Apple Releases MacOS Sonoma Including Numerous Security Patches
As expected, Apple today released macOS Sonoma (14.0). This update, in addition to new features, provides patches for about 60 different vulnerabilities. Older MacOS versions received updates addressing these vulnerabilities last week with the MacOS 13.6. When these updates were released, the security content was not made public, but with today's release of macOS 14, Apple revealed the security content of these prior updates.
The table below includes the updates released on September 21st and today (26th). It does not include CVSS scores. My ChatGPT-driven script to calculate them had too many issues with this set of updates to be helpful.
Also note that some of the "Exploited" vulnerabilities receives specific updates not included in this table.
| macOS Sonoma 14 | Safari 16.6.1 | iOS 17.0.1 and iPadOS 17.0.1 | iOS 16.7 and iPadOS 16.7 | watchOS 10.0.1 | watchOS 9.6.3 | macOS Ventura 13.6 | macOS Monterey 12.7 |
|---|---|---|---|---|---|---|---|
| CVE-2023-40384 [important] Airport A permissions issue was addressed with improved redaction of sensitive information. An app may be able to read sensitive location information |
|||||||
| x | |||||||
| CVE-2023-32377 [important] AMD A buffer overflow issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | |||||||
| CVE-2023-38615 [important] AMD The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | |||||||
| CVE-2023-40448 [moderate] App Store The issue was addressed with improved handling of protocols. A remote attacker may be able to break out of Web Content sandbox |
|||||||
| x | x | ||||||
| CVE-2023-40432 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | |||||||
| CVE-2023-40399 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to disclose kernel memory |
|||||||
| x | |||||||
| CVE-2023-40410 [important] Apple Neural Engine An out-of-bounds read was addressed with improved input validation. An app may be able to disclose kernel memory |
|||||||
| x | x | x | |||||
| CVE-2023-32361 [important] AuthKit The issue was addressed with improved handling of caches. An app may be able to access user-sensitive data |
|||||||
| x | |||||||
| CVE-2023-35984 [moderate] Bluetooth The issue was addressed with improved checks. An attacker in physical proximity can cause a limited out of bounds write |
|||||||
| x | |||||||
| CVE-2023-40402 [moderate] Bluetooth A permissions issue was addressed with additional restrictions. An app may be able to access sensitive user data |
|||||||
| x | |||||||
| CVE-2023-40426 [moderate] Bluetooth A permissions issue was addressed with additional restrictions. An app may be able to bypass certain Privacy preferences |
|||||||
| x | |||||||
| CVE-2023-41065 [important] bootp A privacy issue was addressed with improved private data redaction for log entries. An app may be able to read sensitive location information |
|||||||
| x | |||||||
| CVE-2023-29497 [moderate] Calendar A privacy issue was addressed with improved handling of temporary files. An app may be able to access calendar data saved to a temporary directory |
|||||||
| x | |||||||
| CVE-2023-38596 [moderate] CFNetwork The issue was addressed with improved handling of protocols. An app may fail to enforce App Transport Security |
|||||||
| x | |||||||
| CVE-2023-40406 [moderate] ColorSync The issue was addressed with improved checks. An app may be able to read arbitrary files |
|||||||
| x | x | x | |||||
| CVE-2023-40420 [moderate] CoreAnimation The issue was addressed with improved memory handling. Processing web content may lead to a denial-of-service |
|||||||
| x | x | x | x | ||||
| CVE-2023-40407 [moderate] CUPS The issue was addressed with improved bounds checks. A remote attacker may be able to cause a denial-of-service |
|||||||
| x | |||||||
| CVE-2023-32396 [important] Dev Tools This issue was addressed with improved checks. An app may be able to gain elevated privileges |
|||||||
| x | |||||||
| CVE-2023-41980 [important] FileProvider A permissions issue was addressed with additional restrictions. An app may be able to bypass Privacy preferences |
|||||||
| x | |||||||
| CVE-2023-40395 [moderate] Game Center The issue was addressed with improved handling of caches. An app may be able to access contacts |
|||||||
| x | x | x | |||||
| CVE-2023-40391 [important] GPU Drivers The issue was addressed with improved memory handling. An app may be able to disclose kernel memory |
|||||||
| x | |||||||
| CVE-2023-40441 [moderate] GPU Drivers A resource exhaustion issue was addressed with improved input validation. Processing web content may lead to a denial-of-service |
|||||||
| x | |||||||
| CVE-2023-23495 [moderate] iCloud A permissions issue was addressed with improved redaction of sensitive information. An app may be able to access sensitive user data |
|||||||
| x | |||||||
| CVE-2023-40434 [moderate] iCloud Photo Library A configuration issue was addressed with additional restrictions. An app may be able to access a user's Photos Library |
|||||||
| x | |||||||
| CVE-2023-38586 [moderate] Image Capture An access issue was addressed with additional sandbox restrictions. A sandboxed process may be able to circumvent sandbox restrictions |
|||||||
| x | |||||||
| CVE-2023-40436 [moderate] IOAcceleratorFamily The issue was addressed with improved bounds checks. An attacker may be able to cause unexpected system termination or read kernel memory |
|||||||
| x | |||||||
| CVE-2023-41995 [important] Kernel A use-after-free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | |||||||
| CVE-2023-41981 [moderate] Kernel The issue was addressed with improved memory handling. An attacker that has already achieved kernel code execution may be able to bypass kernel memory mitigations |
|||||||
| x | x | x | |||||
| CVE-2023-41984 [important] Kernel The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | ||||
| CVE-2023-40429 [moderate] Kernel A permissions issue was addressed with improved validation. An app may be able to access sensitive user data |
|||||||
| x | |||||||
| CVE-2023-41067 [important] LaunchServices A logic issue was addressed with improved checks. An app may bypass Gatekeeper checks |
|||||||
| x | |||||||
| CVE-2023-40400 [critical] libpcap This issue was addressed with improved checks. A remote user may cause an unexpected app termination or arbitrary code execution |
|||||||
| x | |||||||
| CVE-2023-40454 [moderate] libxpc A permissions issue was addressed with additional restrictions. An app may be able to delete files for which it does not have permission |
|||||||
| x | x | x | x | ||||
| CVE-2023-41073 [moderate] libxpc An authorization issue was addressed with improved state management. An app may be able to access protected user data |
|||||||
| x | x | x | x | ||||
| CVE-2023-40403 [moderate] libxslt The issue was addressed with improved memory handling. Processing web content may disclose sensitive information |
|||||||
| x | x | x | x | ||||
| CVE-2023-40427 [important] Maps The issue was addressed with improved handling of caches. An app may be able to read sensitive location information |
|||||||
| x | x | x | |||||
| CVE-2023-32421 [moderate] Messages A privacy issue was addressed with improved handling of temporary files. An app may be able to observe unprotected user data |
|||||||
| x | |||||||
| CVE-2023-41986 [important] Music The issue was addressed with improved checks. An app may be able to modify protected parts of the file system |
|||||||
| x | |||||||
| CVE-2023-40455 [moderate] NetFSFramework A permissions issue was addressed with additional restrictions. A sandboxed process may be able to circumvent sandbox restrictions |
|||||||
| x | |||||||
| CVE-2023-40386 [moderate] Notes A privacy issue was addressed with improved handling of temporary files. An app may be able to access Notes attachments |
|||||||
| x | |||||||
| CVE-2023-37448 [important] Power Management A lock screen issue was addressed with improved state management. A user may be able to view restricted content from the lock screen |
|||||||
| x | |||||||
| CVE-2023-41063 [important] Pro Res The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | |||||
| CVE-2023-40422 [important] QuartzCore The issue was addressed with improved memory handling. An app may be able to cause a denial-of-service |
|||||||
| x | |||||||
| CVE-2023-39233 [moderate] Safari The issue was addressed with improved checks. Processing web content may disclose sensitive information |
|||||||
| x | |||||||
| CVE-2023-40388 [moderate] Safari A privacy issue was addressed with improved handling of temporary files. Safari may save photos to an unprotected location |
|||||||
| x | |||||||
| CVE-2023-35990 [moderate] Safari The issue was addressed with improved checks. An app may be able to identify what other apps a user has installed |
|||||||
| x | x | ||||||
| CVE-2023-40417 [moderate] Safari A window management issue was addressed with improved state management. Visiting a website that frames malicious content may lead to UI spoofing |
|||||||
| x | |||||||
| CVE-2023-40452 [moderate] Sandbox The issue was addressed with improved bounds checks. An app may be able to overwrite arbitrary files |
|||||||
| x | x | x | |||||
| CVE-2023-41078 [moderate] Screen Sharing An authorization issue was addressed with improved state management. An app may be able to bypass certain Privacy preferences |
|||||||
| x | |||||||
| CVE-2023-41070 [moderate] Share Sheet A logic issue was addressed with improved checks. An app may be able to access sensitive data logged when a user shares a link |
|||||||
| x | x | x | |||||
| CVE-2023-40541 [moderate] Shortcuts This issue was addressed by adding an additional prompt for user consent. A shortcut may output sensitive user data without consent |
|||||||
| x | |||||||
| CVE-2023-41079 [important] Shortcuts The issue was addressed with improved permissions logic. An app may be able to bypass Privacy preferences |
|||||||
| x | |||||||
| CVE-2023-41968 [moderate] Disk Management This issue was addressed with improved validation of symlinks. An app may be able to read arbitrary files |
|||||||
| x | x | x | |||||
| CVE-2023-40450 [important] System Preferences The issue was addressed with improved checks. An app may bypass Gatekeeper checks |
|||||||
| x | |||||||
| CVE-2023-40424 [important] TCC The issue was addressed with improved checks. An app may be able to access user-sensitive data |
|||||||
| x | |||||||
| CVE-2023-39434 [critical] WebKit A use-after-free issue was addressed with improved memory management. Processing web content may lead to arbitrary code execution |
|||||||
| x | |||||||
| CVE-2023-41074 [critical] WebKit The issue was addressed with improved checks. Processing web content may lead to arbitrary code execution |
|||||||
| x | |||||||
| CVE-2023-35074 [critical] WebKit The issue was addressed with improved memory handling. Processing web content may lead to arbitrary code execution |
|||||||
| x | |||||||
| CVE-2023-41993 [critical] *** EXPLOITED *** WebKit The issue was addressed with improved checks. Processing web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited against versions of iOS before iOS 16.7. |
|||||||
| x | x | x | x | ||||
| CVE-2023-41066 [moderate] Windows Server An authentication issue was addressed with improved state management. An app may be able to unexpectedly leak a user's credentials from secure text fields |
|||||||
| x | |||||||
| CVE-2023-41979 [important] XProtectFramework A race condition was addressed with improved locking. An app may be able to modify protected parts of the file system |
|||||||
| x | |||||||
| CVE-2023-41992 [moderate] *** EXPLOITED *** Kernel The issue was addressed with improved checks. A local attacker may be able to elevate their privileges. Apple is aware of a report that this issue may have been actively exploited against versions of iOS before iOS 16.7. |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-41991 [important] *** EXPLOITED *** Security A certificate validation issue was addressed. A malicious app may be able to bypass signature validation. Apple is aware of a report that this issue may have been actively exploited against versions of iOS before iOS 16.7. |
|||||||
| x | x | x | x | x | |||
| CVE-2023-41232 [important] Biometric Authentication An out-of-bounds read was addressed with improved bounds checking. An app may be able to disclose kernel memory |
|||||||
| x | x | x | |||||
| CVE-2023-41068 [important] MobileStorageMounter An access issue was addressed with improved access restrictions. A user may be able to elevate privileges |
|||||||
| x | |||||||
| CVE-2023-40412 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | ||||||
| CVE-2023-40409 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | ||||||
| CVE-2023-41071 [important] Apple Neural Engine A use-after-free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | |||||||
| CVE-2023-41996 [moderate] Sandbox The issue was addressed with improved checks. Apps that fail verification checks may still launch |
|||||||
| x | |||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
A new spin on the ZeroFont phishing technique
Last week, I came across an interesting phishing e-mail, in which a text written in a font with zero-pixel size was used in quite a novel way.
The technique of embedding text with zero font size in phishing e-mails to break up text written in normal, visible way, in order to make detection of suspicious messages by automated means more difficult has been with us for quite some time now. In fact, all the way back in 2018, the team at Avanan coined the term “ZeroFont Phishing”[1] for it.
Nevertheless, the “invisible” text in the e-mail which was delivered to our handler e-mail address last Friday did not serve the usual purpose – it wasn’t intended to hinder automated scanners from identifying the message as potentially fraudulent/malicious, but instead to make the message appear more trustworthy to the recipient.
Before we get to how it did this, let us quickly set the stage.
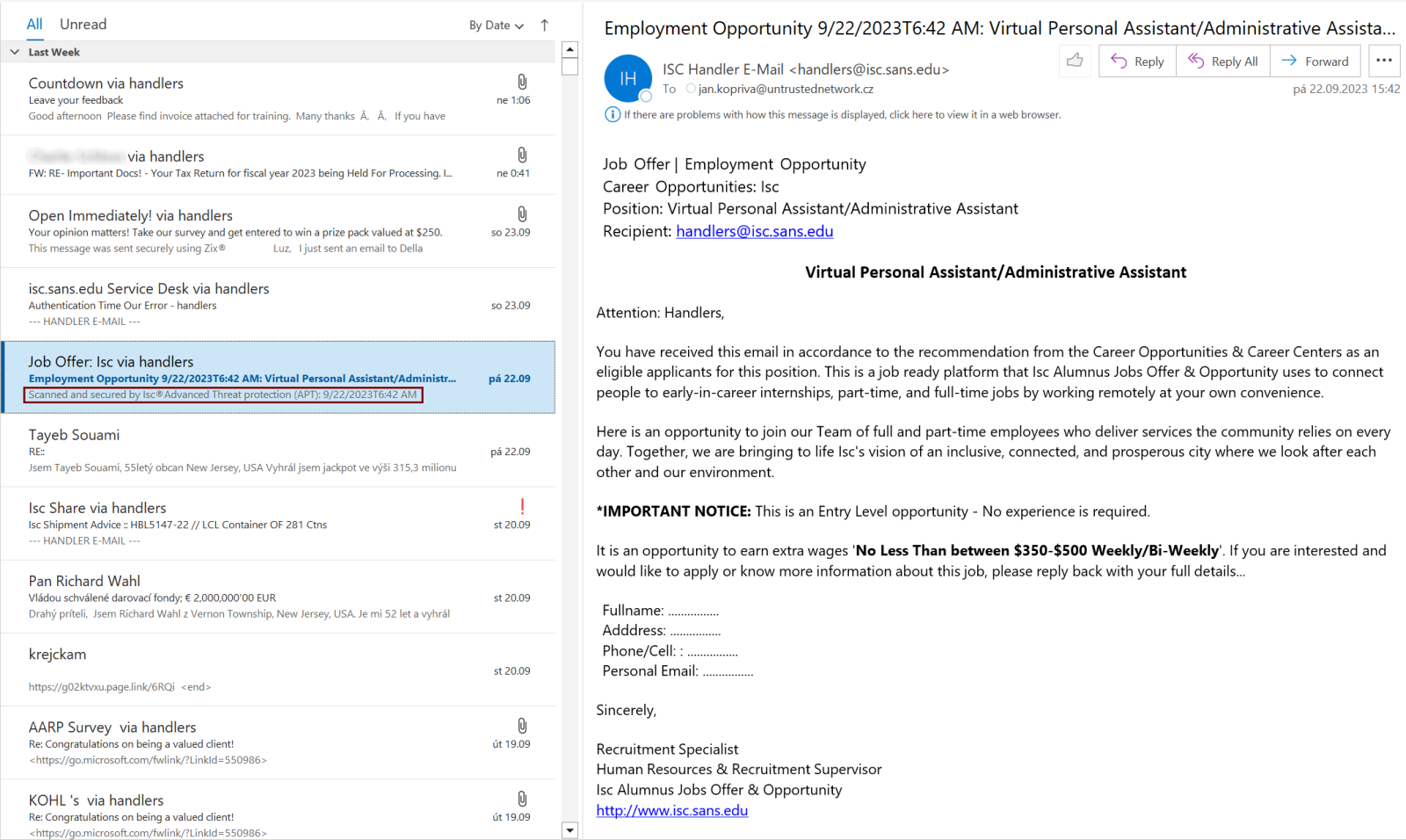
Modern e-mail clients commonly display received e-mail messages in a layout containing two side-by-side windows – one showing the list of received (or sent, drafted, etc.) messages and the other showing the body of a selected message. As you may see in the following image, Microsoft Outlook displays the name of a sender, its subject and the beginning of a text of each message in the left window, as do many other MUAs.
The fact that e-mail clients display the beginning of the text of a message in the listing of folder content is quite important for us.
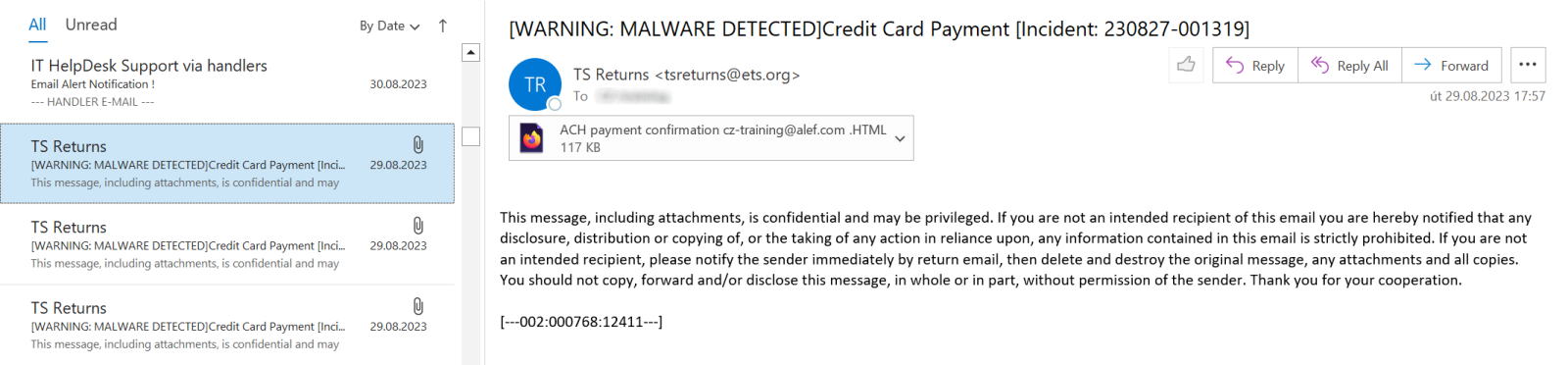
This is because although the e-mail, to which I alluded, looked like a run-of-the-mill phishing when one looked only at the body of the message…
…the text, which was displayed in the “listing pane” in Outlook for the message, was somewhat unexpected.
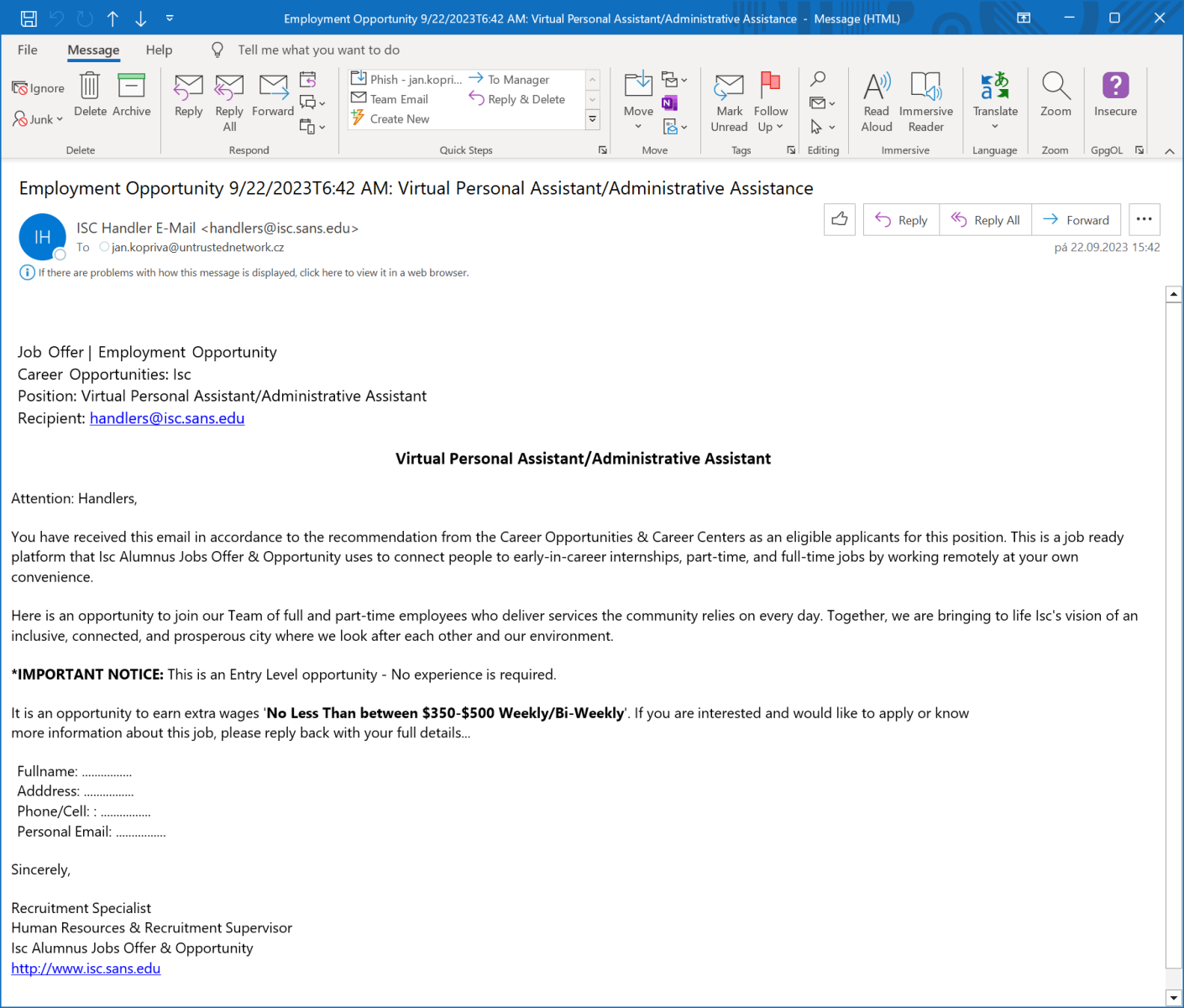
This was because instead of the visible beginning of the message (i.e., “Job Offer | Employment Opportunity”), the text “Scanned and secured by Isc®Advanced Threat protection (APT): 9/22/2023T6:42 AM” was displayed in the listing.
As you have undoubtedly already surmised, this was because this text was contained at the beginning of the message and was set to be 0 pixels in size (as well as to be transparent and hidden). You may see this in the following excerpt from the HTML code of the body of the message.
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<title> Employment Opportunity 9/22/2023T6:42 AM: Virtual Personal Assistant/Administrative Assistance</title>
</head>
<body>
<span style="mso-hide:all;display:none !important;font-size:0;max-height:0;line-height:0;visibility:hidden;overflow:hidden;opacity:0;color:transparent;height:0;width:0;">
Scanned and secured by IscAdvanced Threat protection (APT): 9/22/2023T6:42 AM
</span>
<FONT size=4>
<FONT color=#ffffff>
<FONT color=#000000 size=3 face="Segoe UI"> <P align=left>
<FONT size=4>
<FONT color=#ffffff>
<FONT color=#000000 size=3 face="Segoe UI">
<FONT color=#ffffff>
*
</FONT>
Job
<FONT color=#ffffff>
*
</FONT>
Offer |
<FONT color=#ffffff>
*
</FONT>
Employment
<FONT color=#ffffff>
*
</FONT>
Opportunity
<BR>
It seems that Outlook (and likely other MUAs) displays any text which is present at the beginning of a message in the listing view, even if it has zero font size, which can unfortunately be (mis)used in the way we've shown.
While I wouldn’t be surprised if this technique has been used before, this was the first time I came across it. And since I couldn’t find any previous write-ups of it, I decided to share it here.
Although it is a technique with only minor impact, it might still confuse some recipients into believing that a phishing message is trustworthy – especially if the text displayed in the “listing window” was well chosen. It is, in any case, one more small addition to the threat actor toolbox which may be used to create more effective phishing campaigns, and it is therefore certainly good for us – as defenders – to be aware of it…
Furthermore, since it is currently being used “in the wild”, it might not be a bad idea to mention it in any phishing-oriented security awareness courses.
[1] https://www.avanan.com/blog/zerofont-phishing-attack
-----------
Jan Kopriva
@jk0pr
Nettles Consulting


Comments