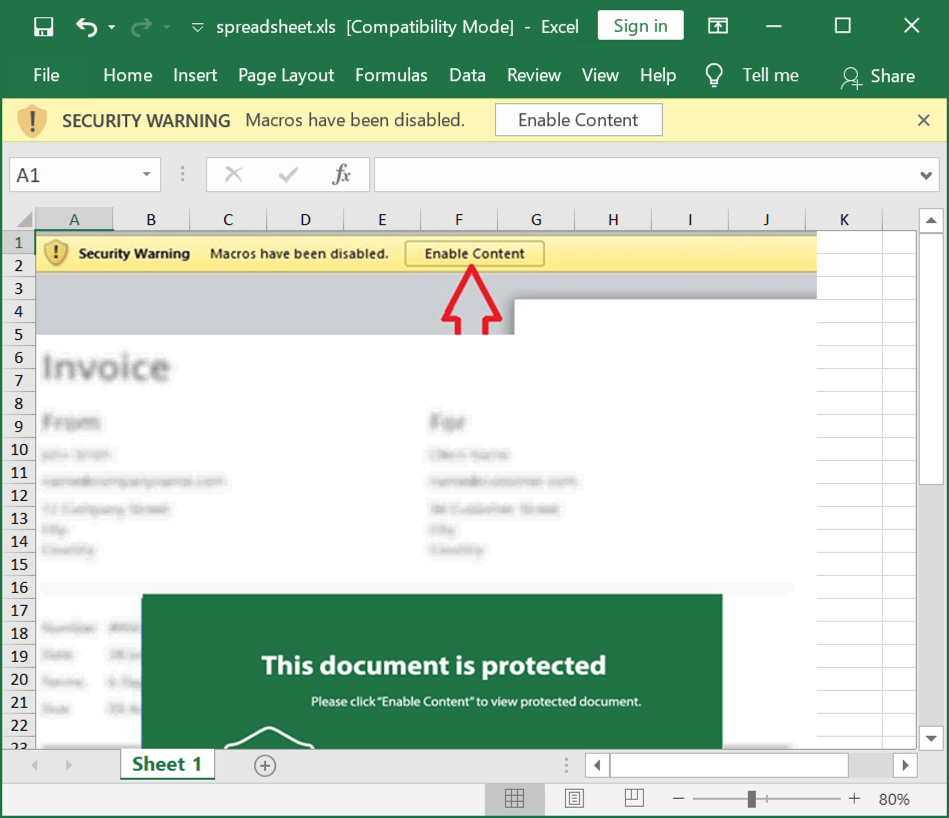
Shown above: Screenshot of the spreadsheet used for this infection.
Enabling macros on this spreadsheet caused my vulnerable host to download a malicious Windows executable (EXE) and save it as C:\Users\Public\svchost32.exe where it was initially run.
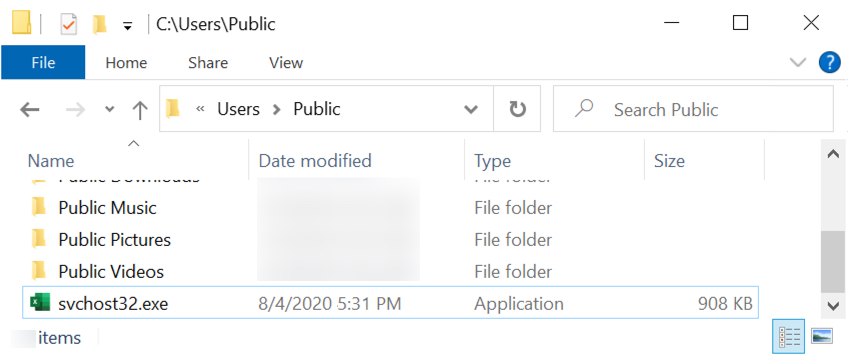
Shown above: The initial location of the malicious EXE on my infected lab host.
After a minute or two, the malware was deleted from C:\Users\Public\svchost32.exe and saved under a randomly-named directory under C:\Program Files (x86)\ using a random file name. The directory and new file name are different for each infection. The malware was made persistent through an update to the Windows registry as shown below.
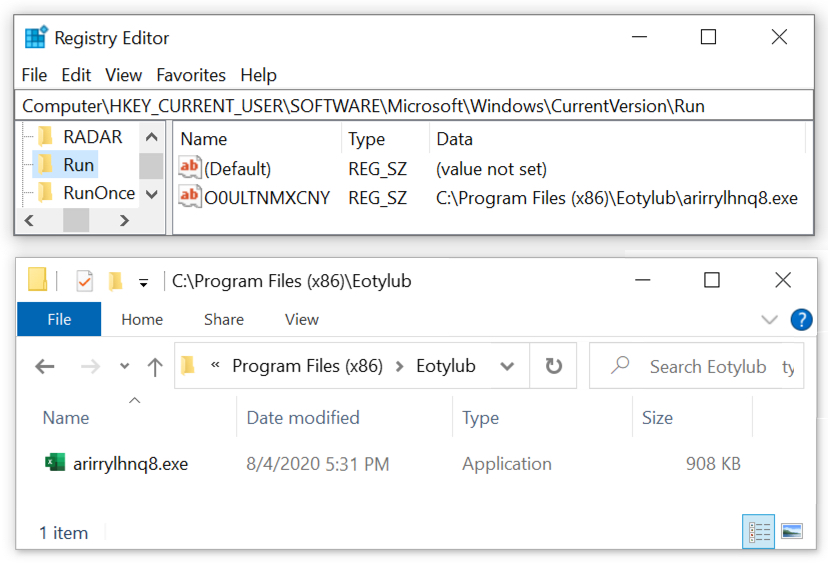
Shown above: Windows registry update and location of the malware persistent on my infected host.
This method is used by different families of malware. The chain of events:
- Victim receives a malicious Microsoft Office document (usually an Excel spreadsheet or Word document)
- Victim enables macros on a vulnerable Windows host
- Vulnerable Windows host retrieves a Windows EXE or DLL through web-based traffic
- EXE or DLL is saved to disc
- The EXE or DLL infects the vulnerable Windows host and is made persistent
Fortunately, this chain is rarely effective against an up-to-date version of Windows with default security settings. In this case, Microsoft Office would not run the macro unless I disabled some key security functions.
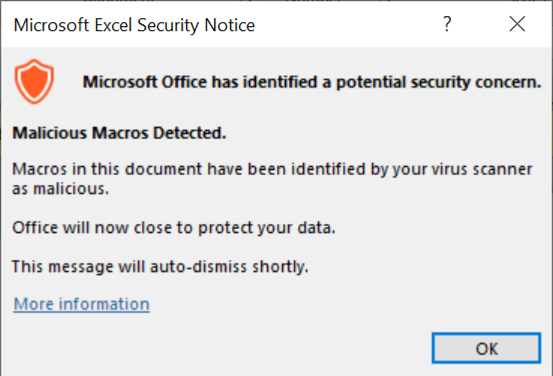
Shown above: Warning message I initially saw on my lab host.
Reviewing the pcap
If you've set up Wireshark according to the previously-mentioned tutorials, open the pcap and use the basic web filter to find an HTTP request to aromaterapiaclinicabrasil[.]com[.]br on 162.214.51[.]208.
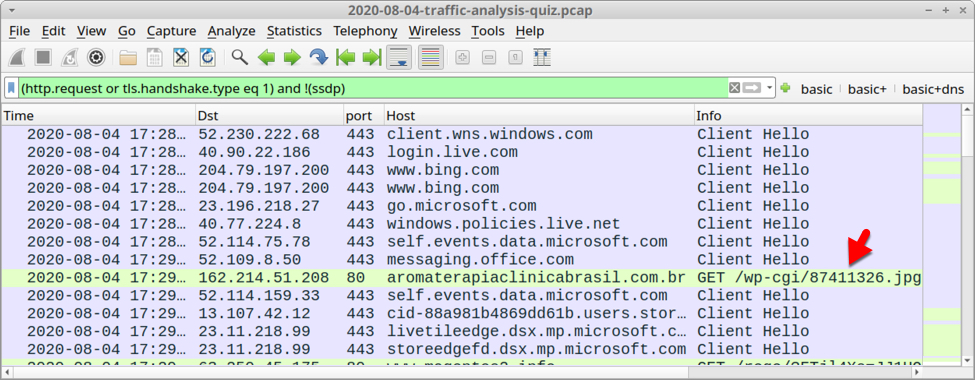
Shown above: Traffic from the quiz pcap filtered in Wireshark.
