Phishing asking recipients not to report abuse
It can be a little disheartening to deal with well-prepared phishing attacks every day, since one can easily see how even users who are fully “security-aware” could fall for some them. The messages don’t even have to be too complex to be believable. For example, a message containing seemingly innocuous text and a link that points to legitimate, well-known domain hosting an application that is affected by open redirect vulnerability (I’m looking at you, Google[1], though – to be fair – you’re hardly alone[2]) can look quite trustworthy, if no obvious red flags are present.
Fortunately, most phishing messages in the wild are easy to spot, even if anti-spam and anti-phishing filters on e-mail gateways don’t stop them. We usually tend not to give these run of the mill messages a second look, since they are not too dangerous under most circumstances. However, if we do, some of them might prove to be at least somewhat interesting, even if it is only due to a mistake on the part of their author. One such easy to spot message that made me smile was forwarded to me this week by one of my Hungarian colleagues, but before we get to it, however, let’s set the stage a little.
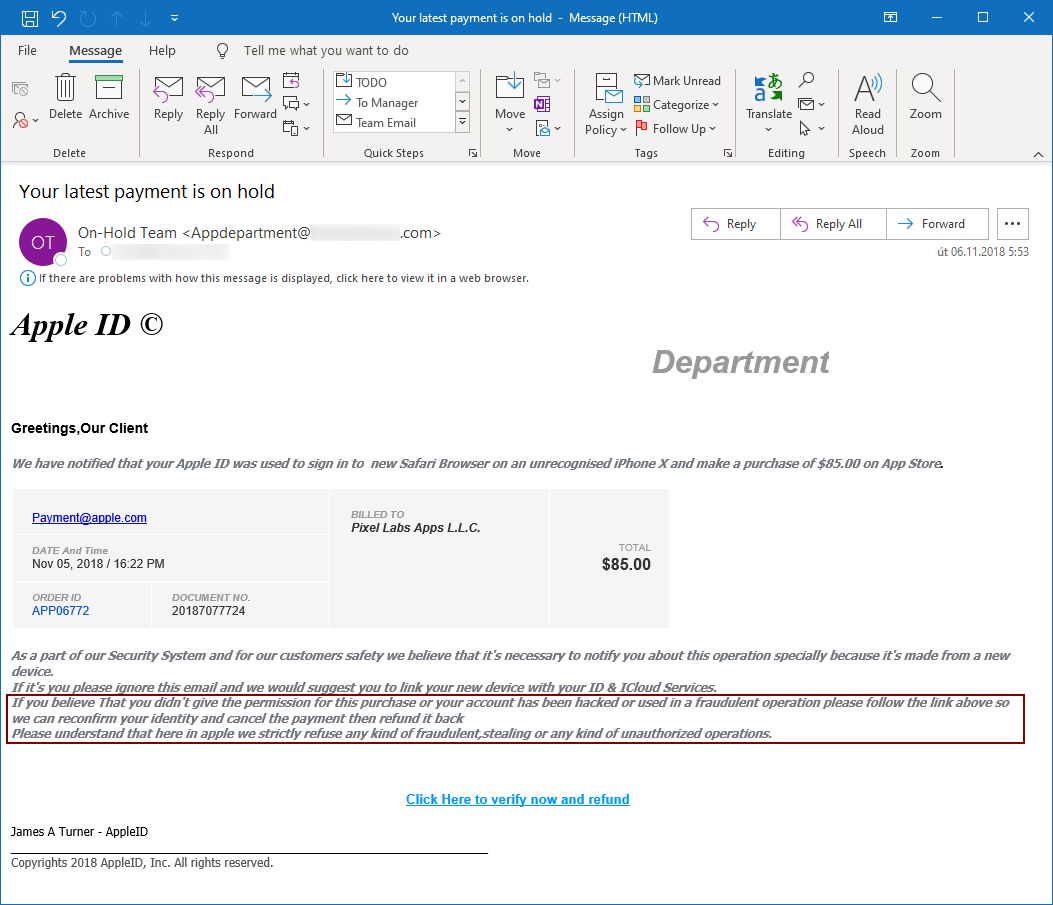
It is not unusual for phishing authors to use lures along the lines of “if you believe that this message was sent to you in error, please let us know by clicking here”, “if you were not the one to request the transfer of funds, you may cancel it on this link” or “if you believe that your account was used in a fraudulent operation, let us know immediately”, as the following example shows.
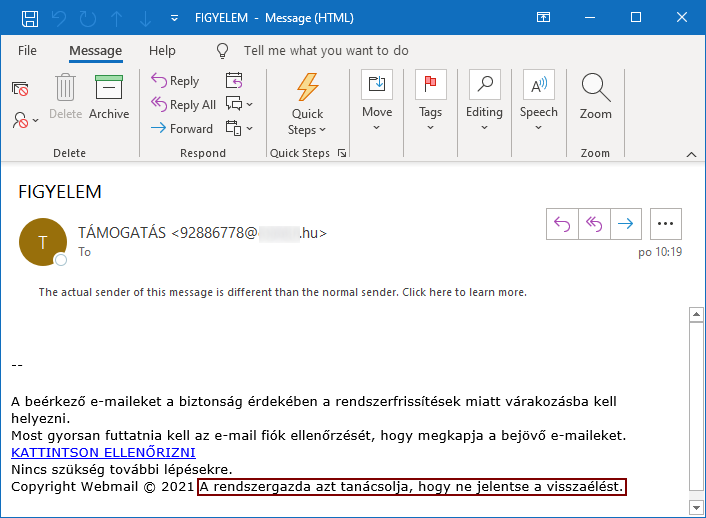
It is quite out of the ordinary to find the complete opposite of these sentiments – i.e. “do not report abuse” – in a phishing e-mail. This was, however, indeed the case with the message I was sent…
As you may see, it is in Hungarian, and according to a translation by Google Translate, it basically says “you need to run a check on your e-mail using this link to be able to receive further messages”. This would be hardly unusual, however the last sentence next to the copyright comes down to “Your system administrator has advised you not to report abuse”.
I don’t dare guess whether this less than usual instruction was the result of an error in automatic translation from another language, an unsuccessful attempt at making the message appear more trustworthy or whether the author of the e-mail included it in the hope that users really wouldn’t report the phishing, if they saw through it… In either case, it certainly wouldn’t add to the credibility of the message, even if the link didn’t lead to a very generic page containing a form requesting e-mail, username and password.
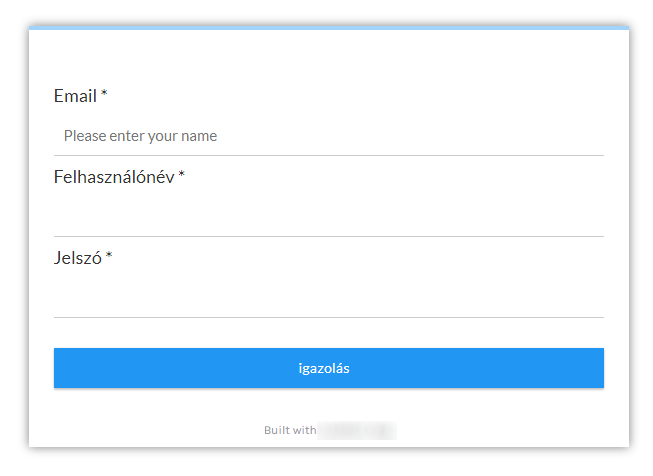
As this message shows, even looking at some of the less-than-stellar phishing attempts can sometimes be interesting… and after dealing with more sophisticated attacks, it can be good for morale as well.
[1] https://isc.sans.edu/forums/diary/Open+redirects+and+why+Phishers+love+them/27542/
[2] https://isc.sans.edu/forums/diary/Guest+Diary+Open+Redirect+A+Small+But+Very+Common+Vulnerability/25276/


Comments