SMBGhost - the critical vulnerability many seem to have forgotten to patch
You probably remember that back in March, Microsoft released a patch for a vulnerability in SMBv3 dubbed SMBGhost (CVE-2020-0796), since at that time, it received as much media attention as was reasonable for a critical (CVSS 10.0) vulnerability in Windows, which might lead to remote code execution[1].
Luckily, achieving RCE through SMBGhost turned out to be anything but simple so although the first public exploits appeared fairly quickly, they used the vulnerability “only” for local privilege escalation[2]. It wasn’t until June that a PoC for achieving RCE was published[3]. Since release of this PoC was again met with wide attention from the media, one might reasonably expect that by now, most of the vulnerable machines would have been patched – especially those accessible from the internet.
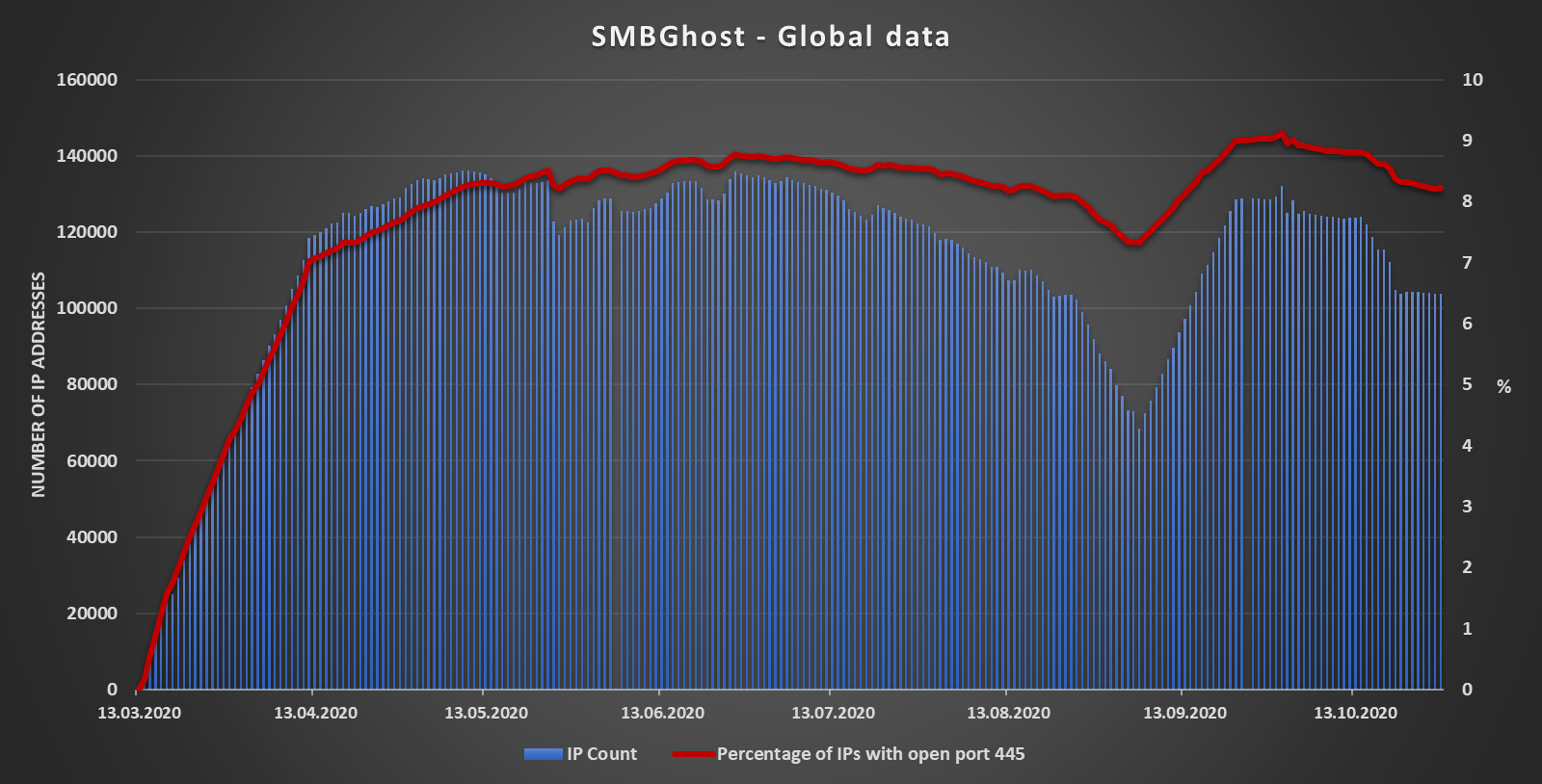
Going by data I’ve gathered from Shodan over the last eight months, this doesn’t appear to be true, however.
Besides scanning for open ports and running services, Shodan is also capable of identifying machines/IPs which are impacted by specific vulnerabilities – you may try this yourself if you have one of the higher-level account by using the search filter vuln (e.g. “vuln:cve-2020-0796”). I’m unsure what method Shodan uses to determine whether a certain machine is vulnerable to SMBGhost, but if its detection mechanism is accurate, it would appear that there are still over 103 000 affected machines accessible from the internet. This would mean that a vulnerable machine hides behind approximately 8% of all IPs, which have port 445 open.
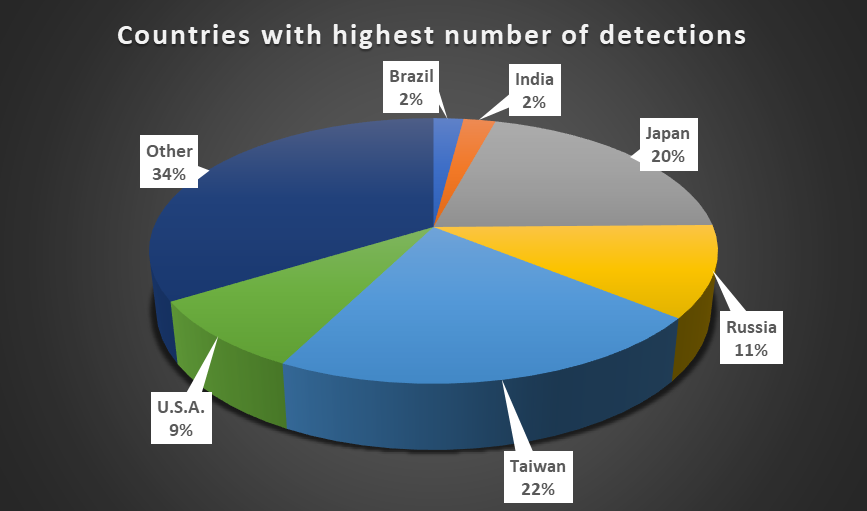
The following chart shows countries with most detections – I've included those with at least 2 000 IPs detected as vulnerable by Shodan.
It is hard to say why are so many unpatched machines are still out there. Microsoft did release the patch for CVE-2020-0796 out-of-band instead as a part of its usual patch Tuesday pack of fixes[4], but that was the only unusual thing about it and doesn’t make much sense that this would be the reason why it still isn't applied on so many systems… In any case, if the numbers provided by Shodan are accurate, they are concerning to say the least, especially since SMBGhost – as an RCE – is “wormable”. If for whatever reason you still haven't patched any of your systems, now would seem to be a good time to do so.
Hopefully, we won’t see any worms or other attempts at mass exploitation of CVE-2020-0796 any time soon, but who knows – it would perhaps be timely given the name of the vulnerability and the upcoming Halloween…
[1] https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0796
[2] https://github.com/danigargu/CVE-2020-0796
[3] https://github.com/chompie1337/SMBGhost_RCE_PoC
[4] https://www.zdnet.com/article/microsoft-patches-smbv3-wormable-bug-that-leaked-earlier-this-week/


Comments