This HTTP request ends with .jpg, but it returned an EXE. Left click on that line and follow the TCP stream, so we can confirm this is, in fact, an EXE.
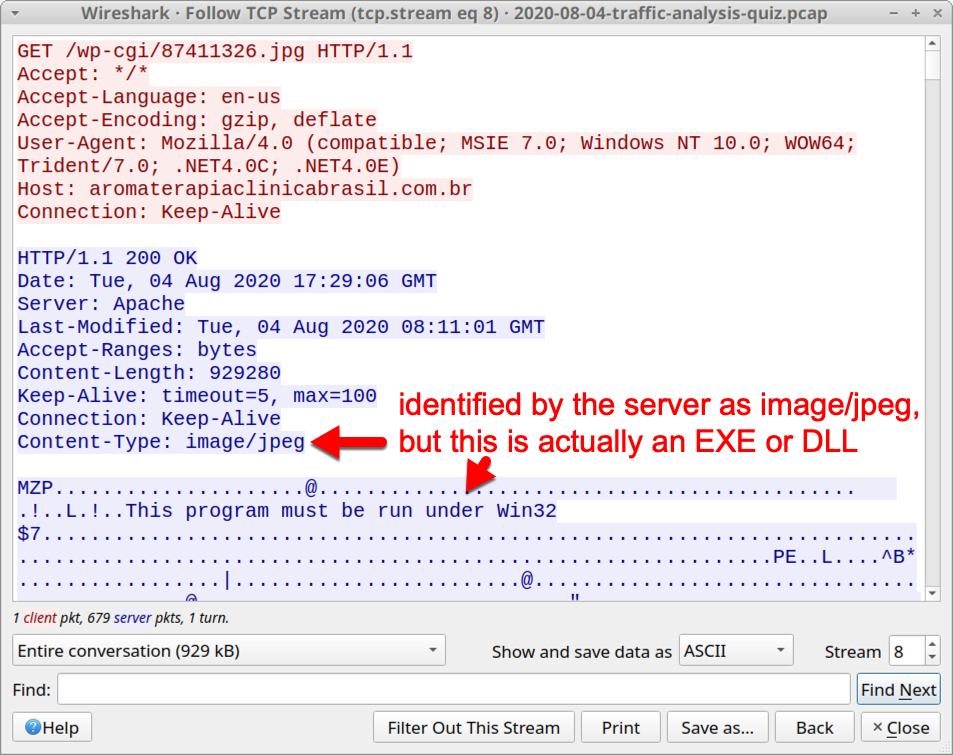
Shown above: HTTP request ending with .jpg returns a Windows EXE or DLL.
Is this is an EXE, or is it a DLL? They both look the same in a TCP stream. The ASCII characters MZ show as the first two bytes, and This program must be run under Win32 could be used by an EXE, or it could be used by a DLL. To get more information on the file, we can explort it from the pcap. A word of caution: this is Windows malware, so you should export this file in a non-Windows environment.
Use the menu path File --> Export Objects --> HTTP and export the file returned from aromaterapiaclinicabrasil[.]com[.]br as shown in the next two images.
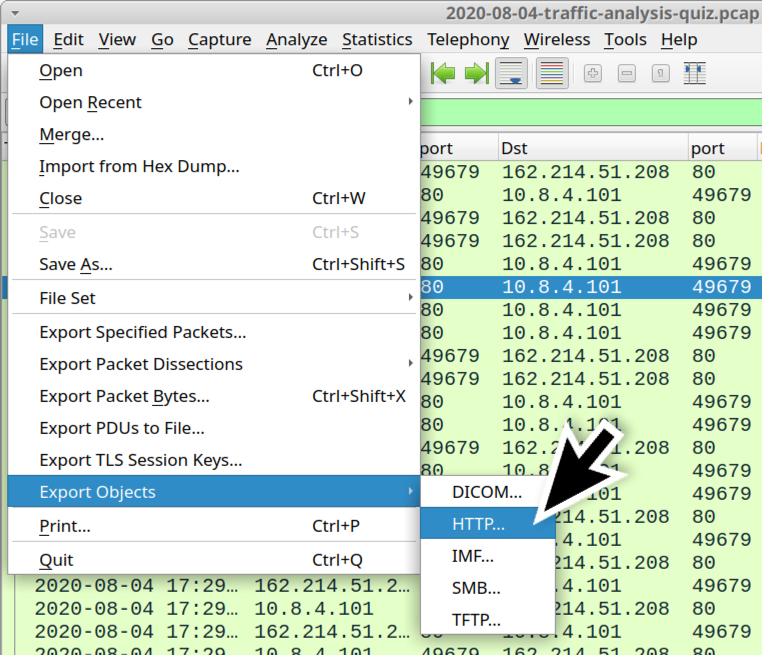
Shown above: Exporting objects from HTTP traffic in the pcap.
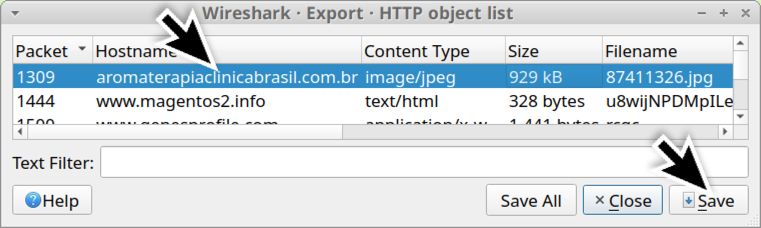
Shown above: Saving the file returned from aromaterapiaclinicabrasil[.]com[.]br.
In a Linux environment, it's easy to confirm what type of file this is. Use the file command in a terminal window. Get the SHA256 hash of the file using the shasum -a 256 command as shown below. I prefer a Debian or Ubuntu-based Linux environment, but any Linux environment will do.
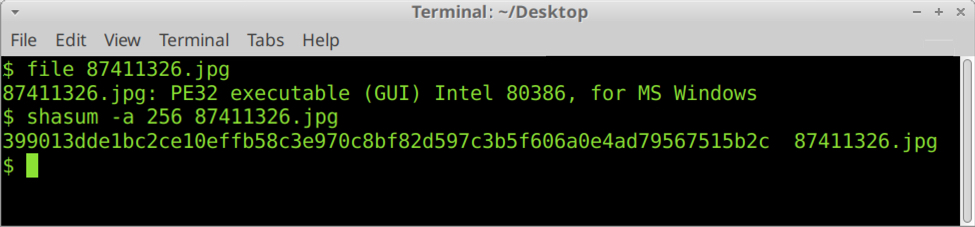
Shown above: Using a terminal window to confirm this is an EXE and get the SHA256 hash.
Once you have the SHA256 hash, search for it in VirusTotal or publicly-available online sandboxes like app.any.run, capesandbox.com, and other sites. You can also do a Google search.
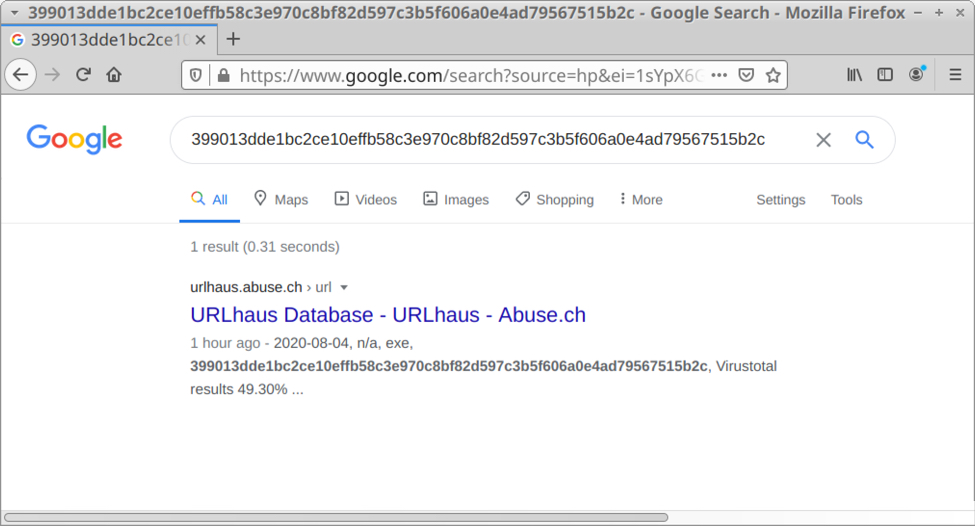
Shown above: Google results when I searched for the SHA256 hash of the EXE.
Keep in mind the Office document is a delivery mechanism. The actual malware is based on the EXE retrieved after enabling macros. What is the malware family in this case? The answer is not as straight-forward as you might think. Different vendors often have their own names for the same type of malware. In this case, alerts from the post-infection traffic will reveal what family of malware caused this infection.
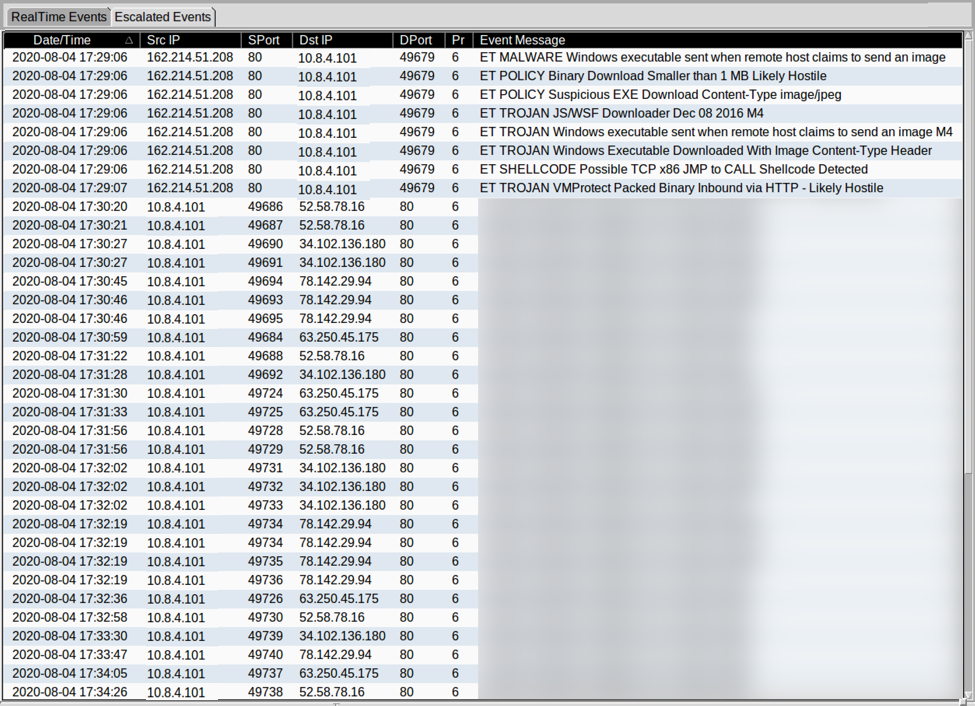
Shown above: Alerts from the infection using Security Onion with Suricata and the EmergingThreats Pro (ETPRO) ruleset.
Final words
If you're an experienced malware analyst, this quiz might provide a minute or two of interest. If you're tempted to immediately know the answer, just review the alerts and find ones for the CnC traffic. If you're new to this type of analysis, hopefully this quiz has helped.
Once again, a pcap of the traffic and the associated alerts are located here.
A copy of the spreadsheet that caused this traffic can be found here.
A copy of the EXE can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments