No-Defender, Yes-Defender
Recently I was made aware of a neat utility (https://github.com/es3n1n/no-defender/) which provides the capability to disable Windows Defender by abusing the WSC (Windows Security Center) registration that other AV and EDR providers utilize to become the main provider on systems, mostly to avoid conflict with Windows Defender.
It does this by abusing the middle-man WSC proxy app Avast bundles with their software, which provides access to the necessary WSC APIs for registration, and registers itself as an fraudulent AV provider, forcing Defender to step down (periodic scanning will still function if enabled manually).
As with all utilities that have the potential to aid in defense evasion, this will eventually make the rounds with active threat groups, until it is deemed obsolete or no longer viable.
To detect usage of this or similar tools, monitoring the “SecurityCenter” Windows event log for event ID 15 is ideal. This can help identify if an unwanted application registered and enabled itself as a security provider in place of Defender.
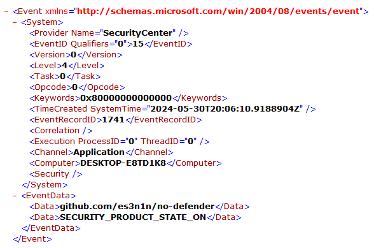
Figure 1: Triggered Event
Additionally, blocking the Avast signing certificate through an AppLocker publisher rule could also help hinder use of the tool.
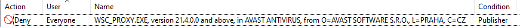
At the time of writing, EDR and AV vendors are picking up on this quickly, as evidenced by the threat label in VirusTotal and the increasing detection count.
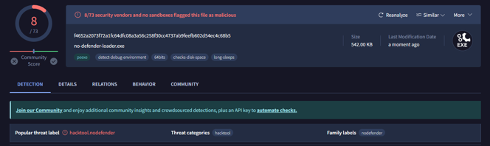
Figure 3: No-defender Loader detection [2]
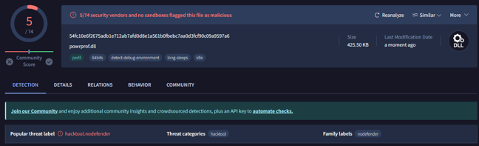
Figure 4: No-defender Detection[3]
Also included is a Yara rule to detect the Avast WSC Proxy components. Hash rules may be sufficient, but older versions of the components may also be equally vulnerable to abuse.
Yara Rule
import "pe"
rule nodefender_avastwsc
{
meta:
description = "Avast wsc proxy components used by no-defender"
hash = "79e53d36a40951ab328e153bac9c1e3adf3330b45899345e645889b9046f06e0"
hash = "de820b5e592cf456f6a4f8356195c4a335a51c6354ca7ac32ccd390e62d9becc"
strings:
$a1 = "Avast Software s.r.o" nocase
$a2 = "Cannot enable RPC marshaling into service when Avast client integration is not set" nocase
$a3 = {77 00 73 00 63 00 2E 00 64 00 6C 00 6C 00 00 00 72 75 6E}
$a4 = "BUILDS\\Release\\x64\\wsc_proxy.pdb" nocase
$s1 = {09 02 B3 6B 32 51 C3 28 08 3F 77 7C A0 84 28 FF}
$s2 = {03 F0 2A CA 05 1D 1C 93 30 EE AB D3 70 6E 83 6F}
condition:
uint16(0) == 0x5a4d
and $a1 and ($s1 or $s2) and ($a2 or $a3 or $a4)
and for any i in (0 .. pe.number_of_signatures) : (
(pe.signatures[i].issuer contains "DigiCert High Assurance Code Signing CA-1"
or pe.signatures[i].issuer contains "DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1")
and pe.signatures[i].subject contains "Avast"
)
}
References:
[1] https://github.com/es3n1n/no-defender
[2] https://www.virustotal.com/gui/file/f4652a2073f72a1fc64dfc08a3a56c258f30cc4737ab9feefb602d54ec4c68b5
[3] https://www.virustotal.com/gui/file/54fc10e6f2675adb1e712ab7afd0d8e1a561b0fbebc7aa0d3fcf90c09a9597a6


Comments