Unsolicited DNS Queries
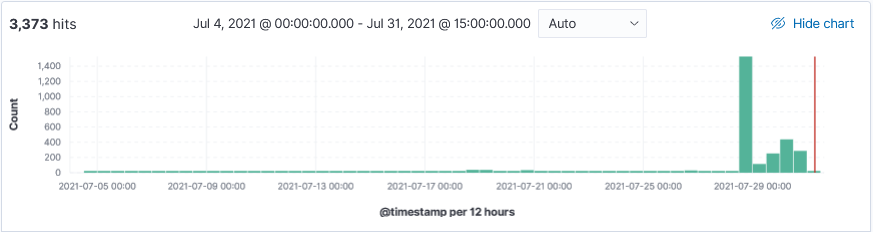
This week I started seeing more DNS related activity being identified by Threatintel and that got me curious. While reviewing my logs, I noticed that Wednesday and Thursday had an unusual spike for many inbound unsolicited DNS queries for the domain census.gov.
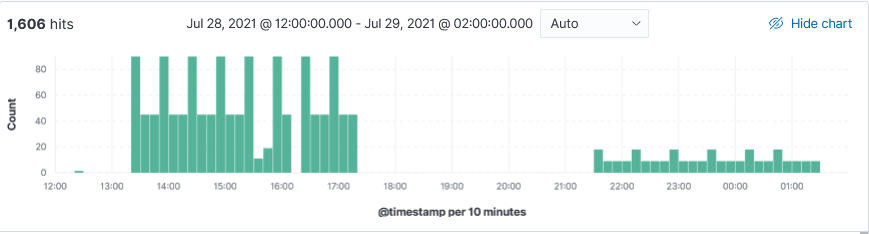
Wednesday and Thursday, in a period of 24 hours, a total of 1606 queries was received for domain census.gov. The two IPs 37.49.230.173 (1335 requests) was the first set of inbound DNS queries followed by IP 162.253.128.82 (271 requests). IP 162.253.128.82 also sent 272 requests for domain pizzaseo.com yesterday. DNS amplification attack?
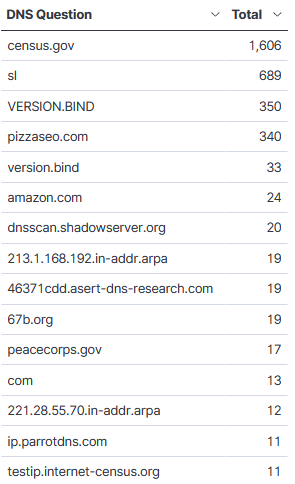
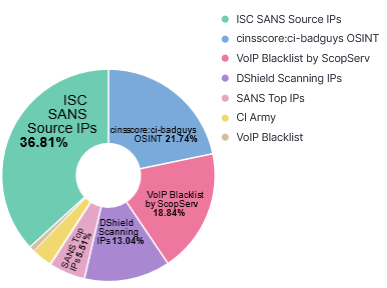
There used to be a time when seeing unsolicited queries to identify vulnerable DNS Bind version was very common. A review of my logs for the month of July contained many other domains including various combination of VERSION.BIND (upper/lower case). This is the top 15 DNS questions asked for this month with the top Threatintel associated with the IPs asking the query:
Indicators - Top 10 IPs
37.49.230.173 -> census.gov, sl
162.253.128.82 -> census.gov, pizzaseo.com, sl
185.53.90.85 -> VERSION.BIND, sl
122.5.207.27
45.61.185.201
37.49.229.228
88.80.186.137
207.244.251.235
209.141.59.224
89.248.165.164
Have you noticed an increase in unsolicited DNS queries?
[1] https://www.abuseipdb.com/check/37.49.230.173
[2] https://www.abuseipdb.com/check/162.253.128.82
[3] https://www.iana.org/assignments/dns-parameters/dns-parameters.xhtml
[4] https://us-cert.cisa.gov/ncas/alerts/TA13-088A
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments