obama224 distribution Qakbot tries .vhd (virtual hard disk) images
Introduction
Qakbot (also called Qbot) is a long-running malware family that has seen wide-spread distribution through malicious spam (malspam) in recent years. During an infection, Qakbot performs different functions as an information stealer, backdoor, and malware downloader.
Metadata tags in the malware code are tied to a specific distribution campaign. The "obama" series distribution tag includes a 3-digit suffix, and it currently represents thread-hijacked emails with attachments for HTML smuggling. When opened, the attached HTML file presents a password-protected zip archive to download, and the web page displays the password.
In recent months, password-protected zip archives for Qakbot have contained disk images using the .iso file extension. However, on Thursday 2022-12-01, zip archives for obama224 Qakbot contained images using the .vhd file extension.
VHD files have been used by other criminal groups to distribute malware, but this is the first I remember seeing them for obama-series Qakbot.
In Microsoft Windows, ISO files can easily be mounted by any normal user account. However, VHD images require an administrative Windows account. Because of this, normal user accounts in an Active Directory (AD) environment cannot mount VHD files on a Windows client without administrative login credentials. VHD images can easily mount on stand-alone Windows 10 or 11 hosts that use administrative accounts.
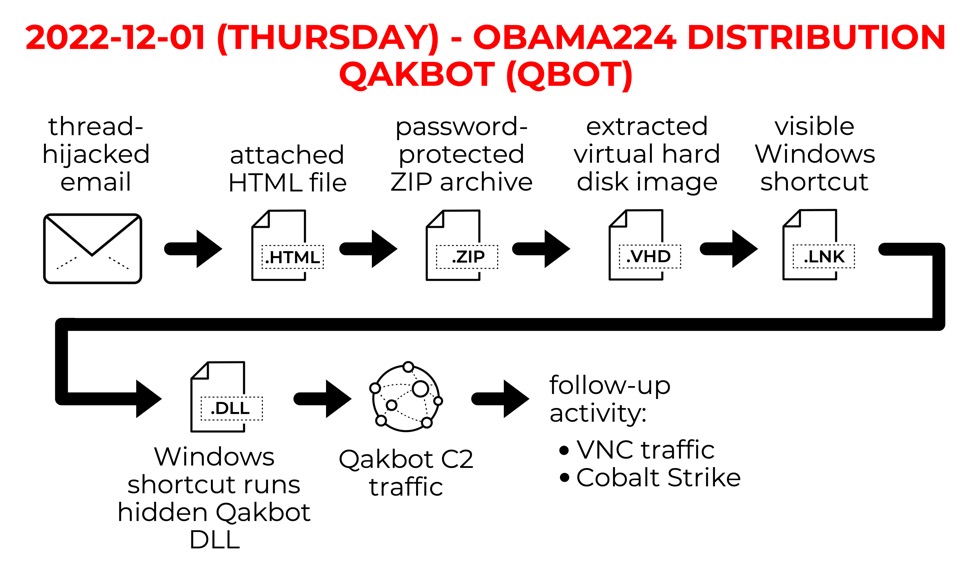
Shown above: Chain of events for obama224 distribution Qakbot activity.
Qakbot infections occasionally lead to VNC activity. Qakbot also leads to Cobalt Strike if the infected host is part of an AD environment. This was the case as recently as Monday 2022-11-28 with a BB08 distribution Qakbot infection.
Let's review an infection in my lab environment, using screenshots from each step of the process.
Step by Step Screenshots
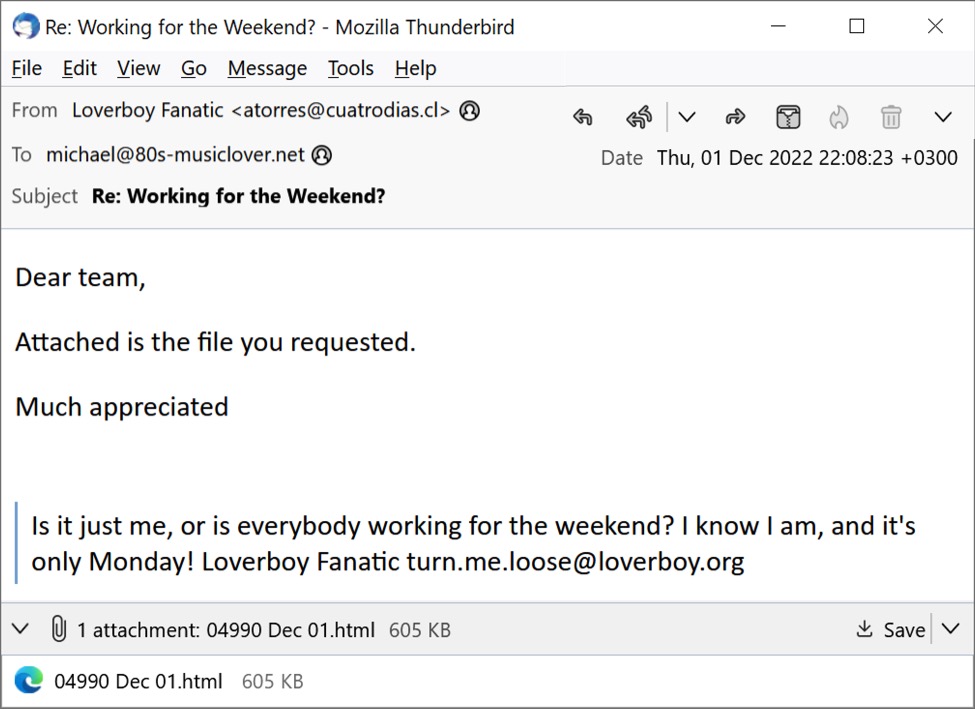
Shown above: Thread-hijacked email with an attachment for HTML smuggling opened in Thunderbird.
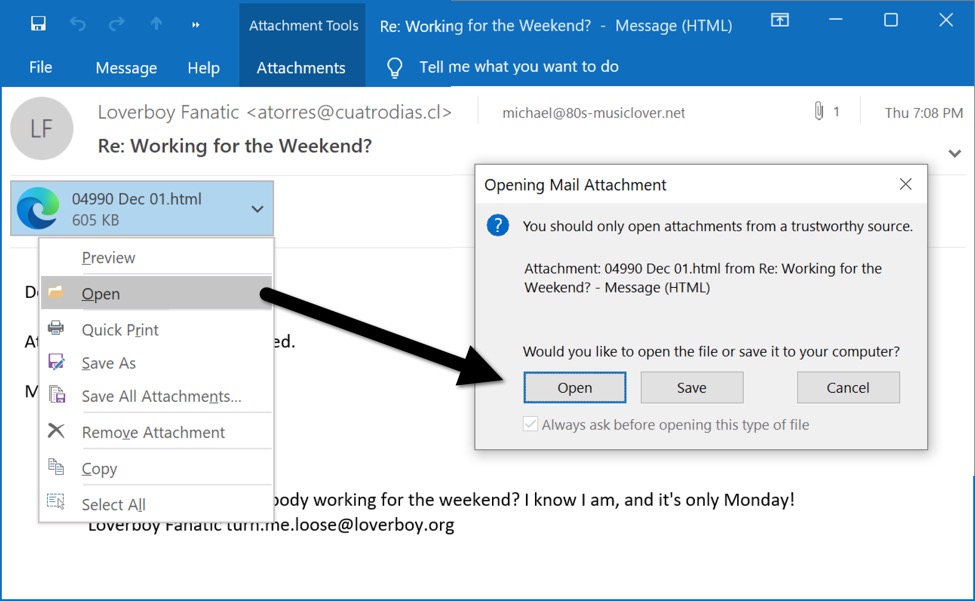
Shown above: The same email in Microsoft Outlook can open the HTML attachment in Microsoft Edge.
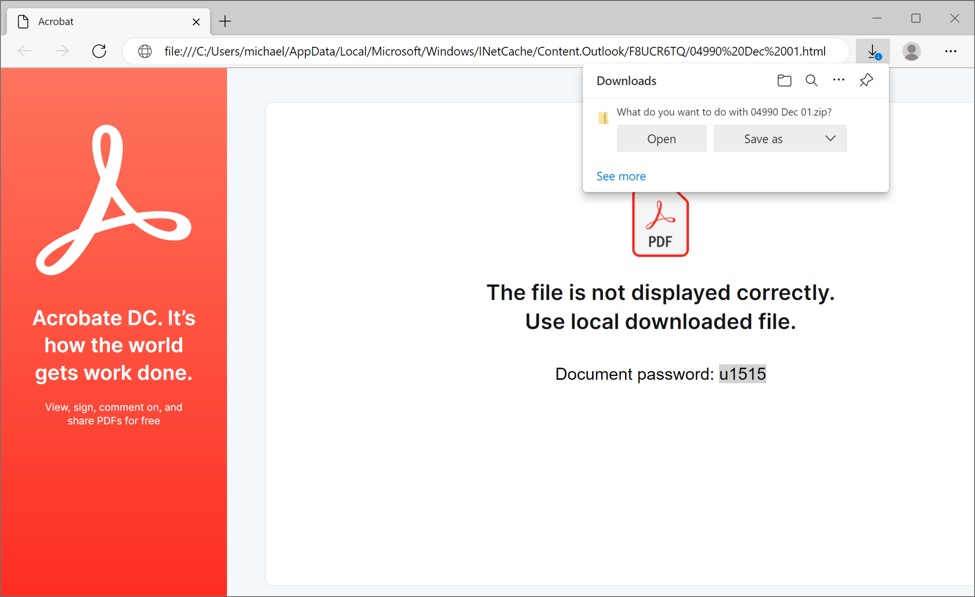
Shown above: Opening the HTML attachment Microsoft Edge presents a password-protected zip archive and shows u1515 as its password.
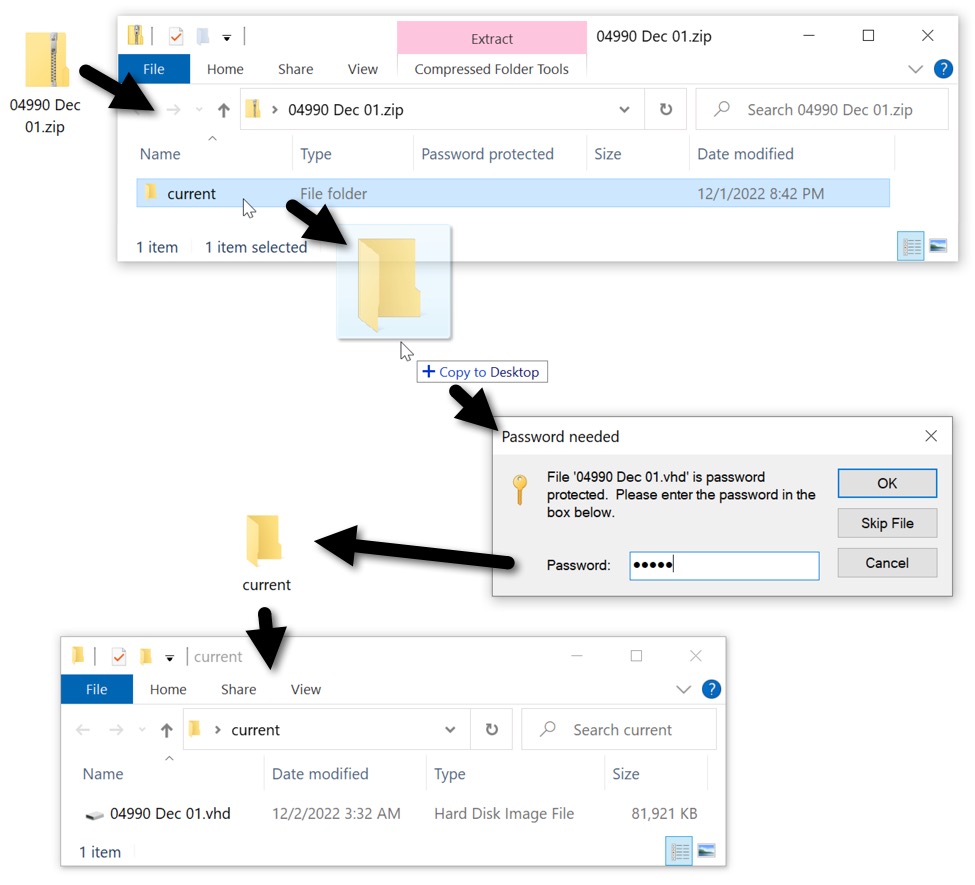
Shown above: Using the password to click our way to the VHD image.
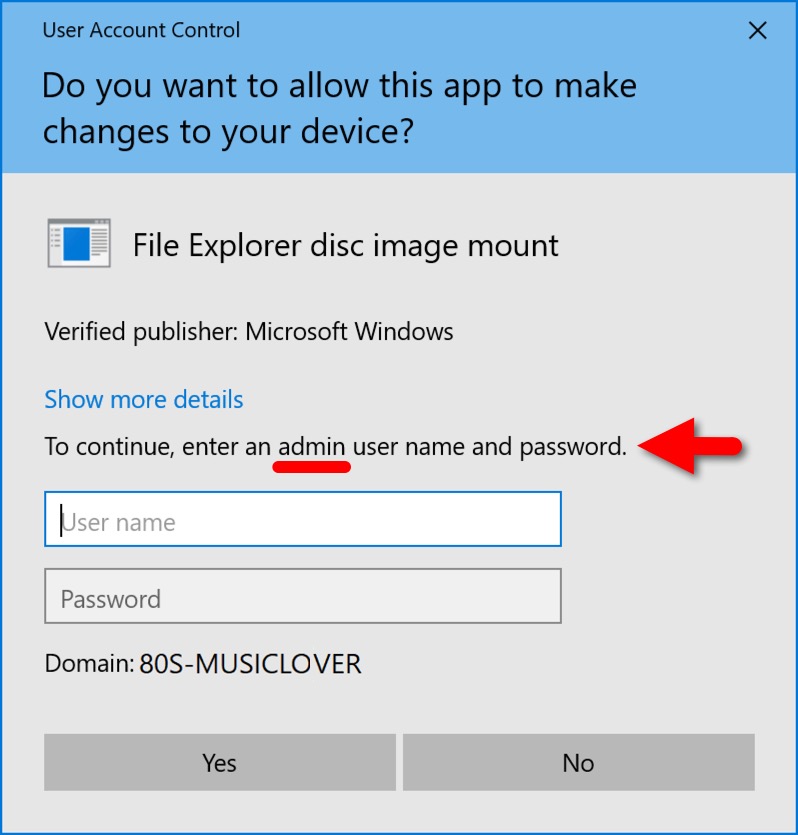
Shown above: In an AD environment, you need administrative permissions to mount the VHD image.
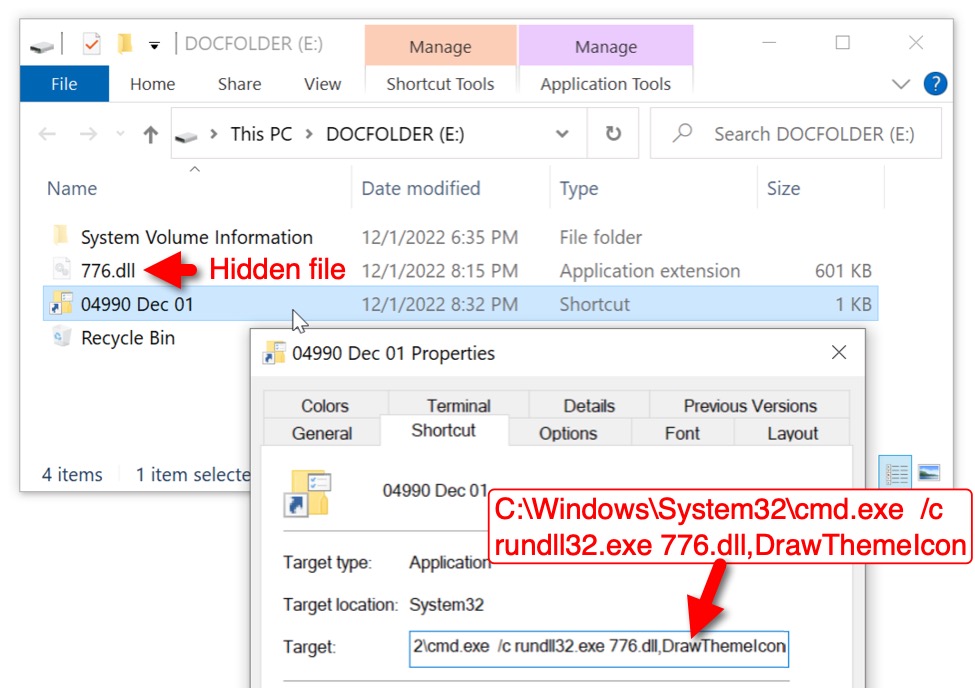
Shown above: Contents of the VHD image.
I used the domain administrator login credentials to mount the VHD image. It mounted as the next available drive letter, using DOCFOLDER as the newly-mounted disk's name. Double-clicking the visible Windows shortcut runs a hidden Qakbot DLL. The shortcut uses a command prompt (cmd.exe) to run rundll32.exe [filename],DrawThemeIcon as its target.
While Qakbot is quite dangerous, this type of infection requires a victim with administrative access willing to click through various notifications and warnings before an infection occurs.
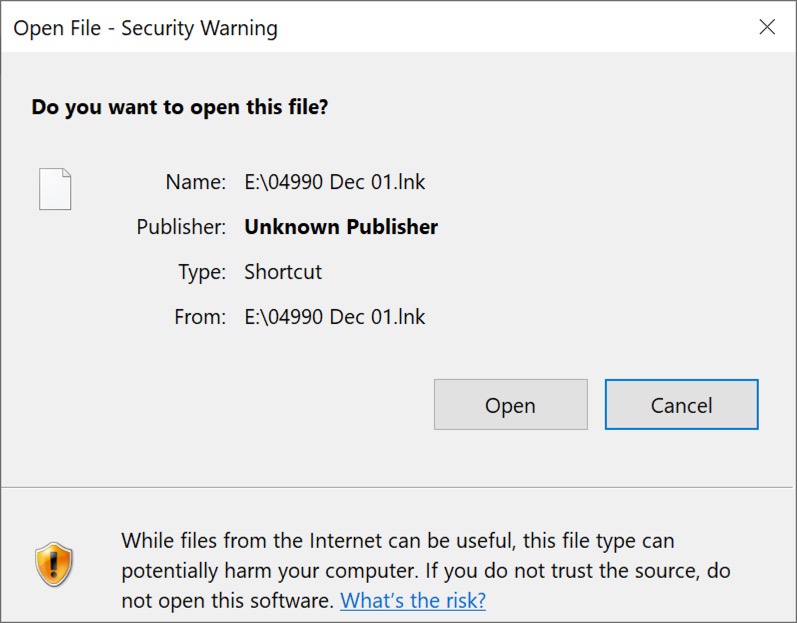
Shown above: The last warning I clicked through to infect my lab host.
Final Words
While this campaign is clever, it uses VHD images that require administrative access to successfully infect a Windows host. How effective this is in an AD environment? How many organizations allow administrative privileges for all user accounts? Unfortunately, poor security practices can overcome some of the most effective security measures. Human nature is why malware like Qakbot remains successful, despite the increased security of default Windows settings.
13 examples of malspam from Thursday 2022-12-01, along with the associated HTML files, VHD images, and Qakbot DLL files are available here.
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments