The .zip gTLD: Risks and Opportunities
About ten years ago, ICANN started the "gTLD" program. "Generic TLDs" allows various brands to register their own trademark as a TLD. Instead of "google.com", you now can have ".google"! Applying for a gTLD isn't cheap, and success isn't guaranteed. But since its inception, dozens of new gTLDs have been approved and started to be used [1].
The reputation of these new gTLDs has been somewhat mixed. On one end, several very cheap TLDs emerged from the process that are often abused. For example, .xyz or .top are often used for cheap "throw-away" domains. But we also had some large companies, for example, Google, use it (try: domains.google). Google submitted applications for several different gTLDs [2].
One of the more interesting gTLDs Google obtained is ".zip". This gTLD was approved in 2014, and has not seen much use since then. The current zone file for ".zip" contains only 1230 names. To access the zone files for many of the gTLDs, ICANN operates the "Centralized Zone Data Service" at czds.icann.org.
So what is the danger here?
Earlier I saw this tweet by @vxunderground
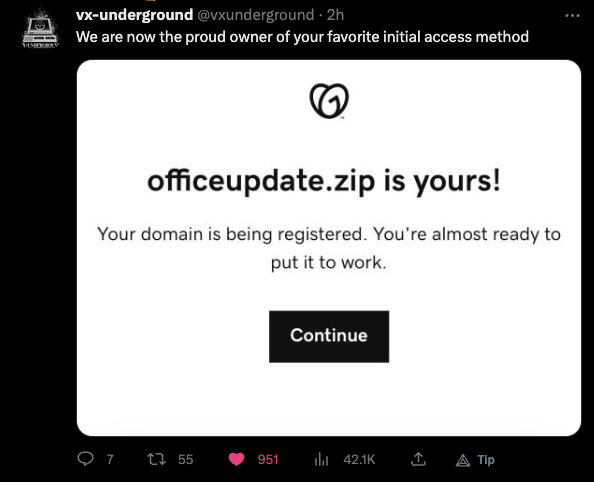
And indeed, the domain has been registered and appears functional. Whois states a creation date of today.
% dig NS officeupdate.zip +short
ns71.domaincontrol.com.
ns72.domaincontrol.com.
You may see how this could be a risk for your organization as it may lead to some interesting phishing sites. It offers some creative opportunities to distribute malware. Just to clarify: I consider @vxunderground "good guys." They distribute malware, but for good reasons (just ask them for the password ;-) ).
So I checked the current zone file from CZDS, and found some other interesting domains:
update.zip - May 5th 2023
installer.zip - May 10th 2023
I could not find any official announcement, but it looks like registrations for .zip started about a month ago.
Another issue with the .zip gTLD is that software may now automatically attach hyperlinks to ZIP file names that show up in the text. The result could be that ZIP file names leak as DNS queries as you hover over them. I have not yet observed this behavior, but it may be possible as .zip domains become more well-known. Let me know if you see anything like this. This behavior has been problematic, not just for .zip domains.
Given the low "real world" usage of .zip domains, it may be best to block access to them until it is clear if it will be useful.
And if you would like to check the domains yourself, I created a quick snapshot of .zip domains with NS records attached to them. See https://isc.sans.edu/diaryimages/zipdomains.txt
Update: I found the press release from Google announcing the availability of these new domains [3]. According to the press release, they started to become available on May 3rd, but the price dropped on May 10th, which explains the increased interest these last couple of days.
[1] https://newgtlds.icann.org/en/about/program
[2] https://icannwiki.org/Google#New_gTLDs
[3] https://blog.google/products/registry/8-new-top-level-domains-for-dads-grads-tech/
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments