CVE-2023-1389: A New Means to Expand Botnets
[This is a Guest Diary by Jonah Latimer, an ISC intern as part of the SANS.edu BACS program]
Introduction
I am currently pursuing a Bachelor degree from SANS Technology Institute, and part of the requirements for graduation is to complete a 20 week internship with the SANS Internet Storm Center. During this internship I created a honeypot using an Amazon EC2 instance, and overserved and reported on seven different attacks that were leveraged against it. The following blog post is going to dive into one of the vulnerabilities that I came across.
Summary
My honeypot was attacked by an actor trying to exploit a fairly new vulnerability (CVE-2023-1389) that was publicly released in March of this year. This particular exploit is found in vulnerable TP-Link Archer routers, and has been primarily been exploited by threat actors as a means to add devices to their botnets which are used for DDoS attacks. I will be going over the vulnerability, and how to protect yourself from it.
Initial Discovery
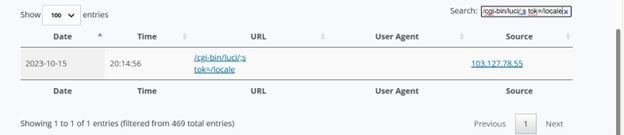
I was looking through my weblogs from October and stumbled upon the URL /cgi-bin/luci/;s tok=/locale from IP 103.127.78.55 which I hadn’t seen before. I looked around on google a little bit and found out that this request is related to the vulnerability (CVE-2023-1389).
What is CVE-2023-1389?
CVE-2023-1389 is a command injection vulnerability (Mitre ATT&CK T1055) [1] with an 8.8 CVSS severity rating that affects TP- Archer AX21 (AX1800) firmware versions before 1.1.4 Build 20230219. The command injection vulnerability is found in the country form of the /cgi-bin/luci;stok=/locale endpoint on the web management interface. Specifically, the country parameter of the write operation was not sanitized before being used in a call to popen(), allowing an unauthenticated attacker to inject commands, which would be run as root, with a simple POST request. [2]
Analysis
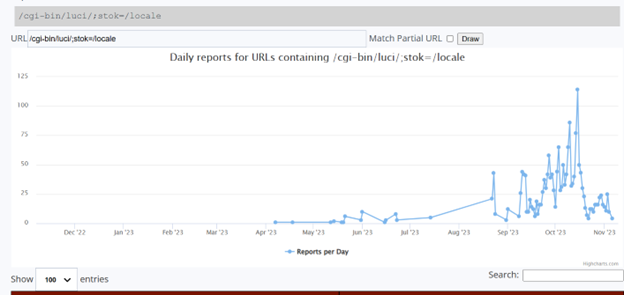
CVE-2023-1389 was publicly released in March of this year and first showed up on the ISC honeypots on 04-07-2023 but didn’t really start showing up more frequently until around September/October.
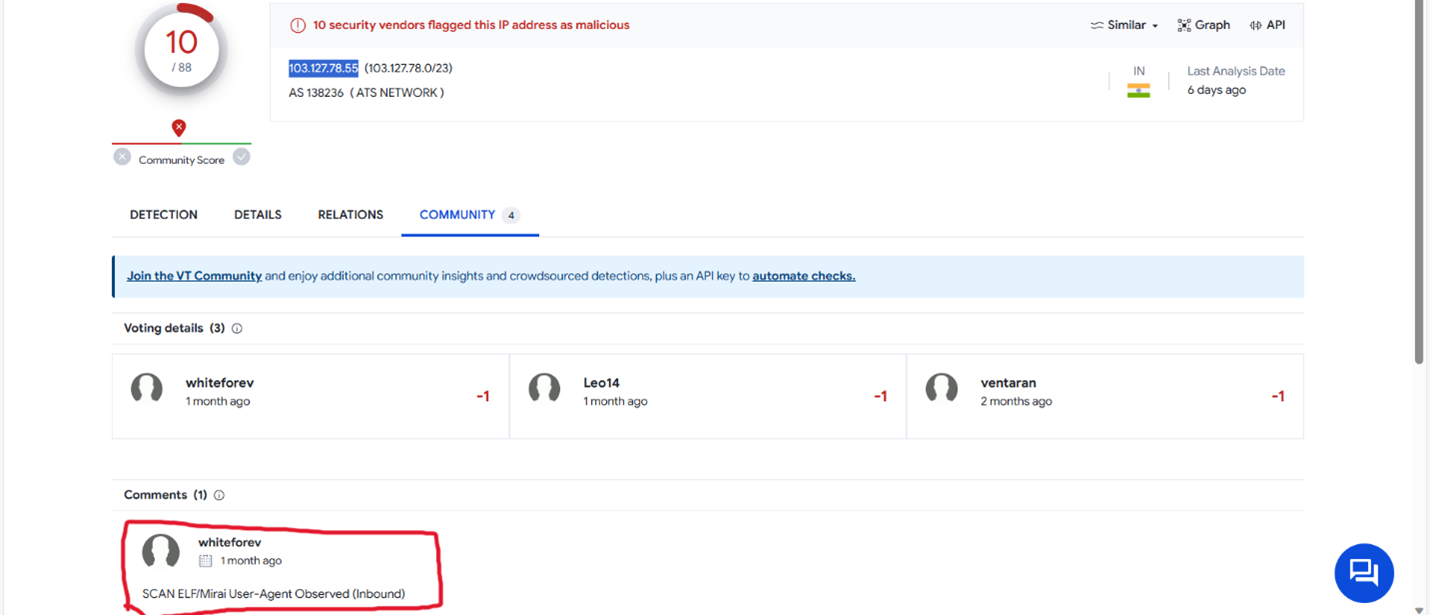
The attack on my honeypot came from an IP address of 103.127.78.55. I searched VirusTotal for the attacker IP of 103.127.78.55 and seen “SCAN ELF/Mirai User-Agent Observed” under the community comments indicating the address is associated with the Mirai malware. [3].
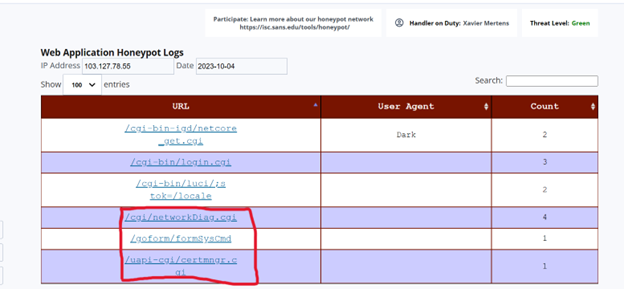
While this was the only attack from this actor towards my honeypot, there where multiple attacks on other honeypots that targeted various devices. A few of these include:
/cgi/networkDiag.cgi which targets Sunhillo SureLine surveillance products [4]
/goform/formSysCmd which targets JetWave pressure washers [5]
/uapi-cgi/certmngr.cgi which targets Geutebruck surveillance cameras [6]
How is CVE-2023-1389 being used in the wild?
CVE-2023-1389 has primarily been used as a way to expand botnets that are used is DDoS attacks. There have been reports that the Mirai malware botnet have been exploiting this vulnerability. Once access is gained to the device from the vulnerability “It then downloads the appropriate binary payload for the router's architecture to recruit the device into its botnet. The particular version of Mirai is focused on launching DDoS attacks, and its features indicate that it focuses primarily on game servers, having the ability to launch attacks against Valve Source Engine (VSE).” [7]
This vulnerability is also being exploited by a relatively new botnet called Condi. The purpose for exploiting the vulnerability remains the same as that of Mirai. The “Condi botnet contains a scanning component which search the internet (on ports 80 or 8080) for vulnerable TP-Link routers, then sends a hard-coded exploitation code that downloads and execute a remote shell script to infect a vulnerable device. [8]
Mitigations
TP-Link patched the vulnerability in April of this year, and pushed the firmware to customer’s whose devices are linked to a TP-Link Cloud account. For those who are still running a vulnerable version, updated firmware can be downloaded from the TP-Link official website here [9]
Conclusion
If there is a vulnerability that can be exploited by actors they will take advantage of it, that’s why it’s so important to stay up to date on patches, and know what devices are used in your environment. Firmware upgrades should be performed on your router on a regular basis to ensure that your device is secured against the latest threats and can usually be found on the routers company website. While CVE-2023-1389 has been primarily used for recruiting devices to botnets, it will be interesting to see what other creative uses actors use it for.
[1] Process Injection, Technique T1055 - Enterprise | MITRE ATT&CK®
[2] NVD - CVE-2023-1389 (nist.gov)
[3] https://www.virustotal.com/gui/ip-address/103.127.78.55
[4] NVD - CVE-2021-36380 (nist.gov)
[5] NVD - CVE-2023-23294 (nist.gov)
[6] Geutebruck Multiple Remote Command Execution (rapid7.com)
[7] TP-Link Archer WiFi router flaw exploited by Mirai malware (bleepingcomputer.com)
[8] Condi is a new botnet-for-hire with a business plan | TechSpot
[9] Download for Archer AX21 | TP-Link]
[10] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments