Malspam pushing Trickbot gtag rob13
Introduction
Trickbot malware has been a relatively constant presence in the cyber threat landscape so far this year. We've seen activity continue this week, and today's diary reviews an infection I generated on Wednesday 2021-02-17.
The infection chain of events:
The email
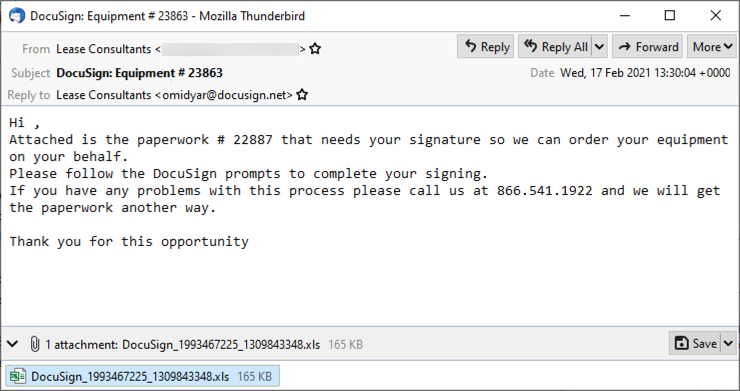
Shown above: Screenshot from an example of malspam seen earlier today (Wednesday 2021-02-17).
The spreadsheet
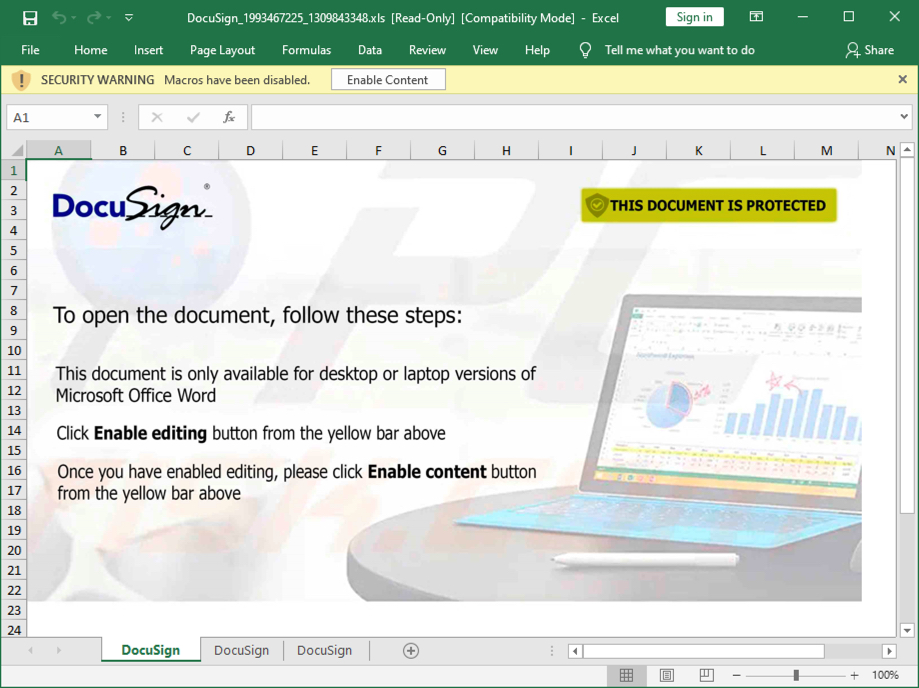
Shown above: Screenshot of the attached Excel spreadsheet with macros for Trickbot.
Infection traffic
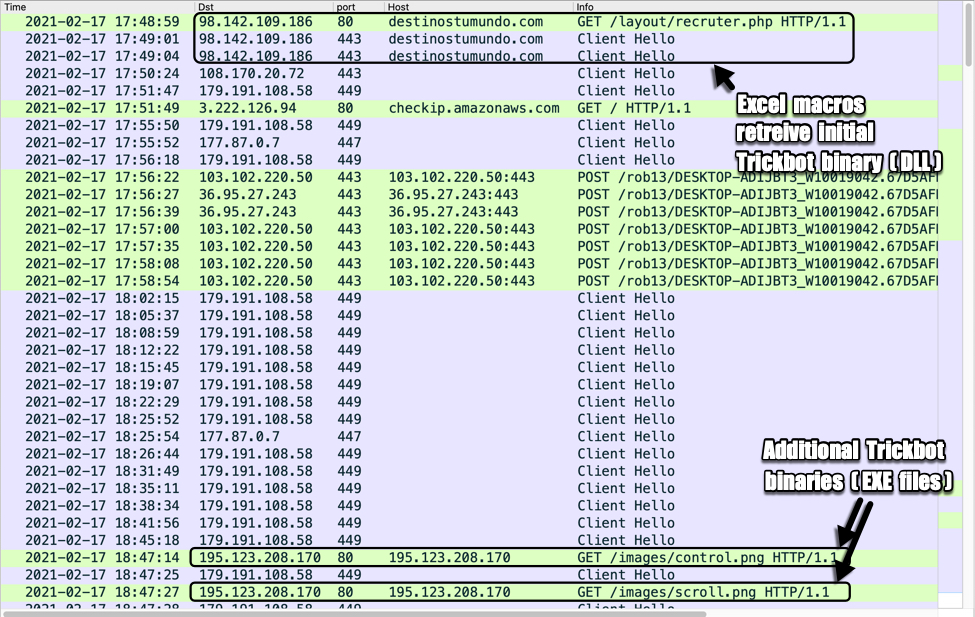
Shown above: Traffic from an infection filtered in Wireshark.
Forensics on an infected Windows host
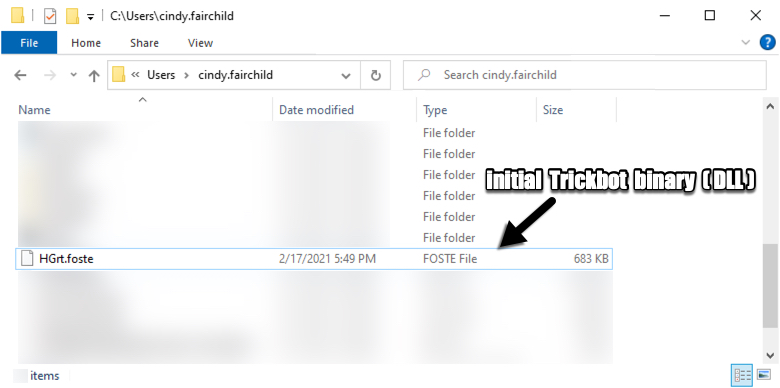
Shown above: Initial Trickbot binary retrieved by the Excel macro.
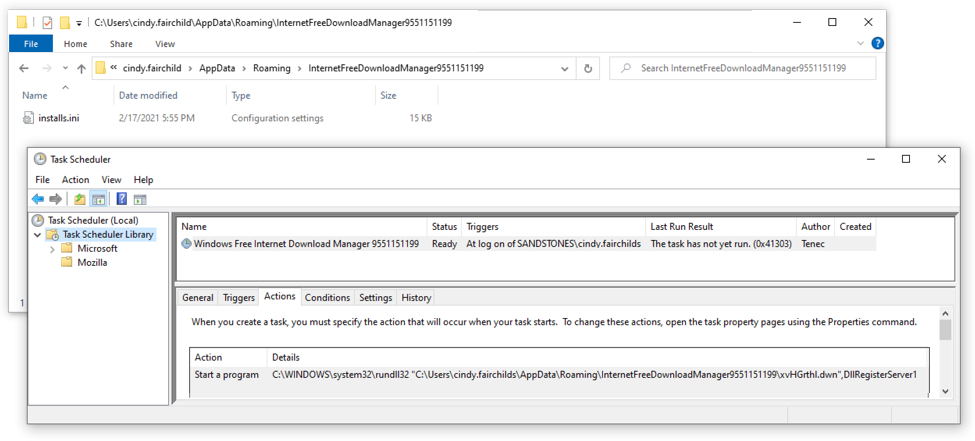
Shown above: Scheduled task for Trickbot.
In the above image (double-click on it to get a higher-resolution picture), you can see the Trickbot DLL is not where the scheduled task points to. When I restarted the infected host, it gave me an error saying it couldn't run the task. I've noticed this during the past several months from Trickbot infections that use a DLL file as the initial binary. Unfortunately, I don't know why this happens.
Indicators of Compromise (IOCs)
EXAMPLES OF SUBJECT LINES AND REPLY-TO ADDRESSES:
- Subject: DocuSign: Equipment # 1332
- Subject: DocuSign: Equipment # 9448
- Subject: DocuSign: Equipment # 9722
- Subject: DocuSign: Equipment # 12169
- Subject: DocuSign: Equipment # 23863
- Reply-To: Lease Consultants <cloying@docusign.net>
- Reply-To: Lease Consultants <dianoetic@docusign.net>
- Reply-To: Lease Consultants <modicum@docusign.net>
- Reply-To: Lease Consultants <omidyar@docusign.net>
- Reply-To: Lease Consultants <rumery@docusign.net>
- Note: Sending addresses may have been from email accounts that were compromised.
FILE HASHES FROM ATTACHMENTS SUBMITTED TO VIRUSTOTAL:
393bc60e292c3e24ab70c459ba1c595daaae68df94a75ebe571d3e75a0fe8109 DocuSign_484590053_1220881832.xls
64392b7c699791e4dddde1a1754d157c284dcc4d54e9cb8974ea661f6443ce86 DocuSign_463828509_1320623172.xls
713a539daad692c8e284718ad73c128128e8257b3c41b233d2f810717df873b7 DocuSign_2026401106_1090792446.xls
99316adbb0514f099d44bf8655486c2332eb5f3f821b80b2c0a6a85b652312e6 DocuSign_649568847_1582762946.xls
9bf4196e8fb7c4ac3be72f79f13697656145ee1cc93bb7c7a31d93ea75bbcae3 DocuSign_1264755469_604175183.xls
9fbbb8b4025b2e46429594b946d2ba74ce381e4c2968966e9a65ffd81791baa1 DocuSign_1283716068_336411873.xls
bc033032b6d2afcea2a07f4b5eb5de3137c9fc83c1302fe28a781137168884eb DocuSign_1993467225_1309843348.xls
bc47683422d0021b2b27b551d81058213fa4d000c544b617adf1bb7b94d5f4a9 DocuSign_558551337_1625623689.xls
f391892523950617f98dd08c5e1e8ffa58f8985f7527d5ffe735944db72a312f DocuSign_1237489607_947076939.xls
MALWARE FROM AN INFECTED WINDOWS HOST:
SHA256 hash: bc033032b6d2afcea2a07f4b5eb5de3137c9fc83c1302fe28a781137168884eb
- File size: 168,960 bytes
- File name: DocuSign_1993467225_1309843348.xls
- File description: Excel spreadsheet with macros for Trickbot gtag rob13
SHA256 hash: e1b67bd8b15bcd422fcbc74fa3b691c40c527ffedc951a6bb8e67ca257240d16
- File size: 698,880 bytes
- File location: hxxps://destinostumundo[.]com/layout/recruter.php
- File location: C:\Users\[username]\HGrt.foste
- File description: Initial Trickbot gtag rob13 binary (DLL file)
- Run method: rundll32.exe [file name],DllRegisterServer1
SHA256 hash: 24bd33f4ba457d77d796620a2cd4b7a3e38d63e2286fec752d898ab7c5204e4b
- File size: 864,256 bytes
- File location: hxxp://195.123.208[.]170/images/control.png
- File description: Follow-up Trickbot EXE file, gtag tot43
SHA256 hash: f0391039f888fb30566295365420868ac8539075e25a690ac4400a8bb91eb803
- File size: 864,256 bytes
- File location: hxxp://195.123.208[.]170/images/scroll.png
- File description: Follow-up Trickbot EXE file, gtag lib43
TRAFFIC TO RETRIEVE THE INITIAL TRICKBOT BINARY (A DLL FILE):
- 98.142.109[.]186 port 80 - destinostumundo[.]com - GET /layout/recruter.php
- 98.142.109[.]186 port 443 (HTTPS) - destinostumundo[.]com - GET /layout/recruter.php
POST-INFECTION TRAFFIC FOR TRICKBOT:
- 108.170.20[.]72 port 443 - HTTPS traffic
- 179.191.108[.]58 port 449 - HTTPS traffic
- port 80 - checkip.amazonaws.com - GET /
- 177.87.0[.]7 port 447 - HTTPS traffic
- 103.102.220[.]50 port 443 - 103.102.220[.]50:443 - POST /rob13/[string with host and infection info]/81/
- 36.95.27[.]243 port 443 - 36.95.27[.]243:443 - POST /rob13/[string with host and infection info]/81/
- 103.102.220[.]50 port 443 - 103.102.220[.]50:443 - POST /rob13/[string with host and infection info]/83/
- 36.95.27[.]243 port 443 - 36.95.27[.]243:443 - POST /rob13/[string with host and infection info]/90
TRAFFIC CAUSED BY TRICKBOT'S PROPAGATION MODULES TO RETRIEVE ADDITIONAL TRICKBOT BINARIES (RETURNED EXE FILES):
- 195.123.208[.]170 port 80 - 195.123.208[.]170 - GET /images/control.png
- 195.123.208[.]170 port 80 - 195.123.208[.]170 - GET /images/scroll.png
ATTEMPTED TCP CONNECTIONS CAUSED BY THE INFECTED WINDOWS HOST:
- 45.14.226[.]115 port 443
- 169.239.45[.]42 port 449
- 92.242.214[.]203 port 449
- 94.158.245[.]54 port 443
- 38.132.99[.]174 port 80
Final words
A pcap of the infection traffic and the associated malware can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
The new "LinkedInSecureMessage" ?
[This is a guest diary by JB Bowers - @cherokeejb_]
With all the talk of secure messenger applications lately, I bet you’d like to have just one more, right? In the past few weeks, we’ve noticed a new variant on a typical cred-stealer, in this case offering itself up as a new, secure messaging format used over the career website LinkedIn.

There’s only one problem with this… there is no such thing as a “LinkedIn Private Shared Document”.
Not Quite Secure
Victims will receive an ordinary message, likely from someone which they already are connected with. These are not from the more recent, unsolicited “InMail” feature, but a regular, internal “Message” on LinkedIn. There is nothing interesting about the message, although it contains a 3rd-party link, claiming to be a “LinkedInSecureMessage” which serves up the nice-looking pdf file shown above.
If you click “VIEW DOCUMENT,” it opens up a convincing LinkedIn login page. The example below was originally hosted at dev-jeniferng153(.)pantheonsite(.)io [1]:
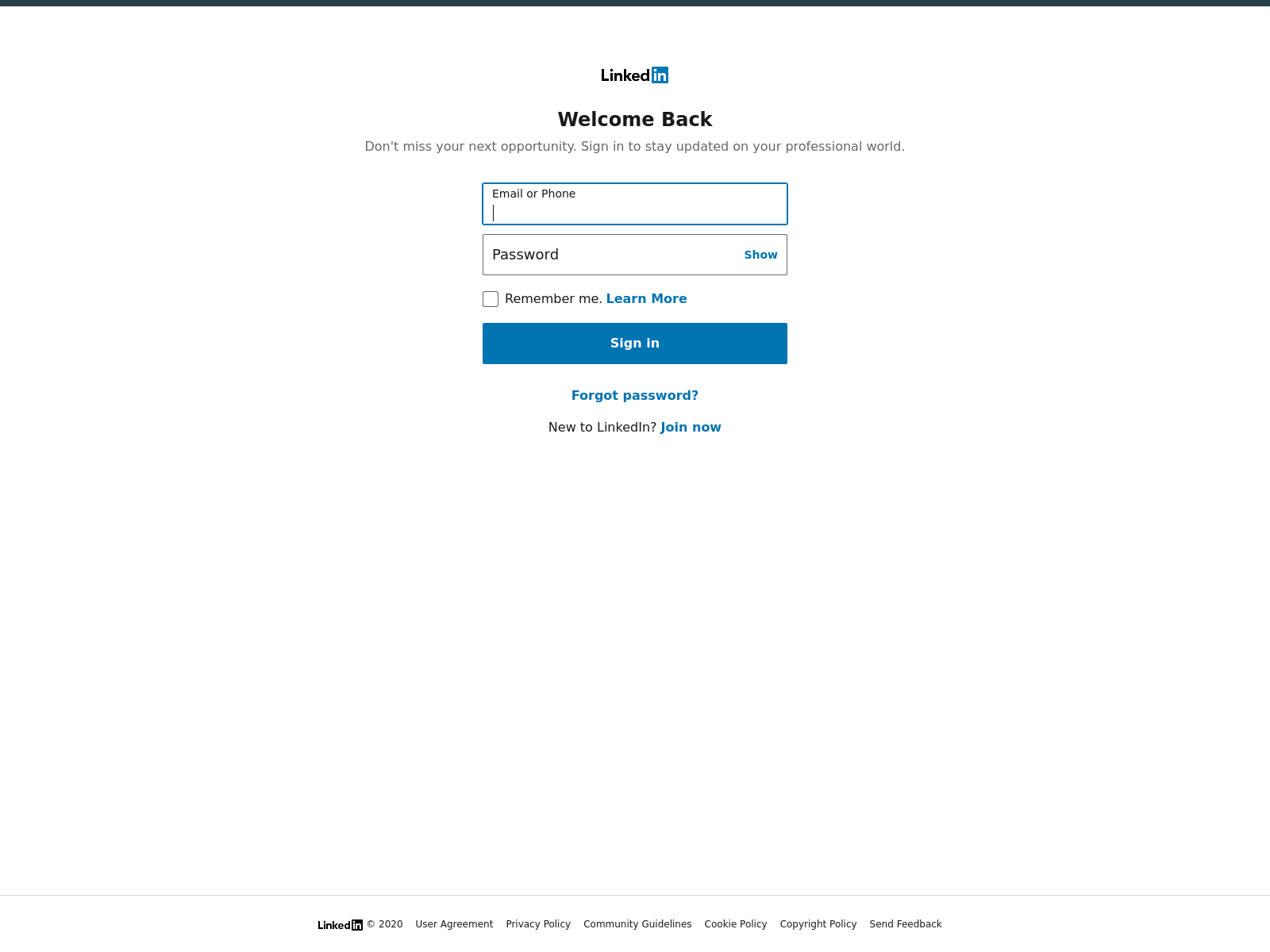
This page comes complete with links directing you back to the real LinkedIn.com site, and as well as a cookie called “test,” which is backdated to 1969.
A bit deeper
I wanted to look at a selection of these domains, so I used Urlquery to find similar domains, and as well, used VirusTotal to search for similar 2nd-stage documents. A common theme here is the use of websites that may also have legitimate work purposes, for example, appspot, firebase, and pantenonsite. The sites use major ASNs including Fastly, Google, and Microsoft, making basic network traffic analysis for the end-user also not so useful.
Here are a few example domains:
dev-jeniferng153.pantheonsite(.)io fluted-house-283121.uc.r.appspot(.)com dev-cloudvpds100.pantheonsite(.)io earnest-sandbox-295108.ey.r.appspot.com
As you can see after reviewing dozens of these domains, blocking the domains, or even some type of regular expression based on known URLs is not going to get very far. If you’re not able to block these sites or their corresponding IP addresses altogether, to prevent attacks like this you’ll need to focus on the human element, and of course enforcing good security practices, like avoiding password reuse across websites.
I found several similar samples on Virus Total, for example sha1 f5884fd520f302654ab0a165a74b9645a31f4379 - Japanbankdocument (1).pdf.[2] All the files I examined used a variety of other generic or known company names, followed by the word “document,” and they had similar metadata in the pdf files. This file is currently flagged as malicious by only 1/62 vendors reporting to VirusTotal (Microsoft alone flags it as a malicious, phishing document).
A 2nd document sampled, currently scores a 0 on VT, with just the very last part of the file name, “document.pdf.”. I used Didier’s Pdf Analysis tools pdfid and pdf-parser [3] to look at samples of the documents; below are the highlights:
PDFiD 0.2.7
PDF Header: %PDF-1.7
obj 50
endobj 50
stream 6
endstream 6...
xref 1
trailer 1
startxref 1
/Page 1...
/XFA 0
/URI 2 ← Here we can see there is a URI present.
/Colors > 2^24 0
>>
obj 50 0 ← Using pdf-parser we find the next-stage phishing link in pdf object 50
Type:
Referencing:
<<
/Flags 0
/S /URI
/URI (hxxps://dev-jeniferng153.pantheonsite(.)io/document(.)zip)
>>
The real danger here is when the campaign targets high-value targets, using their accounts to target more and more of their LinkedIn contacts, or pivot into stealing credentials which would create more access for the adversary, for example, a Microsoft 0365 credential-stealer, like what was shown in a similar, 0365 Phish [4].
Again the main advantage here for the attackers is by compromising accounts, they are provided with a way to reach out convincingly to colleagues, friends, and family of the victims. This provides yet another way an adversary can make the most out of a hacked web server, by hosting countless domains like these, for phishing.
The Human Element
If you see any more LinkedIn messages like this, of course, you’ll want to let that person know out of band that their account has been compromised and that they should update their LinkedIn password, as well as report the abuse to LinkedIn. They’ll need to let all their LinkedIn contacts know their account has been used by someone else. If they have unfortunately used their LinkedIn password on any other sites, those passwords should also be changed as well.
While not very complicated in terms of the malware or tactics used, this is certainly the type of campaign you’ll want to watch out for, and train your colleagues to watch out for, specifically. Since the message is also based on LinkedIn, you may of course want to block, or forbid with policy, the use of social media at work altogether. This choice may not be a good culture fit with many organizations these days, although campaigns like this provide a good reason to consider encouraging employees not to use social media or other personal websites on their work computers.
There are some other general tips for avoiding similar phishing emails on LinkedIn’s page for Identifying Phishing, and also on their page for Recognizing and Reporting Scams [5,6].
JB Bowers
@cherokeejb_
References:
[1] https://urlscan.io/result/fc3ce0f8-f327-44d0-841a-a216d5f782db/
[2] https://www.virustotal.com/gui/file/4f09b9b73008dd1e7c074f5c1b9687ce41aea29006300f4617c1a894bd8864e6/detection
[3] https://blog.didierstevens.com/programs/pdf-tools/
[4] https://www.linkedin.com/pulse/case-phishy-inmail-vasyl-gello/
[5] https://safety.linkedin.com/identifying-abuse#Browsing
[6] https://www.linkedin.com/help/linkedin/answer/56325


Comments