New year, old tricks: Hunting for CircleCI configuration files
I have written before about attackers looking for exposed configuration files. Configuration files often include credentials or other sensitive information.Today, I noticed some scans for a files called "/.circleci/config.yml". Given the recent breach at CircleCI, I dug in a bit deeper.
Spoiler alert: This is not related to the breach. Sometimes organizations lose credentials all by themselves without any third party help.
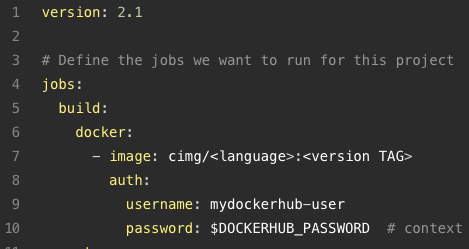
This configu file is indeed "interesting" if it can be found. For the pre-cloud native people around here: Compare it to a Makefile. It describes how to build a certain project using CircleCI, and it may contain credentials as needed. For example, see the example from https://circleci.com/docs/sample-config/ :
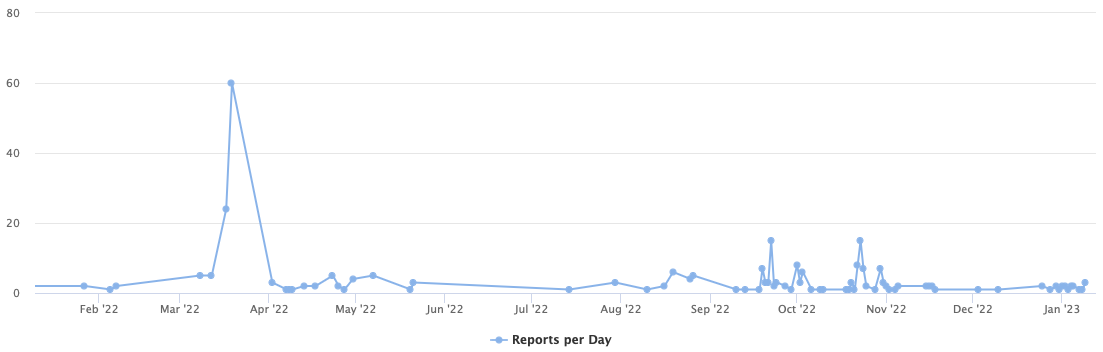
Scans for the file have been ongoing at a low level for a while now
Including scans for these related URLs:
/.circleci/ssh-config
/.circleci/config.yml
/.circleci/circle.yml
/config/database.yml.circleci
/.circleci/
Currently, these 2 IPs are searching for .circleci/config.yml
139.99.120.65 and 139.99.123.180 .
Both are located at OVH, a cloud provider known for harboring many compromised systems. But otherwise, the IPs are not very remarkable. The IPs are scanning for various other configuration files and vulnerabilities. For example:
/wp-config.php.back
/php_info.php
/.env.bak
/.config
/config.json
(42 similar once today alone)
In short: If you leave your configuration files in your document root exposed: They will be found!
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments