Apple Releases iOS/iPadOS 16.6.1, macOS 13.5.2, watchOS 9.6.2 fixing two zeroday vulnerabilities
| macOS Ventura 13.5.2 | iOS 16.6.1 and iPadOS 16.6.1 | watchOS 9.6.2 |
|---|---|---|
| CVE-2023-41064 [critical] ChatGPT-CVSS: 9.8 *** EXPLOITED *** ImageIO A buffer overflow issue was addressed with improved memory handling. Processing a maliciously crafted image may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. |
||
| x | x | |
| CVE-2023-41061 [moderate] ChatGPT-CVSS: 9.8 *** EXPLOITED *** Wallet A validation issue was addressed with improved logic. A maliciously crafted attachment may result in arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. |
||
| x | x | |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Fleezeware/Scareware Advertised via Facebook Tags; Available in Apple App Store
Scareware, software advertised via fake malware messages, or Fleezeware, software providing questionable subscription services, keeps ending up in Apple's app store, bypassing various controls Apple uses to restrict software available to its users. Part of the difficulty in proactively recognizing this type of software is that these apps are often benign. The issue with this software is that it doesn't do much, if anything at all. The program becomes more obvious in how the software is advertised.
The latest example is "Synapse Security," published by Pas Borisa UAB. The software's main feature appears to be a VPN service. The software is advertised via Facebook by "tagging" users. Once a user has been "tagged", the post may also be visible in the feed of friends of the tagged user. The posts used have deceptive clickbait content:
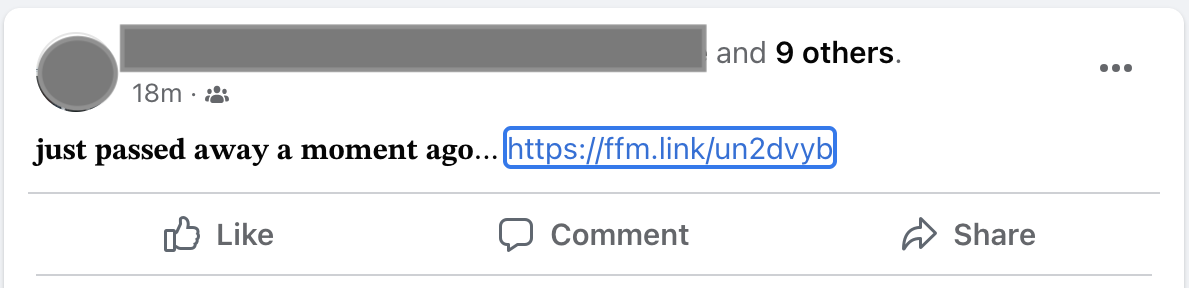
Interestingly, the link results in a TLS error if it is clicked on in a desktop browser. The server appears to perform some TLS fingerprinting. Curl is also not allowed:
% openssl s_client --connect ffm.link:443
CONNECTED(00000005)
00074457F87F0000:error:0A0003E8:SSL routines:ssl3_read_bytes:reason(1000):ssl/record/rec_layer_s3.c:1586:SSL alert number 0
But my iPad was able to connect without problem, and received the typical "scareware" page:
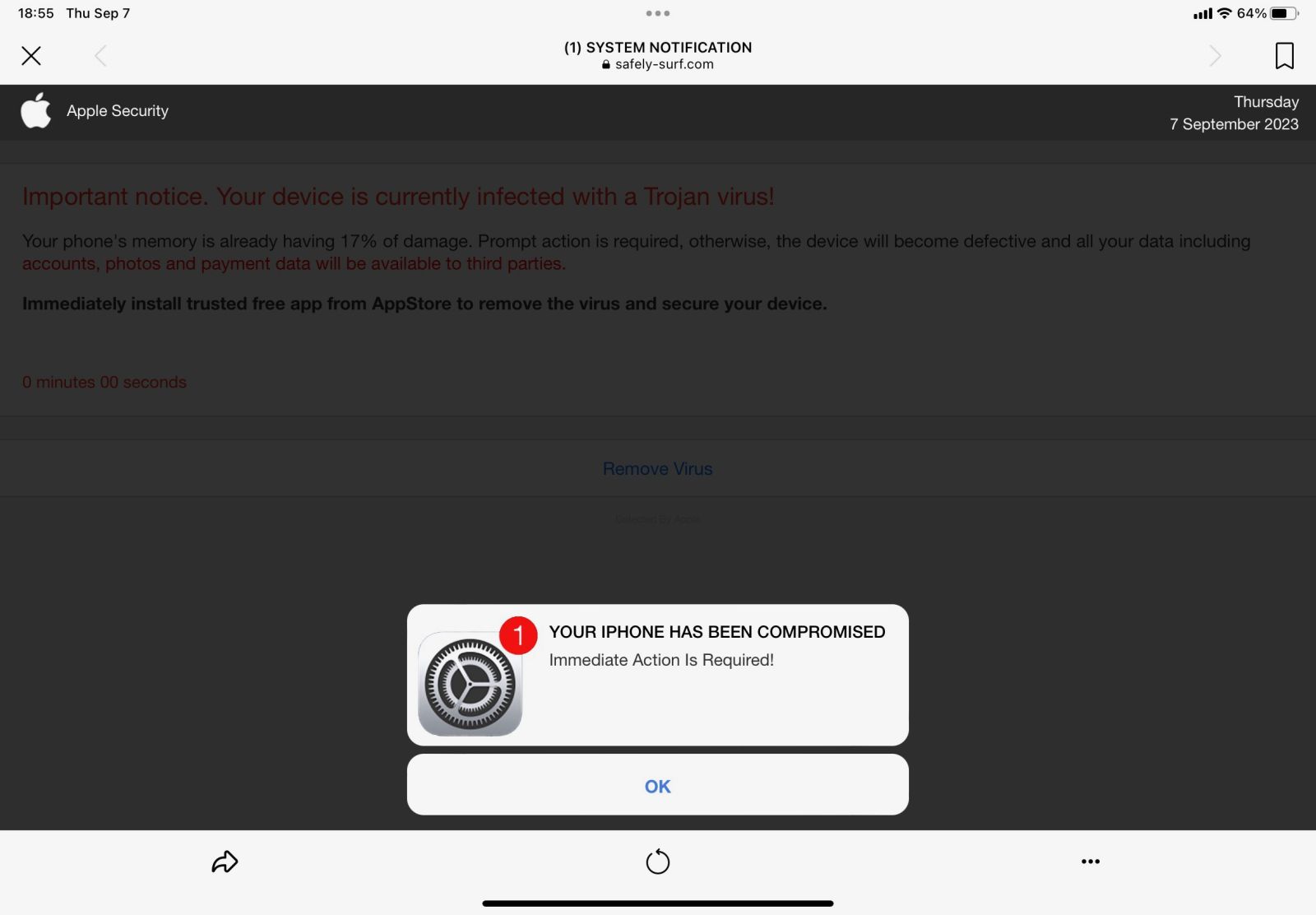
Clicking on OK leads to the Apple Appstore page for "Synape Security", which describes itself as "The pulse of online protection." The app is luckily not popular enough to have received sufficient reviews. It offers a number of subscription options, starting with a one-week option for $8.99. Overall, the price appears to be higher than other VPN offers from well-known companies. In addition to the VPN service, the application offers ad blocking.
I briefly installed the application without paying for premium services. It configured an IPSEC VPN and appeared to work, but I have not had the time to check its effectiveness. Given the deceptive advertising, I do not expect anything useful.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|



Comments